Enterprise Information Protection When DLP is Not Enough
















- Slides: 42

Enterprise Information Protection When DLP is Not Enough? Graham Howton Channel Manager, EMEA © 2011 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

Agenda • Introduction to Verdasys • Gartner • The Insider Threat and APT’s • Enterprise Information Protection (EIP) • Importance of user-awareness • Use-Cases

— Uniquely satisfy an expanding set of critical use cases — Scale from the desktop to the cloud FINANCIAL INSURANCE HI-TECH & OUTSOURCING — Enable ownership & control independent of network infrastructure RETAIL & TELECOM — Secure business processes not infrastructure LIFE SCIENCES & MANUFACTURING — Data-centric, risk based protection of structured and unstructured data GOVERNMENT ENERGY & DEFENSE Enterprise Information Protection FINANCIAL Verdasys: The Leader in EIP © 2011 Verdasys Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY

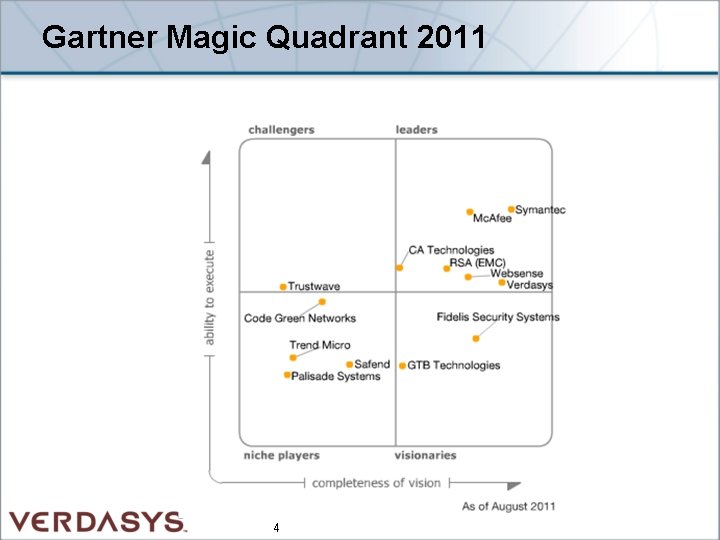
Gartner Magic Quadrant 2011 4

Traditional Approaches Have Failed DE NTROL VICE CO / VENDO R 1 OR 2 TORING / VEND CONTENT MONI EDRM & ENCRYPTION / VENDOR 3 VENDOR 4 DATA CLASSIFICATION / AUDIT & FORENSICS / VENDOR 5 OR 6 HOST IPS / VENDOR N… PROBLEM N… New Threat = New Product, Vendor Force Business Process to Change User Productivity Impacted Numerous Control Panels, Interfaces Multiple disparate Policies, Reports Expensive Deployments, Support Increasing Complexity, Cost and Risk © 2009 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.


US National Security Agency Experts from the US National Security Agency and government labs said America had to change the way it thought about protecting Department of Defense (Do. D) computer networks. "We've got the wrong mental model here, " said Dr James Peery, head of the Information Systems Analysis Centre at the Sandia National Laboratories. "I think we have to go to a model where we assume that the adversary is in our networks. “ That change would mean spending less time shoring up firewalls and gateways and more time ensuring data was safe, he said. Dr Kaigham Gabriel, current head of the Defense Advanced Research Projects Agency, likened the current cybersecurity efforts of the US Do. D to treading water in the middle of the ocean. All that did was slightly delay the day when the Do. D drowned under the weight of maintaining its network defences, he said. The Do. D oversees 15, 000 networks that connect about seven million devices.

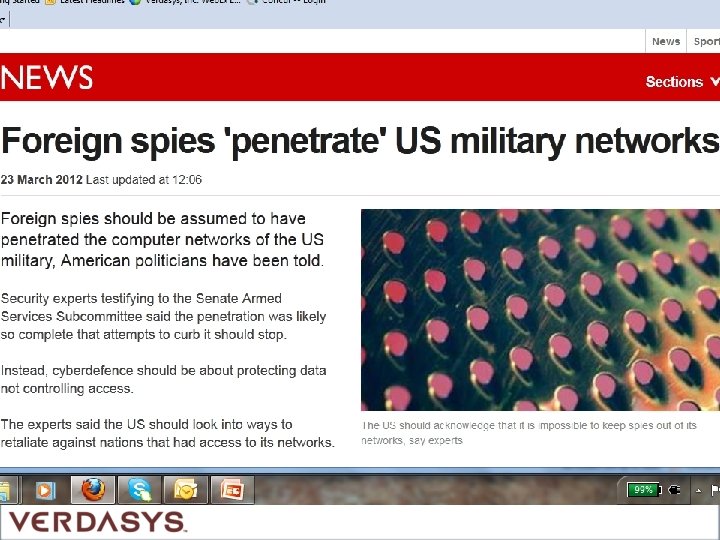
Federal Bureau of Investigation Shawn Henry - “Top Cyber Cop” The Federal Bureau of Investigation's top cyber cop offered a grim appraisal of the nation's efforts to keep computer hackers from plundering corporate data networks: "We're not winning, " he said. 10 years worth of research and development, valued at more than $1 billion, was stolen by hackers unidentified company? Companies need to do more than just react to intrusions! Source: Mar. 28, 2012, on page B 1 in The Wall Street Journal, with the headline: U. S. Outgunned in Hacker War

