Ethics and copyright GEO 802 Data Information Literacy



















![Copyright versus License • Copyright: “ [T]he body of exclusive rights granted by law Copyright versus License • Copyright: “ [T]he body of exclusive rights granted by law](https://slidetodoc.com/presentation_image/595375f5e8f87d839ea37a06f26828c0/image-25.jpg)







- Slides: 37

Ethics and copyright GEO 802, Data Information Literacy Fall 2020 – Lecture 9 Gary Seitz, MA

Lesson 9 Outline Identify ethical, legal, and policy issues Define copyrights, licenses and waivers Understand reasons behind data restrictions Discuss ethical considerations Luis Prado from The Noun Project

Learning objectives • Be aware of ethical requirements that apply to the collection and management of data involving human subjects. • Understand the difference between privacy and confidentiality and how they apply to the management of research data. • Explain ethical and legal considerations related to data sharing and retention

Learning Outcomes After completing this lesson, participants will be able to: • Identify ethical, legal, and policy issues for managing research data • Define copyrights, licenses and waivers • Understand reasons behind data restrictions and how to observe them • Discuss ethical considerations surrounding the use of research data

Why might data use or sharing be restricted? • Threatened and endangered species • National security and classified research • Export controls • Can apply to technologies and data • Use of Human Subjects • Personally identifiable information of any kind

Ethics of collecting data on human subjects • What data needs to be safeguarded during analysis and destroyed after its use • People-related data need to be preserved according to Swiss data protection law • The deletion of individual datasets must be possible at all times • Ethic principles of the University of Zurich

Which research is subject to ethical review? Any research involving the use of human participants or live animals will usually be subject to ethical review. Similarly, research which involves referencing individual subjects (people) or storing identifiers for individuals will usually be subject to ethical review, unless the data is obtained through pure observational studies of public behaviour. 'Pure' observational studies • • are of human action that occurs in a forum open to the general public are non-invasive and non-interactive (pure observational) require no interaction with participants do not identify participants

Privacy and research • • Individuals are normally considered to have a ‘right to privacy’ - the state of being free from intrusion or disturbance in one's private life or affairs. Research proposals need to indicate how data will be collected about human subjects. Ethical reviews will consider how intrusive this is for the subjects. The right to privacy implies the need to obtain consent from research subjects. Consent form of UZH

Privacy vs. Confidentiality Privacy Protects access to individuals (or entities) Confidentiality Protects access to information about individuals Can be thought of as information privacy

Confidentiality and research • Oftentimes the consent form will include a promise to the subject that the researcher will not disclose confidential information. • Keeping this agreement implies controls on storage, handling, and sharing of personal data. • Strategies can include • If possible, collect the necessary data without using personally identifying information. • If personally identifying information is required, de-identify your data upon collection or as soon as possible thereafter. • Avoid transmitting unencrypted personal data electronically.

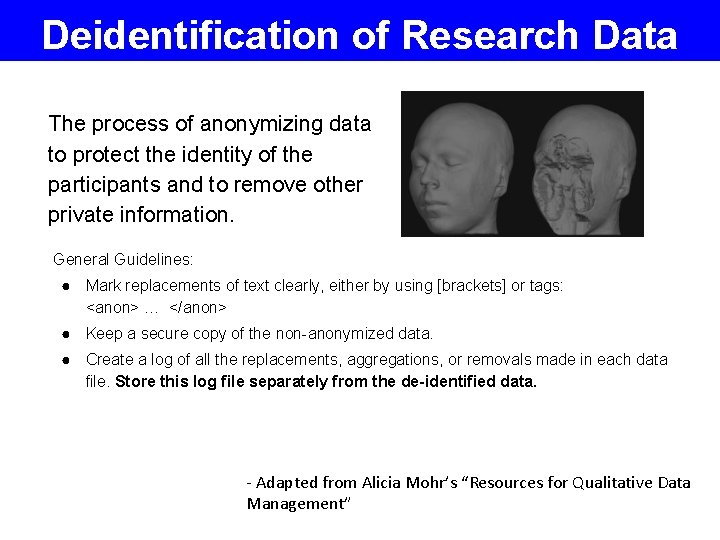
Deidentification of Research Data The process of anonymizing data to protect the identity of the participants and to remove other private information. General Guidelines: ● Mark replacements of text clearly, either by using [brackets] or tags: <anon> … </anon> ● Keep a secure copy of the non-anonymized data. ● Create a log of all the replacements, aggregations, or removals made in each data file. Store this log file separately from the de-identified data. - Adapted from Alicia Mohr’s “Resources for Qualitative Data Management” Image: http: //www. na-mic. org/Wiki/index. php/Mbirn: _Defacer_for_structural_MRI

