Error control Network architecture Protocols Transmission Efficiency and



- Slides: 27

☻Error control☻ ☻ Network architecture ☻ ☻ Protocols ☻ ☻ Transmission Efficiency and Throughput ☻ SYST 5030/4030

Causes of errors • Errors are caused by: – various kinds of surrounding noise which disturbs the signal going through a medium like copper, coaxial cable, etc. – properties of the medium • attenuation distortion (high frequencies lose power more rapidly than low frequencies) • delay distortion (different frequencies travel through the medium at different speeds) SYST 5030/4030

Error Prevention • Shielding • Relocating cables • Conditioning (carriers guarantee the maximum number of errors that can occur) – C-type conditioning compensates for attenuation and delay distortions. – D-type conditioning improves signal to noise ratio. SYST 5030/4030

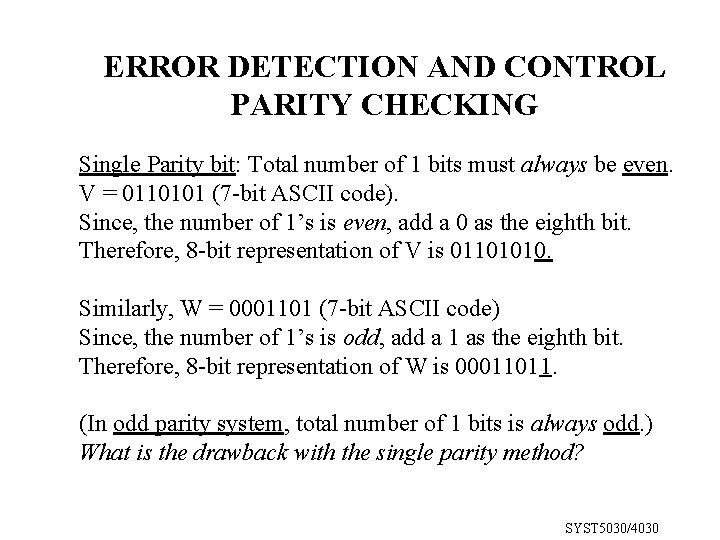
ERROR DETECTION AND CONTROL PARITY CHECKING Single Parity bit: Total number of 1 bits must always be even. V = 0110101 (7 -bit ASCII code). Since, the number of 1’s is even, add a 0 as the eighth bit. Therefore, 8 -bit representation of V is 01101010. Similarly, W = 0001101 (7 -bit ASCII code) Since, the number of 1’s is odd, add a 1 as the eighth bit. Therefore, 8 -bit representation of W is 00011011. (In odd parity system, total number of 1 bits is always odd. ) What is the drawback with the single parity method? SYST 5030/4030

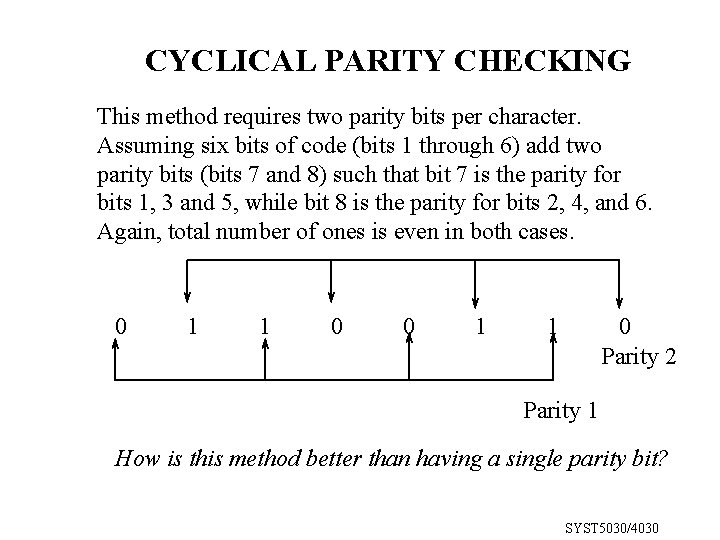
CYCLICAL PARITY CHECKING This method requires two parity bits per character. Assuming six bits of code (bits 1 through 6) add two parity bits (bits 7 and 8) such that bit 7 is the parity for bits 1, 3 and 5, while bit 8 is the parity for bits 2, 4, and 6. Again, total number of ones is even in both cases. 0 1 1 0 Parity 2 Parity 1 How is this method better than having a single parity bit? SYST 5030/4030

