Enhanced alerting and collaborative incident management How to

Enhanced alerting and collaborative incident management | How to supervise alerts and incidents in a railway context ? EU Project 730843
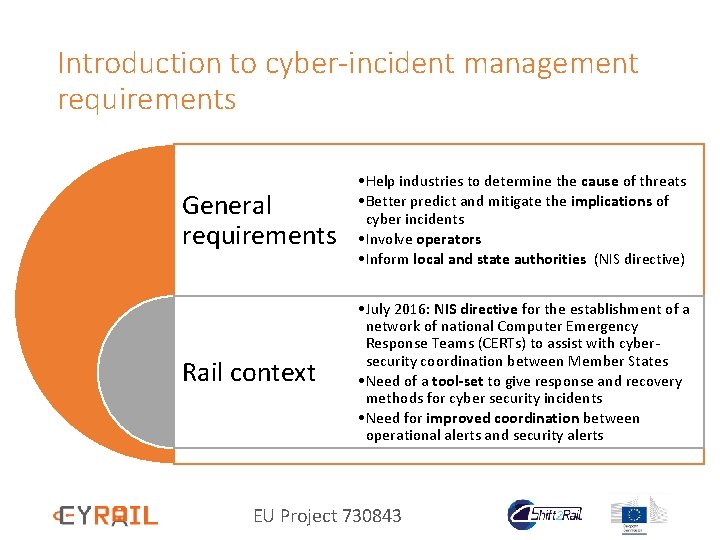
Introduction to cyber-incident management requirements General requirements • Help industries to determine the cause of threats • Better predict and mitigate the implications of cyber incidents • Involve operators • Inform local and state authorities (NIS directive) Rail context • July 2016: NIS directive for the establishment of a network of national Computer Emergency Response Teams (CERTs) to assist with cybersecurity coordination between Member States • Need of a tool-set to give response and recovery methods for cyber security incidents • Need for improved coordination between operational alerts and security alerts EU Project 730843
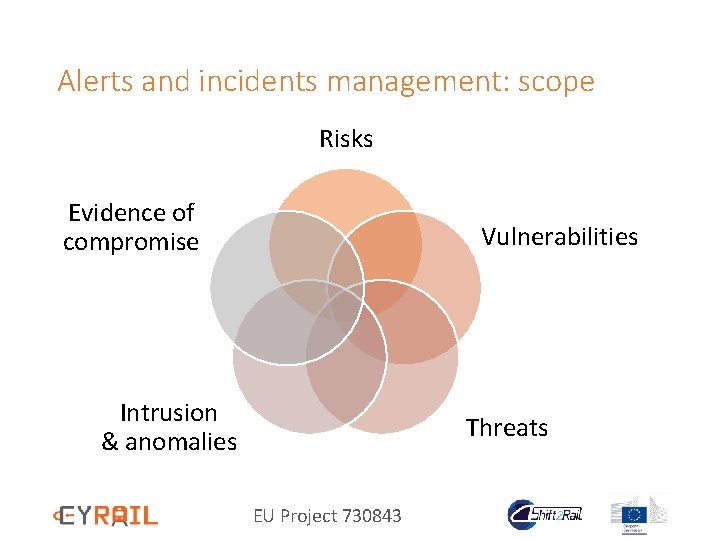
Alerts and incidents management: scope Risks Evidence of compromise Vulnerabilities Intrusion & anomalies Threats EU Project 730843
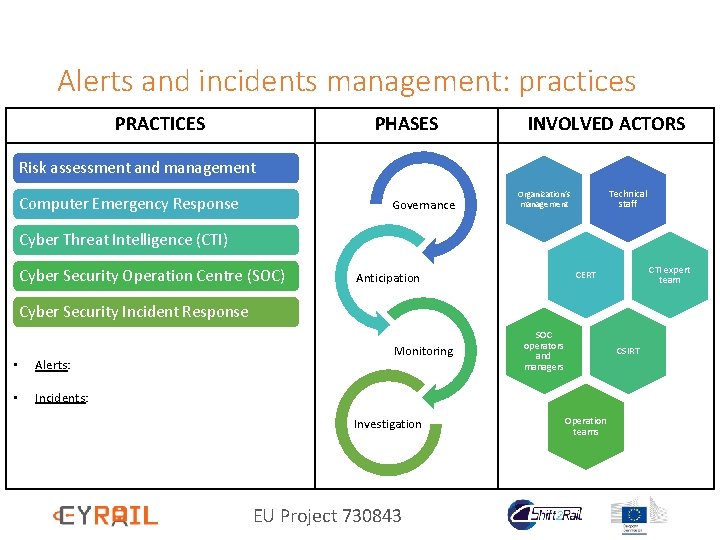
Alerts and incidents management: practices PRACTICES PHASES INVOLVED ACTORS Risk assessment and management Computer Emergency Response Governance Technical staff Organization’s management Cyber Threat Intelligence (CTI) Cyber Security Operation Centre (SOC) CTI expert team CERT Anticipation Cyber Security Incident Response • Alerts: • Incidents: Monitoring Investigation EU Project 730843 SOC operators and managers CSIRT Operation teams
