Ethics Privacy and Information Security Chapter 3 Introduction




















- Slides: 34

Ethics, Privacy, and Information Security Chapter 3 Introduction to Information System Marcello Singadji (singadji@gmail. com)

Pengantar Sistem Informasi – SIF 101 Learning Objectives • Describe the major ethical issues related to information technology and identify situations in which they occur. • Identify the many threats to information security. • Understand the various defense mechanisms used to protect • information systems. • Explain IT auditing and planning for disaster recovery.

Pengantar Sistem Informasi – SIF 101 Topic • Ethical Issues • Threats to Information Security • Protecting Information Resources

Ethical Issues

Pengantar Sistem Informasi – SIF 101 Kasus • Tahun 2001, duplikasi klikbca. com • Tahun 2004, data KPU yang acak-acak • Tahun 2013, ATM dibobol oleh kakakberadik

Pengantar Sistem Informasi – SIF 101 Ethical Issues • Ethics • Code of Ethics

Pengantar Sistem Informasi – SIF 101 Fundamental Tenets of Ethics • Responsibility • Accountability • Liability

Pengantar Sistem Informasi – SIF 101 Unethical vs Illegal • What is unethical is not necessarily illegal

Pengantar Sistem Informasi – SIF 101 The Four Categories of Ethical Issues • Privacy issues ▫ collecting, storing, and disseminating information about individuals. • Accuracy issues ▫ the authenticity, fidelity, and accuracy of information that is collected and processed • Property issues ▫ the ownership and value of information • Accessibility issues ▫ revolve around who should have access to information and whether they should have to pay for this access

Pengantar Sistem Informasi – SIF 101

Threats to Information Security


Pengantar Sistem Informasi – SIF 101 Factor Increasing the Treats to Information Security • Today’s interconnected, interdependent, wirelessly networked business environment • Government legislation • Smaller, faster, cheaper computers and storage devices • Decreasing skills necessary to be a computer hacker • International organized crime taking over cybercrime • Downstream liability • Increased employee use of unmanaged devices • Lack of management support

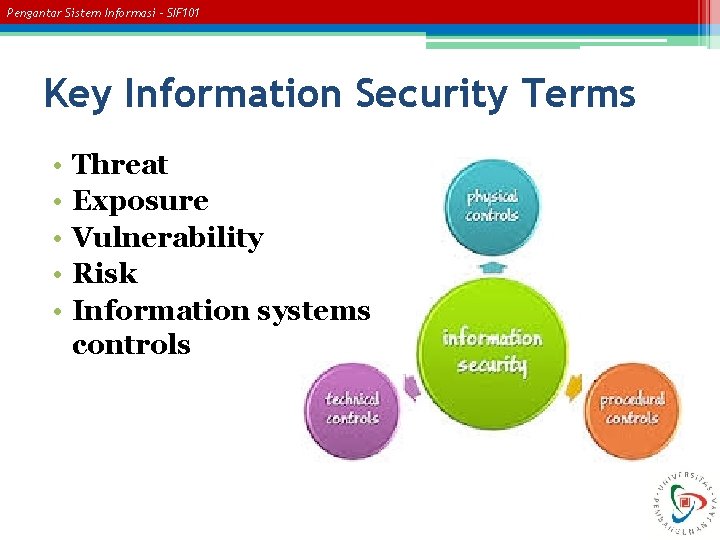
Pengantar Sistem Informasi – SIF 101 Key Information Security Terms • • • Threat Exposure Vulnerability Risk Information systems controls

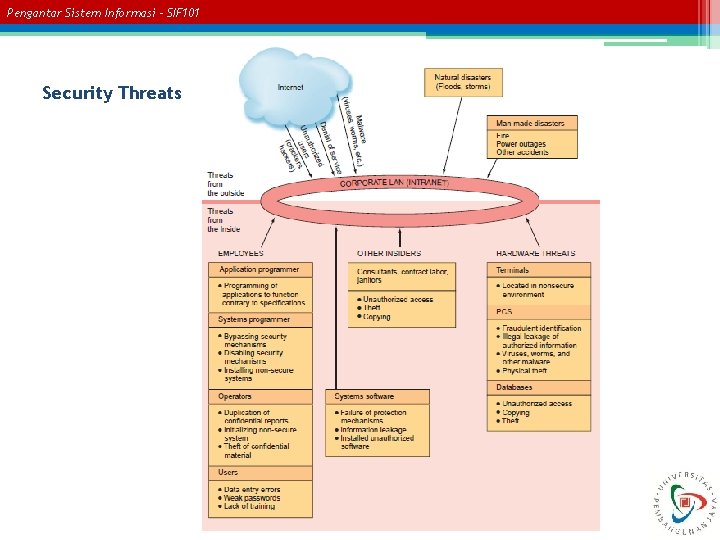
Pengantar Sistem Informasi – SIF 101 Security Threats

