Enterprise Risk Management Miami FL September 2010 Information

Enterprise Risk Management Miami, FL September 2010 Information Security. Facing the Risks in Electronic Channels and Social Media © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL September 2010 Agenda n Implementing a Comprehensive Security Program n Conducting Security Risk Assessments – Best Practices n Security Attack Trends and Prevention Strategies n Emerging Technologies and Social Media – Security Threats and Countermeasures © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Implementing a Comprehensive Security Program © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL September 2010 Information Security Program n It is an initiative which serves to ensure that information assets are properly protected. © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL September 2010 Reasons for a Security Program n Minimize costly risks n Provide a structure manner to address information security n n Align information security initiatives with business strategies, goals and objectives – IT Governance Comply with laws, regulations and industry standards © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL September 2010 Information Security Program Every organization’s information security program should be guided by the following: n n n Plans for achieving information security goals and objectives Clear and comprehensive mission, goals, and objectives Performance measures to continuously monitor the efficiency and effectiveness of identified goals and objectives © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL Information Security Program An information security program should cover: n Security function n Security risk assessment n Security plans n Security policies n Security standards n Security procedures © 2010 Enterprise Risk Management September 2010

Enterprise Risk Management Miami, FL September 2010 Information Security Program An information security program should cover: n Information assets ownership n Classification of information assets n Information security laws, regulations and industry standards n Logical security n Physical security n Disaster recovery and contingency planning © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL Information Security Program An information security program should cover: n Auditing and monitoring n Security incident response n Security awareness and training n Human Resources n Legal n Help Desk user support © 2010 Enterprise Risk Management September 2010
Enterprise Risk Management Miami, FL Information Security Program An information security program should cover: n System life cycle management n External service providers n Security reviews © 2010 Enterprise Risk Management September 2010

Enterprise Risk Management Miami, FL Security Program Life Cycle ISO 27001: 2005 © 2010 Enterprise Risk Management September 2010

Enterprise Risk Management Miami, FL September 2010 Security Program Life Cycle Organizations should follow a life cycle approach in developing, implementing and maintaining their information security program. n Establish ISMS n Implement and Operate ISMS n Monitor and Review ISMS n Maintain and Improve ISMS This approach ensures that security is an on-going and continually improving process. © 2010 Enterprise Risk Management
Enterprise Risk Management Who Directs This Initiative? n Board of Directors n Top Management n Information Security Committee © 2010 Enterprise Risk Management Miami, FL September 2010