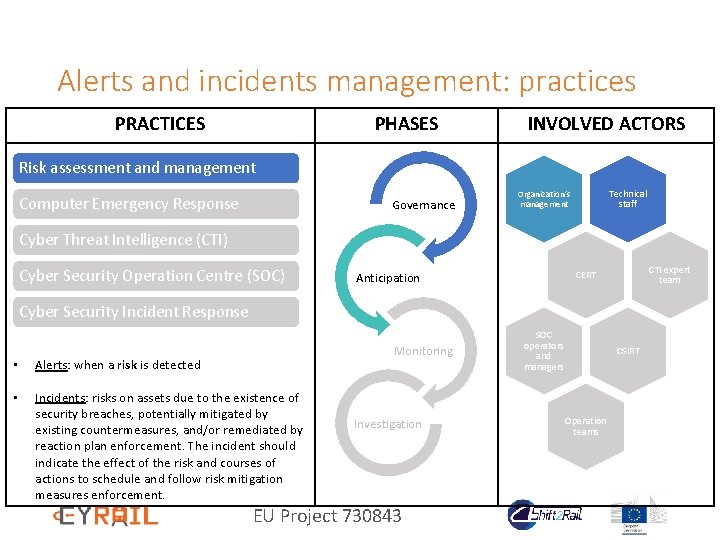
Alerts and incidents management: practices PRACTICES PHASES INVOLVED ACTORS Risk assessment and management Computer Emergency Response Governance Technical staff Organization’s management Cyber Threat Intelligence (CTI) Cyber Security Operation Centre (SOC) CTI expert team CERT Anticipation Cyber Security Incident Response Monitoring • Alerts: when a risk is detected • Incidents: risks on assets due to the existence of security breaches, potentially mitigated by existing countermeasures, and/or remediated by reaction plan enforcement. The incident should indicate the effect of the risk and courses of actions to schedule and follow risk mitigation measures enforcement. Investigation EU Project 730843 SOC operators and managers CSIRT Operation teams
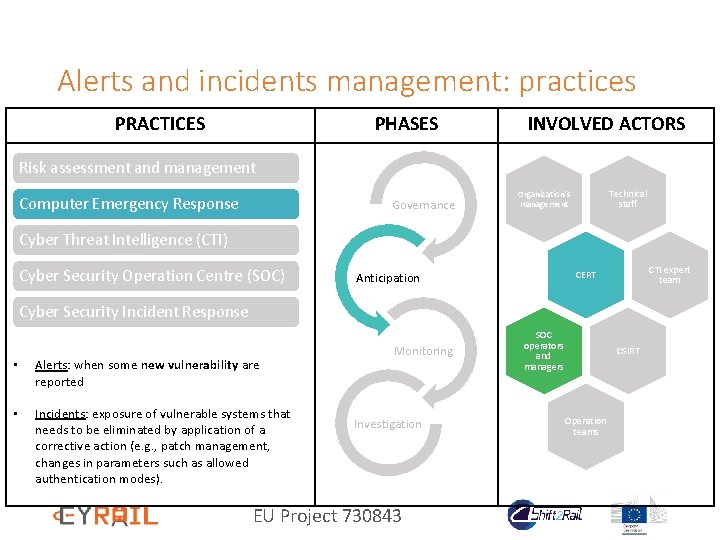
Alerts and incidents management: practices PRACTICES PHASES INVOLVED ACTORS Risk assessment and management Computer Emergency Response Governance Technical staff Organization’s management Cyber Threat Intelligence (CTI) Cyber Security Operation Centre (SOC) CTI expert team CERT Anticipation Cyber Security Incident Response • Alerts: when some new vulnerability are reported • Incidents: exposure of vulnerable systems that needs to be eliminated by application of a corrective action (e. g. , patch management, changes in parameters such as allowed authentication modes). Monitoring Investigation EU Project 730843 SOC operators and managers CSIRT Operation teams
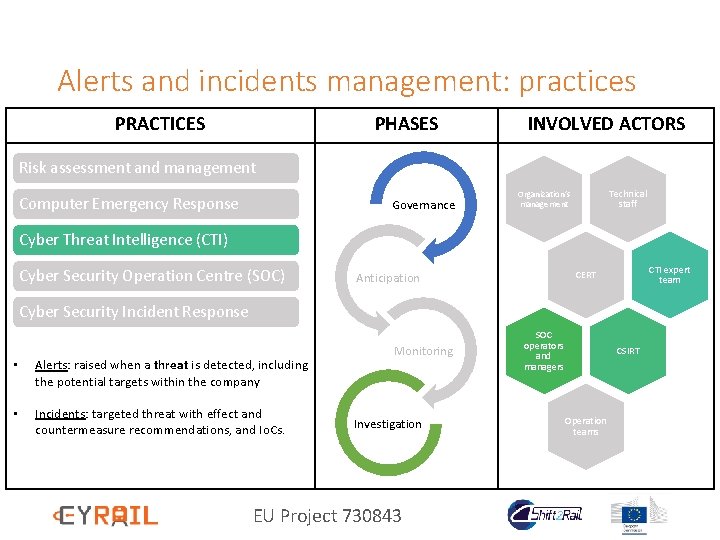
Alerts and incidents management: practices PRACTICES PHASES INVOLVED ACTORS Risk assessment and management Computer Emergency Response Governance Technical staff Organization’s management Cyber Threat Intelligence (CTI) Cyber Security Operation Centre (SOC) CTI expert team CERT Anticipation Cyber Security Incident Response • Alerts: raised when a threat is detected, including the potential targets within the company • Incidents: targeted threat with effect and countermeasure recommendations, and Io. Cs. Monitoring Investigation EU Project 730843 SOC operators and managers CSIRT Operation teams
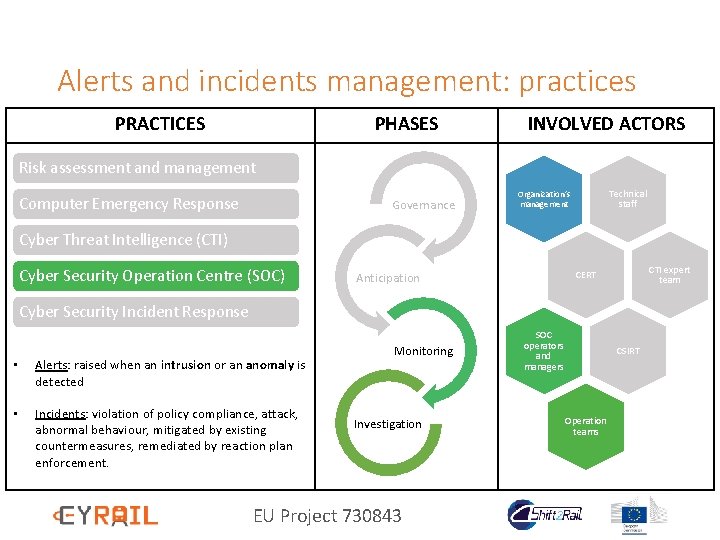
Alerts and incidents management: practices PRACTICES PHASES INVOLVED ACTORS Risk assessment and management Computer Emergency Response Governance Technical staff Organization’s management Cyber Threat Intelligence (CTI) Cyber Security Operation Centre (SOC) CTI expert team CERT Anticipation Cyber Security Incident Response • Alerts: raised when an intrusion or an anomaly is detected • Incidents: violation