M-of-N Codes The code is designed in such a way that there will always be M 1’s and N-M 0’s in each valid character of the code. Example 4 -of-8 Code (from IBM) In this 8 -bit code there must be exactly 4 ones and 4 zeros. Valid characters: Invalid characters: 00001111 00000111 01011010 11100000 00011110 SYST 5030/4030

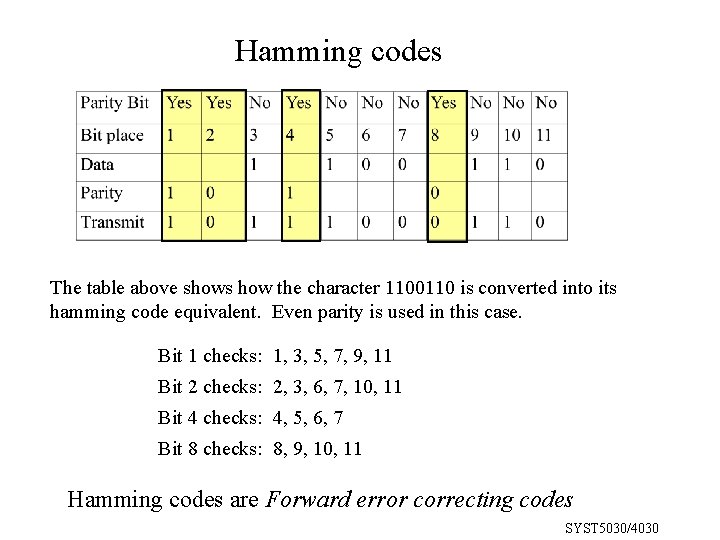
Hamming codes The table above shows how the character 1100110 is converted into its hamming code equivalent. Even parity is used in this case. Bit 1 checks: 1, 3, 5, 7, 9, 11 Bit 2 checks: 2, 3, 6, 7, 10, 11 Bit 4 checks: 4, 5, 6, 7 Bit 8 checks: 8, 9, 10, 11 Hamming codes are Forward error correcting codes SYST 5030/4030

Cyclical Redundancy Check (CRC) • This is applied to an entire block of data in synchronous communication. • A 16 -bit (or more commonly 32 -bit) number is calculated from the entire block, and attached to the end of the block by the sender. • The receiver performs a similar calculation and compares the 16 -bit value to see if it is the same. If they are not the same, it indicates an error in the transmission. • This is a highly reliable scheme with almost 100% error detection capability. SYST 5030/4030

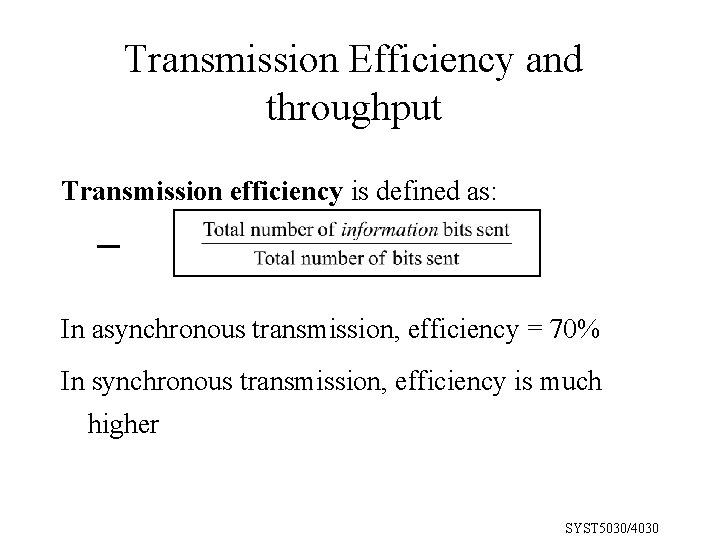
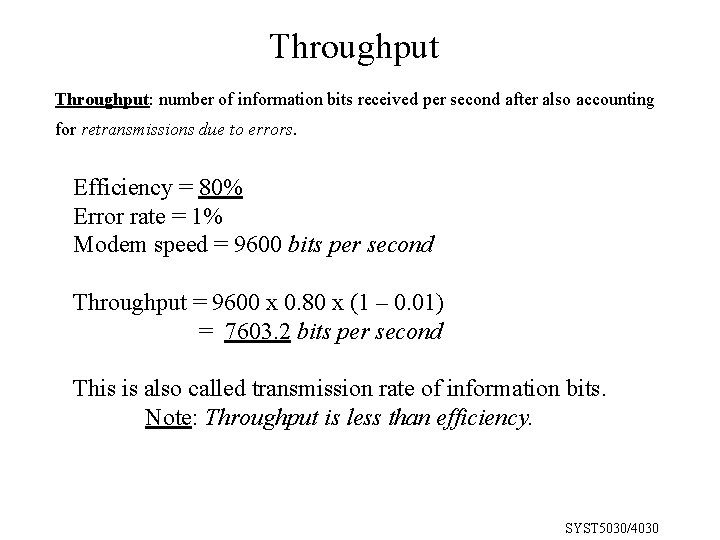
Transmission Efficiency and throughput Transmission efficiency is defined as: In asynchronous transmission, efficiency = 70% In synchronous transmission, efficiency is much higher SYST 5030/4030