Top Data Security Challenges Insider Threats © 2011 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

Insider Threat • Privileged user data management is the “last mile” of data security • Insiders are trusted with IP, but it is difficult to hold them accountable for its use • When incidents occur, investigations are costly, timeconsuming, and don’t necessarily provide smoking guns to prosecute • So far, Wiki. Leaks has not been a game-changer for privileged user management in banks or insurers, but APT has taken the Insider Threat to another level • Solution value dependent on potential damages caused if insider steals IP

Defining Insider Threat Types • Malicious – Motivation = anger, dissatisfaction – Threat = attack systems and network • Theft – Motivation = money, economic gain – Includes corporate & state espionage – Threat = data theft • Hacktivits (e. g. Anonymous) – Motivation = anger & dissatisfaction or belief – Threat = data theft

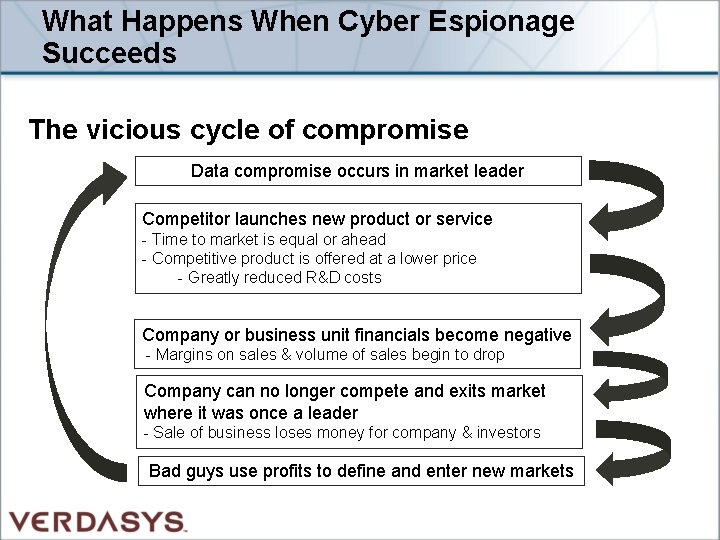
What Happens When Cyber Espionage Succeeds The vicious cycle of compromise Data compromise occurs in market leader Competitor launches new product or service - Time to market is equal or ahead - Competitive product is offered at a lower price - Greatly reduced R&D costs Company or business unit financials become negative - Margins on sales & volume of sales begin to drop Company can no longer compete and exits market where it was once a leader - Sale of business loses money for company & investors Bad guys use profits to define and enter new markets

Insider Threat Incident: LG Joeng (only known name) • Copied 1, 182 top secret plasma display design files onto his personal drive and went to Changhong-Orion PDP – Changhong, reportedly paid Joeng $300, 000 per year, an apartment and a car (while he still collecting his LG salary) • LG was unaware Jeong had left, leaving his access to the network open – Stole file: plasma display panel production – Stole files: plant’s power system and construction blueprints • LG was made aware of thefts by a distributor in SE Asia • Joeng was extradited, Prosecutors in Seoul indicted Joeng for spying • Cost to LG - estimated at more than $1 Billion – Changhong has not returned any of the stolen secrets

Lessons Learned • How was Joeng caught? – Third party distributor recognized technical manuals were copied and alerted LG • Lessons Learned – Data monitoring: location, access and movement related to sensitive data must be understood – De-provisioning process at the network, application and data levels needs to be in place an effective. – Business Managers and HR must work with Security – USB device usage monitoring and controls, as well as other channels need to be in place

Insider Threat Mitigation: Best Practices 1. Create integrated processes Business, HR and Security – Create standard on-boarding and off-boarding processes – Increase data usage monitoring for incidents & departures 2. Distribute trust amongst multiple parties to force collusion – Most insiders act alone 3. Link Policy Training w/ Risk and Compliance Analysis – Real-time education, alerting & justification prompts – Allow self-compliance; create clear deterrence

Insider Threat Mitigation: Best Practices • Assess insider risks by content and context – Not just “what”, but “who, where, when, & how” – Using a sliding response scale; risk based approach • Create Data Identification & Classification – Automatic or manual tagging (w/ auditing) – Files using previously tagged content inherit classification • Use Identity-based Data Controls – Based on user rights, file sensitivity, source & destination, etc – Use encryption for data access - closes “super user” loopholes

Insider Threat Mitigation: Best Practices • Implement integrated physical and logical (technical) security controls to cover more risks effectively – Camera monitoring, linked with data usage and movement controls • Put Data Usage Monitoring & Control in Place – Host based monitoring is a requirement – Establish data usage norms, watch for behavioral changes • Forensically Log Events – Assure all data transactions are user-attributable – Logs must be evidentiary grade and tamper proof

