Enhancing Malware Detection Doug Cooke Director Sales Engineering





- Slides: 16

Enhancing Malware Detection Doug Cooke Director, Sales Engineering Canada January 19, 2022

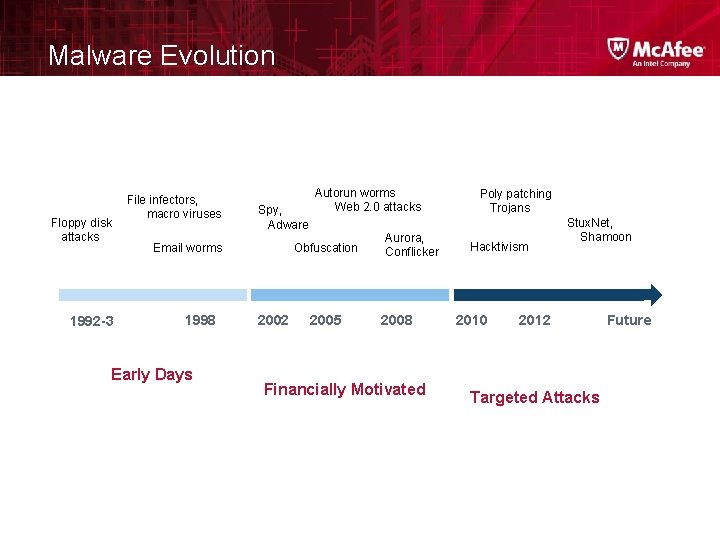
Malware Evolution Floppy disk attacks 1992 -3 File infectors, macro viruses Spy, Adware Obfuscation Email worms 1998 Early Days Autorun worms Web 2. 0 attacks 2002 2005 Aurora, Conflicker 2008 Financially Motivated Poly patching Trojans Hacktivism 2010 Stux. Net, Shamoon 2012 Targeted Attacks Future

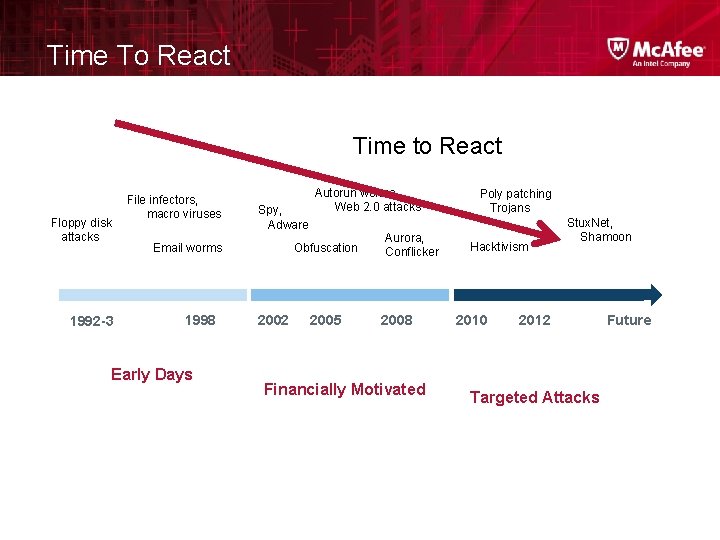
Time To React Time to React Floppy disk attacks 1992 -3 File infectors, macro viruses Spy, Adware Obfuscation Email worms 1998 Early Days Autorun worms Web 2. 0 attacks 2002 2005 Aurora, Conflicker 2008 Financially Motivated Poly patching Trojans Hacktivism 2010 Stux. Net, Shamoon 2012 Targeted Attacks Future

Case Study: What is Project Blitzkrieg • Code name for a Mc. Afee Labs project monitoring an attack against NA banking community • RAS identified the malware as belonging to the Gozi family and labeled it Prinimalka • Man in the Middle attack targeting banking customers • Banks security measures could not detect or prevent • Incorporates “web injects” – code injected into the browser based on URL • Campaign of attacks started in Spring 2012, continued activity with new variants had continued into 2013. How can we monitor these attack campaigns? How quickly can we identify Patient Zero and stop propagation?

