Embedding Secrets in Digital Images and Their Compression

Embedding Secrets in Digital Images and Their Compression Codes 嵌入機密訊息於數位影像及其壓縮碼之技術 Advisor: Chin-Chen Chang 1, 2 Student: Yi-Pei Hsieh 2 Dept. of Information Engineering and Computer Science, Feng Chia University 2 Dept. of Computer Science and Information Engineering, National Chung Cheng University 1 MSN lab
Motivation - data hiding (1/4) Information Sender 2021/9/25 Illegal user Public network Receiver 2
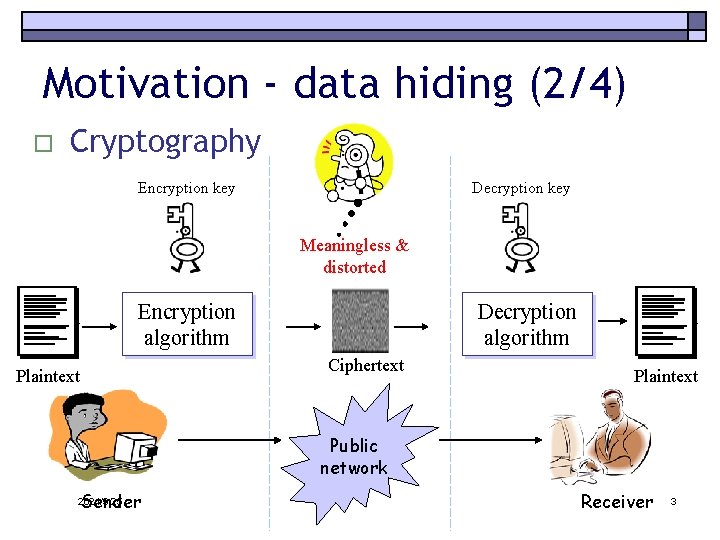
Motivation - data hiding (2/4) o Cryptography Encryption key Decryption key Meaningless & distorted Encryption algorithm Decryption algorithm Ciphertext Plaintext Public network Sender 2021/9/25 Receiver 3
Motivation - data hiding (3/4) Information Sender Public network Illegal user Information 2021/9/25 Receiver 4
Motivation - data hiding (4/4) Compressed codes: 11010110 01…. . 1011 11…. . Information Sender 2021/9/25 Public network 5 Receiver

Outline o Part I: embedding secrets into digital images n o Image hiding Part II: embedding secrets into compressed codes n Reversible hiding with high capacity in VQ domain 2021/9/25 6