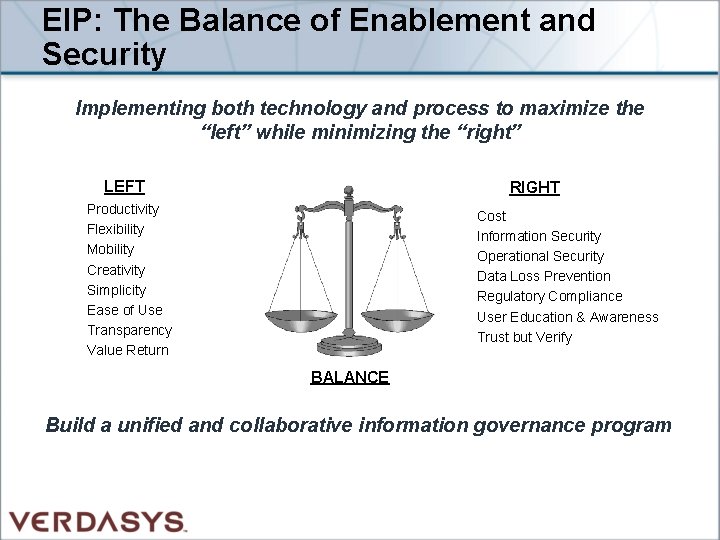
EIP: The Balance of Enablement and Security Implementing both technology and process to maximize the “left” while minimizing the “right” LEFT RIGHT Productivity Flexibility Mobility Creativity Simplicity Ease of Use Transparency Value Return Cost Information Security Operational Security Data Loss Prevention Regulatory Compliance User Education & Awareness Trust but Verify BALANCE Build a unified and collaborative information governance program

Beware!!!! All DLP solutions are not the same!!!!!!

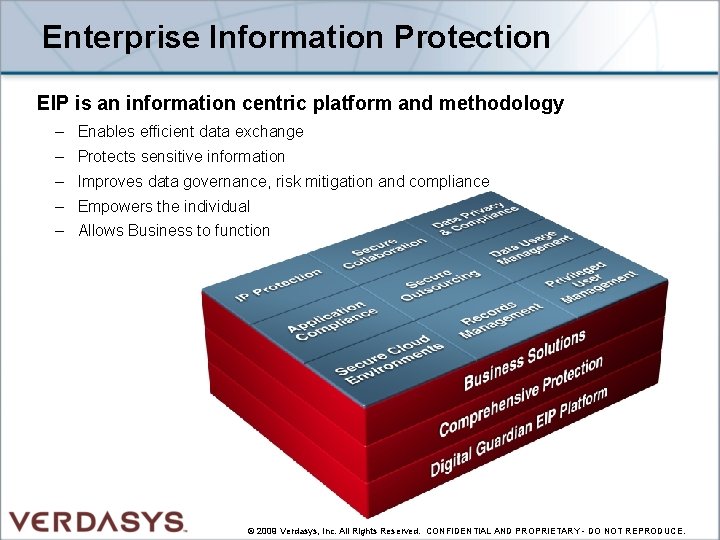
Enterprise Information Protection EIP is an information centric platform and methodology – Enables efficient data exchange – Protects sensitive information – Improves data governance, risk mitigation and compliance – Empowers the individual – Allows Business to function © 2009 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

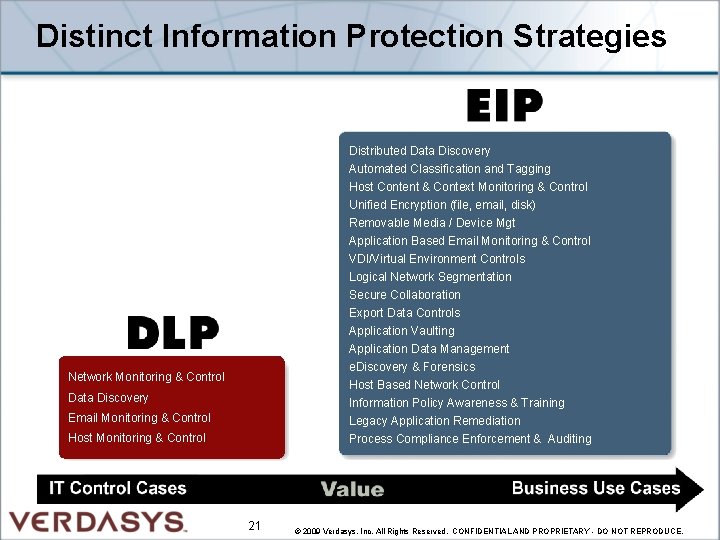
Distinct Information Protection Strategies Distributed Data Discovery Automated Classification and Tagging Host Content & Context Monitoring & Control Unified Encryption (file, email, disk) Removable Media / Device Mgt Application Based Email Monitoring & Control VDI/Virtual Environment Controls Logical Network Segmentation Secure Collaboration Export Data Controls Application Vaulting Application Data Management e. Discovery & Forensics Host Based Network Control Information Policy Awareness & Training Legacy Application Remediation Process Compliance Enforcement & Auditing Network Monitoring & Control Data Discovery Email Monitoring & Control Host Monitoring & Control 21 © 2009 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