Throughput: number of information bits received per second after also accounting for retransmissions due to errors. Efficiency = 80% Error rate = 1% Modem speed = 9600 bits per second Throughput = 9600 x 0. 80 x (1 – 0. 01) = 7603. 2 bits per second This is also called transmission rate of information bits. Note: Throughput is less than efficiency. SYST 5030/4030

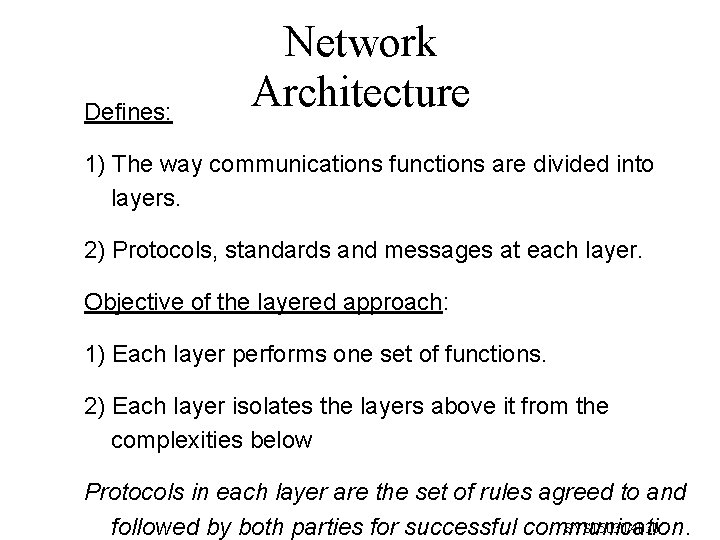
Defines: Network Architecture 1) The way communications functions are divided into layers. 2) Protocols, standards and messages at each layer. Objective of the layered approach: 1) Each layer performs one set of functions. 2) Each layer isolates the layers above it from the complexities below Protocols in each layer are the set of rules agreed to and SYST 5030/4030 followed by both parties for successful communication.

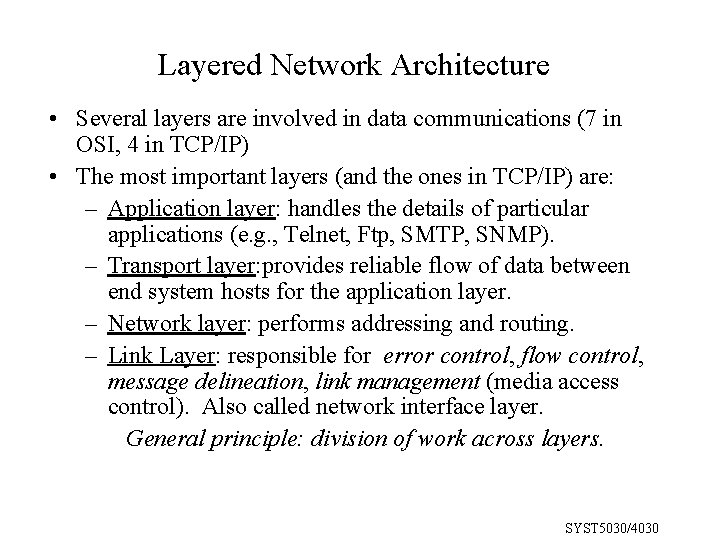
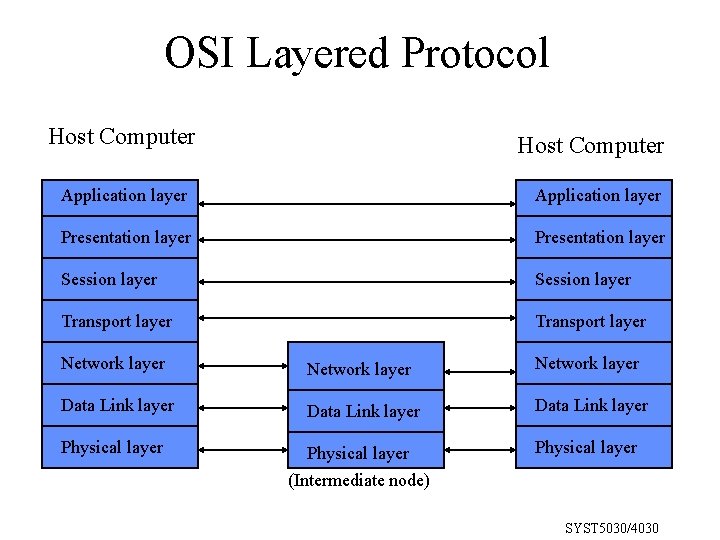
Layered Network Architecture • Several layers are involved in data communications (7 in OSI, 4 in TCP/IP) • The most important layers (and the ones in TCP/IP) are: – Application layer: handles the details of particular applications (e. g. , Telnet, Ftp, SMTP, SNMP). – Transport layer: provides reliable flow of data between end system hosts for the application layer. – Network layer: performs addressing and routing. – Link Layer: responsible for error control, flow control, message delineation, link management (media access control). Also called network interface layer. General principle: division of work across layers. SYST 5030/4030

