Enabling Encryption for Data at Rest IBM SECURITY

Enabling Encryption for Data at Rest IBM SECURITY KEY LIFECYCLE MANAGER
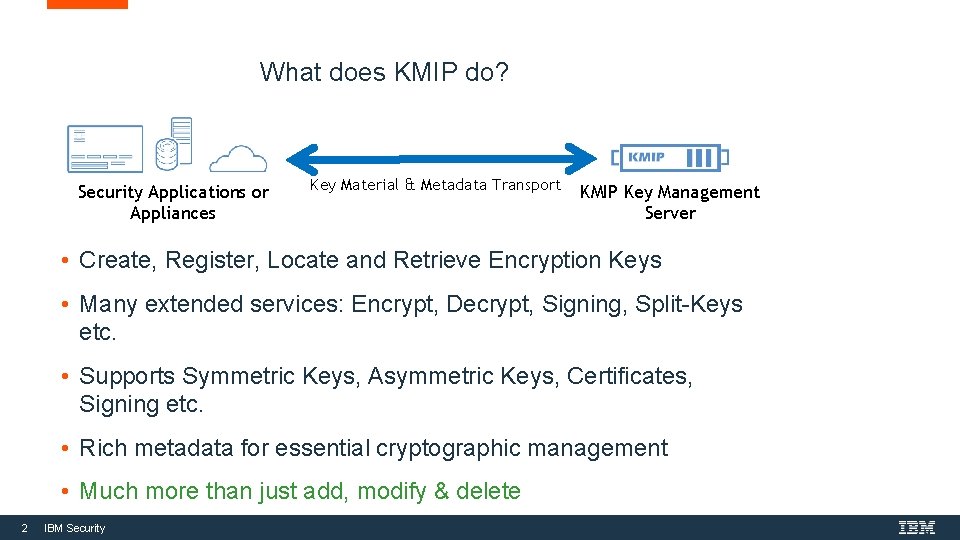
What does KMIP do? Security Applications or Appliances Key Material & Metadata Transport KMIP Key Management Server • Create, Register, Locate and Retrieve Encryption Keys • Many extended services: Encrypt, Decrypt, Signing, Split-Keys etc. • Supports Symmetric Keys, Asymmetric Keys, Certificates, Signing etc. • Rich metadata for essential cryptographic management • Much more than just add, modify & delete 2 IBM Security

KMIP 2018 RSA Interop Demonstration 3 IBM Security
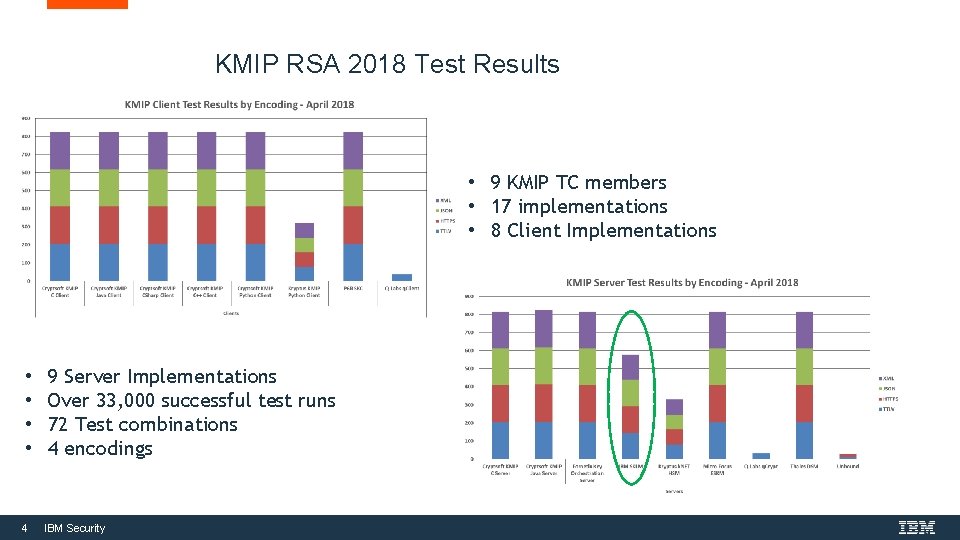
KMIP RSA 2018 Test Results • 9 KMIP TC members • 17 implementations • 8 Client Implementations • • 9 Server Implementations Over 33, 000 successful test runs 72 Test combinations 4 encodings 4 IBM Security
KMIP Deployed in Solutions 5 IBM Security

KMIP Deployed by Organizations 6 IBM Security
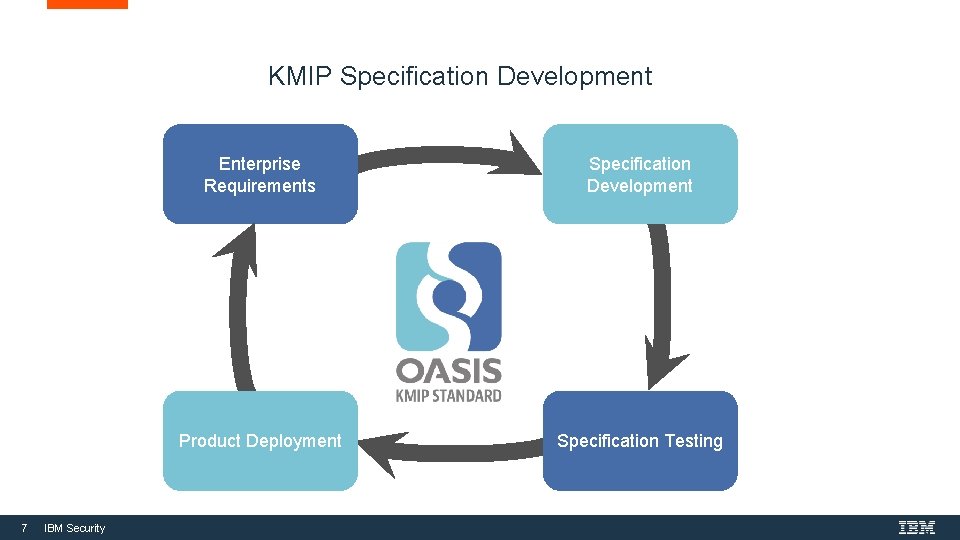
KMIP Specification Development 7 IBM Security Enterprise Requirements Specification Development Product Deployment Specification Testing
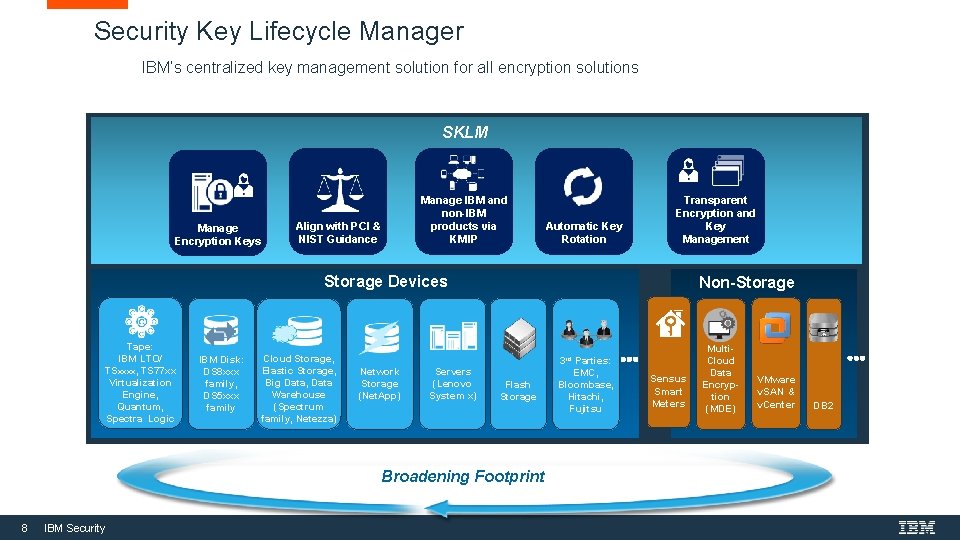