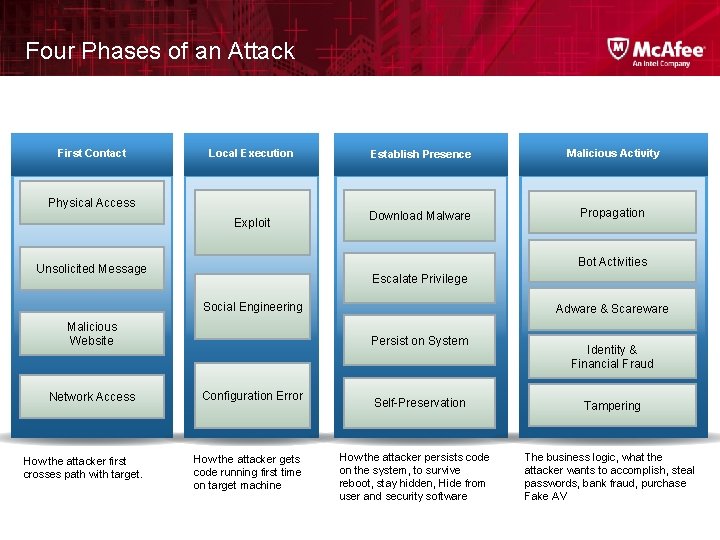
Four Phases of an Attack First Contact Local Execution Physical Access Exploit Establish Presence Malicious Activity Download Malware Propagation Bot Activities Unsolicited Message Escalate Privilege Social Engineering Malicious Website Network Access How the attacker first crosses path with target. Adware & Scareware Persist on System Configuration Error How the attacker gets code running first time on target machine Self-Preservation How the attacker persists code on the system, to survive reboot, stay hidden, Hide from user and security software Identity & Financial Fraud Tampering The business logic, what the attacker wants to accomplish, steal passwords, bank fraud, purchase Fake AV

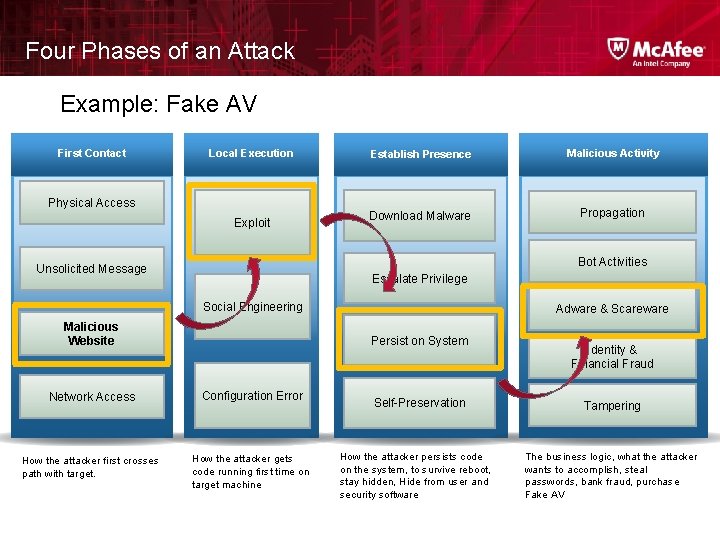
Four Phases of an Attack Example: Fake AV First Contact Local Execution Physical Access Exploit Establish Presence Malicious Activity Download Malware Propagation Bot Activities Unsolicited Message Escalate Privilege Social Engineering Malicious Website Adware & Scareware Persist on System Network Access Configuration Error How the attacker first crosses path with target. How the attacker gets code running first time on target machine Self-Preservation How the attacker persists code on the system, to survive reboot, stay hidden, Hide from user and security software Identity & Financial Fraud Tampering The business logic, what the attacker wants to accomplish, steal passwords, bank fraud, purchase Fake AV