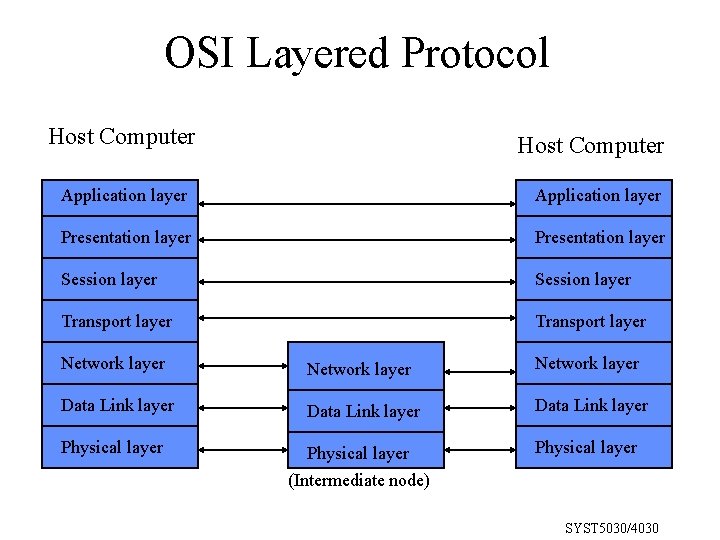
OSI Layered Protocol Host Computer Application layer Presentation layer Session layer Transport layer Network layer Network layer Data Link layer Data Link layer Physical layer (Intermediate node) Physical layer SYST 5030/4030

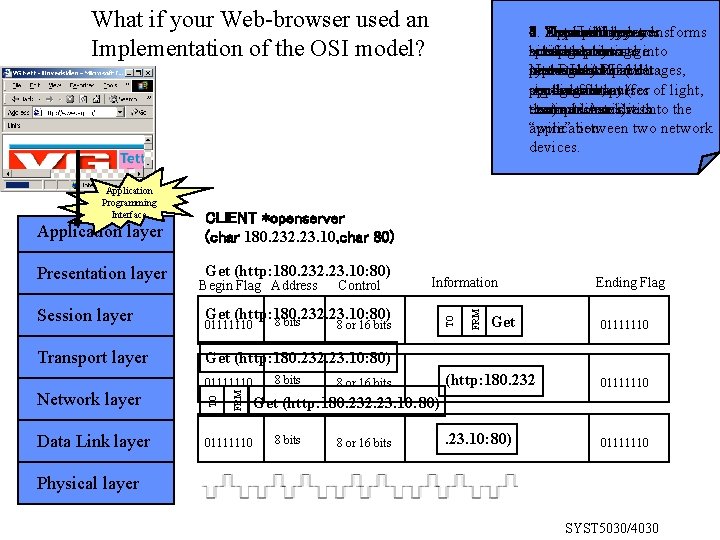
What if your Web-browser used an Implementation of the OSI model? Presentation layer Get (http: 180. 232. 23. 10: 80) Network layer Data Link layer Information 8 or 16 bits Get Ending Flag 01111110 Get (http: 180. 232. 23. 10: 80) 01111110 FRM Transport layer Control Get (http: 180. 232. 23. 10: 80) 8 bits 01111110 TO Session layer Begin Flag Address FRM Application layer CLIENT *openserver (char 180. 232. 23. 10, char 80) TO Application Programming Interface 3. 5. Session Network layer 7. 1. 2. Application Presentation layer sends layer transforms 4. Physical Transport layer 6. Data Link layer notifies encapsulates endbits encodes message into message physical down splits data into to into breaks up message system message with of a data representation commonly Network API used and (voltages, packets and into DLhost size packets pending sender and datalayer sign-waves, storage application format pulses (for of light, controls flow transmission. destination address etc. ) example communicates and Ascii) sends with it onto the “wire” application between two network devices. 01111110 8 bits 8 or 16 bits (http: 180. 232 01111110 . 23. 10: 80) 01111110 Get (http: 180. 232. 23. 10: 80) 8 bits 8 or 16 bits Physical layer SYST 5030/4030