Security Key Lifecycle Manager IBM’s centralized key management solution for all encryption solutions SKLM Manage Encryption Keys Manage IBM and non-IBM products via KMIP Align with PCI & NIST Guidance Automatic Key Rotation Transparent Encryption and Key Management Storage Devices Tape: IBM LTO/ TSxxxx, TS 77 xx Virtualization Engine, Quantum, Spectra Logic IBM Disk: DS 8 xxx family, DS 5 xxx family Cloud Storage, Elastic Storage, Big Data, Data Warehouse (Spectrum family, Netezza) Network Storage (Net. App) Servers (Lenovo System x) Non-Storage Flash Storage Broadening Footprint 8 IBM Security 3 rd Parties: EMC, Bloombase, Hitachi, Fujitsu Sensus Smart Meters Multi. Cloud Data Encryption (MDE) VMware v. SAN & v. Center DB 2
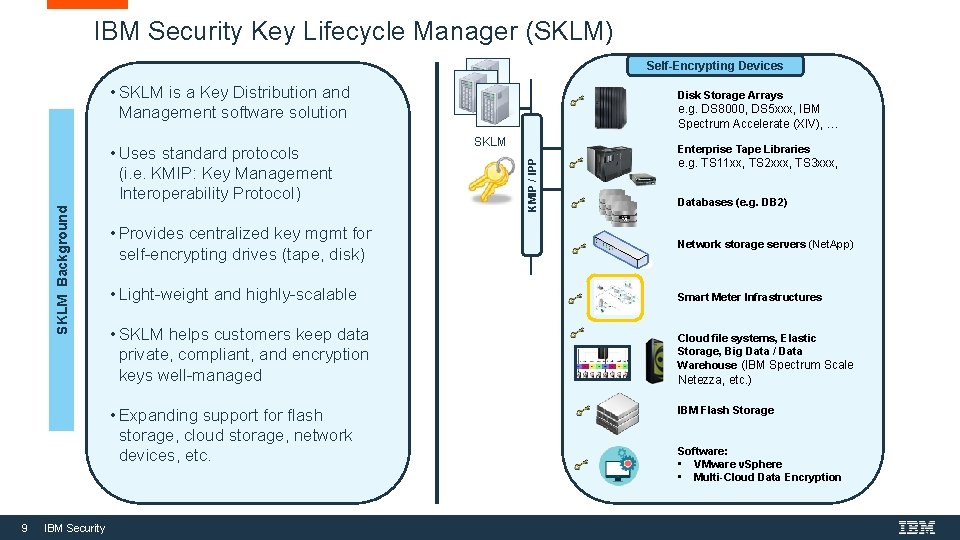
IBM Security Key Lifecycle Manager (SKLM) Self-Encrypting Devices • SKLM is a Key Distribution and Management software solution IBM Security SKLM Enterprise Tape Libraries e. g. TS 11 xx, TS 2 xxx, TS 3 xxx, Databases (e. g. DB 2) • Provides centralized key mgmt for self-encrypting drives (tape, disk) Network storage servers (Net. App) • Light-weight and highly-scalable Smart Meter Infrastructures • SKLM helps customers keep data private, compliant, and encryption keys well-managed Cloud file systems, Elastic