Ethics in an Intranet Culture Intranet Culture Intranet
































- Slides: 38


Ethics in an Intranet Culture

Intranet Culture Intranet Network that companies use to share files, utilize websites, and collaborate. Usually cannot be accessed from the Internet. Intranet Culture The system of shared beliefs, values, customs, and behaviours that the members of a company use to cope with their world and with one another.

Internet/Intranet Realities Good News It is estimated that by the year 2002 more than 88 million employees in U. S. alone will be connected to the Internet through their company Intranet. This will allow employees to gather information and correspond with clients more efficiently and effectively than ever before. Bad News The introduction of the Intranet to the company toolbox comes with many dangers. These dangers pose a troublesome paradox for executives across America. On one hand, companies have to much to gain from the Internet to banish it from the workplaces. At the same time, there is far too much to lose by granting employees free reign.

Facts • 268 million corporate PC’s are connected to the World Wide Web • 60% of Internet activity includes visits to unproductive, inappropriate, and potentially dangerous sites • Most companies have no company rules on computer use and misuse

Ethical Responsibilities The Intranet is setup with a firewall to protect the institution from “outside harm” but must also protect itself from “harm from within”. Ethical responsibility must be part of the Intranet culture to help inform and provide guidelines to “insiders”.

Problem Areas • EMAIL • WEB SURFING • SOFTWARE


You’ve Got Mail Email is a tremendously powerful communications tool, used by millions of people in thousands of positive ways. Unfortunately, such a powerful tool has the potential to be used in other, less productive, ways. Can be used to breach security of an Intranet - by disgruntled employees who can distribute company secrets through email - by accidents such as attaching important documents to emails Total collaboration of emails - add up to loss of work hours - work-related activities suffer - instant messaging breaks concentration

Email Statistics - Men are the worst offenders for trying to kindle an online office romance, with 27% admitting to using email for “flirting in the office” compared with 13% of women - Gossiping about colleagues online was the secondbiggest waste of working time by men - Among women the biggest email abuse was “planning social life with friends, ’’ followed by contacting brothers and sisters and gossiping about other staff - 13% of men and seven percent of women admitted using email at work to forward Internet sex links - Other misuses of email included forwarding jokes to colleagues and seeking new employment.

Email Abuse Email can be “piggybacked” with: - Sexual Harassment - Mail bombs - Tasteless jokes Knock Who's there ! Adder who ? Adder you get in here ? - Viruses - Porn

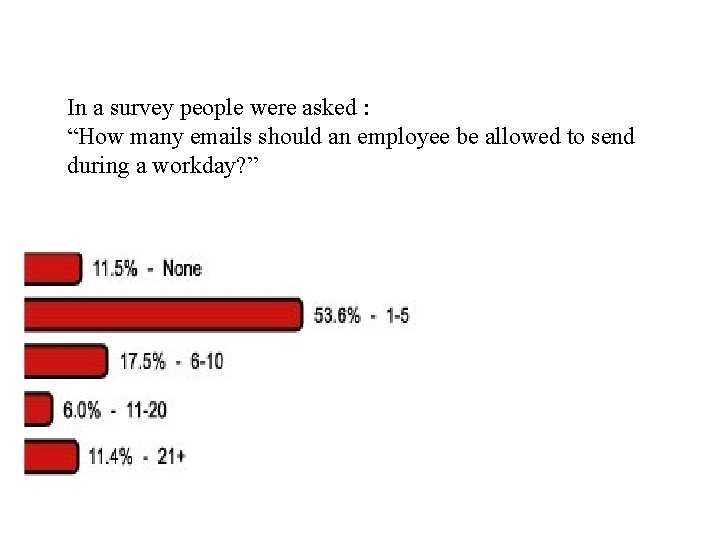
In a survey people were asked : “How many emails should an employee be allowed to send during a workday? ”

Web Surfing

Harm in Surfing? So what’s the harm in a little personal surfing every now and then? Actually the costs and consequences associated with non-related Internet use are staggering. They hit corporations most commonly in three forms: - productivity costs - bandwidth loss - legal liability - security breaches

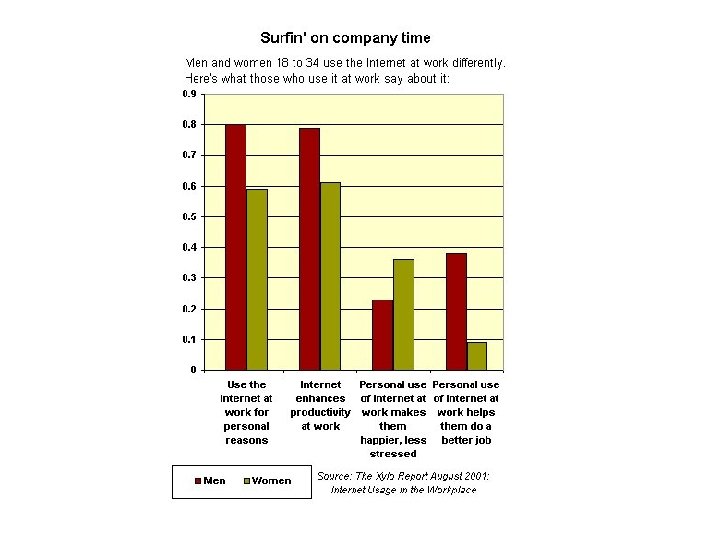
Surfing on the job On any given day a survey reveals 18% of employees visit the Internet 10 or more times for nonwork-related activity If not working, then what are they doing? 72% 40% 37% 34% 28% 12% read the news shop search for another job check stock reports coordinate social events visit adult sites