Additional De-identification Techniques ● Get consent to share (later) (Example language from ICPSR) ● Don't “identify” in the data creation process ○ When recording audio, do not use names, place of employment, etc. ○ Arrange with participants on using pseudonyms, instead of “my uncle John, ” use “an uncle of mine. ” ● Audio/Video: Bleep out names or blur faces. Remember: Document the steps taken to remove identifiers.

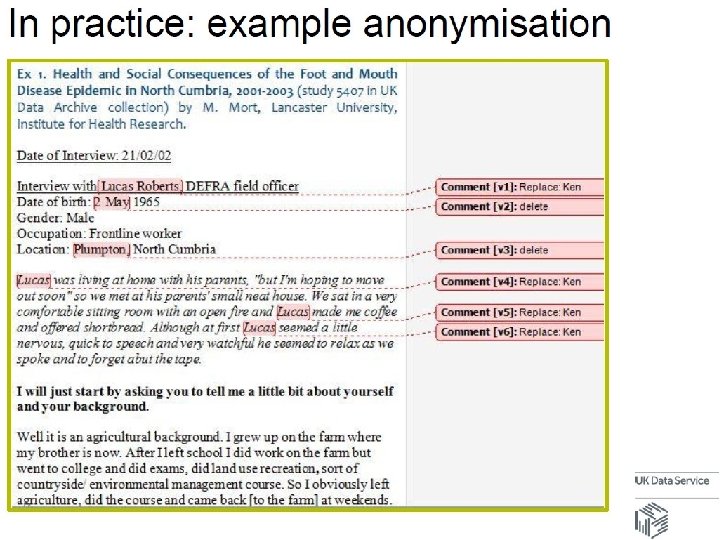
Some key anonymisation techniques Data masking: This involves stripping out obvious personal identifiers such as names from a piece of information, to create a data set in which no person identifiers are present. • Partial data removal – results in data where some personal identifiers, eg name and address have been removed but others such as dates of birth, remain. • Data quarantining - The technique of only supplying data to a recipient who is unlikely or unable to have access to the other data needed to facilitate re-identification. It can involve disclosing unique personal identifiers – eg reference numbers – but not the ‘key’ needed to link these to particular individuals.

Some key anonymisation techniques Pseudonymisation : De-identifying data so that a coded reference or pseudonym is attached to a record to allow the data to be associated with a particular individual without the individual being identified. Deterministic modification is a similar technique. ‘Deterministic’ here means that the same original value is always replaced by the same modified value. This means that if multiple data records are linked, in the sense that the same name (or address, or phone number, for example) occurs in all those records, the corresponding records in the modified data set will also be linked in the same way. This facilitates certain types of data analysis.

Some key anonymisation techniques Text anonymisation helper tool An add-on MS Word macro developed by the UK Data Archive for aiding anonymisation of qualitative data. Available to download as a zip file, with how to install instructions via Wiki

Some key anonymisation techniques


Examples of published sensitive data Explore one of these examples of published sensitive data: 1. Pregnancy and Lifestyle dataset shows how sensitive, deidentified data can be safely and openly shared. Click on “Go to Data Provider” to see the actual data. 2. This one page story tells how sensitive data from the Australian Longitudinal Study of Women’s Health data has been successfully published for almost 20 years. 3. A practice in anonymising qualitative data https: //www. cessda. eu/Training. Resources/Library/Data-Management-Expert-Guide/5. Protect/Anonymisation (in the middle of the Webpage)

How do you share and publish sensitive data? • Open the Publishing and sharing sensitive data poster below to get an overview of issues and solutions.