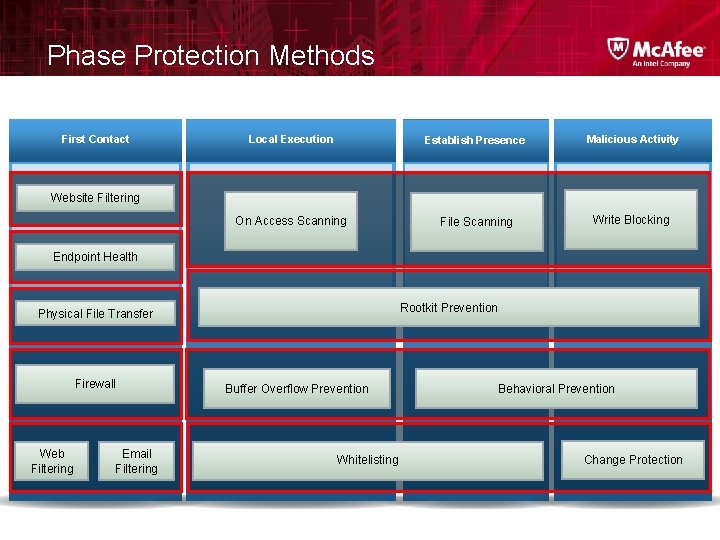
Phase Protection Methods First Contact Local Execution Establish Presence Malicious Activity On Access Scanning File Scanning Write Blocking Website Filtering Endpoint Health Rootkit Prevention Physical File Transfer Firewall Web Filtering Email Filtering Buffer Overflow Prevention Whitelisting Behavioral Prevention Change Protection

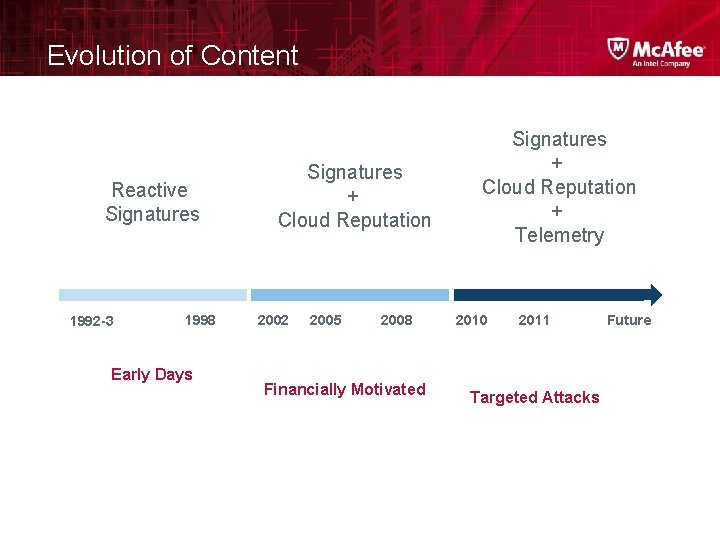
Evolution of Content Time to Protect Reactive Signatures Months 1992 -3 1998 Early Days Hours Days 2002 2005 2008 Financially Motivated 2010 2012 Targeted Attacks Future

Evolution of Content Reactive Signatures 1992 -3 1998 Early Days Signatures + Cloud Reputation 2002 2005 2008 Financially Motivated 2010 2011 Targeted Attacks Future

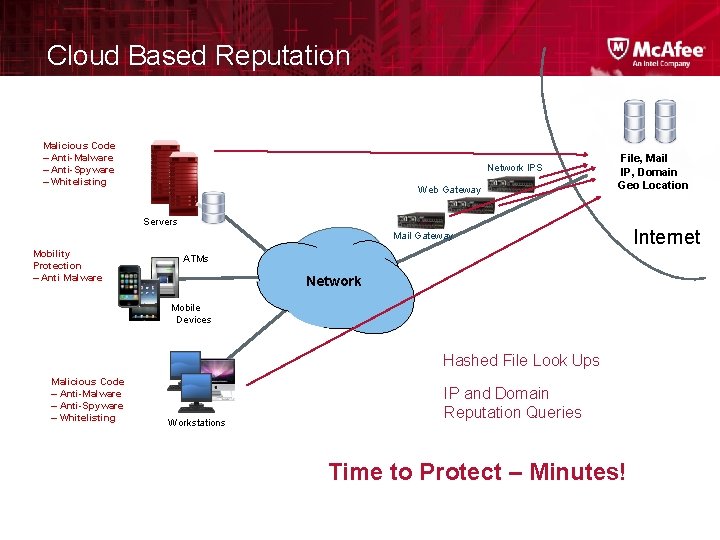
Cloud Based Reputation Malicious Code – Anti-Malware – Anti-Spyware – Whitelisting Network IPS Web Gateway File, Mail IP, Domain Geo Location Servers Mail Gateway Mobility Protection – Anti Malware ATMs Network Mobile Devices Hashed File Look Ups Malicious Code – Anti-Malware – Anti-Spyware – Whitelisting Workstations IP and Domain Reputation Queries Time to Protect – Minutes! Internet