of policy compliance, attack, abnormal behaviour, mitigated by existing countermeasures, remediated by reaction plan enforcement. Monitoring Investigation EU Project 730843 SOC operators and managers CSIRT Operation teams
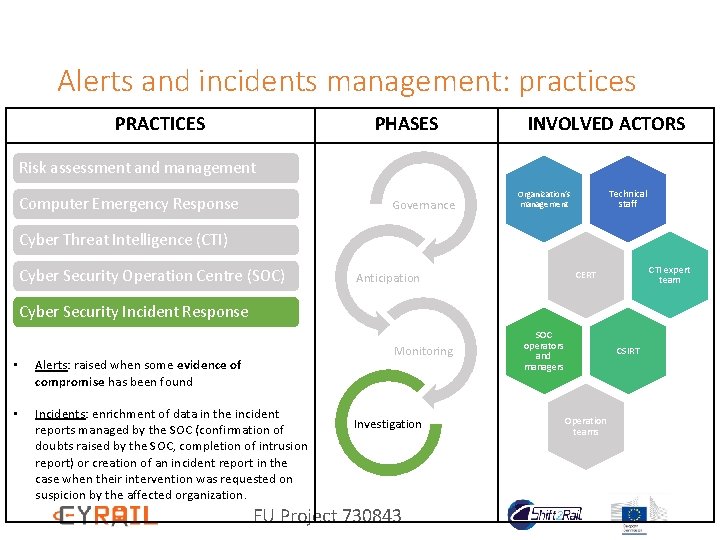
Alerts and incidents management: practices PRACTICES PHASES INVOLVED ACTORS Risk assessment and management Computer Emergency Response Governance Technical staff Organization’s management Cyber Threat Intelligence (CTI) Cyber Security Operation Centre (SOC) CTI expert team CERT Anticipation Cyber Security Incident Response Monitoring • Alerts: raised when some evidence of compromise has been found • Incidents: enrichment of data in the incident reports managed by the SOC (confirmation of doubts raised by the SOC, completion of intrusion report) or creation of an incident report in the case when their intervention was requested on suspicion by the affected organization. Investigation EU Project 730843 SOC operators and managers CSIRT Operation teams
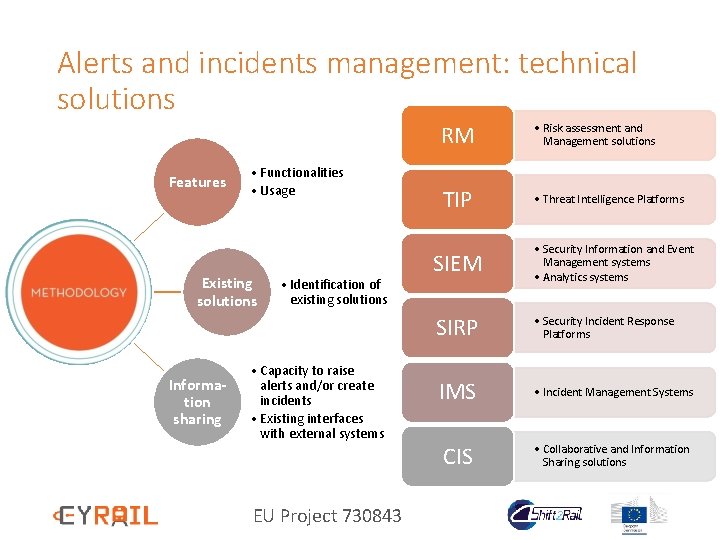
Alerts and incidents management: technical solutions Features • Functionalities • Usage Existing solutions Information sharing • Identification of existing solutions • Capacity to raise alerts and/or create incidents • Existing interfaces with external systems EU Project 730843 RM • Risk assessment and Management