Storage, Big Data / Data Warehouse (IBM Spectrum Scale • Expanding support for flash storage, cloud storage, network devices, etc. 9 e. g. DS 8000, DS 5 xxx, IBM Spectrum Accelerate (XIV), … KMIP / IPP SKLM Background • Uses standard protocols (i. e. KMIP: Key Management Interoperability Protocol) Disk Storage Arrays Netezza, etc. ) IBM Flash Storage Software: • VMware v. Sphere • Multi-Cloud Data Encryption
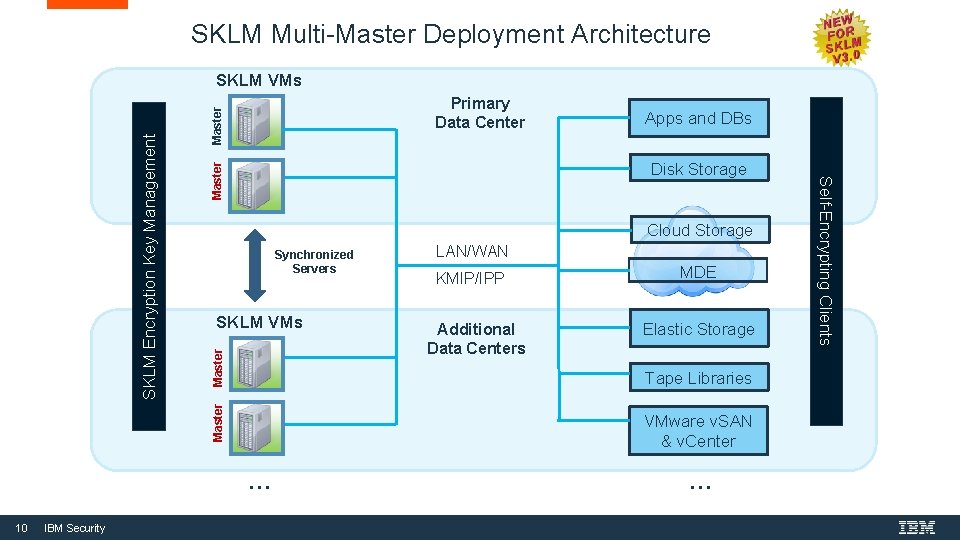
SKLM Multi-Master Deployment Architecture Master Primary Data Center Master Disk Storage Cloud Storage Synchronized Servers Master SKLM VMs Master IBM Security LAN/WAN KMIP/IPP Additional Data Centers MDE Elastic Storage Tape Libraries VMware v. SAN & v. Center … 10 Apps and DBs … Self-Encrypting Clients SKLM Encryption Key Management SKLM VMs
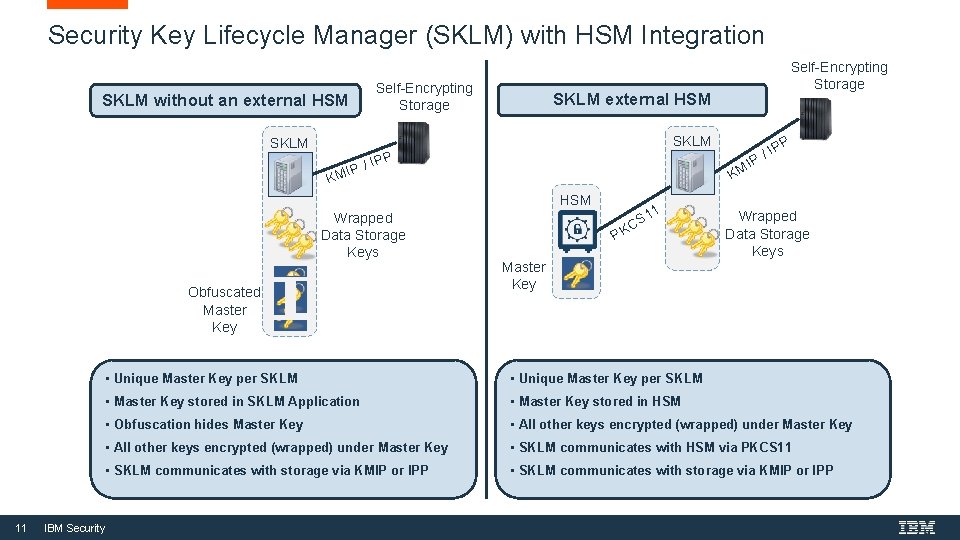
Security Key Lifecycle Manager (SKLM) with HSM Integration SKLM without an external HSM Self-Encrypting Storage SKLM external HSM SKLM IP / KM IPP Wrapped Data Storage Keys Obfuscated Master Key IPP / P I KM HSM 11 Self-Encrypting Storage 1 1 CS PK Master Key Wrapped Data Storage Keys • Unique Master Key per SKLM • Master Key stored in SKLM Application • Master Key stored in HSM • Obfuscation hides Master Key • All other keys encrypted (wrapped) under Master Key • SKLM communicates with HSM via PKCS 11 • SKLM communicates with storage via KMIP or IPP IBM Security