Evolution of Content Reactive Signatures 1992 -3 1998 Early Days Signatures + Cloud Reputation 2002 2005 2008 Financially Motivated Signatures + Cloud Reputation + Telemetry 2010 2011 Targeted Attacks Future

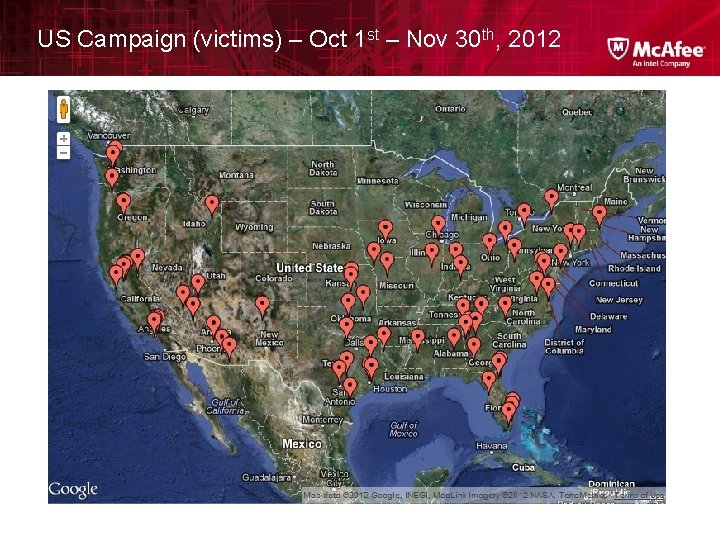
US Campaign (victims) – Oct 1 st – Nov 30 th, 2012

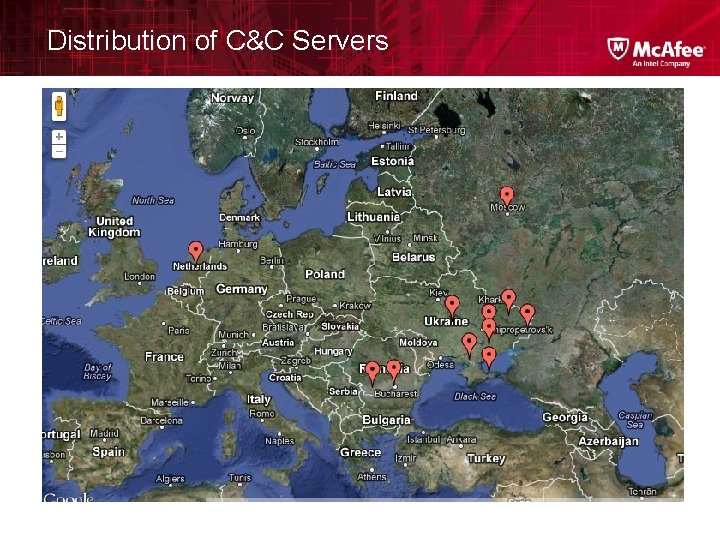
Distribution of C&C Servers

Adding Context to the Content • Leverage 100 M+ consumers base plus opt-in enterprises • Enhanced scanning engines to collect further data during scanning activities – HASH of malware file & originating IP – file paths, processes, features of the file etc. – upload suspicious file • Enhanced scanning drivers allow specific data to be pulled from specific types of malware – e. g. Blitzkrieg – establish cloud based data for FI to monitor attacking IPs – e. g. Spy. Eye - pull institution specific data from java scripts • The enriched data introduces the opportunity for greater analysis and correlation of collected data • Expose this data to customers through a service offering Access to Zero Day Attacks as Quickly as Possible

Getting Out in Front!

Summary • Will use these talking point for previous slide • The malware community will continue to find creative approaches to wreak havoc around the computing community. • New technologies (whitelisting etc. ) will help but the opportunity still exists to leverage more sophisticated detection capabilities. • Pulling contextual information from active systems will enhance the effectiveness of cloud based reputation databases.