EXE Automatically Generating Inputs of Death Cristian Cadar











- Slides: 18

EXE: Automatically Generating Inputs of Death Cristian Cadar, Vijay Ganesh, Peter M. Pawlowski, David L. Dill, Dawson R. Engler 13 th ACM conference on Computer and communications security (CCS), 2006 Presented By: Clayton Andrews

Outline EXE Optimization Motivation Experiments Real bugs Search Heuristics How to use Conclusion Example Contributions STP

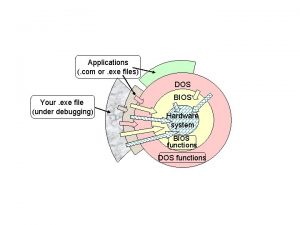
EXE EXecution generated Executions An effective-bug finding tool Not manual or randomly constructed input Runs on symbolic input allowed to be “anything”

EXE Code can generate its own test cases Runs the code on all inputs at once Follows all paths

Motivation Possible paths of code execution can be large Manual testing far from exhaustive Difficult for developers to reason all paths Random testing not sufficient Suppose bug exists for 1 input of 100 trillion Dynamic tools require initial test cases Presents same problem as manual test

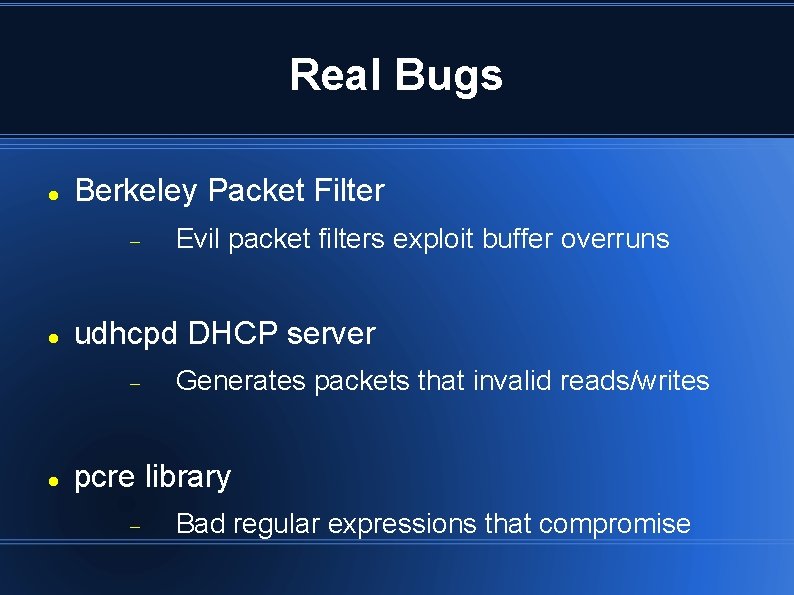
Real Bugs Berkeley Packet Filter udhcpd DHCP server Evil packet filters exploit buffer overruns Generates packets that invalid reads/writes pcre library Bad regular expressions that compromise

How to Use Simply call the method make_symbolic() on any input that is unconstrained Compiled using the EXE compiler, exe-cc Then compiled using a standard compiler E. g. gcc

