Enterprise Wireless LAN WLAN Management and Services Jitu








- Slides: 19

Enterprise Wireless LAN (WLAN) Management and Services Jitu Padhye (Joint work with Ranveer Chandra, Alec Wolman, Brian Zill & Victor Bahl)

Wireless Network Woes • Corporations spend lots of $$ on WLAN infrastructure – Worldwide enterprise WLAN business expected to grow from $1. 1 billion this year to $3. 5 billion in 2009 • Wireless networks perceived to be “flaky”, less secure – Microsoft’s IT Dept. logs several hundred complaints / month – Users complain about: w Lack of coverage, performance, reliability w Authentication problems (802. 1 x protocol issues) – Network administrators worry about w Providing adequate coverage, performance w Security and unauthorized access – Def. Con 2005 : Wi. Fi Pistol, Wi. Fi Sniper Rifle, Wi. Fi Bouncing, Air. Snarf box Better WLAN management system needed!

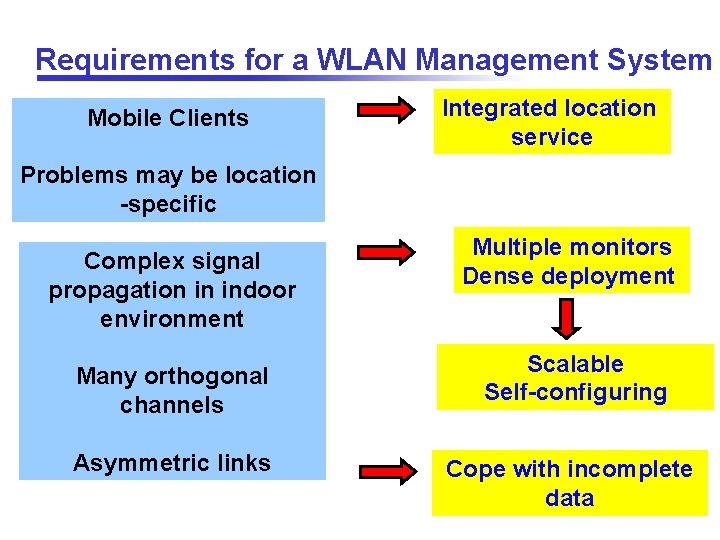
Requirements for a WLAN Management System Mobile Clients Integrated location service Problems may be location -specific Complex signal propagation in indoor environment Many orthogonal channels Asymmetric links Multiple monitors Dense deployment Scalable Self-configuring Cope with incomplete data

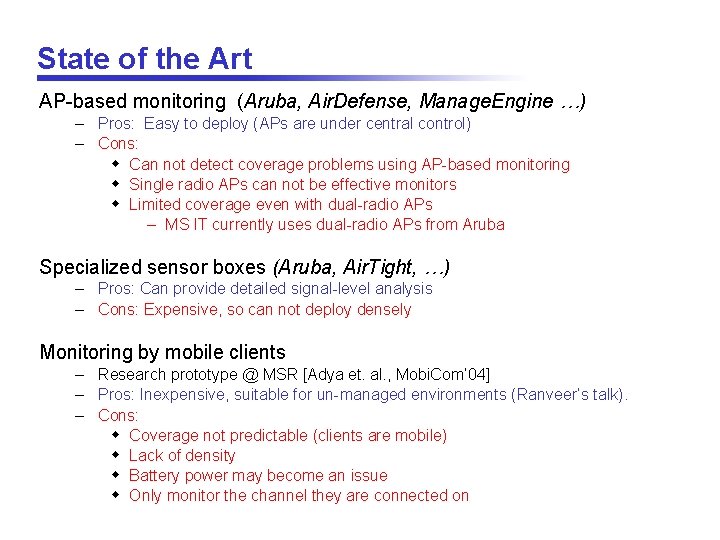
State of the Art AP-based monitoring (Aruba, Air. Defense, Manage. Engine …) – Pros: Easy to deploy (APs are under central control) – Cons: w Can not detect coverage problems using AP-based monitoring w Single radio APs can not be effective monitors w Limited coverage even with dual-radio APs – MS IT currently uses dual-radio APs from Aruba Specialized sensor boxes (Aruba, Air. Tight, …) – Pros: Can provide detailed signal-level analysis – Cons: Expensive, so can not deploy densely Monitoring by mobile clients – Research prototype @ MSR [Adya et. al. , Mobi. Com’ 04] – Pros: Inexpensive, suitable for un-managed environments (Ranveer’s talk). – Cons: w Coverage not predictable (clients are mobile) w Lack of density w Battery power may become an issue w Only monitor the channel they are connected on