Pengantar Sistem Informasi – SIF 101 Categories of Threats to Information Systems - Whitman and Mattord (2003) • Unintentional acts ▫ Human Errors • Natural disasters • Technical failures ▫ Technical failures include problems with hardware and software • Management failures ▫ Management failures involve a lack of funding for information security efforts and a lack of interest in those efforts. • Deliberate acts ▫ Software attacks ▫ Identity theft

Protecting Information Resources

Pengantar Sistem Informasi – SIF 101 Risk!! There is always risk!

Pengantar Sistem Informasi – SIF 101 Risk Management • Risk analysis • Risk mitigation ▫ Risk acceptance ▫ Risk limitation ▫ Risk transference • Controls evaluation

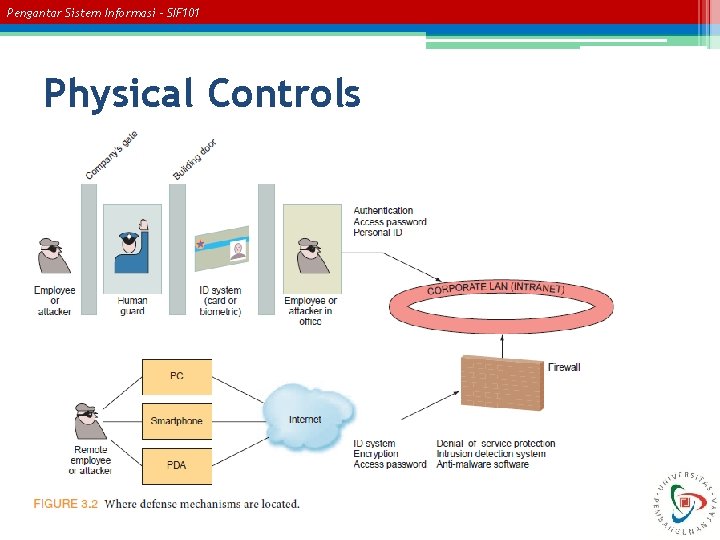
Pengantar Sistem Informasi – SIF 101 Controls • Physical Controls • Access Controls • Communications Controls

Pengantar Sistem Informasi – SIF 101 Physical Controls

Pengantar Sistem Informasi – SIF 101 Access Controls • Authentication

Pengantar Sistem Informasi – SIF 101 Access Controls • Authorization ▫ Privilege ▫ Least privilege

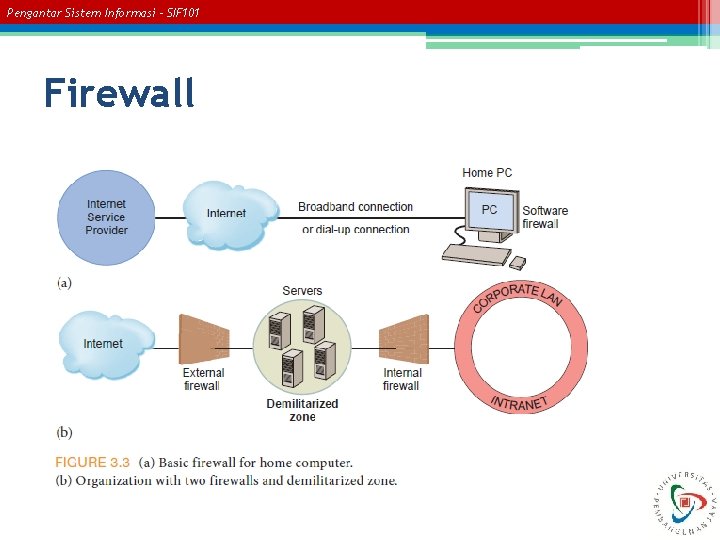
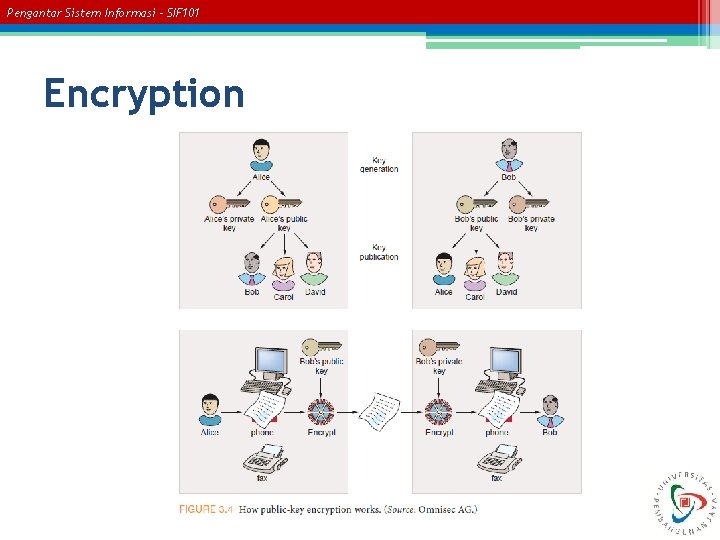
Pengantar Sistem Informasi – SIF 101 Communications Controls • • • Firewalls Anti-malware systems Whitelisting and Blacklisting Intrusion Detection Systems Encryption.