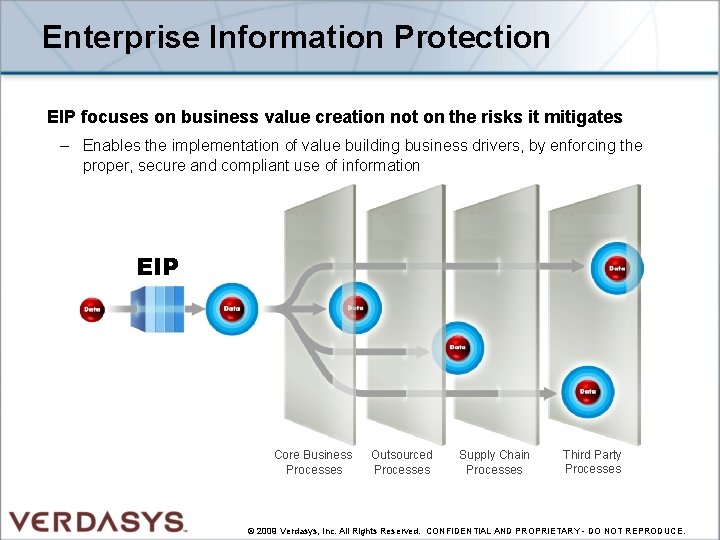
Enterprise Information Protection EIP focuses on business value creation not on the risks it mitigates – Enables the implementation of value building business drivers, by enforcing the proper, secure and compliant use of information EIP Core Business Processes Outsourced Processes Supply Chain Processes Third Party Processes © 2009 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

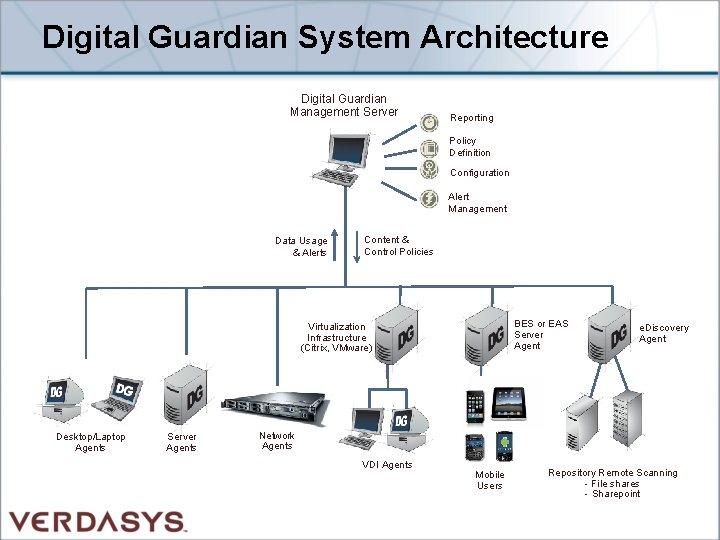
Digital Guardian System Architecture Digital Guardian Management Server Reporting Policy Definition Configuration Alert Management Data Usage & Alerts Content & Control Policies BES or EAS Server Agent Virtualization Infrastructure (Citrix, VMware) Desktop/Laptop Agents Server Agents e. Discovery Agent Network Agents VDI Agents Mobile Users Repository Remote Scanning - File shares - Sharepoint

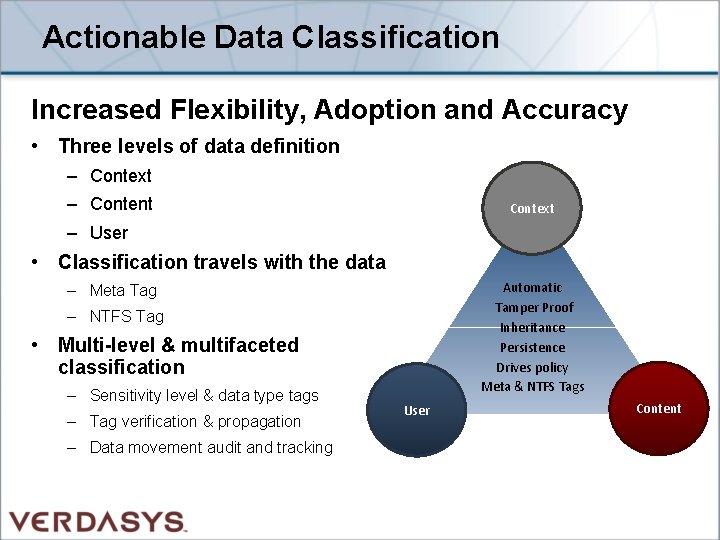
Actionable Data Classification Increased Flexibility, Adoption and Accuracy • Three levels of data definition – Context – Content Context – User • Classification travels with the data Automatic Tamper Proof Inheritance Persistence Drives policy Meta & NTFS Tags – Meta Tag – NTFS Tag • Multi-level & multifaceted classification – Sensitivity level & data type tags – Tag verification & propagation – Data movement audit and tracking User Content

