Espionage and the Insider Threat Mike Weissert COSC
















- Slides: 17

Espionage and the Insider Threat Mike Weissert COSC 481 April 20, 2006

Outline Definition: Espionage u Facts u Preconditions for Espionage u Statistics u Counter-Espionage Techniques u References u Questions u

Definition: Espionage u “The practice of obtaining information about an organization or a society that is considered secret or confidential (spying) without the permission of the holder of the information” • Wikipedia

Facts u Espionage effects all businesses • Large (government) • Medium • Small u Unfortunately, smaller businesses are unaware of espionage in workplace u “ 72 per cent of businesses (small, medium and larger companies) without any kind of counterespionage protocols in place are destined to suffer some kind of related financial loss within two years” • Canadian Security Intelligence Service (CSIS)

Preconditions for Espionage u 4 necessary preconditions for Espionage to occur: 1) Opportunity to commit espionage 2) A motive or a need to be satisfied through espionage 3) An ability to overcome natural inhibitions to the espionage 4) A triggering event that sets the espionage in motion

Precondition #1 Opportunity u Two types of opportunity exist: 1) Having access to sensitive information or material 2) Having personal acquaintance with, or easy access to, persons interested in the sensitive information/material u With opportunity there is always temptation

Precondition #2 Motive u Money • success, power, influence, happiness, self-esteem u u A method to feel powerful An outlet for anger Revenge Ideology • Belief that the espionage act is in the best interest of the company/US government u u Excitement Coercion (Blackmail)

Precondition #3 Ability to Overcome Natural Inhibitions u Natural Inhibitions • • Moral values Loyalty to managers or co-workers Loyalty to country Fear of being caught u u Laws and punishments When one looses their morals or feels that there are no morals in today’s society, their willingness to commit espionage increases

Precondition #4 Triggering Event u “Significant event that pushes the insider past their breaking point and they are no longer able to take the stress” • • u Unable to learn from the event Unable to adjust their expectations Unable to work harder to make changes Give in too easily to the stress presented by the event When triggering event occurs, the person’s actions can hurt themselves or the organization

Statistics u “ 70 percent of the market value of US firms resides in their trade secrets and intellectual properties” • (ASIS/Price. Waterhouse. Coopers) u From 1994 to 1997, the number of economic espionage cases investigated by the Federal Bureau of Investigation has doubled (Fitzpatrick)

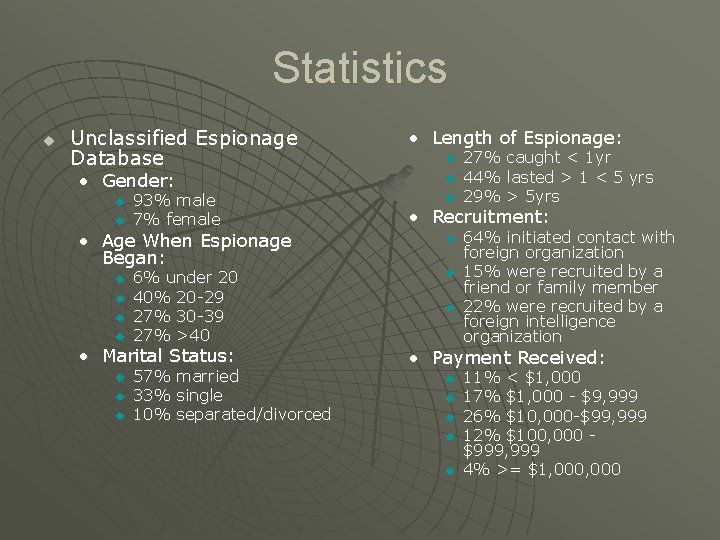
Statistics u Unclassified Espionage Database • Gender: u u 93% male 7% female • Age When Espionage Began: u u 6% under 20 40% 20 -29 27% 30 -39 27% >40 • Marital Status: u u u 57% married 33% single 10% separated/divorced • Length of Espionage: u u u 27% 44% 29% caught < 1 yr lasted > 1 < 5 yrs > 5 yrs • Recruitment: u u u 64% initiated contact with foreign organization 15% were recruited by a friend or family member 22% were recruited by a foreign intelligence organization • Payment Received: u u u 11% < $1, 000 17% $1, 000 - $9, 999 26% $10, 000 -$99, 999 12% $100, 000 $999, 999 4% >= $1, 000