Read and write a one page memo 1. Scan the ANDS Safely sharing sensitive data webpage. 2. Follow a couple of the links on the sensitive data page which are of particular interest to you. 3. Consider the different techniques required to de-identify quantitative and qualitative data. The UK data service has information on anonymisation of both. 4. Explore some tools and resources for practical advice on how to de-identify data. Have a look at the ANDS Deidentification Guide

Who Owns Data? It depends… • Who is funding your research? • What is your institution’s data ownership policy? • Are you working under a grant or contract? • Who owns my data? Module 5: Legal & Ethical Considerations

Intellectual Property Rights • Intellectual Property Rights (IPR) can be defined as rights acquired over any work created or invented with the intellectual effort of an individual. These rights are time-limited and do not require explicit assertion. • Owners of works are granted exclusive rights • to publish the work • to license the work’s distribution to others • to sue in case of unlawful or deceptive copying • It may be possible to waive these rights through a public declaration similar to a licence.

Intellectual Property Rights and Research Data “Intellectual property rights, very broadly, are rights granted to creators and owners of works that are the result of human intellectual creativity” (jisclegal. ac. uk) Copyright Creative works fixed in material form. Designs Appearance and shape of product Patents Inventions – things that make things work Trade marks Signs that distinguish goods and services • Moral Rights – Right to be attributed for your work. – Right to object to derogatory treatment of your work.

Who can claim ownership? • • • You A funder Scientist, researcher, PI An institution A private company Nobody
![Copyright versus License Copyright The body of exclusive rights granted by law Copyright versus License • Copyright: “ [T]he body of exclusive rights granted by law](https://slidetodoc.com/presentation_image/595375f5e8f87d839ea37a06f26828c0/image-25.jpg)
Copyright versus License • Copyright: “ [T]he body of exclusive rights granted by law to copyright owners for protection of their work. ” (U. S. Copyright Office) • • Facts and data cannot be protected by copyright Metadata and data arrangement can be protected (sometimes) • License: States what can be done with the data and how that data can be redistributed (e. g. , GPL and CC) • Waiver: (e. g. , CC 0) relinquishes all rights of ownership and usually commits the “work” to the public domain • Intellectual property laws will vary depending upon country or region