Part I: embedding secrets in digital images o Image hiding: hiding multiple, relatively-large secret images into a relatively-small cover image MSN lab
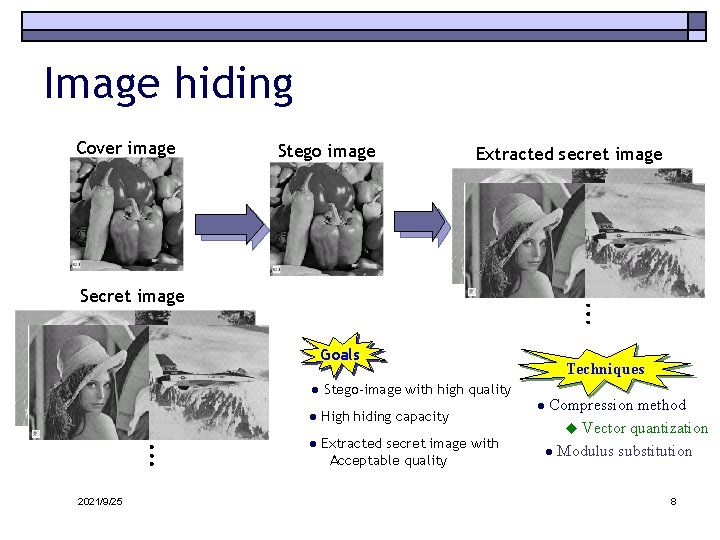
Image hiding Cover image Stego image Extracted secret image Secret image Goals ● Stego-image with high quality ● High hiding capacity ● Extracted secret image with Acceptable quality 2021/9/25 Techniques ● Compression method u Vector quantization ● Modulus substitution 8
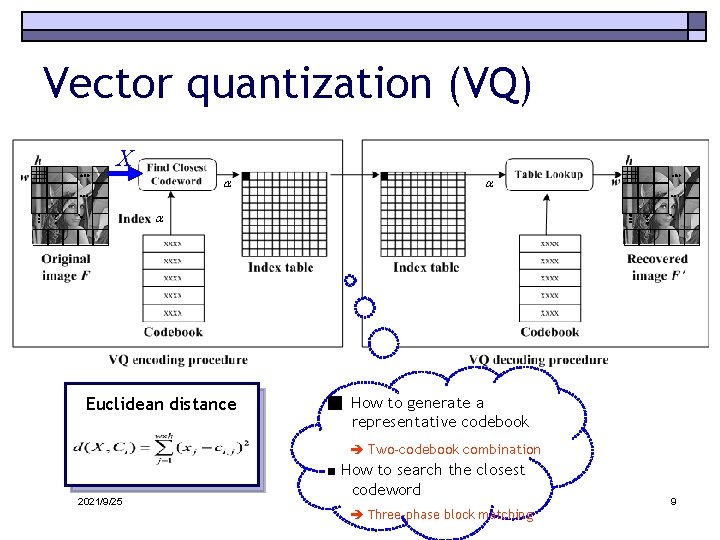
Vector quantization (VQ) X Euclidean distance ■ How to generate a representative codebook Two-codebook combination 2021/9/25 ■ How to search the closest codeword Three-phase block matching 9
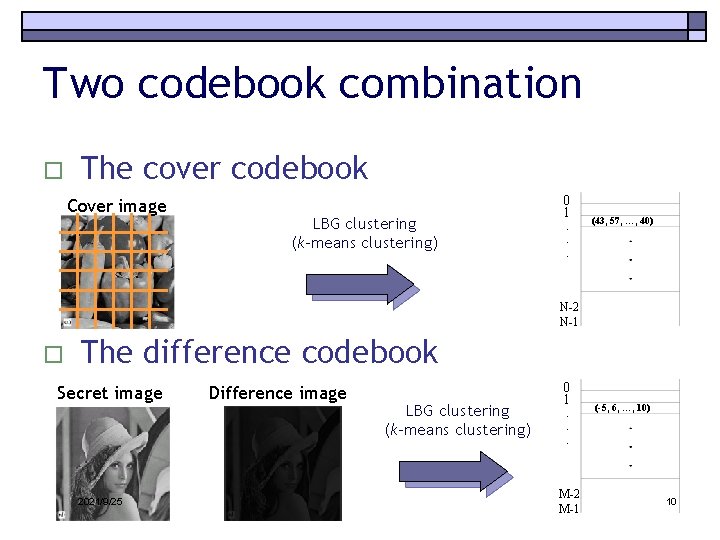
Two codebook combination o The cover codebook Cover image LBG clustering (k-means clustering) 0 1. . . (43, 57, …, 40) N-2 N-1 o The difference codebook Secret image 2021/9/25 Difference image LBG clustering (k-means clustering) 0 1. . . M-2 M-1 (-5, 6, …, 10) 10
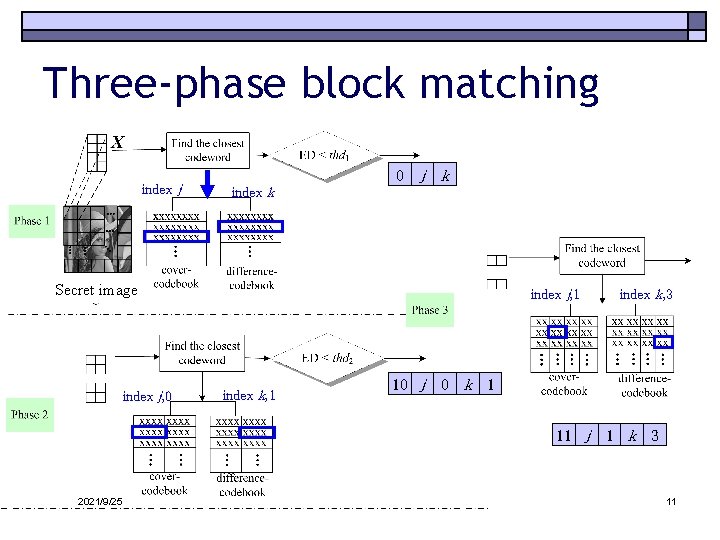
Three-phase block matching index j 0 j k index k Secret image index j, 0 index j, 1 index k, 1 10 j 0 k 1 11 j 2021/9/25 index k, 3 1 k 3 11
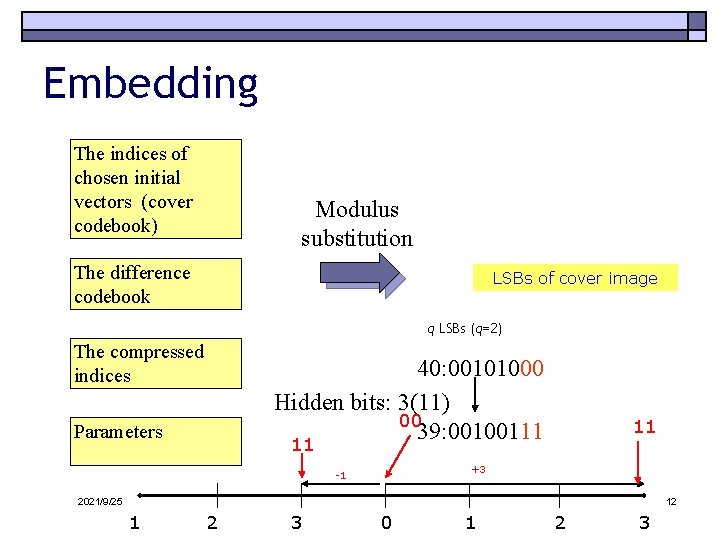