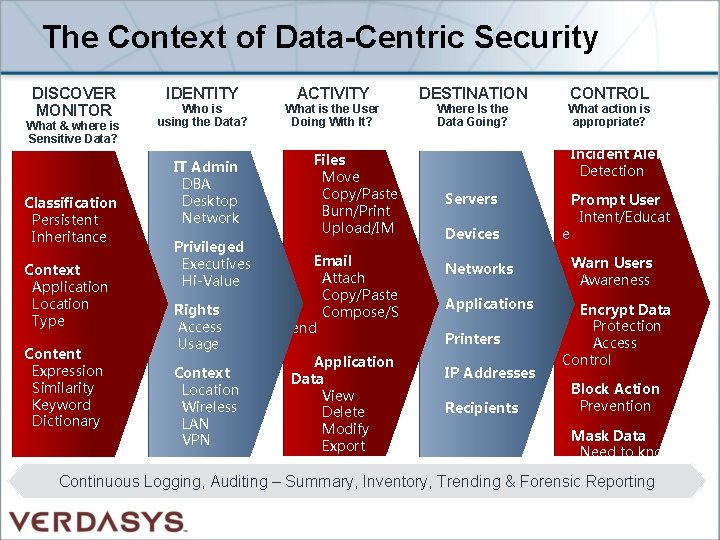
The Context of Data-Centric Security DISCOVER MONITOR What & where is Sensitive Data? Classification Persistent Inheritance Context Application Location Type Content Expression Similarity Keyword Dictionary IDENTITY Who is using the Data? IT Admin DBA Desktop Network Privileged Executives Hi-Value Rights Access Usage Context Location Wireless LAN VPN ACTIVITY What is the User Doing With It? Files Move Copy/Paste Burn/Print Upload/IM Email Attach Copy/Paste Compose/S end Application Data View Delete Modify Export DESTINATION Where Is the Data Going? CONTROL What action is appropriate? Incident Alert Detection Servers Devices Networks Applications Printers IP Addresses Recipients e Prompt User Intent/Educat Warn Users Awareness Encrypt Data Protection Access Control Block Action Prevention Mask Data Need to know Continuous Logging, Auditing – Summary, Inventory, Trending & Forensic Reporting

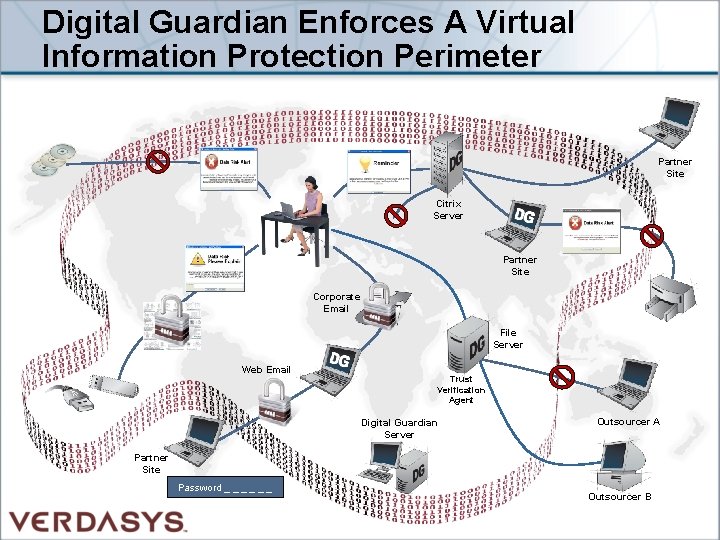
Digital Guardian Enforces A Virtual Information Protection Perimeter Partner Site Citrix Server DG Partner Site Corporate Email File Server Web Email Trust Verification Agent Digital Guardian Server Outsourcer A Partner Site Password _ _ _ Outsourcer B

Use-Case - Social Networking Risks • With the tremendous power of social networking, comes a myriad of associated risk: • IP Protection • Privacy Protection • Risks to Reputation • National Security Risk • Key location and movement information • IT Risk • • Apps written quickly by unknown parties, Security and intrusion vulnerabilities, Inability to control apps contained within browser User ability to install unauthorized apps. • Incident – Soldier posts operational details on Facebook! 27 © 2010 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