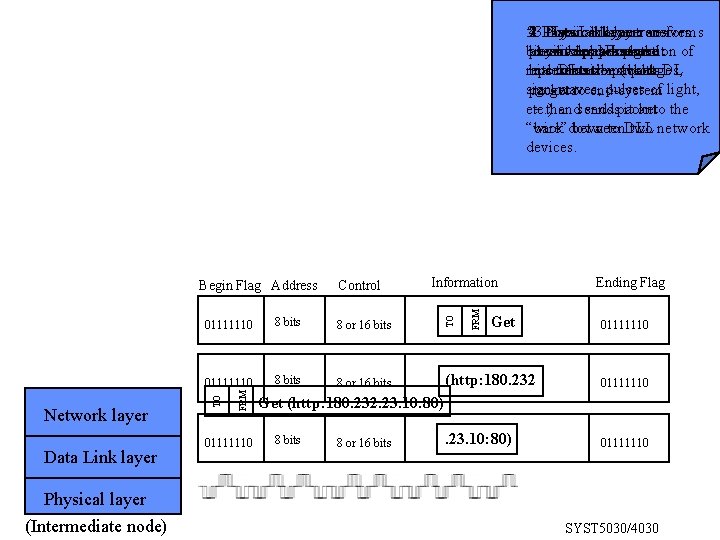
5. layer transforms Network layer 1. Physical layer receives 4. Data Link layer 2. 3 Physical rebits intoup physical receives packet and of physical representation breaks message assembles NL packet representation (voltages, calculates best port DL bits turns them back into DL size packets sign-waves, pulses of light, to get to end-system packets etc. ) andsendspacket it onto the – then “wire” between two network back down to DLL devices. Data Link layer Physical layer (Intermediate node) FRM Information Get Ending Flag 8 bits 8 or 16 bits 01111110 8 bits 8 or 16 bits (http: 180. 232 01111110 . 23. 10: 80) 01111110 FRM 01111110 TO Network layer Control TO Begin Flag Address 01111110 Get (http: 180. 232. 23. 10: 80) 8 bits 8 or 16 bits SYST 5030/4030

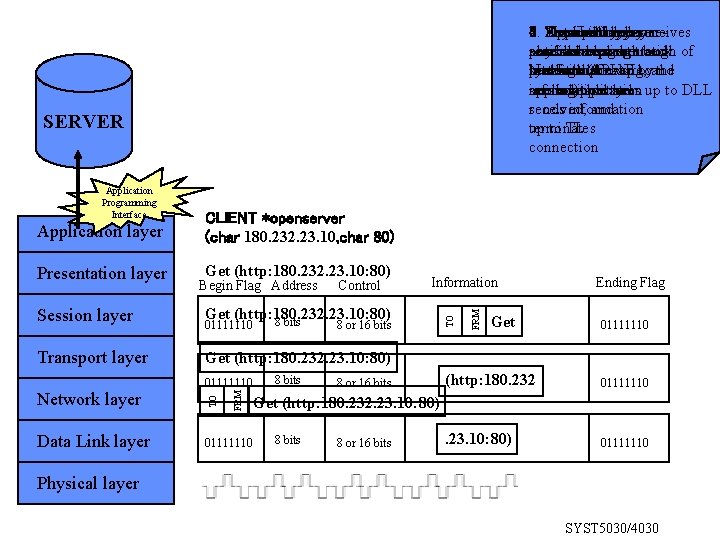
7. 2. Presentation layer receives 3. Physical 5. Session Network layer 4. 1. Transport Application layer 6. Data Link layer rephysical encodes message representation back notifies removes sending re-assembles sends message through assembles packet and of bits into from format the used wire, system packet/addressing message Network (if API up by toand the sends itthat up to NL sends application message information haslayer and been up to DLL needed) serverbit-patterns application received, sends information and terminates up to TL connection SERVER Presentation layer Get (http: 180. 232. 23. 10: 80) Network layer Data Link layer Information 8 or 16 bits Get Ending Flag 01111110 Get (http: 180. 232. 23. 10: 80) 01111110 FRM Transport layer Control Get (http: 180. 232. 23. 10: 80) 8 bits 01111110 TO Session layer Begin Flag Address FRM Application layer CLIENT *openserver (char 180. 232. 23. 10, char 80) TO Application Programming Interface 01111110 8 bits 8 or 16 bits (http: 180. 232 01111110 . 23. 10: 80) 01111110 Get (http: 180. 232. 23. 10: 80) 8 bits 8 or 16 bits Physical layer SYST 5030/4030