Enterprise Risk Management Miami, FL September 2010 How Does a Security Program Affects My Job? n n Information security is part of every employee’s responsibility. Security policies, standards and procedures affect everyone – for example: – Each time someone enters the building – Each time a password is used – Each time customer information is viewed or edited © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL Ongoing Monitoring n n An effective information security program requires constant review. Organizations should monitor the status of their programs to ensure that: – – – Ongoing information security activities are providing appropriate support to the organization's mission. Policies, standards and procedures are current and aligned with evolving technologies. Security controls are accomplishing their intended purpose. © 2010 Enterprise Risk Management September 2010
Enterprise Risk Management Miami, FL September 2010 Conducting Security Risk Assessments – Best Practices © 2010 Enterprise Risk Management
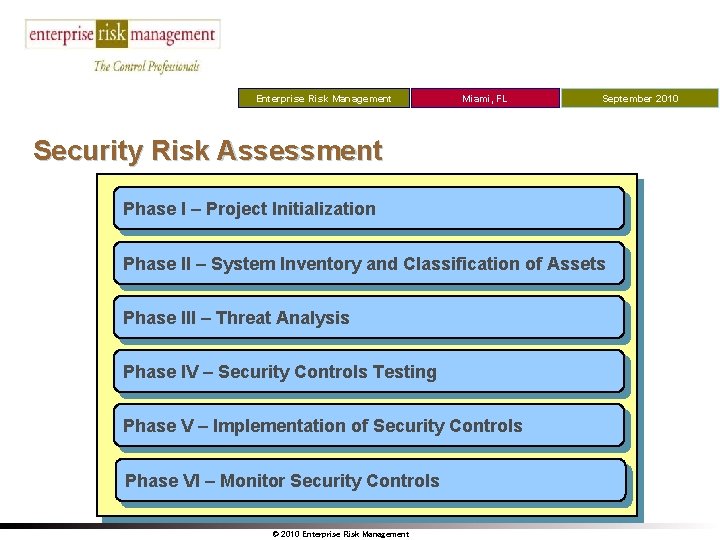
Enterprise Risk Management Miami, FL September 2010 Security Risk Assessment Phase I – Project Initialization Phase II – System Inventory and Classification of Assets Phase III – Threat Analysis Phase IV – Security Controls Testing Phase V – Implementation of Security Controls Phase VI – Monitor Security Controls © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Phase I – Project Initialization n Define the objective n Define the scope n Define the method required (e. g. , Qualitative, Quantitative) n Define the personnel required n Define the approach to gather the information n Define the deliverables per each phase © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Phase II – System Inventory and Classification of Assets n n Document the organization information assets – Consider all departments and business processes – Consider information assets in physical and logical format Classify the information assets: – – – Critical – the organization cannot operate without this information asset. Essential – the organization needs the information asset at some point in time. Normal – the organization can operate without this information asset for an extended period of time. © 2010 Enterprise Risk Management
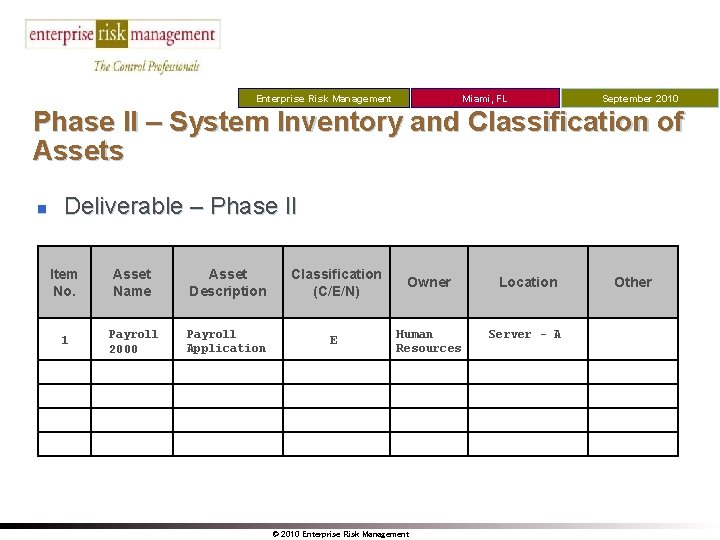
Miami, FL Enterprise Risk Management September 2010 Phase II – System Inventory and Classification of Assets n Deliverable – Phase II Item No. Asset Name Asset Description Classification (C/E/N) Owner Location 1 Payroll 2000 Payroll Application E Human Resources Server - A © 2010 Enterprise Risk Management Other

Enterprise Risk Management Miami, FL Phase III – Threat Analysis n Identify security threats n Identify security vulnerabilities n Identify existing security controls to reduce the risk n Determine the likelihood of occurrence n Determine the severity of impact n Determine the risk level © 2010 Enterprise Risk Management September 2010
Enterprise Risk Management Miami, FL September 2010 Phase III – Threat Analysis n Identify different types of security threats – A starting point would be to consider those threats that might actually impact an enterprise Unauthorized access n. Denial of Service n. Social Engineering n. Theft n. Hurricane n. Fire n. Pharming n. Phishing n. Virus/Worms n © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Phase III – Threat Analysis n Identify different types of security vulnerabilities – Identify vulnerabilities associated with each threat to produce a threat/vulnerability pair. Vulnerabilities may be associated with either a single or multiple threats There is not a disaster recovery plan n. Flammable materials store in the Data Centre n. Lack of fire extinguishers n. User-id and passwords by default n. Operating System without the last patch n. Data center’s door does not have lock n. TFTP service enabled in the Unix hosts n. Shared folder with Everyone full control n © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL September 2010 Phase III – Threat Analysis n Identify existing controls to reduce the risk – Identify existing controls that reduce: Ø The likelihood or probability of a threat exploiting an identified security vulnerability. Ø The magnitude of impact of the exploited vulnerability on the system. © 2010 Enterprise Risk Management
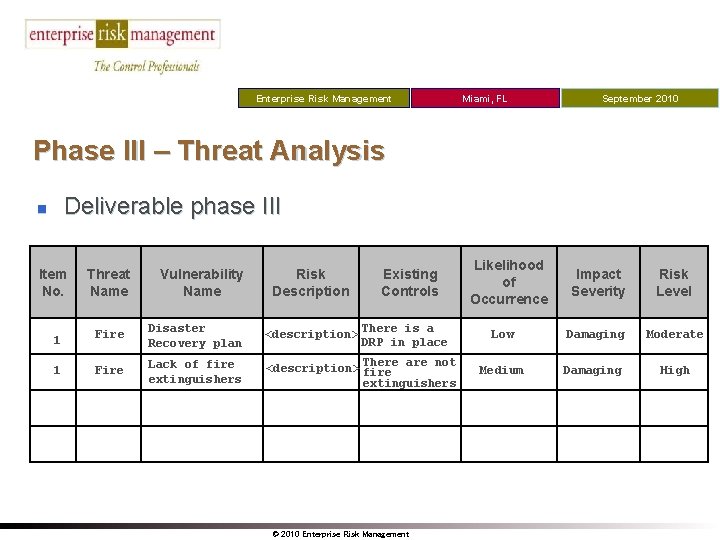
Enterprise Risk Management Miami, FL September 2010 Phase III – Threat Analysis Deliverable phase III n Item No. Threat Name Vulnerability Name Risk Description Existing Controls 1 Fire Disaster Recovery plan <description> There is a DRP in place 1 Fire Lack of fire extinguishers There are not <description> fire extinguishers © 2010 Enterprise Risk Management Likelihood of Occurrence Impact Severity Risk Level Low Damaging Moderate Medium Damaging High