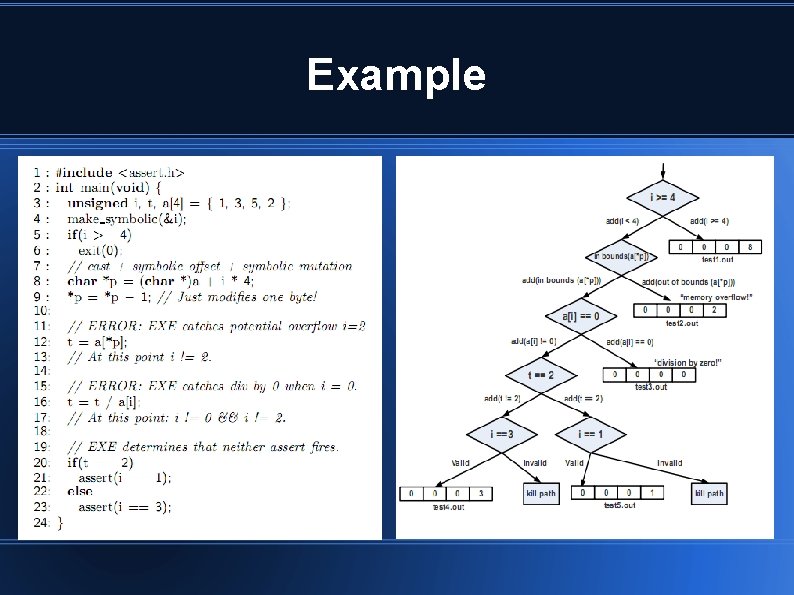
Example

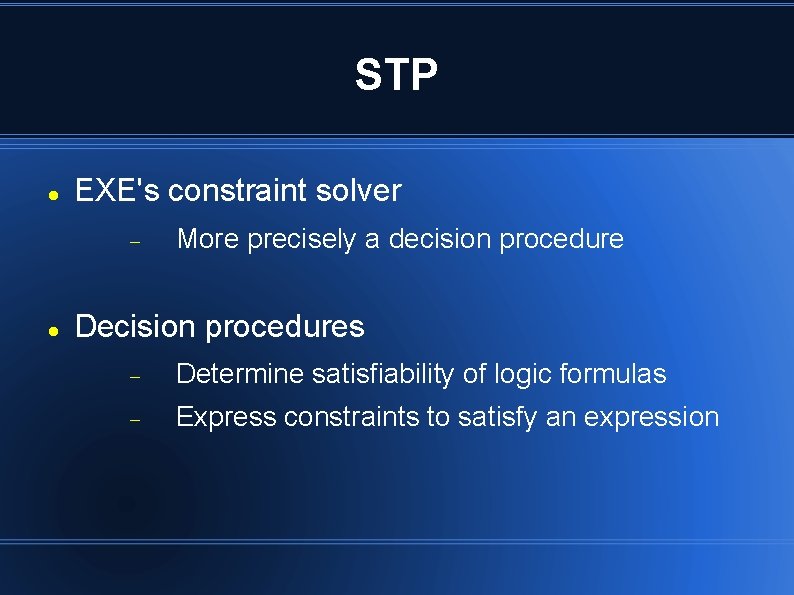
STP EXE's constraint solver More precisely a decision procedure Decision procedures Determine satisfiability of logic formulas Express constraints to satisfy an expression

STP Co-designed for EXE Faster than CVCL, a similar system 550 x faster

Optimizations Caching EXE caches results of satisfiability queries Constraint independence Breaks apart constraints into subsets (A[1]= A[2]+ A[3]) ∧ (A[2] >A[4]) ∧ (A[7]= A[8]) (A[1]= A[2]+ A[3]) ∧ (A[2] >A[4]) A[7]= A[8]

Experiments Bpf, pcre, udhcpd, expant and tcpdump

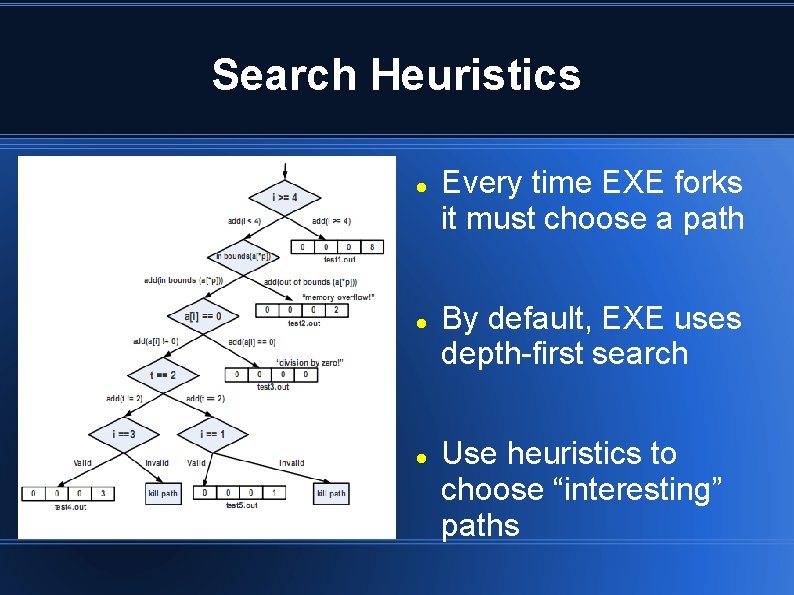
Search Heuristics Every time EXE forks it must choose a path By default, EXE uses depth-first search Use heuristics to choose “interesting” paths