solutions TIP • Threat Intelligence Platforms SIEM • Security Information and Event Management systems • Analytics systems SIRP • Security Incident Response Platforms IMS • Incident Management Systems CIS • Collaborative and Information Sharing solutions

Detection strategy for CYRAIL • For each threat from the risk analysis, the detection strategy gives the list of detection means along with the list of alerts that could be raised by the alerting system. Assets Threats Detection means EU Project 730843 ALERTS
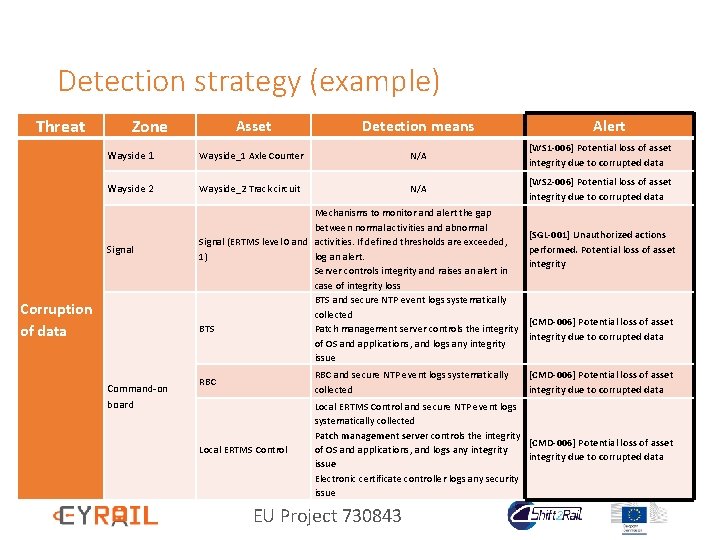
Detection strategy (example) Threat Zone Asset Detection means Wayside 1 Wayside_1 Axle Counter N/A [WS 1 -006] Potential loss of asset integrity due to corrupted data Wayside 2 Wayside_2 Track circuit N/A [WS 2 -006] Potential loss of asset integrity due to corrupted data Signal Corruption of data Command-on board Mechanisms to monitor and alert the gap between normal activities and abnormal Signal (ERTMS level 0 and activities. If defined thresholds are exceeded, 1) log an alert. Server controls integrity and raises an alert in case of integrity loss BTS and secure NTP event logs systematically collected Patch management server controls the integrity BTS of OS and applications, and logs any integrity issue Alert [SGL-001] Unauthorized actions performed. Potential loss of asset integrity [CMD-006] Potential loss of