Emerging Database course DEVELOPMENTOF MULTILEVEL SECURE DATABASE SYSTEMS
Emerging Database course: DEVELOPMENTOF MULTILEVEL SECURE DATABASE SYSTEMS Architectures

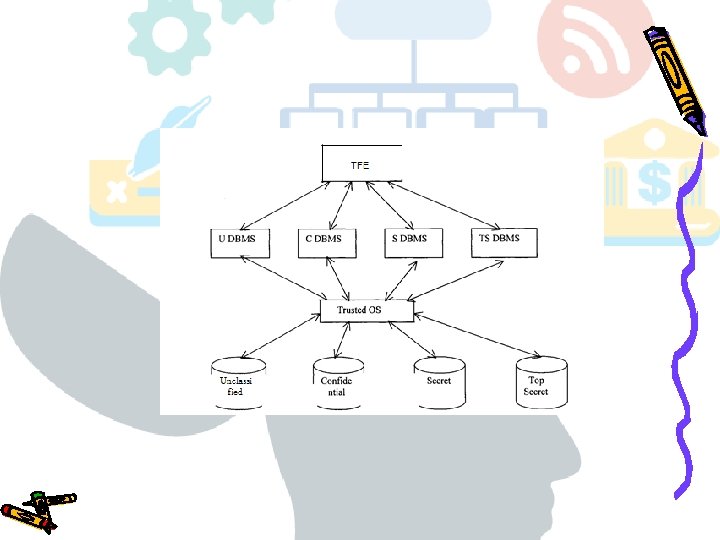
Architectures Most of the research on secure transaction processing in MLS/DBMSs can be categorized into two broad categories: one based on a kernelized architecture and the other based on a replicated architecture. Both architectures rely on the notion of trusted front end (TFE), which cannot be bypassed. In the kernelized architecture (illustrated in the following figure) a multilevel database is partitioned into a set of single-level databases, each of which stores data at one particular level. The TFE component ensures that when a subject submits a query to the system, this query is submitted to the DBMS with the same security level as the subject. By contrast, the trusted back end makes sure that the Bell and La. Padula principles are satisfied. The main drawback of the kernelized architecture is that the query execution performance greatly degrades when queries access data from multiple security levels, since data at different levels are stored separately. In contrast, the main advantage of the kernelized architecture is that the transaction scheduler can be decomposed into several untrusted schedulers, one for each security level.
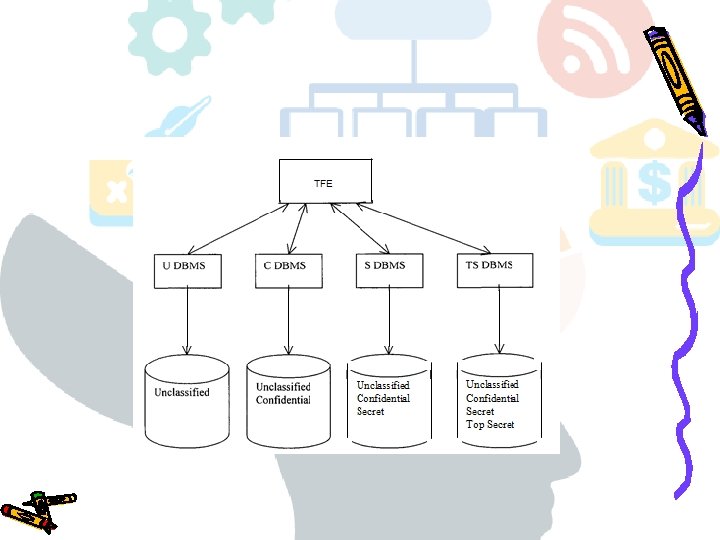
The replicated architecture, like the kernelized architecture, uses differ entdatabases to store data at different levels. For each security level, a dif ferent database exists. However, unlike the case of the kernelized architecture, the database at a security level L contains all the data which are classified either at level L or at a level lesser than L. The replicated architecture is illustrated in the following figure. In this architecture, when a transaction at a given level wishes to read data at lower levels, it will be given the replica of the lower level data stored in the database at its own security level. Although, the replicated architecture makes query execution more efficient with respect to the kernelized architecture, it suffers from several drawbacks. First, this architectures is not practical for a large number of security levels. The propagation of updates from lower to higher levels is also a critical issue. For these reasons, in the following we consider the kernelized architecture only.
REFERENCES • Timon C. Du. , Emerging Database System Architectures • Bochmann, G. Concepts for Distributed Systems Design • Capron, H. L. Computers: Tools for an Information Age
- Slides: 6