Enterprise Risk Management Miami, FL September 2010 Phase IV – Security Control Testing n Tests the security controls / safeguards that are in place n Consider performing different types of security tests n Determine if the control exists and if the control works effectively and consistently n Determine the residual risk n Determine if additional security controls are required n Develop an action plan to remediate security issues noted © 2010 Enterprise Risk Management
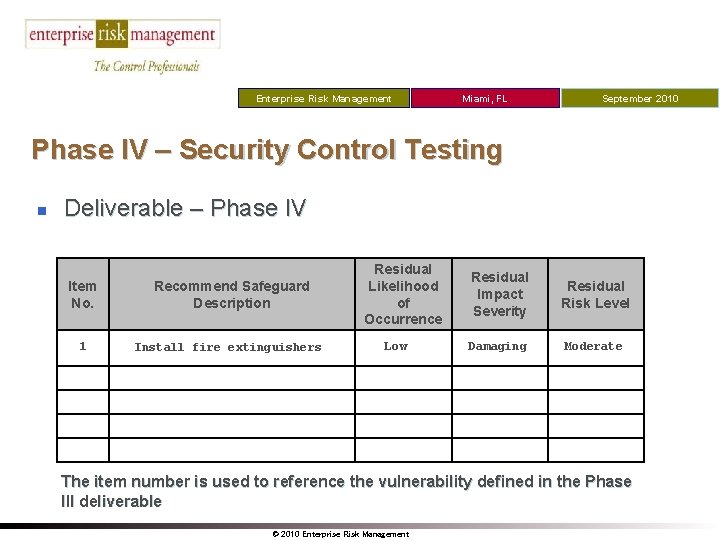
Enterprise Risk Management Miami, FL September 2010 Phase IV – Security Control Testing n Deliverable – Phase IV Item No. Recommend Safeguard Description 1 Install fire extinguishers Residual Likelihood of Occurrence Low Residual Impact Severity Residual Risk Level Damaging Moderate The item number is used to reference the vulnerability defined in the Phase III deliverable © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Phase V – Implementation of Security Controls n Prioritize implementation of security controls: Ø Based on risk Ø By business area Ø By technical area © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL September 2010 Phase VI – Monitoring Security Controls n Implement mechanisms to monitor security controls. This phase can include: Ø Review of system and application logs Ø Review of system and application exception reports Ø Different types of audits Ø Different types of security assessments Ø Department self assessments © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Security Attack Trends and Prevention Strategies © 2010 Enterprise Risk Management
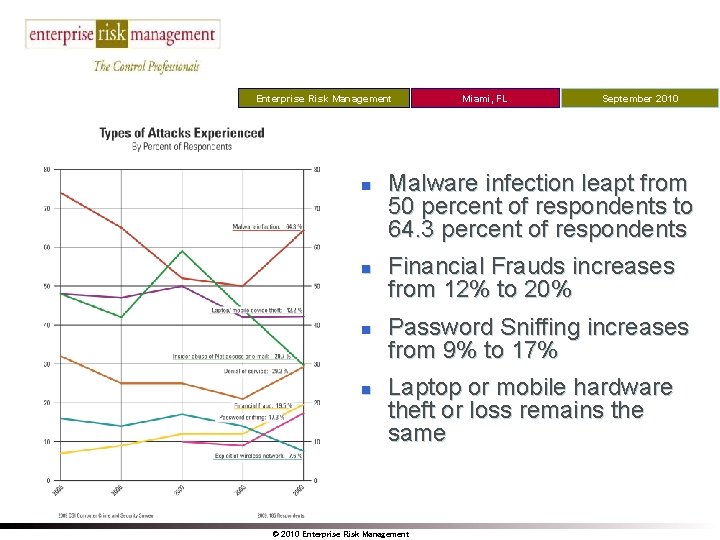
Enterprise Risk Management Miami, FL September 2010 Title n n Malware infection leapt from 50 percent of respondents to 64. 3 percent of respondents Financial Frauds increases from 12% to 20% Password Sniffing increases from 9% to 17% Laptop or mobile hardware theft or loss remains the same © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Countermeasures n n n Apply patches and updates Implement strong security policies, procedures, and standards Turn off and remove services that are not needed for normal company network operations Perform filtering on all network traffic to ensure that malicious activity and unauthorized communications are not taking place Provide additional security awareness training to end users Install additional security software (e. g. Data Leakage products) © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Countermeasures n Change or replace software or systems n Apply sound configurations to system and applications n Apply frequent updates to antivirus systems n Apply sound encryption mechanisms n Apply general logical and physical security measures © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Source of Information for Developing a Security Strategy n Information security and privacy laws (GLBA, FACT Act) n Industry standards (ISO 27001: 2005) n Sector specific information security standards (PCI) n Previous attacks on your organization / other organizations n General news reports of other attacks / incidents n Information shared in associations / reputable forums n Executive and management priorities n Contract with business partners © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Emerging Technologies and Social Media – Security Threats and Countermeasures © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL September 2010 Social Media and Networking n n n Social media technology involves