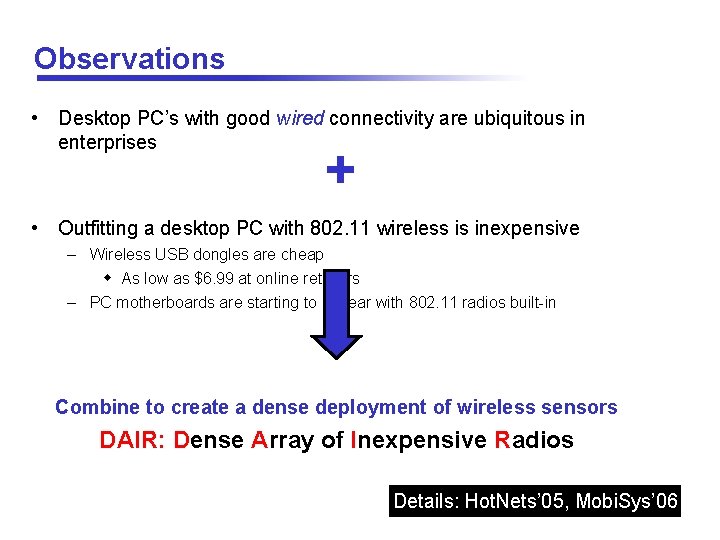
Observations • Desktop PC’s with good wired connectivity are ubiquitous in enterprises + • Outfitting a desktop PC with 802. 11 wireless is inexpensive – Wireless USB dongles are cheap w As low as $6. 99 at online retailers – PC motherboards are starting to appear with 802. 11 radios built-in Combine to create a dense deployment of wireless sensors DAIR: Dense Array of Inexpensive Radios Details: Hot. Nets’ 05, Mobi. Sys’ 06

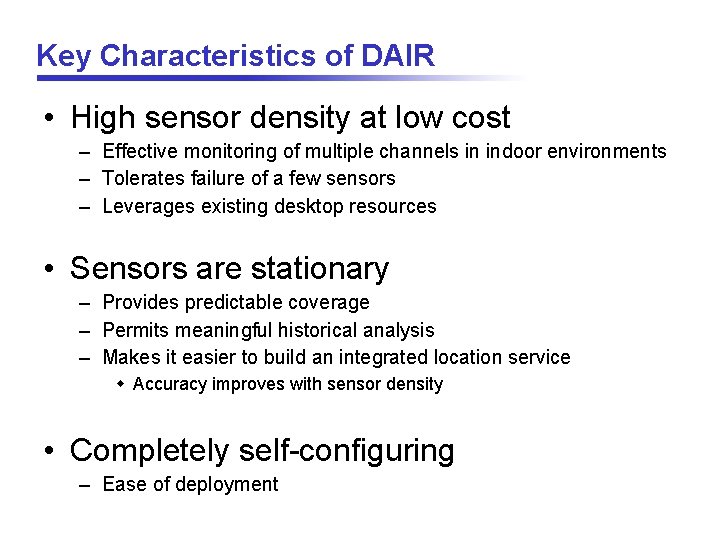
Key Characteristics of DAIR • High sensor density at low cost – Effective monitoring of multiple channels in indoor environments – Tolerates failure of a few sensors – Leverages existing desktop resources • Sensors are stationary – Provides predictable coverage – Permits meaningful historical analysis – Makes it easier to build an integrated location service w Accuracy improves with sensor density • Completely self-configuring – Ease of deployment

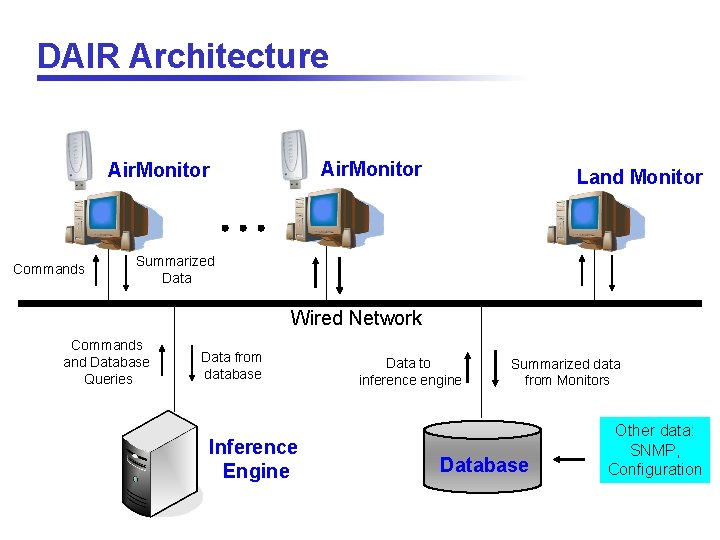
DAIR Architecture Air. Monitor Commands Land Monitor Summarized Data Wired Network Commands and Database Queries Data from database Inference Engine Data to inference engine Summarized data from Monitors Database Other data: SNMP, Configuration

