Enhancing Users Comprehension of Android Permissions Liu Yang










![Comparison to Privacy as Expectations (PAE) [Lin et al. , Ubicomp’ 12] PAE Goals: Comparison to Privacy as Expectations (PAE) [Lin et al. , Ubicomp’ 12] PAE Goals:](https://slidetodoc.com/presentation_image_h/ebaa5ed5596edc84deaf00d05376a486/image-20.jpg)


- Slides: 22

Enhancing Users’ Comprehension of Android Permissions Liu Yang, Nader Boushehrinejad, Pallab Roy, Vinod Ganapathy, Liviu Iftode Department of Computer Science Rutgers University

Android Apps Social networking Online shopping Gaming Communication Entertainment Transportation Sports …

Resources on Android

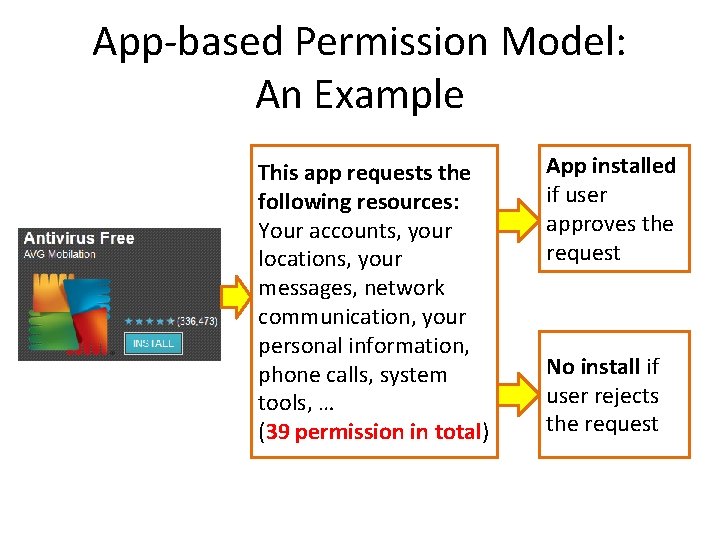
App-based Permission Model: An Example This app requests the following resources: Your accounts, your locations, your messages, network communication, your personal information, phone calls, system tools, … (39 permission in total) App installed if user approves the request No install if user rejects the request

Users Puzzled by Permissions • 3% of users correctly answer three permission questions [Felt. et al. SOUPS’ 12, Kelly et al. , USEC’ 12] – A lot of permissions defined (134, Android 2. 2) – Not always self-explanatory, e. g. , SUBSCRIBED_FEEDS_READ, WRITE_SYN_SETTINGS, … • Confusion exists for developers [Felt et al. CCS’ 11]

Permission Misuse com. antivirus com. kayak. android com. taskos com. kakao. talk Locations IMEI com. facebook Contacts Phone number Locations: 45/110 apps IMEI: 31/110 apps Contacts: 7/110 apps Phone#: 5/110 apps [Hornyack et al. , App. Fence, CCS’ 11] [Lin et al. , Ubicom’ 12] com. myyearbook. m

Our Contribution • Enhancing users’ comprehension of permissions using crowdsourcing – Permission usage commented by app users – Permission comments shared among users • Designing Droidganger which provides clues of permission usage – Record/replay + permission suppression • Feasibility study

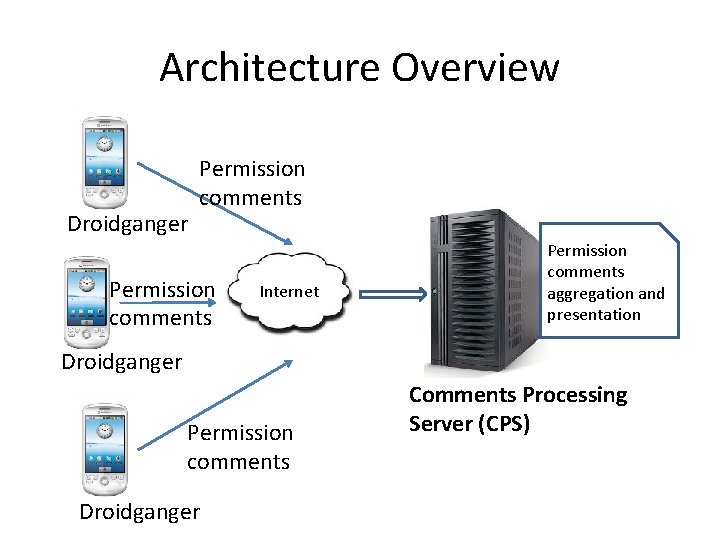
Architecture Overview Droidganger Permission comments Internet Permission comments aggregation and presentation Droidganger Permission comments Droidganger Comments Processing Server (CPS)

Crowdsourcing • Users of same apps form user communities • Users use Droidganger to help permission understanding • Each user reviews one permission (small task) • More users – more permissions covered – more execution paths covered – more apps covered