Pengantar Sistem Informasi – SIF 101 Firewall

Pengantar Sistem Informasi – SIF 101 Encryption

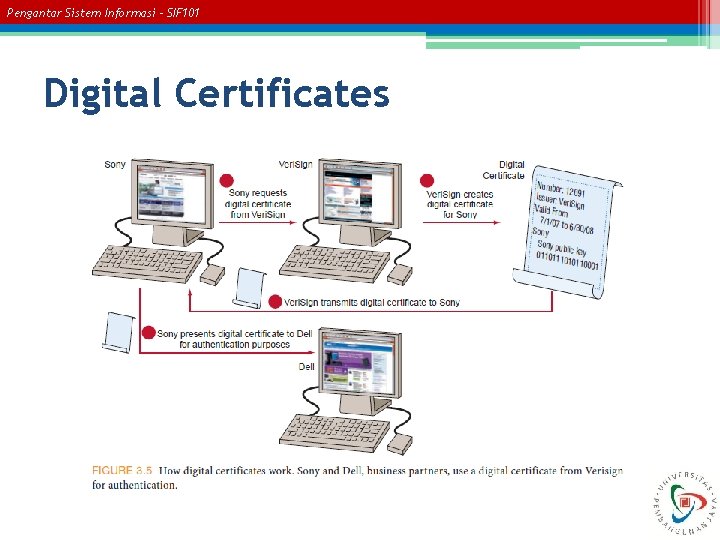
Pengantar Sistem Informasi – SIF 101 Digital Certificates

Pengantar Sistem Informasi – SIF 101 Communications & Network Controls • • Virtual Private Networking Secure Socket Layer (SSL) Vulnerability Management Systems Employee Monitoring Systems

Pengantar Sistem Informasi – SIF 101 Business Continuity Planning, Backup, and Recovery • Hot site ▫ fully configured computer facility, with all services, communications links, and physical plant operations • Warm site ▫ does include computing equipment such as servers, but it often does not include user work stations

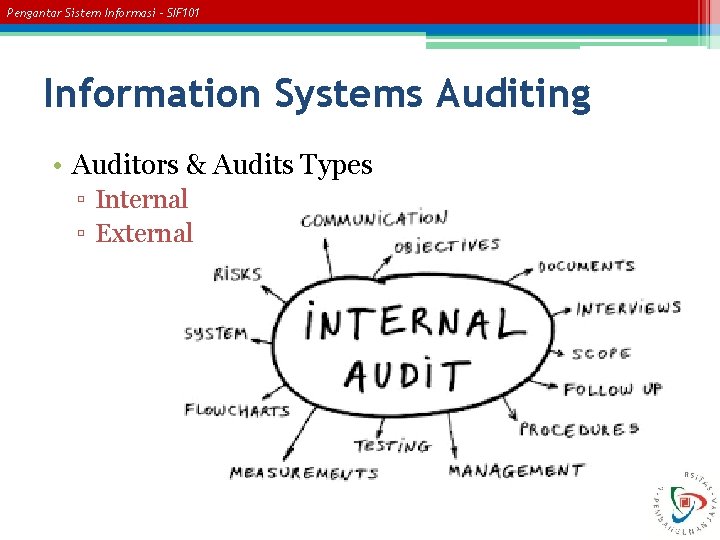
Pengantar Sistem Informasi – SIF 101 Information Systems Auditing • Auditors & Audits Types ▫ Internal ▫ External

Pengantar Sistem Informasi – SIF 101 How Is Auditing Executed? • Auditing around the computer • Auditing through the computer • Auditing with the computer

Pengantar Sistem Informasi – SIF 101

Referensi Introduction to Information Systems, Third Edition, R. Kelly Rainer Jr, Casey G. Cegielski, Wiley