asset integrity due to corrupted data RBC and secure NTP event logs systematically collected Local ERTMS Control and secure NTP event logs systematically collected Patch management server controls the integrity [CMD-006] Potential loss of asset of OS and applications, and logs any integrity due to corrupted data issue Electronic certificate controller logs any security issue EU Project 730843 [CMD-006] Potential loss of asset integrity due to corrupted data
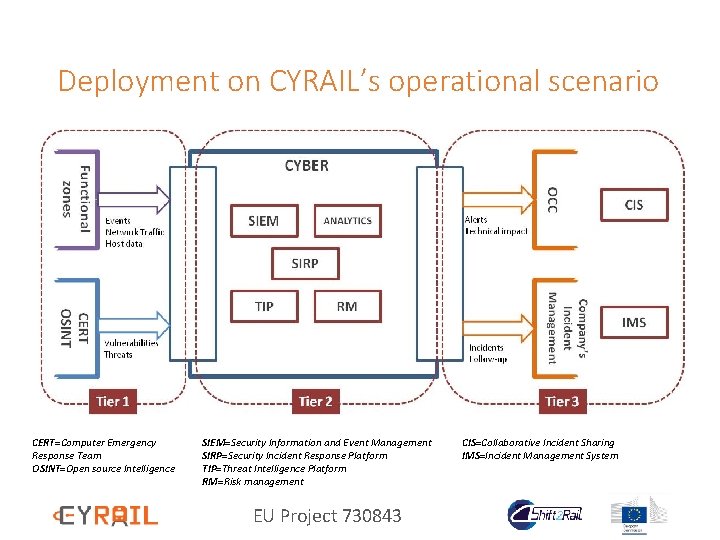
Deployment on CYRAIL’s operational scenario CERT=Computer Emergency Response Team OSINT=Open source Intelligence SIEM=Security Information and Event Management SIRP=Security Incident Response Platform TIP=Threat Intelligence Platform RM=Risk management EU Project 730843 CIS=Collaborative Incident Sharing IMS=Incident Management System
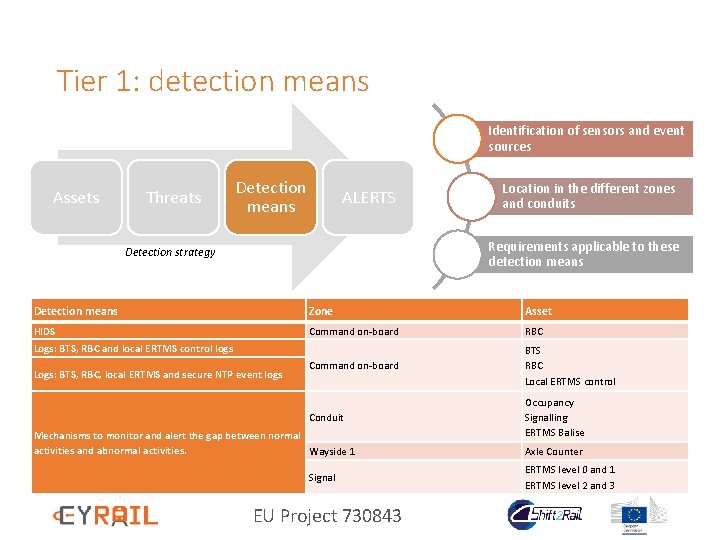
Tier 1: detection means Identification of sensors and event sources Assets Threats Detection means ALERTS Location in the different zones and conduits Requirements applicable to these detection means Detection strategy Detection means Zone Asset HIDS Command on-board RBC Command on-board BTS RBC Local ERTMS control Conduit Occupancy Signalling ERTMS Balise Logs: BTS, RBC and local ERTMS control logs Logs: BTS, RBC, local ERTMS and secure NTP event logs Mechanisms to monitor and alert the gap between normal activities and abnormal activities. Wayside 1 Signal EU Project 730843 Axle Counter ERTMS level 0 and 1 ERTMS level 2 and 3