Monitor Architecture

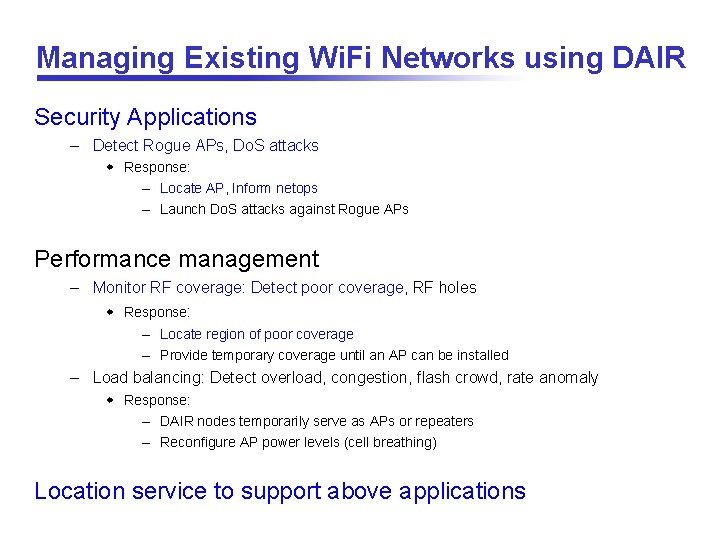
Managing Existing Wi. Fi Networks using DAIR Security Applications – Detect Rogue APs, Do. S attacks w Response: – Locate AP, Inform netops – Launch Do. S attacks against Rogue APs Performance management – Monitor RF coverage: Detect poor coverage, RF holes w Response: – Locate region of poor coverage – Provide temporary coverage until an AP can be installed – Load balancing: Detect overload, congestion, flash crowd, rate anomaly w Response: – DAIR nodes temporarily serve as APs or repeaters – Reconfigure AP power levels (cell breathing) Location service to support above applications

Overview of location service • Distinguishing features: – – – Self-configuring Can locate un-cooperative transmitters (e. g. unauthorized APs) Office-level accuracy • How it works: 1. 2. 3. Air. Monitors locate themselves Air. Monitors regularly profile the environment to determine radio propagation characteristics Inference engine uses profiles and observations from multiple Air. Monitors to locate clients, sources of interference (Do. S attack? ), determine regions of poor performance

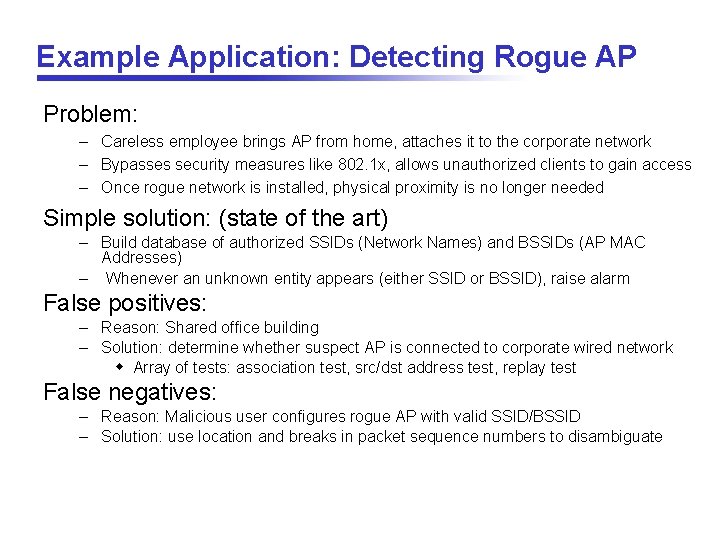
Example Application: Detecting Rogue AP Problem: – Careless employee brings AP from home, attaches it to the corporate network – Bypasses security measures like 802. 1 x, allows unauthorized clients to gain access – Once rogue network is installed, physical proximity is no longer needed Simple solution: (state of the art) – Build database of authorized SSIDs (Network Names) and BSSIDs (AP MAC Addresses) – Whenever an unknown entity appears (either SSID or BSSID), raise alarm False positives: – Reason: Shared office building – Solution: determine whether suspect AP is connected to corporate wired network w Array of tests: association test, src/dst address test, replay test False negatives: – Reason: Malicious user configures rogue AP with valid SSID/BSSID – Solution: use location and breaks in packet sequence numbers to disambiguate