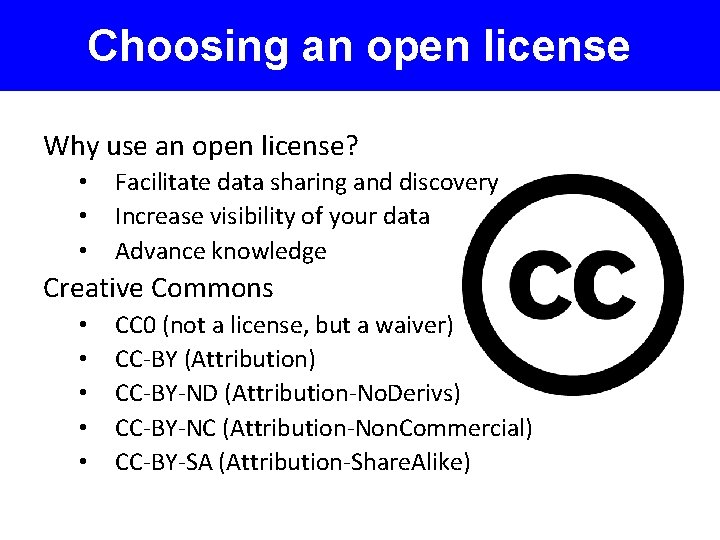
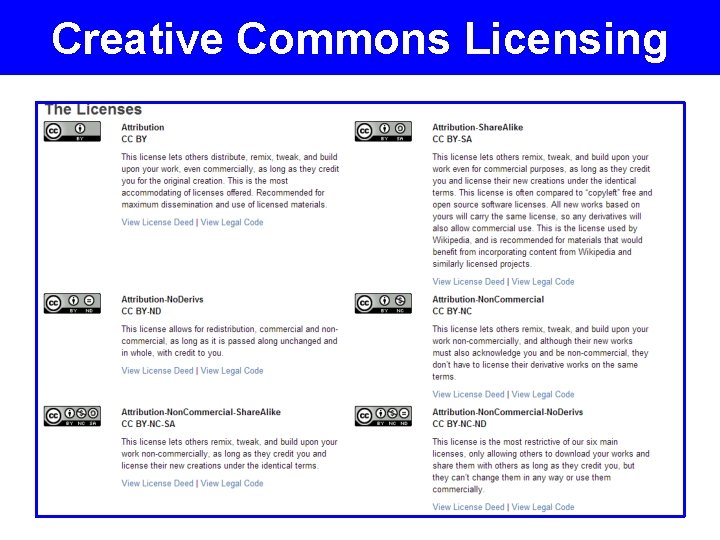
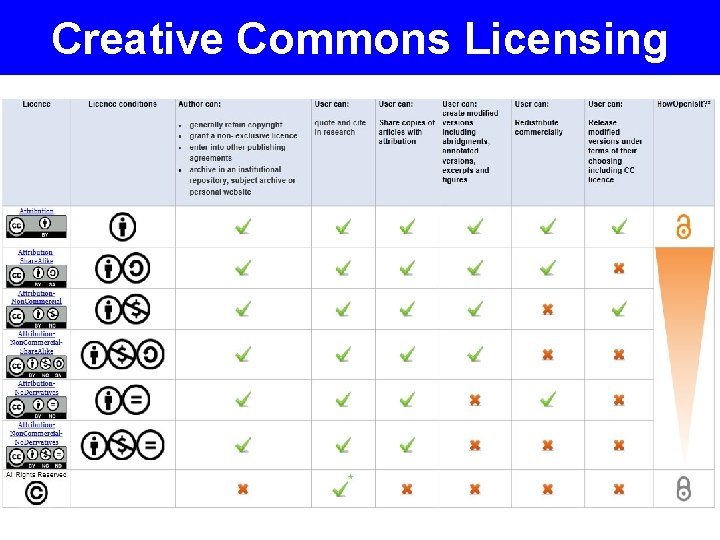
Choosing an open license Why use an open license? • • • Facilitate data sharing and discovery Increase visibility of your data Advance knowledge Creative Commons • • • CC 0 (not a license, but a waiver) CC-BY (Attribution) CC-BY-ND (Attribution-No. Derivs) CC-BY-NC (Attribution-Non. Commercial) CC-BY-SA (Attribution-Share. Alike)

Creative Commons Licensing

Creative Commons Licensing

Other Considerations Copyright vs. Copyleft “a strategy of utilizing copyright law to pursue the policy goal of fostering and encouraging the equal and inalienable right to copy, share, modify and improve creative works of authorship. ” (copyleft. org) Attribution Stacking CC-BY requires all derivative works to acknowledge all contributors to all works from which they are derived. Redistribution CC-BY-SA requires all works that derive from a work designated BY-SA must be distributed under the same license.

Norms for Data Use When using data • • • Give credit to the data authors Be responsible with the data Share what you learned Respect the Data License or Waiver Understand follow any restrictions or regulations

When do data enjoy copyright • When the dataset is an expressive work • Even if not, the metadata may enjoy copyright • What if the data are merely a set of facts? • A simple list or spreadsheet might not enjoy copyright • The EU established a ‘database right’ (‘sui generis’ right) to protect substantial investment made by database producers in obtaining, verifying and presenting database contents. • Also, the structure of the database, including the selection and arrangement of the database’s contents may meet a test of intellectual creativity bestowing copyright.