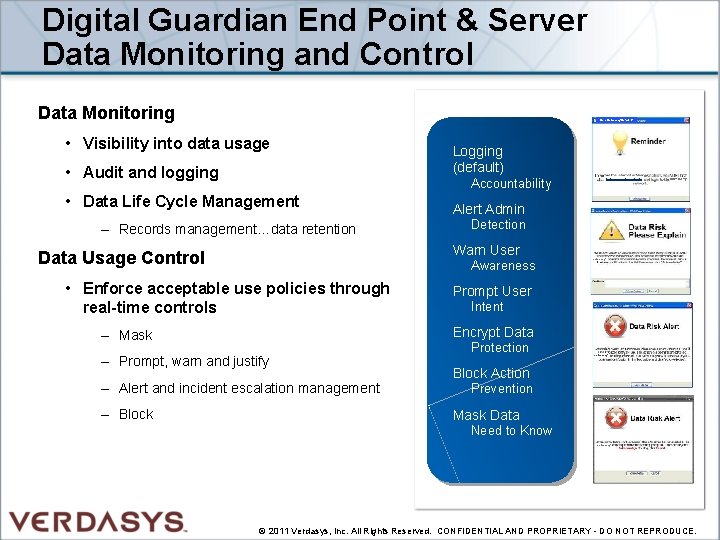
Digital Guardian End Point & Server Data Monitoring and Control Data Monitoring Non-Company Network • Visibility into data usage • Audit and logging Logging (default) • Data Life Cycle Management Alert Admin Accountability – Records management…data retention Awareness • Enforce acceptable use policies through real-time controls company Prompt User Intent Encrypt Data – Mask – Prompt, warn and justify – Alert and incident escalation management – Block company Detection Warn User Data Usage Control myaccess. company. com Protection company Block Action Prevention Mask Data Need to Know company © 2011 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

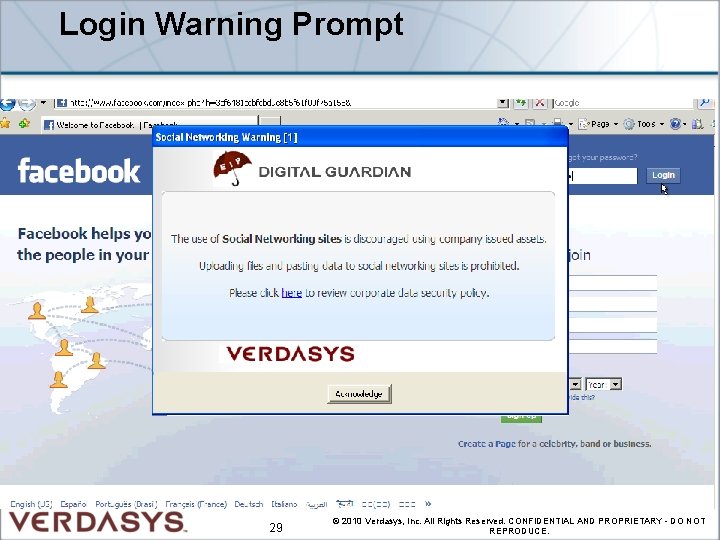
Login Warning Prompt 29 © 2010 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

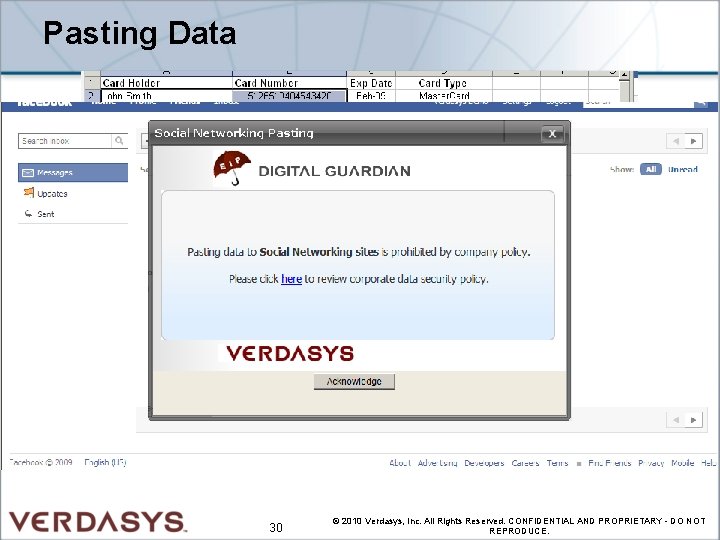
Pasting Data 30 © 2010 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

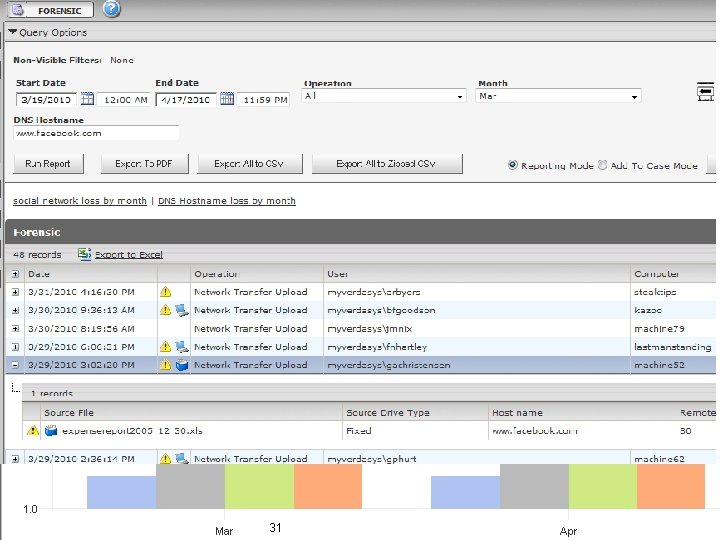
Report Capability • Logins by site (When Possible) • Uploads by site • Uploads by file extension • Downloads by site • Downloads by file extension • ADE attempts by site • ADE attempts by extension 31 PA © 2010 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