Counter-Espionage Techniques u Hiring • Background Checks u u u u Identity checks Education and credential checks Previous employment verification Reference checks Worker’s compensation history Motor vehicle records Drug history Medical history Credit history Civil court history Criminal court history Nondisclosure or non-compete agreements Monitoring Agreements

Counter-Espionage Techniques u u Firing / Exit procedures Secure meeting rooms or areas where sensitive discussion or material may be present • Locking offices, file cabinets, safes u u Proper destruction of sensitive material Classification of sensitive material • Confidential, Secret, Top Secret u Security Clearances • allow government employees to have access to classified information

Counter-Espionage Techniques u Factors Affecting Approval/Disproval of Security Clearances: • • • • Allegiance to the United States Foreign Influence Foreign Preference Sexual Behavior Emotional, Mental, and Personality Disorders Personal conduct Financial considerations Alcohol consumption Drug involvement Criminal conduct Security violations Outside activities Misuse of information technology systems

Counter-Espionage Techniques Separation of Duties u Two man control u Job rotation u Least Privilege (need-to-know) u Training & Awareness u

References u u u u u Donnelly, Jim. Security specialists say it pays to be paranoid. Ottawa Business Journal, 15 February 2006. http: //www. infowarmonitor. net/modules. php? op=modload&name=News&file=article&sid=1320 > Fitzpatrick, William M. , Di. Lullo, Samuel A. , Burke, Donald R. Corporate Espionage, Corporate Security and the Protection of Trade Secrets: a Legal Perspective. Global Competitiveness: Annual, 2002 issue. <http: //www. allbusiness. com/periodicals/article. asp? ID=332550&Page=1& > Heuer, Jr. , Richards J. The Insider Espionage Threat. Defense Personnel Security Research Center. <http: //rfweb. tamu. edu/security/secguide/Treason/Insider. htm#1> Heuer, Richards J. , Herbig, Katherine. Espionage by the Numbers: A Statistical Overview. <http: //www. intelligencesearch. com/ia 097. html> Information Security. <http: //www. ffiec. gov/ffiecinfobase/booklets/information_security/04 f_personne_sec urity. htm> Powers, Rod. Security Clearance Guidelines <http: //usmilitary. about. com/od/theorderlyroom/l/blsecmenu. htm > Powers, Rod. Security Clearance Secrets: Part 1, The Basics. <http: //usmilitary. about. com/cs/generalinfo/a/security. htm > Whitman, Michael E. Mattord, Herbert J. Management of Information Security. Thomson Learning, Inc, 2004. Wikipedia, The Free Encyclopedia. Espionage, <http: //en. wikipedia. org/wiki/Espionage>

Questions?
 Insider threat awareness training
Insider threat awareness training Potential insider threat indicators cyber awareness
Potential insider threat indicators cyber awareness Preconditions for an insider threat
Preconditions for an insider threat Insider threat automation
Insider threat automation Insider threat awareness training powerpoint
Insider threat awareness training powerpoint Espionage indicators
Espionage indicators Potential espionage indicators
Potential espionage indicators The espionage act of 1917
The espionage act of 1917 Pengertian cyber espionage
Pengertian cyber espionage Insider and outsider system of corporate governance
Insider and outsider system of corporate governance Insider trading and market abuse
Insider trading and market abuse Rspca pressure group
Rspca pressure group Insider trading adalah
Insider trading adalah Avoiding insider trading training
Avoiding insider trading training Insiderscore llc
Insiderscore llc Accidental insider trading
Accidental insider trading Alan linning
Alan linning Yg insider trading
Yg insider trading