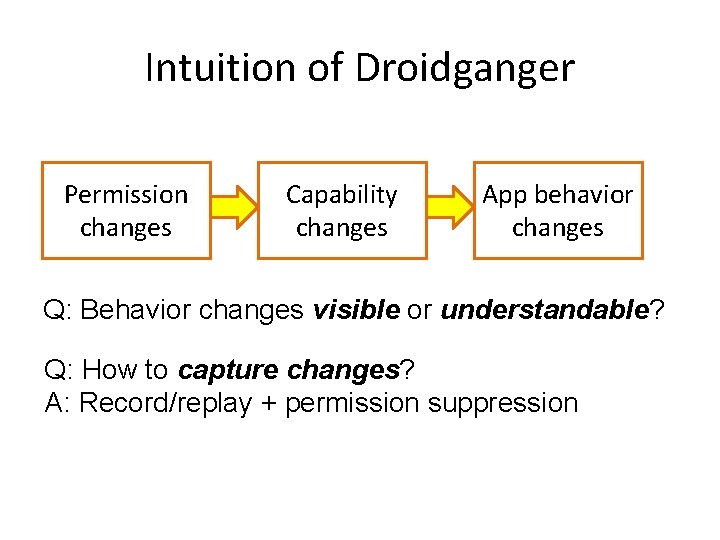
Intuition of Droidganger Permission changes Capability changes App behavior changes Q: Behavior changes visible or understandable? Q: How to capture changes? A: Record/replay + permission suppression

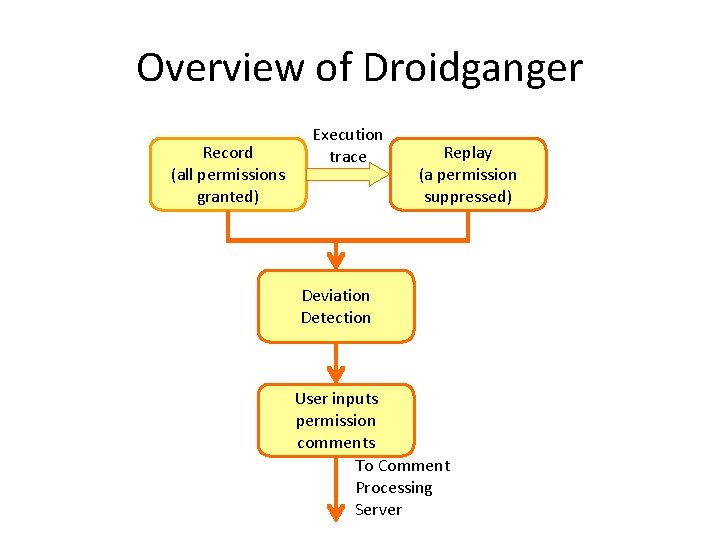
Overview of Droidganger Record (all permissions granted) Execution trace Replay (a permission suppressed) Deviation Detection User inputs permission comments To Comment Processing Server

Record and Replay • Record app execution – non-deterministic inputs and events, e. g. , keystrokes, touches/drags, etc. (saved as a trace) – outputs, e. g. , screenshots, etc. • Replay a trace – each time a different permission suppressed – snapshots taken for comparison

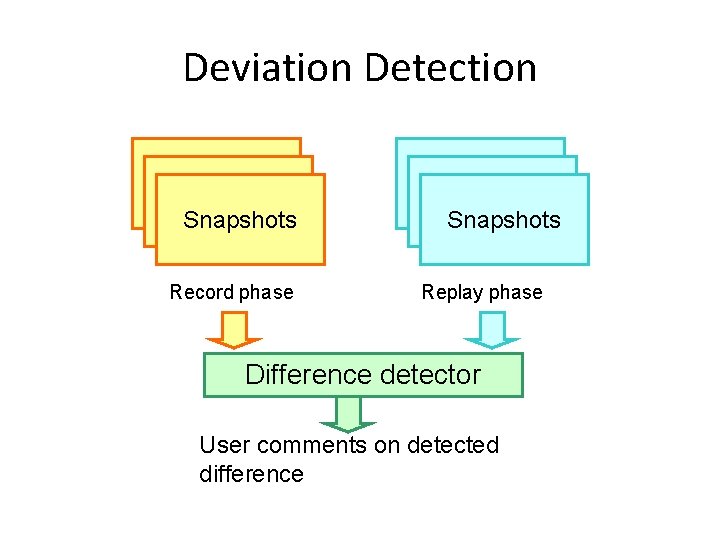
Deviation Detection Snapshots Record phase Snapshots Replay phase Difference detector User comments on detected difference