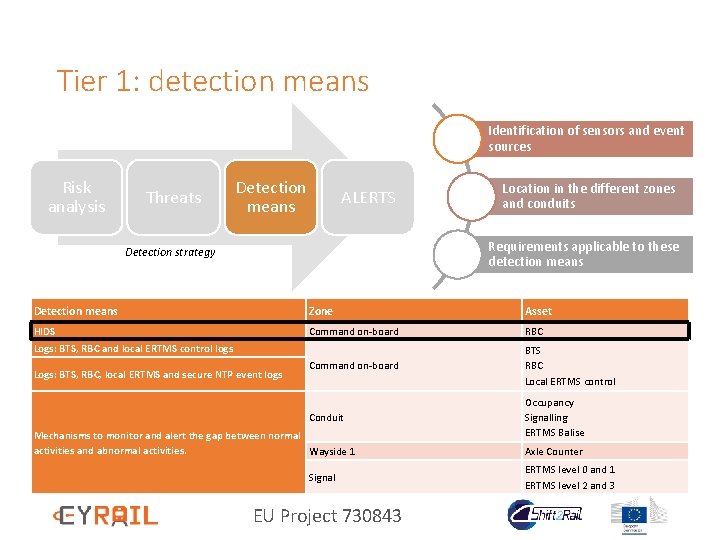
Tier 1: detection means Identification of sensors and event sources Risk analysis Threats Detection means ALERTS Location in the different zones and conduits Requirements applicable to these detection means Detection strategy Detection means Zone Asset HIDS Command on-board RBC Command on-board BTS RBC Local ERTMS control Conduit Occupancy Signalling ERTMS Balise Logs: BTS, RBC and local ERTMS control logs Logs: BTS, RBC, local ERTMS and secure NTP event logs Mechanisms to monitor and alert the gap between normal activities and abnormal activities. Wayside 1 Signal EU Project 730843 Axle Counter ERTMS level 0 and 1 ERTMS level 2 and 3
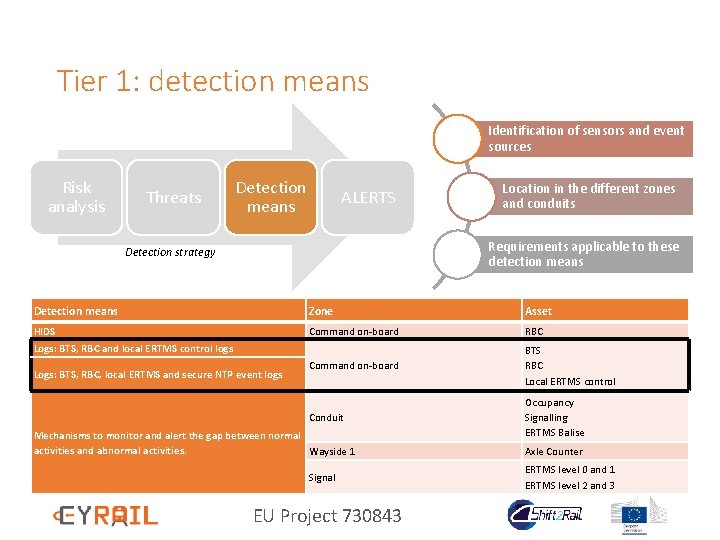
Tier 1: detection means Identification of sensors and event sources Risk analysis Threats Detection means ALERTS Location in the different zones and conduits Requirements applicable to these detection means Detection strategy Detection means Zone Asset HIDS Command on-board RBC Command on-board BTS RBC Local ERTMS control Conduit Occupancy Signalling ERTMS Balise Logs: BTS, RBC and local ERTMS control logs Logs: BTS, RBC, local ERTMS and secure NTP event logs Mechanisms to monitor and alert the gap between normal activities and abnormal activities. Wayside 1 Signal EU Project 730843 Axle Counter ERTMS level 0 and 1 ERTMS level 2 and 3