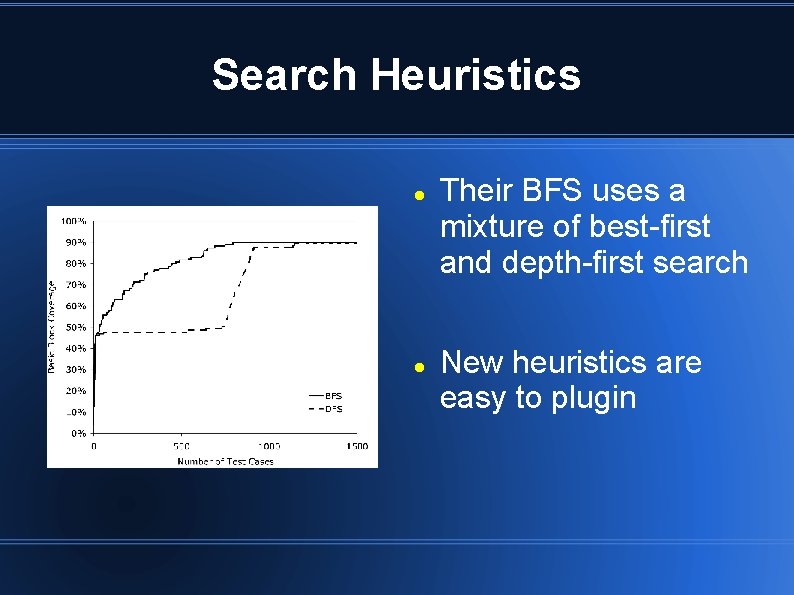
Search Heuristics Their BFS uses a mixture of best-first and depth-first search New heuristics are easy to plugin

Conclusion EXE uses symbolic execution to find bugs STP was co-designed to be fast EXE was powerful enough to uncover bugs in real programs

Contributions The decision procedure STP was created Code can be tested through all paths at once Does not rely on manual input or “luck”

Reference "EXE: automatically generating inputs of death", Cadar, Cristian and Ganesh, Vijay and Pawlowski, Peter M. and Dill, David L. and Engler, Dawson R. , 13 th ACM conference on Computer and communications security (CCS), 2006.

Questions?
 Exe: automatically generating inputs of death
Exe: automatically generating inputs of death Exe: automatically generating inputs of death
Exe: automatically generating inputs of death Cristian cadar
Cristian cadar Clint whaley
Clint whaley Difference between somatic death and molecular death
Difference between somatic death and molecular death Cristian ignat
Cristian ignat Cristian duarte edad
Cristian duarte edad Cristian valle ronceros
Cristian valle ronceros App1store
App1store Cristian torti
Cristian torti Cristian's algorithm
Cristian's algorithm Cristian viscione
Cristian viscione Dr cristian lara
Dr cristian lara Estomago e intestinos
Estomago e intestinos Cristian dragos
Cristian dragos Cristian david ocampo
Cristian david ocampo Cristian algorithm example
Cristian algorithm example Cristian fugaciu
Cristian fugaciu Tefido
Tefido