OSI Layered Protocol Host Computer Application layer Presentation layer Session layer Transport layer Network layer Network layer Data Link layer Data Link layer Physical layer (Intermediate node) Physical layer SYST 5030/4030

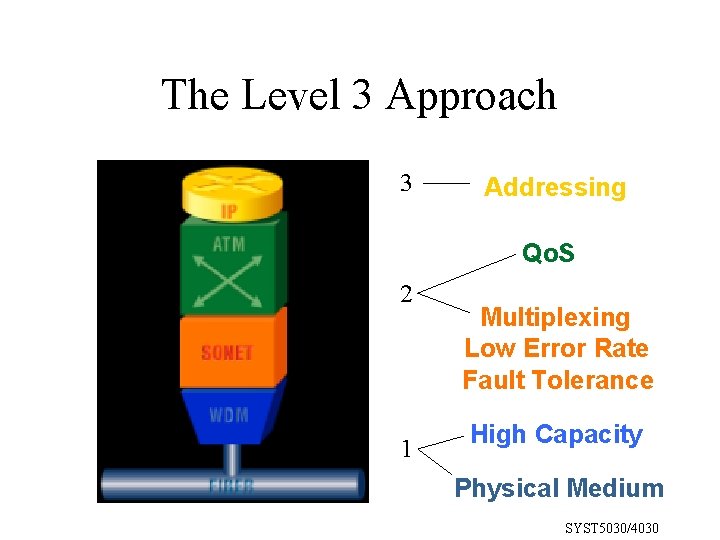
The Level 3 Approach Network Layer Primary Attribute 3 Addressing Qo. S 2 1 Multiplexing Low Error Rate Fault Tolerance High Capacity Physical Medium SYST 5030/4030

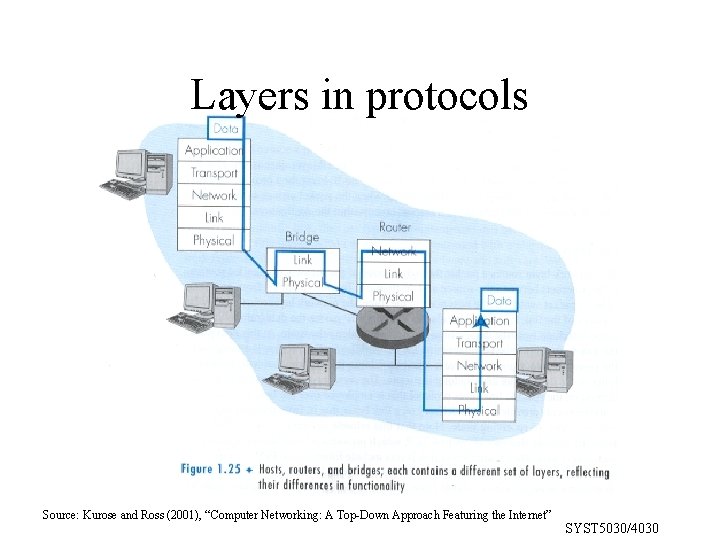
Layers in protocols Source: Kurose and Ross (2001), “Computer Networking: A Top-Down Approach Featuring the Internet” SYST 5030/4030

