Encryption Cryptography and Steganography An introduction to coded













- Slides: 16

Encryption, Cryptography, and Steganography: An introduction to coded communications 12/27/2021 1

Agenda • • • Introduction to Encryption Cryptography Steganography Surveillance Summary 12/27/2021 2

Encryption • The translation of information into a secret code • Typically utilizes secret keys or passwords • Security that is exercised heavily in E-Commerce transactions and authentication 12/27/2021 3

Cryptography • The science of information security • Includes analog methods: ex. microdots, merging words with images • Scrambling plaintext into ciphertext 12/27/2021 4

Example of microdots. . . From this. To this. . . 12/27/2021 Example magnified 300 X 5

Cryptography Plaintext encryption ciphertext decryption Plaintext ---------> 12/27/2021 6

Types of Cryptography • Hash Functions: no key, “digital fingerprint” of a larger document • Secret Key Cryptography (symmetric encryption): one key • Public Key Cryptography: two keys - public & private 12/27/2021 7

Use of Cryptography • Security for corporate and government information. • Privacy • Digital signatures and authentication 12/27/2021 • Currently no restrictions on use in the United States • Possible criminal use: impede investigation • Rumored to be used in recent terrorist attacks 8

Steganography • Steganography is the art of hiding a secret message inside another message. • Digital watermarking and fingerprinting of audio and video. • Not intended to replace cryptography, but supplement it. 12/27/2021 9

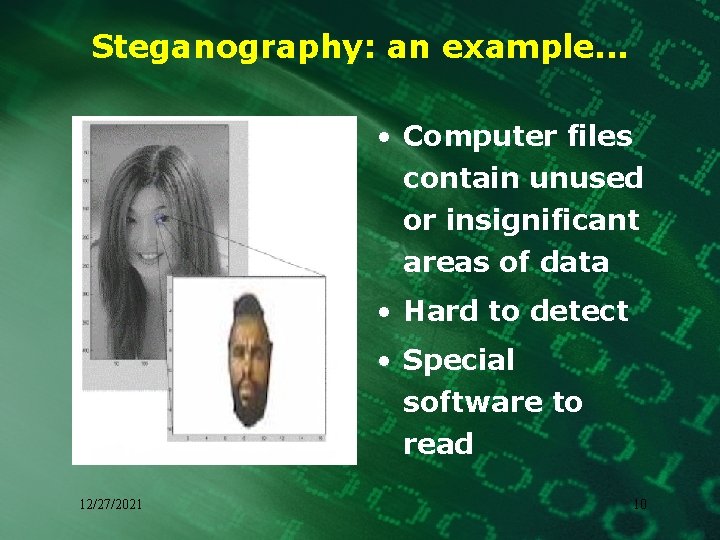
Steganography: an example. . . • Computer files contain unused or insignificant areas of data • Hard to detect • Special software to read 12/27/2021 10

Steganography: Other Examples 12/27/2021 11

FBI Methods of Policing Encryption Carnivore (DCS 1000) “Magic Lantern” 12/27/2021 12

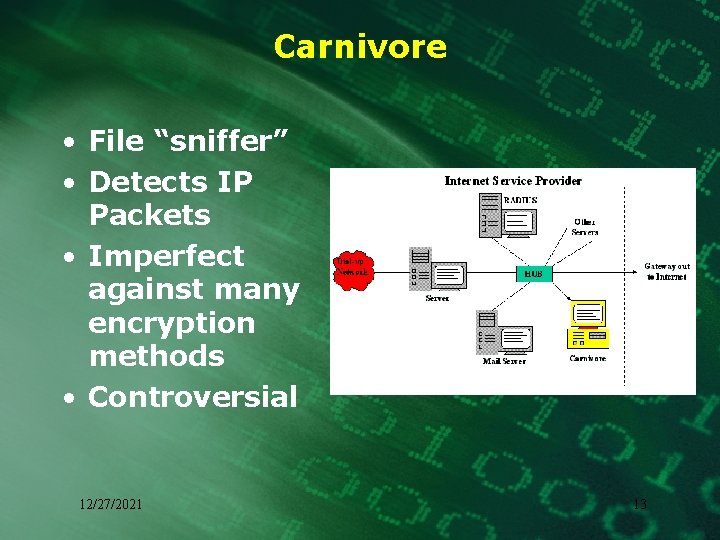
Carnivore • File “sniffer” • Detects IP Packets • Imperfect against many encryption methods • Controversial 12/27/2021 13

“Magic Lantern” • Based on Carnivore • Trojan Horse program • Installs on a suspect’s machine and obtains encryption keys • Reads keystrokes • Ethics and implementation debated 12/27/2021 14

Conclusion • Encryption currently has many legitimate and necessary uses • Government has become more concerned about its applications • Future…? 12/27/2021 15

Questions & Answers This presentation is also on the Web at: Turbokinetic. com/files. html 12/27/2021 16