Software

Software Abuse Downloading software from the company - can be held liable under both civil and criminal law - can seek to stop you from using its software immediately and can seek monetary damages - the copyright owner may then choose between actual damages, which includes the amount it has lost because of your infringement as well as any profits attributable to the infringement, and statutory damages, which can be as much as $150, 000 for each program copied - the government can criminally prosecute you for copyright infringement, if convicted, you can be fined up to $250, 000, or sentenced to jail for up to five years, or both

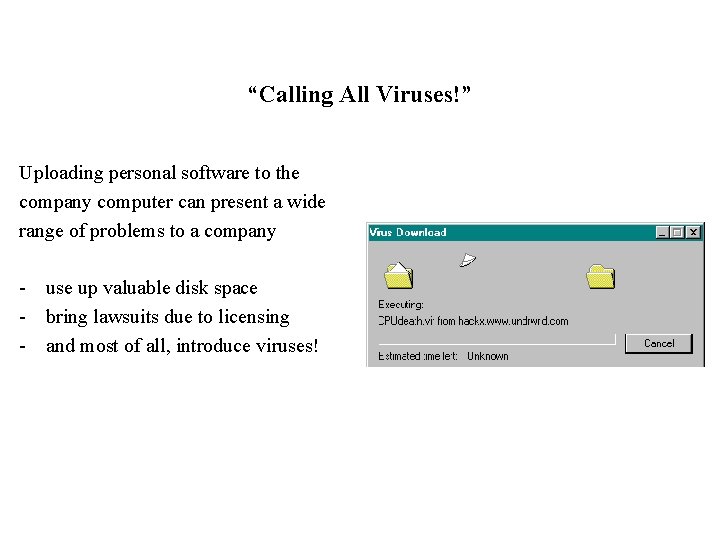
“Calling All Viruses!” Uploading personal software to the company computer can present a wide range of problems to a company - use up valuable disk space - bring lawsuits due to licensing - and most of all, introduce viruses!

Bandwidth Hogs - Nonwork-related surfing clogs digital pipelines According to a survey by Dataquest, 20% of workers use Internet connections more than three hours a week for personal matters. Downloading music, shopping, or just browse the Web can impede work-related activity of co-workers. Workers sending or receiving personal emails with large attachments Servers routinely crash on Valentine’s day and Christmas due to load Spam, chain letters, “junk” mail compound problem

Enter Ethics

Setting the Stage for Ethics policies are still evolving or even non-existent in most companies. IAP’s (Internet Access Policy) or AUP’s (Access Use Policy) are laying the groundwork for ethical guidelines in dealing with the company Intranet and Internet. As the number of employee connections to the Intranet increase, so does the awareness that ethical policies are needed to combat abuse.

AUP At a minimum, every company that provides Internet access for its employees should have a detailed Acceptable Use Policy (AUP) in place. Similar to other company policies, the AUP should clearly define • where employees can and cannot go online • when they can surf the Internet and use email for personal reasons • which types of online activity are strictly forbidden • what consequences will result if the policy is violated

Why Does the Industry Care About Ethics? • Link between ethics and customer/employee loyalty • What kind of company do you want to work for or deal with? • It takes years to build a good company reputation • Each employee has the power to tarnish that reputation • Any one employee can get the company into serious trouble

Why Does the Industry Care About Ethics? • Companies can build a company culture of ethical business conduct • Commitment to integrity must start at the top • Employees watch to see if “management walks the walk” • Employees need to see that ethical behavior is valued and rewarded • Fines for civil or criminal violations

Tools That Help Us Make Good Ethical Decisions • The code of ethics and business conduct sets the standard • Company ethics officers promote a comprehensive and consistent ethics program monitor performance of other employees respond to helpline calls facilitate training • Helpline toll-free confidential help disciplinary actions • Ethics awareness training • Compliance training employees need to know and understand laws, regulations, and policies applicable to their job duties • Communication

Benefits of Ethics Program to a Company • • • Service Reduced misconduct New business Higher margins Shareholder confidence

Costs to the Company Lack of control or policy with regard to the Intranet can affect the bottom line of a company - company must expend dollars for software to combat and survey their company Intranet - resources must be allocated to extra staff and technology personnel to handle abuse - productivity loss in the workplace

What about the financial impact? Cyber-slacking wreaks havoc on the bottom line. Equation to figure out fully burdened cost(FBC) of an employee: 1. FBC = 2(mean hourly wage) 2. Then multiply FBC by Internet usage(in hours) 3. Finally multiply by # of employees with Internet access Example : mean =$16. 54 per hour 1. FBC = ($16. 54 * 2) = $33. 08 2. $33. 08 * 1. 5(hours) 3. 82. 7 * 500(Intranet employees) = $16, 540 per day cost to the company Result: Corporate Networks Are Paying the Price. Wasting time online accounts for thirty to forty percent of all lost productivity in the workplace.

