End User Computing Control IT Audit End User







- Slides: 15

End User Computing Control IT Audit

End User Computing Control About George Kisaka Profession: Manager, Information Systems Audit - Britam Holdings (Insurance, Asset Management & Property) Ten years’ experience in Information Systems Audit & IT Project Management across the Financial, Hospitality and Manufacturing sectors) Certs o o o Certified Information Systems Auditor (CISA) Project Management Professional (PMP) ITIL v 3 Foundation MSc - IT (Information Security & Audit) BSc - Computer Science Higher Diploma Institute of Management Information Systems (IMIS) I combine the above to offer advisory and assurance services on the internal control environment to executive management and the board of directors

End User Computing Control Preamble n In IT today there are two parallel universes. In one, companies operate more effectively than ever before, powered by a rash of new technologies that tackle every aspect of financial management, from the mundane (if complex) processing of invoices and payments right up to strategic planning and long-term forecasting. n In the second universe, new technologies don't fare as well and workarounds are the order of the day. It is said that every single company uses spreadsheets for some tasks today, and this not because technologies do not exist, but because cost and integration problems pose formidable barriers to implementing new technologies. This universe could be labeled "reality. “ n This harsh reality has led knowledge workers to develop and use tools (spreadsheets, databases, macros, queries etc. ) to assist their own work. Such tools, developed,

End User Computing Control Defining End User Computing n EUCAs are developed to supplement automated systems, provide interfaces between automated systems or institute efficiencies into manual tasks, especially those of routine / mundane nature. n To the extent that they are in place, they are an extension of the IT environment and results generated from them, in assessing their impact, have an effect on the company's financial statements. n They are hidden somewhere between the automated environment as viewed by IT and the manual tasks thus get overlooked by Risk & Audit. Missing them in the annual IS audit plan makes them the weakest link in the control environment n This is compounded by the fact that their appeal, ubiquity and convenience of use often

End User Computing Control What‘s the problem n Developed & used by knowledge workers to assist their own work so they are not taken seriously and not controlled. The developers have little training in how to avoid or detect high risk defects and therefore have tremendous power to create such defects. n The programming logic and data structuring is done by “near experts” and error rates are unmeasured leading to unjustified confidence. n Key risks as a result of this include: o Misstated financial statements due to simple data entry or calculation errors in spreadsheets. o Regulatory & compliance violations (especially around maintenance of financial records).

End User Computing Control What‘s the problem (cont. ) n o Operational inefficiencies leading to loss of time, staff apathy, losses due to errors, etc. (Integrity) o Higher risk of fraud. o Lack of recovery / forensic capabilities / audit trails. o Repetitive audit findings due to lack of controls around EUCAs. o Incomplete data / program logic. (Integrity) o Insufficient training and awareness / unclear roles and responsibilities. o Challenges in implementing changes / version control. o Inadequate backup procedures (Availability) The need for robust end user computing control procedures is therefore undeniable and should form a key component of any operational risk management strategy.

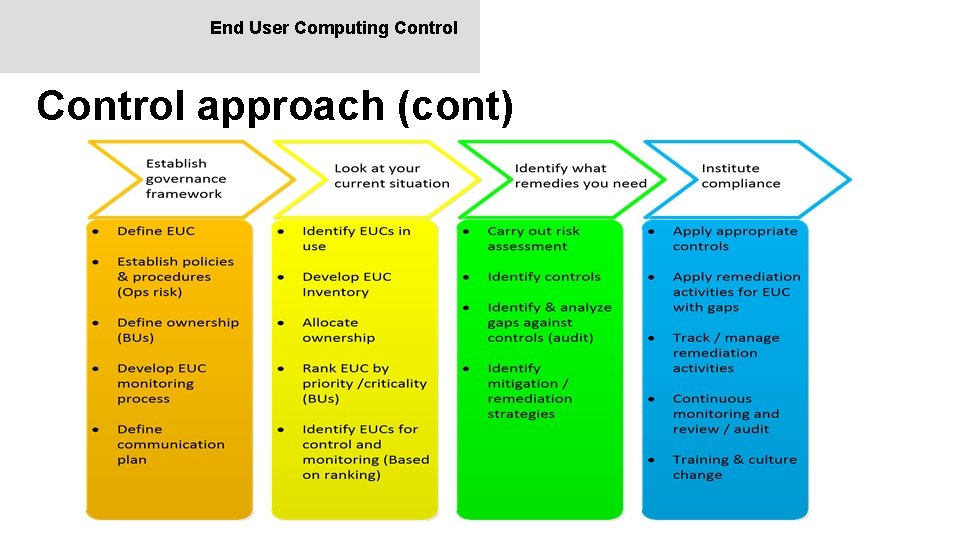
End User Computing Control approach n A holistic approach, covering the entire EUC governance to institute EUC control across the enterprise. n Need to understand the interdependencies between people, processes and technology: - n o People - The ‘human factor’, both technical & non-technical. o Processes - The many organizational activities, procedures, roles and information. o Technology – Technology, or lack thereof, is the key driver of EUCA proliferation. Common approach postulated across different industries and markets, with subtle differences. The 4 key components of the approach are: Establishing a governance framework, assessing the current situation, Identifying what remedies are need and Instituting compliance.