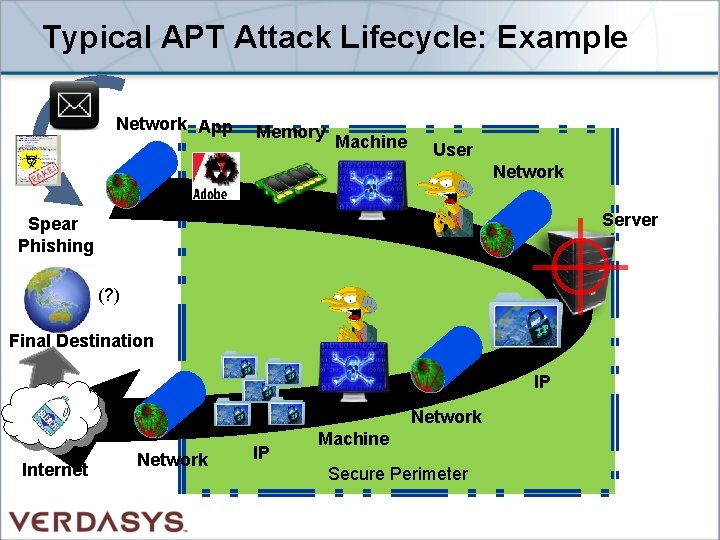
Typical APT Attack Lifecycle: Example Network App Memory Machine User Network Server Spear Phishing (? ) Final Destination IP Network Internet Network IP Machine Secure Perimeter

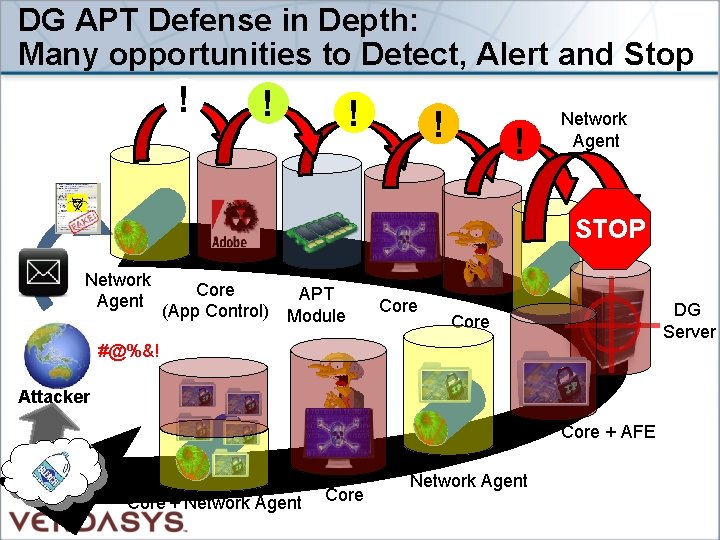
DG APT Defense in Depth: Many opportunities to Detect, Alert and Stop ! ! ! Network Agent STOP Network Agent Core (App Control) APT Module Core DG Server Core #@%&! Attacker Core + AFE Core + Network Agent Core Network Agent

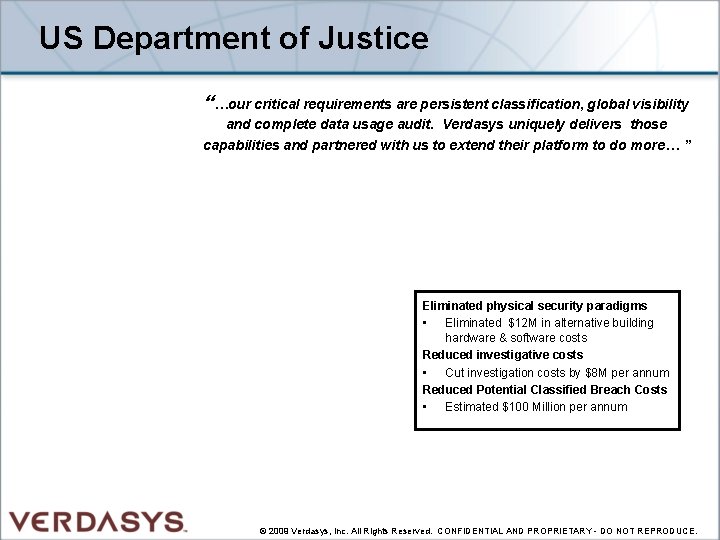
US Department of Justice “…our critical requirements are persistent classification, global visibility and complete data usage audit. Verdasys uniquely delivers those capabilities and partnered with us to extend their platform to do more… ” Eliminated physical security paradigms • Eliminated $12 M in alternative building hardware & software costs Reduced investigative costs • Cut investigation costs by $8 M per annum Reduced Potential Classified Breach Costs • Estimated $100 Million per annum © 2009 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