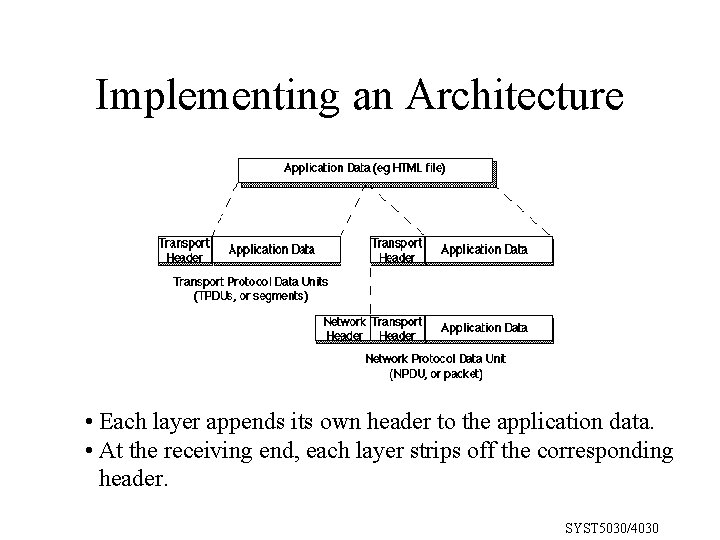
Implementing an Architecture • Each layer appends its own header to the application data. • At the receiving end, each layer strips off the corresponding header. SYST 5030/4030

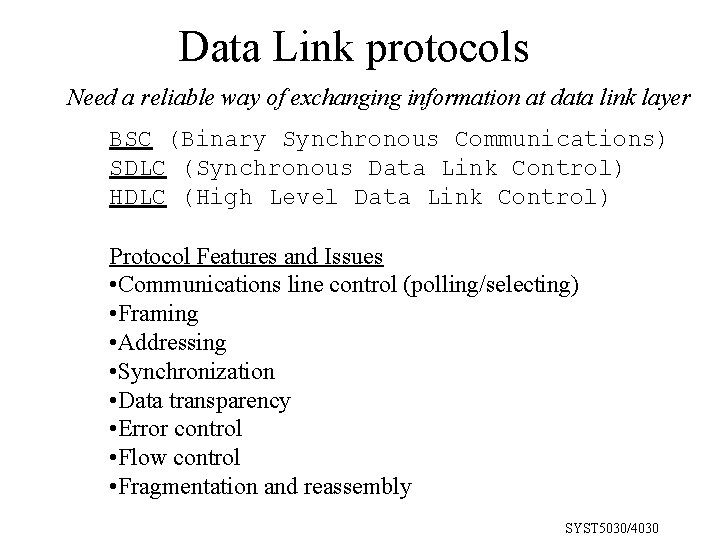
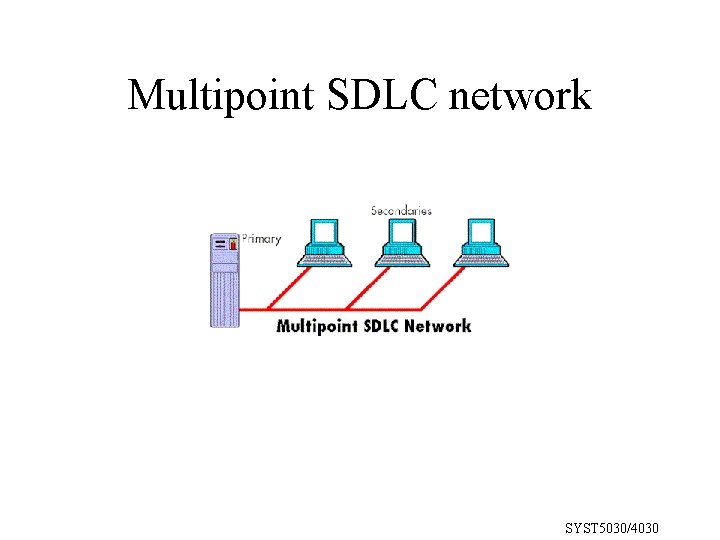
Data Link protocols Need a reliable way of exchanging information at data link layer BSC (Binary Synchronous Communications) SDLC (Synchronous Data Link Control) HDLC (High Level Data Link Control) Protocol Features and Issues • Communications line control (polling/selecting) • Framing • Addressing • Synchronization • Data transparency • Error control • Flow control • Fragmentation and reassembly SYST 5030/4030