Exercise 9. 1: Copyright Quiz • • The ownership of copyright is the same for creators of work regardless of their academic status (e. g. students or lecturers), employment status (e. g. employed or self employed)? Intellectual Property Rights can be bought, sold, rented, gifted and bequeath? • Copyright requires registration? • Copyright protection lasts forever? • Most web content can be re-used freely? • The onus of responsibility lies with the user of a work to get permission, even if the rights holder is unknown or cannot be traced?

Copyright Quiz • • The ownership of copyright is the same for creators of work regardless of their academic status (e. g. students or lecturers), employment status (e. g. employed or self employed)? Intellectual Property Rights can be bought, sold, rented, gifted and bequeath? • Copyright requires registration? • Copyright protection lasts forever? • Most web content can be re-used freely? • The onus of responsibility lies with the user of a work to get permission, even if the rights holder is unknown or cannot be traced? False True False True

Exercise 9. 2: Copyright & Research Data Copyright protects the expression of an idea Data is not covered by copyright Copyright does not need to be registered Different forms of creative work are copyrighted for different lengths of time. Different institutions have different copyright clauses in their employment contracts. Different countries have different copyright law.

Copyright & Research Data Copyright protects the expression of an idea not the idea itself. Data is not covered by copyright but the arrangement of data in a spreadsheet or database is. Copyright does not need to be registered it is automatically assigned when a creative work is produced. Different forms of creative work are copyrighted for different lengths of time. Different institutions have different copyright clauses in their employment contracts. Different countries have different copyright law.

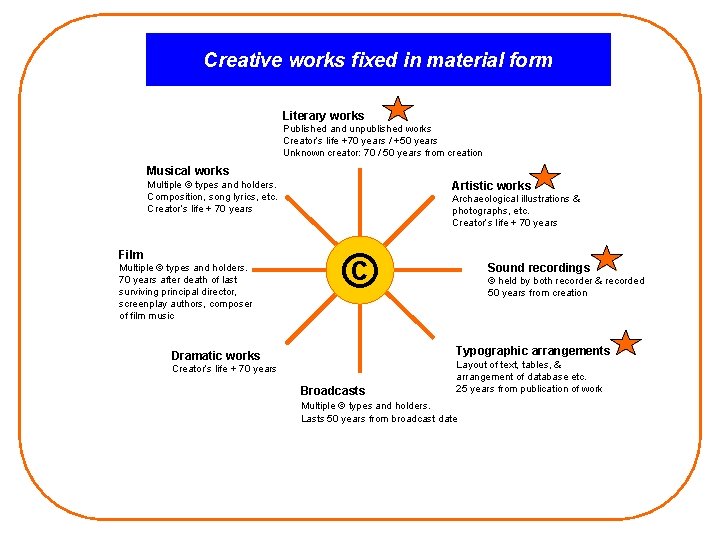
Creative works fixed in material form Literary works Published and unpublished works Creator’s life +70 years / +50 years Unknown creator: 70 / 50 years from creation Musical works Multiple © types and holders. Composition, song lyrics, etc. Creator’s life + 70 years Film Multiple © types and holders. 70 years after death of last surviving principal director, screenplay authors, composer of film music Artistic works Archaeological illustrations & photographs, etc. Creator’s life + 70 years © Sound recordings © held by both recorder & recorded 50 years from creation Typographic arrangements Dramatic works Creator’s life + 70 years Broadcasts Layout of text, tables, & arrangement of database etc. 25 years from publication of work Multiple © types and holders. Lasts 50 years from broadcast date

Last word Best to create a public use dataset that you are comfortable about getting used, if putting online. And don’t forget the Freedom of Information Act and related legislation may compel you to release data, especially if in the public interest!