ING BANK “Our security goal is to create more collaborative environments. Digital Guardian mitigates the risk of data loss in our open work places and supports are partnership with Workers Councils ” Eric Luiken, Chief Architect Protecting PII while supporting an open and collaborative working environment Use Case Coverage • • PII protection User policy awareness & training Remote media control and encryption Social networking control (Face Book & Linked in) Future Coverage ROI: Reduced Software Costs Displaced USB device and Email gateway & monitoring software reducing licenses and support costs by $2. 5 M • Email encryption Critical Differentiators • Social Networking upload controls • Workers Council approval © 2011 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

Ferrari Formula-1 Racing “Digital Guardian has grown to be one of the pillars of our security strategy and our foremost tool for insider threat prevention and protection. ” Davide Ferrari, Direzione Operazioni Securing critical design IP across the enterprise and at 20 race tracks around the globe. Current Use Case Coverage • • • Race car design and racing strategy IP protection Privileged user monitoring & Control e. Discovery and Forensics Future Platform Development • Unified encryption (email, file and full disk) Critical Differentiators • • Real-time Privileged user monitoring and audit Forensic case management Secure collaboration at race sites • Save $2 M per annum in alternative security costs Decreased administrative staff • Reduce FTE costs by $4 M per annum Prosecuted Insider Compromise • $100 Million fine to F-1 Racing • Default victory of Constructor Cup $500 M © 2009 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

Data-Centric Questions? • How do you know where your sensitive data is right now? • How do you know how data moves within your business processes and what your employees are actually doing with the data they access to do their jobs? • What are your employees doing with your data when they are off or outside the network? • How do you manage data on mobile devices and BYOPC?

More Data-Centric Questions? • What is the 3 rd line of your corporate security policy? • How many of your employees actually know it? • How do you effectively train your employees on data security polices and ensure they are in compliance in real-time? • What would the benefit be to the organization if security enabled the business instead of security controls or policies hindering business processes?

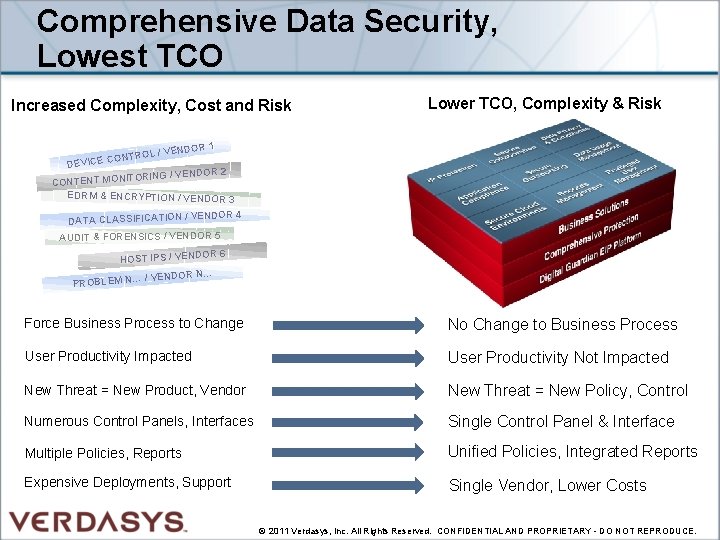
Comprehensive Data Security, Lowest TCO Increased Complexity, Cost and Risk Lower TCO, Complexity & Risk 1 ENDOR TROL / V N O C E DEVIC OR 2 TORING / VEND CONTENT MONI EDRM & ENCRYPTION / VENDOR 3 VENDOR 4 DATA CLASSIFICATION / AUDIT & FORENSICS / VENDOR 5 OR 6 HOST IPS / VENDOR N… PROBLEM N… Force Business Process to Change No Change to Business Process User Productivity Impacted User Productivity Not Impacted New Threat = New Product, Vendor New Threat = New Policy, Control Numerous Control Panels, Interfaces Single Control Panel & Interface Multiple Policies, Reports Unified Policies, Integrated Reports Expensive Deployments, Support Single Vendor, Lower Costs © 2011 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

Proven EIP Success Lower TCO, Complexity & Risk “Rival Racing Team Fined $100 Million in Spy Scandal” No Changewith to Business Process USG agrees settlement Lafarge Mon, 07 Dec 2009 User Productivity Impacted Under the agreement USG will receive. Not USD 105 m New Threat = New Policy, Control Single Control Panel & Interface Unified Policies, Integrated Reports Single Vendor, Lower Costs © 2011 Verdasys, Inc. All Rights Reserved. CONFIDENTIAL AND PROPRIETARY - DO NOT REPRODUCE.

The Four Seminal Ideas of Data Security 1. Data is the correct unit of measurement • Requirement is data-centric not Network or Device centric • Visibility, monitoring, control 2. Operate close to the user • The desktop is today’s data router • Understand full-context of data type, content & user action 3. Take a risk based approach to protection • Automated, persistent discovery & classification of data • Classification-driven information monitoring and policy enforcement 4. Flexibility to support and enhance business processes • No one response/control is appropriate to all risks • Shaping user behavior through warnings/prompts of greatest value • Encryption as an integrated control safeguards data; establishes trust

Thank You