Multipoint SDLC network SYST 5030/4030

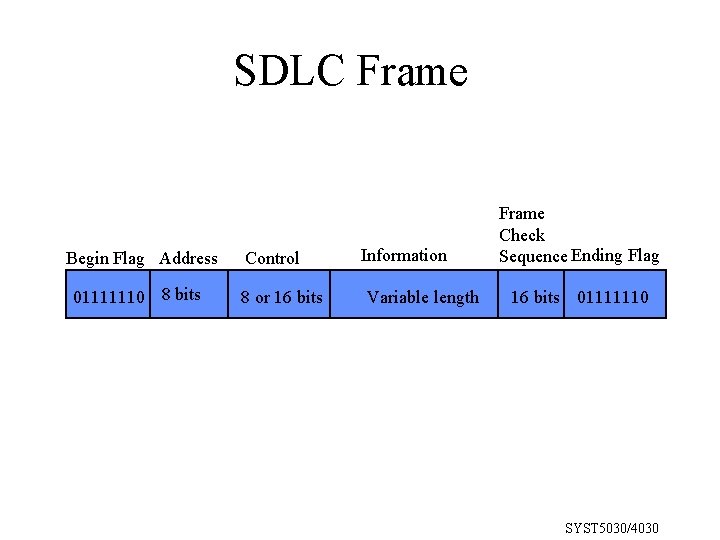
SDLC Frame Begin Flag Address 01111110 8 bits Control 8 or 16 bits Information Variable length Frame Check Sequence Ending Flag 16 bits 01111110 SYST 5030/4030

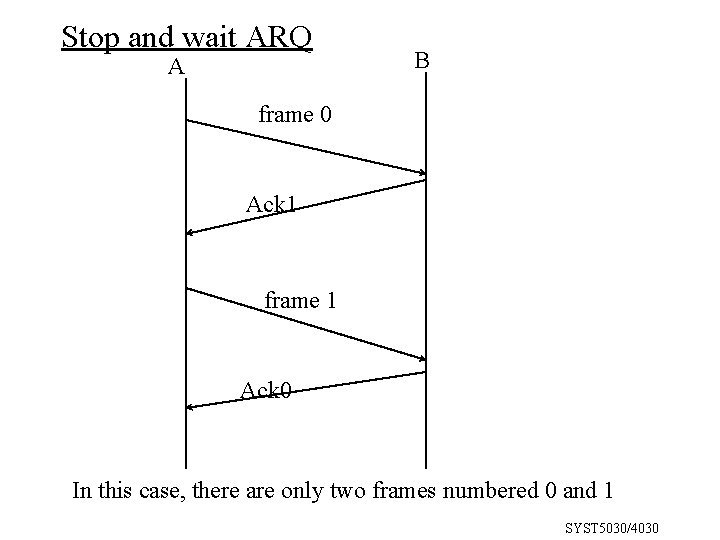
How Data Link Protocol Works (Automatic Repeat Request - ARQ - method) • Stop and wait ARQ: – Sender stops and waits for response from receiver after each packet – Receiver sends ACK if no errors in message – Receiver sends NACK if errors in message. This is a half-duplex method used in BSC protocol. SYST 5030/4030

Stop and wait ARQ A B frame 0 Ack 1 frame 1 Ack 0 In this case, there are only two frames numbered 0 and 1 SYST 5030/4030

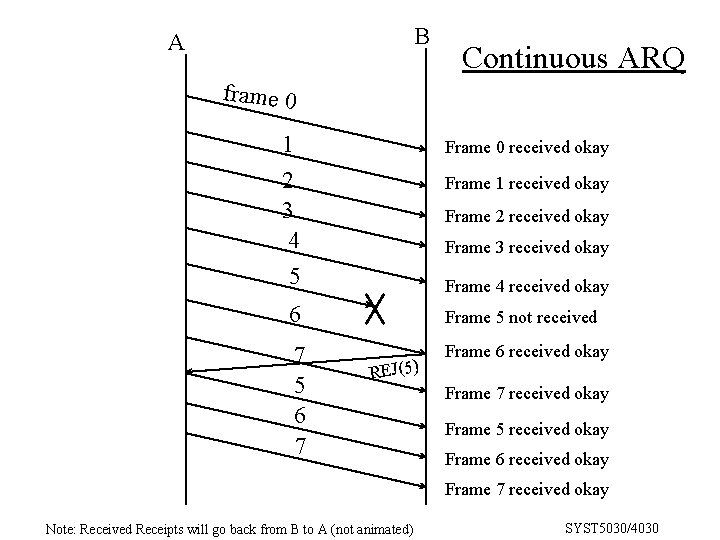
Protocol for error correction (Automatic Repeat Request) • Continuous ARQ: – sender does not wait for response from receiver after each packet – receiver asks for retransmission of erroneous packets. This is a full-duplex method. It is also called sliding window protocol. It is used in SDLC protocol. SYST 5030/4030

B A Continuous ARQ frame 0 1 2 3 4 Frame 0 received okay Frame 1 received okay Frame 2 received okay Frame 3 received okay 5 Frame 4 received okay 6 Frame 5 not received 7 5 6 7 Frame 6 received okay REJ(5) Frame 7 received okay Frame 5 received okay Frame 6 received okay Frame 7 received okay Note: Received Receipts will go back from B to A (not animated) SYST 5030/4030