End User Computing Control approach (cont)

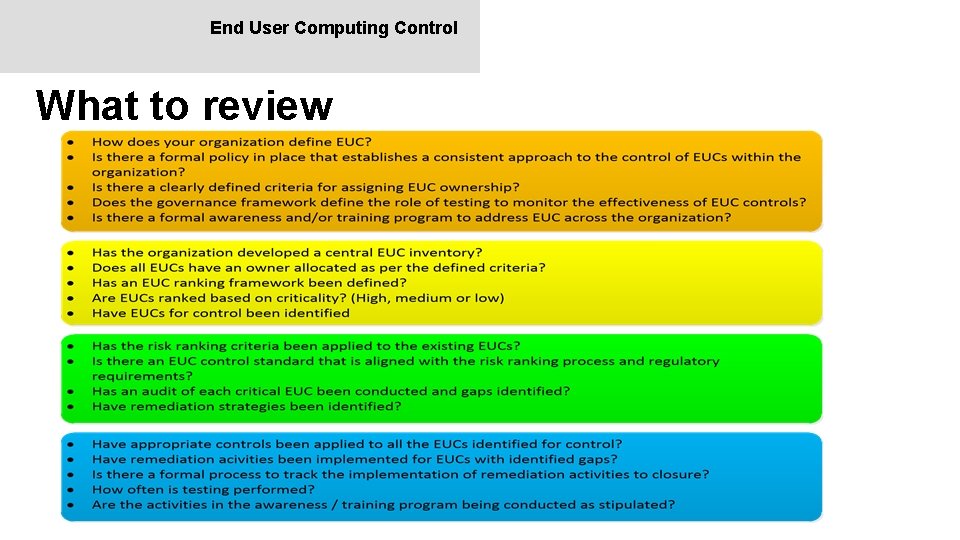
End User Computing Control What to review

End User Computing Control Sample EUC controls and audit tests Governance controls n Is there a policy governing the use of EUCAs? n Is there an up-to-date inventory of EUCAs across the enterprise? n Is there a formal process to identify and assess the risk from EUCAs? Access controls n Are the EUCA is stored in a directory with restricted access? n Is password control in place to access the EUC? n Do all users who can access the EUCA have appropriate access profiles? n Does management periodically review access rights? n Are there periodic reviews of network shares and permissions performed? n What controls are in place over data transfer mechanisms for sending EUCA data to

End User Computing Control Sample EUC controls and audit tests (cont. ) Data Integrity controls n Are the EUCAs stored in a protected directory? n Are the EUCAs stored on a shared drive on the network? n Are spreadsheet cells protected or locked where necessary? Input control n Is a reliable audit trail maintained? n What validation checks are performed on input data? n Is input data properly reconciled to its sources?

End User Computing Control Sample EUC controls and audit tests (cont. ) Version Control n What procedures are in place for managing EUCA versions? n Are old versions date stamped and saved in a clearly identified server directory? Change Control n Are proposed changes reviewed before implementation? n Are changes to the EUCA logic and data structuring logged? n Is application testing and user sign-off done place before implementing changes? n Do changes go through the same change control rigor and scrutiny as other applications under the control of IT?

End User Computing Control Sample EUC controls and audit tests (cont. ) Archival controls n Are archives properly stored? n Is access to archives granted only to authorized persons? n Are file shares considered in the DRP and / or BCP? Segregation of duties n Has the definition and implementation of roles, authorities, responsibilities over the EUC been established? n Is EUCA ownership defined? n Is there adequate segregation of duties over changes and use of the EUC? n Does the person who performs the controls over the input data have capacity to make changes to the sources?

End User Computing Control Sample EUC controls and audit tests (cont. ) Logic controls n Has the EUCA been reviewed by someone other than the author? n Are there detective controls to find errors in EUCAs used for computations? n Review the algorithms for complex spreadsheets to ensure that they work correctly (Black box & White box testing) Dissemination controls n Are the EUCAs shared outside the BU? (Must be limited as much as possible. ) n What controls are in place for EUCAs that need to be shared (password protecting, frozen formula cells, hidden cells, encryption etc. )

The end Questions?