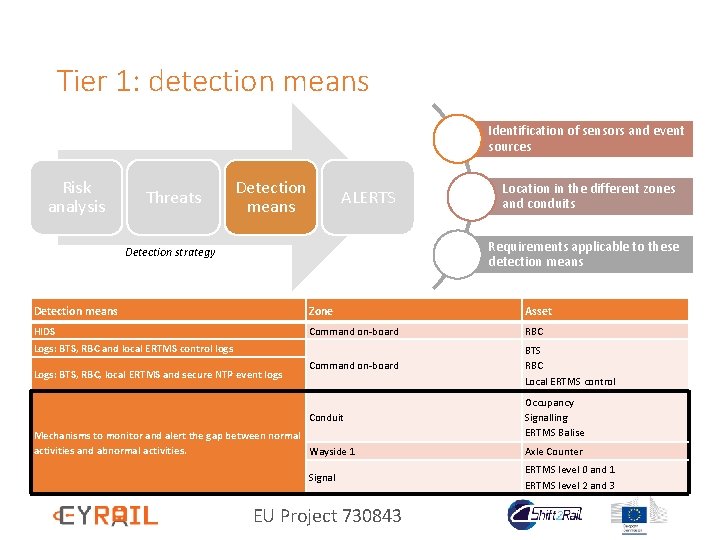
Tier 1: detection means Identification of sensors and event sources Risk analysis Threats Detection means ALERTS Location in the different zones and conduits Requirements applicable to these detection means Detection strategy Detection means Zone Asset HIDS Command on-board RBC Command on-board BTS RBC Local ERTMS control Conduit Occupancy Signalling ERTMS Balise Logs: BTS, RBC and local ERTMS control logs Logs: BTS, RBC, local ERTMS and secure NTP event logs Mechanisms to monitor and alert the gap between normal activities and abnormal activities. Wayside 1 Signal EU Project 730843 Axle Counter ERTMS level 0 and 1 ERTMS level 2 and 3
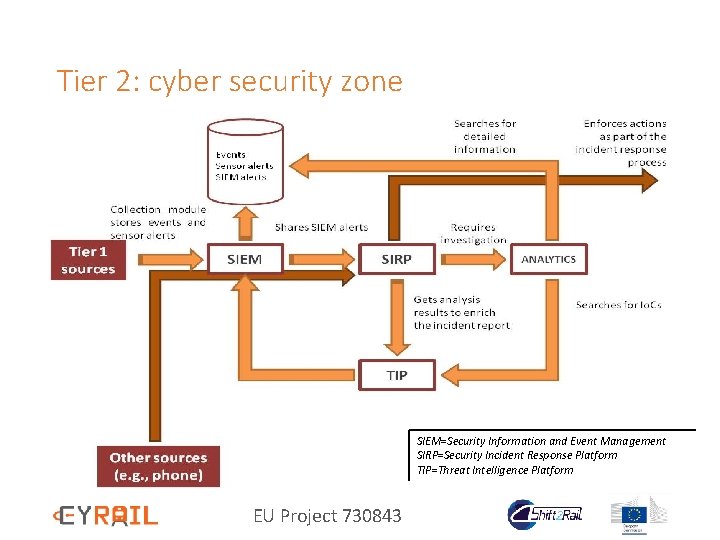
Tier 2: cyber security zone SIEM=Security Information and Event Management SIRP=Security Incident Response Platform TIP=Threat Intelligence Platform EU Project 730843
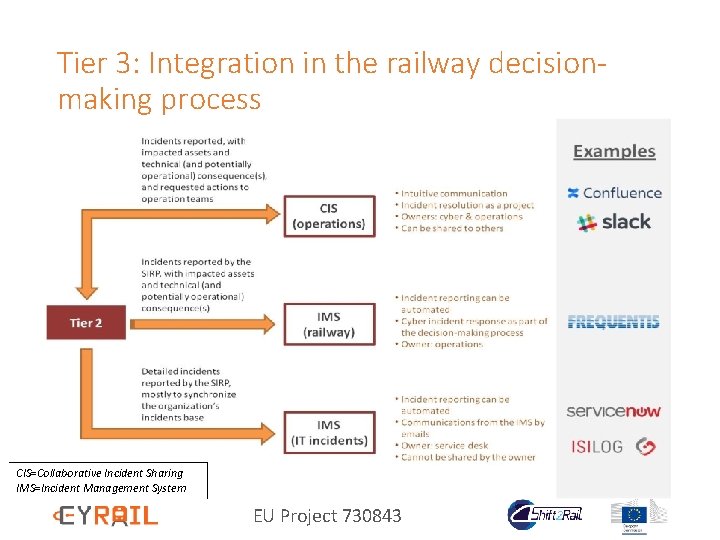
Tier 3: Integration in the railway decisionmaking process CIS=Collaborative Incident Sharing IMS=Incident Management System EU Project 730843
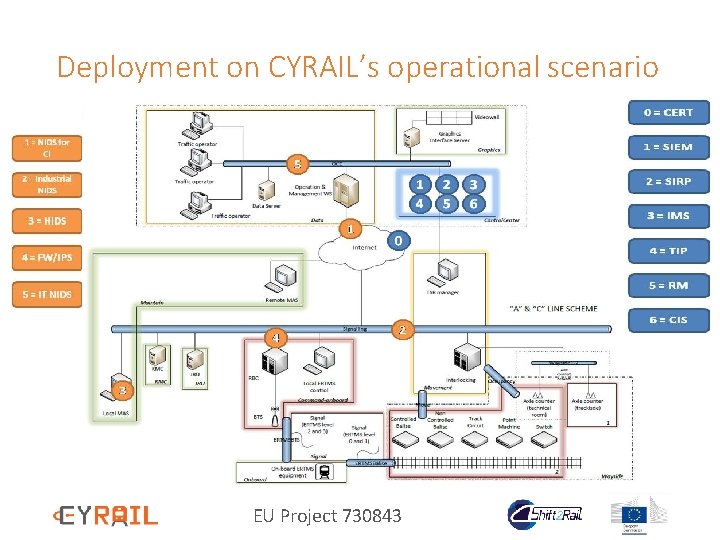
Deployment on CYRAIL’s operational scenario EU Project 730843

Video Collaborative incident management system EU Project 730843
- Slides: 21