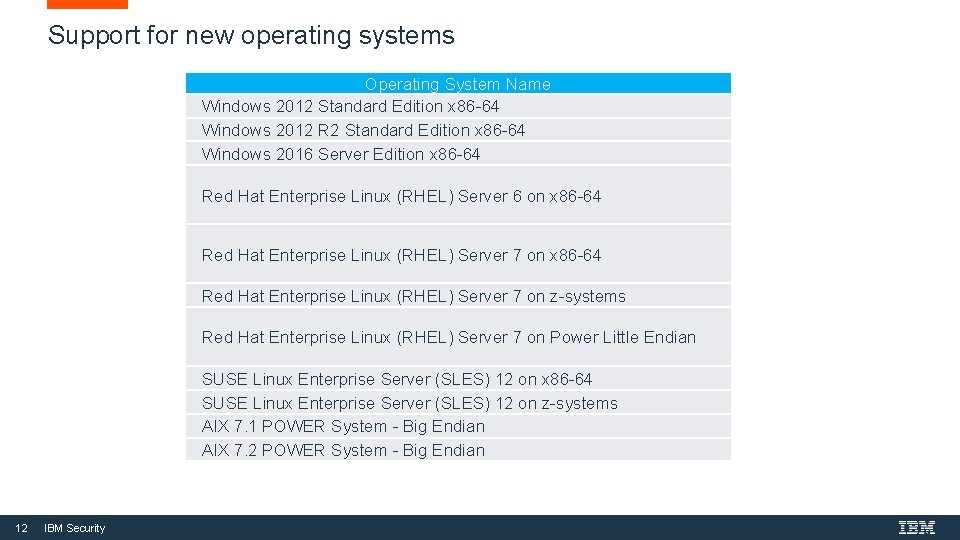
Support for new operating systems Operating System Name Windows 2012 Standard Edition x 86 -64 Windows 2012 R 2 Standard Edition x 86 -64 Windows 2016 Server Edition x 86 -64 Red Hat Enterprise Linux (RHEL) Server 6 on x 86 -64 Red Hat Enterprise Linux (RHEL) Server 7 on z-systems Red Hat Enterprise Linux (RHEL) Server 7 on Power Little Endian SUSE Linux Enterprise Server (SLES) 12 on x 86 -64 SUSE Linux Enterprise Server (SLES) 12 on z-systems AIX 7. 1 POWER System - Big Endian AIX 7. 2 POWER System - Big Endian 12 IBM Security
THANK YOU FOLLOW US ON: ibm. com/securityintelligence. com xforce. ibmcloud. com @ibmsecurity youtube/user/ibmsecuritysolutions © Copyright IBM Corporation 2017. All rights reserved. The information contained in these materials is provided for informational purposes only, and is provided AS IS without warranty of any kind, express or implied. Any statement of direction represents IBM's current intent, is subject to change or withdrawal, and represent only goals and objectives. IBM, the IBM logo, and other IBM products and services are trademarks of the International Business Machines Corporation, in the United States, other countries or both. Other company, product, or service names may be trademarks or service marks of others. Statement of Good Security Practices: IT system security involves protecting systems and information through prevention, detection and response to improper access from within and outside your enterprise. Improper access can result in information being altered, destroyed, misappropriated or misused or can result in damage to or misuse of your systems, including for use in attacks on others. No IT system or product should be considered completely secure and no single product, service or security measure can be completely effective in preventing improper use or access. IBM systems, products and services are designed to be part of a lawful, comprehensive security approach, which will necessarily involve additional operational procedures, and may require other systems, products or services to be most effective. IBM does not warrant that any systems, products or services are immune from, or will make your enterprise immune from, the malicious or illegal conduct of any party.
- Slides: 13