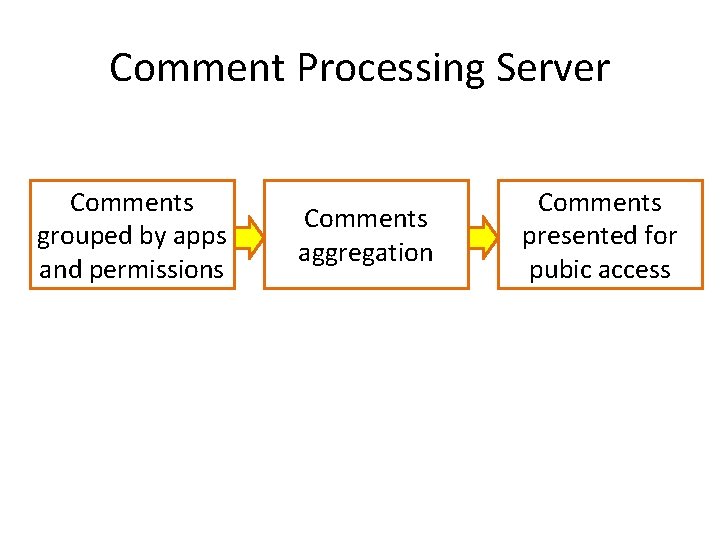
Comment Processing Server Comments grouped by apps and permissions Comments aggregation Comments presented for pubic access

Feasibility Study • Implementation of Droidganger – Android 4. 0 + Emulator – Record: Intercepting Key. Events and Motion. Events – Compiling events to Python scripts – Replaying scripts with Monkeyrunner • Data Sets – Angry. Birds Rio (6 permissions) – Antivirus (39 permissions)

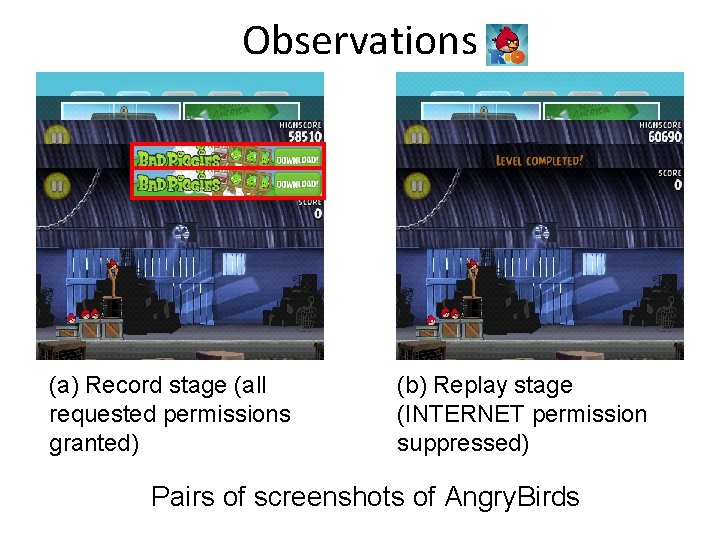
Observations (a) Record stage (all requested permissions granted) (b) Replay stage (INTERNET permission suppressed) Pairs of screenshots of Angry. Birds

Observations (cont. ) Record (all requested permissions granted) Replay WRITE_SYNC _SETTINGS permission suppressed

Observations (cont. ) Summary of observed effects with replay + permission suppression Meaningful: permission suppression provides helpful clues of purposes of permissions Crashed: app crashed due to permission suppression Syslog only: execution deviation was only captured by syslog None: no difference was observed with permission suppression

Challenges • Network proxy: recording network traffic • Randomness, e. g. , card games, etc. • Non-repeatable execution, e. g. , online payments, etc. • Application failure when permission suppressed • User incentives
![Comparison to Privacy as Expectations PAE Lin et al Ubicomp 12 PAE Goals Comparison to Privacy as Expectations (PAE) [Lin et al. , Ubicomp’ 12] PAE Goals:](https://slidetodoc.com/presentation_image_h/ebaa5ed5596edc84deaf00d05376a486/image-20.jpg)
Comparison to Privacy as Expectations (PAE) [Lin et al. , Ubicomp’ 12] PAE Goals: capturing users’ expectations on privacy Objects: Access to privacy related resources Techs: Crowdsourcing Taint. Droid New interfaces Our work improving users’ comprehension of permissions Permissions requested by apps Crowdsourcing Record/replay + Permission suppression

Related Work • Information flow and permission misuse – App. Fence [Hornyack et al. , CCS’ 11] – Taint. Droid [Enck et al. , OSDI’ 10] – Permission demystified [Felt et al. , CCS’ 11] • Privacy-preserving – Apex [Nauman et al. , Asia. CCS’ 10] – Mock. Droid [Beresford et al. , Hotmobile’ 11] • Permission comprehension and attention – [Felt et al. , SOUPS’ 12], [Kelley et al. , USEC’ 12] – [Lin et al. , Ubicom’ 12]

Conclusion • Crowdsourcing – Collections of users help each other on permission understanding • Record/replay + permission suppression: – Changes of app behavior provide clues of permission usage • Feasibility study – Droidganger providing helpful clues on permission usage