the creation and dissemination of content through social networks using the Internet. Social media and networking is rapidly growing and becoming more popular than e-mail communication. Examples: Facebook, Myspace, Twitter and Linked. In © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL September 2010 Security Issues Relevant to Social Media: n Social Engineering: Exploits people n Spam and Malware Attacks: Exploits systems n n Disgruntled Employee: Reputational damage of the organization Legal Issues: Regulatory sanctions and fines assessed on the organization © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL Countermeasures n Policies and Procedures – Corporate privacy protection – Nondisclosure / posting of business-related content – Acceptable use in the workplace – Acceptable use outside of the workplace – Action plan for privacy breaches and escalation © 2010 Enterprise Risk Management September 2010
Enterprise Risk Management Miami, FL September 2010 Countermeasures n n n Training and Awareness – Communicate policies to employees – Inform employees of risks involved with social media sites – Social engineering trends and techniques Technical Safeguards – Up-to-date antivirus and antimalware controls – Content filtering programs to restrict/limit access Audits and Assessments © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL September 2010 Emerging Technologies that can Help n Emerging security technologies – Biometrics – Self-encrypting hard drives – – USB tokens for authentication Mobile Device Security • Authentication, antivirus, firewalls, anti-spam and encryption for mobile devices © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Technologies that Require New Security Measures n n n Cloud Computing – Share infrastructure – Becomes difficult to control and protect Smart Phones – Becoming the standard phones – Another version of a regular computer I-spoof and other Applications – Spoof your telephone number and trick individuals who rely on it © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Countering New Challenges n n n Establish and enforce strong authentication policies for devices trying to access corporate networks Require employees to use a corporate VPN and encryption when handling sensitive data Devices and software applications are configured as per configuration standards © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Countering New Challenges n n Corporate security policies prevent workers from transferring sensitive data to mobile devices or unauthorized computers For laptops/netbooks consider air cards, which require a service plan, instead of hot spots for wireless connections © 2010 Enterprise Risk Management

Enterprise Risk Management Miami, FL September 2010 Countering New Challenges n Establish ground rules for the use of devices like the i. Pad, and develop policies and procedures that take the security limitations of the device into consideration and adequately protect sensitive business data n Perform periodic risk and security assessments n Set resource controls © 2010 Enterprise Risk Management
Enterprise Risk Management Miami, FL Countering New Challenges n Provide security awareness and training n Eliminate any unnecessary services © 2010 Enterprise Risk Management September 2010

Enterprise Risk Management Miami, FL Enterprise Risk Management Phone: 305. 447 -6750 Fax: 305. 447 -6752 e-mail: info@emrisk. com URL: www. emrisk. com © 2010 Enterprise Risk Management September 2010
- Slides: 46