Making a Case for Discipline Nonwork-related Intranet use can cost companies dearly in the courtroom - could lead to potentially embarrassing and expensive lawsuit - threatens credibility of company - company unity and trust is at risk

Ten Commandments for Computer Ethics 1. Thou shalt not use a computer to harm other people. 2. Thou shalt not interfere with other people's computer work. 3. Thou shalt not snoop around in other people's files. 4. Thou shalt not use a computer to steal. 5. Thou shalt not use a computer to bear false witness. 6. Thou shalt not use or copy software for which you have not paid. 7. Thou shalt not use other people's computer resources without authorization. 8. Thou shalt not appropriate other people's intellectual output. 9. Thou shalt think about the social consequences of the program you write. 10. Thou shalt use a computer in ways that show consideration and respect.

Laws

Data Protection Act 1998 (DPA) This Act regulates the processing of employees' personal data by employers. The Data Protection Commissioner has issued a draft Code of Practice in which she deals with monitoring of emails and internet use by employers. This appears to impose stricter limitations on employers' ability to monitor than the Regulations, but is likely to change to be brought into line with them.

Obscene Publications Act 1959 This Act makes it a criminal offence to send material to another person which is likely to ‘deprave or corrupt’ the recipient. There are tighter provisions relating to the handling of child pornography, under the Criminal Justice Act 1988 and the Protection of Children Act 1978.

Contract of Employment – Employee Rights The contract of employment imposes an implied duty on the employer to act in a manner that will not undermine its duty of ‘trust and confidence’. If the employer is unreasonable in its investigation of suspected internet and email misuse, it could be in breach of this duty, which could entitle the employee to resign and claim constructive dismissal.

Contract of Employment – Employer Rights Sex Discrimination Act 1975 and Race Relations Act 1976 These Acts outlaw sex and race-based discrimination. The sending of an email by an employee (or even possibly someone from outside the company) which has sexual or racial content, may amount to an act of sexual or racial harassment for which the employer could be liable, unless it has taken steps to reduce the risk of such emails being distributed.

The Telecommunications (Lawful Business Practice) (Interception of Communications) Regulations 2000 These Regulations dilute the requirements of RIPA and allow certain monitoring in the course of legitimate business practice. They allow email (and telephone) monitoring without consent for, among others, the following reasons: -Quality control monitoring -Combating crime -Combating unauthorized use of the system (for instance, investigating suspected misuse of email or internet) -Determining whether the communication is business-related (this allows an employer to inspect the inbox of an employee who is absent from work, in order to check whether any business-related emails have come in).

The End!
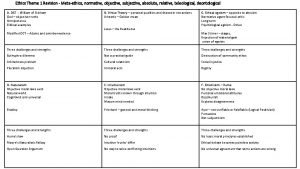
 Deontology
Deontology Compare micro-ethics and macro-ethics.
Compare micro-ethics and macro-ethics. Beneficence examples
Beneficence examples Teleological ethics vs deontological ethics
Teleological ethics vs deontological ethics 6075 meaning
6075 meaning Theological voluntarism
Theological voluntarism Descriptive ethics
Descriptive ethics Metaethics vs normative ethics
Metaethics vs normative ethics Branches of ethical philosophy
Branches of ethical philosophy Non cognitivism
Non cognitivism Descriptive ethics vs normative ethics
Descriptive ethics vs normative ethics Ethics in business communication
Ethics in business communication Culture
Culture Individualistic culture definition
Individualistic culture definition Quality culture changing hearts minds and attitudes
Quality culture changing hearts minds and attitudes Vocational subculture
Vocational subculture Ethnocentrism examples
Ethnocentrism examples Inert organizational culture
Inert organizational culture Difference between american culture and indian culture
Difference between american culture and indian culture Surface culture deep culture and esol
Surface culture deep culture and esol Popular culture examples
Popular culture examples Batch culture vs continuous culture
Batch culture vs continuous culture Individual culture traits combine to form culture patterns.
Individual culture traits combine to form culture patterns. Stroke culture method
Stroke culture method Stroke culture method
Stroke culture method Stroke culture method
Stroke culture method Fed-batch
Fed-batch Describe lawn culture and surface plating
Describe lawn culture and surface plating Folk culture and popular culture venn diagram
Folk culture and popular culture venn diagram Homework due today
Homework due today Slogan promoting deontological ethics
Slogan promoting deontological ethics Professional issues in information system
Professional issues in information system Holistic technology in human values
Holistic technology in human values What is sociocentrism in ethics
What is sociocentrism in ethics Etika tidak tertulis
Etika tidak tertulis Chapter 4 business ethics and social responsibility pdf
Chapter 4 business ethics and social responsibility pdf Acm code of ethics summary
Acm code of ethics summary Teachers violating the code of ethics in georgia
Teachers violating the code of ethics in georgia Ethics photojournalism
Ethics photojournalism