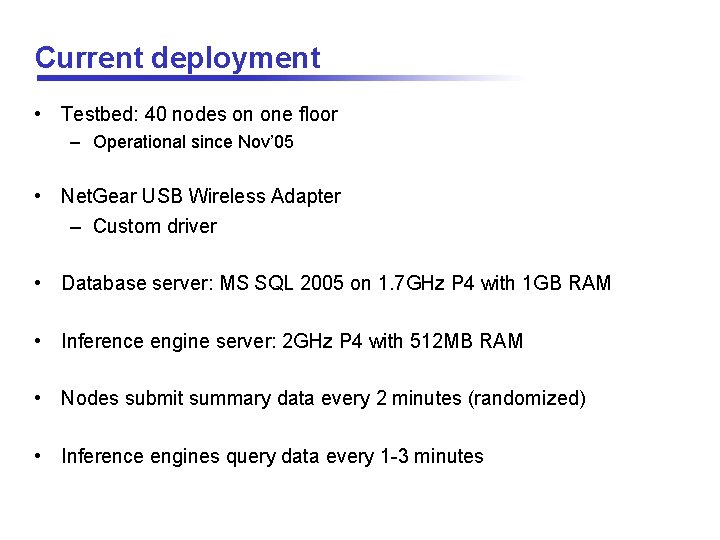
Current deployment • Testbed: 40 nodes on one floor – Operational since Nov’ 05 • Net. Gear USB Wireless Adapter – Custom driver • Database server: MS SQL 2005 on 1. 7 GHz P 4 with 1 GB RAM • Inference engine server: 2 GHz P 4 with 512 MB RAM • Nodes submit summary data every 2 minutes (randomized) • Inference engines query data every 1 -3 minutes

System Scalability • Load on database server < 75% • Additional load on desktops < 2 -3% • Wired network traffic per node < 5 Kbps One database server per building should be sufficient.


Backup slides

Demo …. . 1. Rogue AP detection and location 2. Do. S attack (Disassociation attack) detection and location 3. Location-aware client performance monitoring See 2 & 3 during break after the talk

How do Air. Monitors locate themselves? • Monitor machine activity to determine primary user • Look up Active. Directory to determine office number • Parse office map to determine coordinates of the office • Verify and adjust coordinates by observing which Air. Monitors are nearby

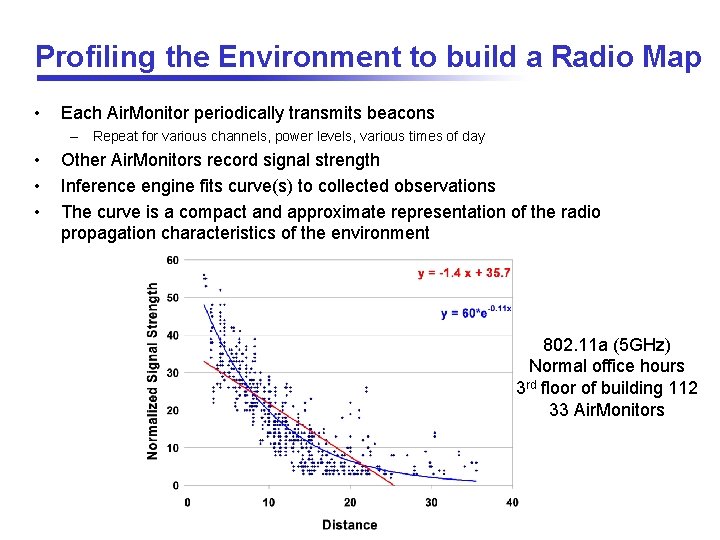
Profiling the Environment to build a Radio Map • Each Air. Monitor periodically transmits beacons – Repeat for various channels, power levels, various times of day • • • Other Air. Monitors record signal strength Inference engine fits curve(s) to collected observations The curve is a compact and approximate representation of the radio propagation characteristics of the environment 802. 11 a (5 GHz) Normal office hours 3 rd floor of building 112 33 Air. Monitors

Determining location of clients (any “transmitter”) • Air. Monitors capture packets from the client, report observed signal strength of database • Inference engine: 1. 2. Selects appropriate profile (frequency, time of day) Locates client using the observations from Air. Monitors and the profile – Spring-and-ball algorithm for fast convergence