Embedding The indices of chosen initial vectors (cover codebook) Modulus substitution The difference codebook LSBs of cover image q LSBs (q=2) The compressed indices 40: 00101000 Hidden bits: 3(11) 00 39: 00100111 Parameters 11 11 +3 -1 2021/9/25 12 1 2 3 0 1 2 3
Experimental results (1/3) o Test images Baboon Tiffany Scene 2021/9/25 13 Lena Jet Pepper
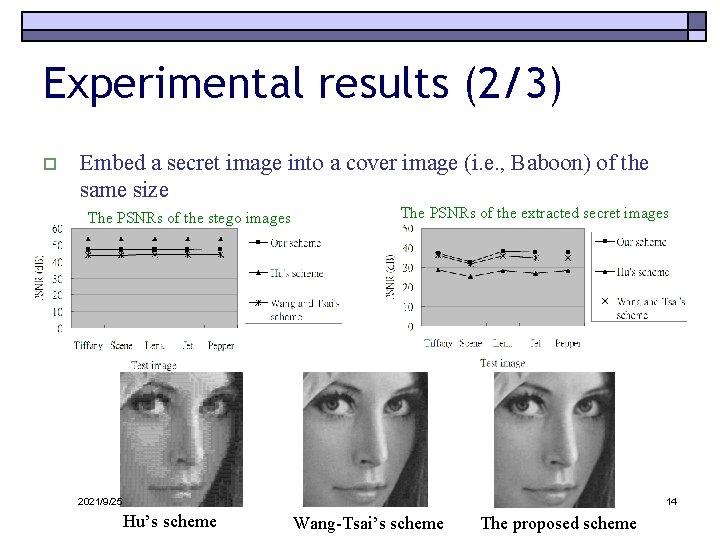
Experimental results (2/3) o Embed a secret image into a cover image (i. e. , Baboon) of the same size The PSNRs of the stego images The PSNRs of the extracted secret images 2021/9/25 14 Hu’s scheme Wang-Tsai’s scheme The proposed scheme
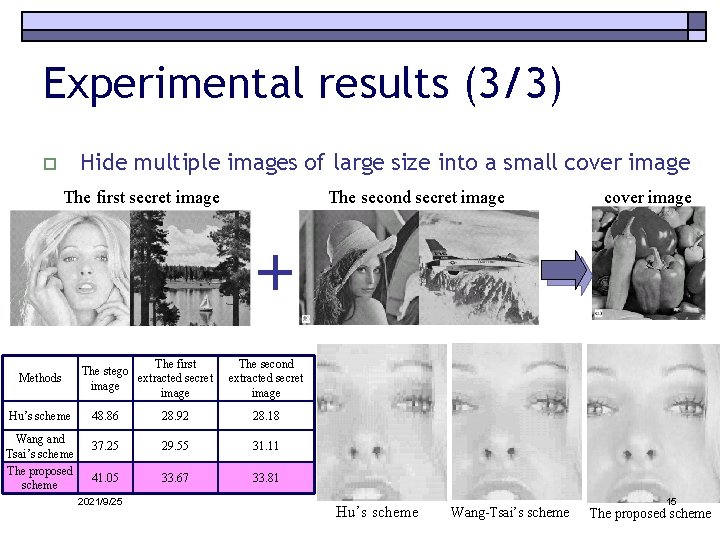
Experimental results (3/3) Hide multiple images of large size into a small cover image o The first secret image Methods Hu’s scheme Wang and Tsai’s scheme The proposed scheme The first The stego extracted secret image The second extracted secret image 48. 86 28. 92 28. 18 37. 25 29. 55 31. 11 41. 05 33. 67 33. 81 2021/9/25 cover image Hu’s scheme Wang-Tsai’s scheme 15 The proposed scheme
Part II: embedding secrets in compressed codes o Reversible data embedding with high embedding capacity MSN lab
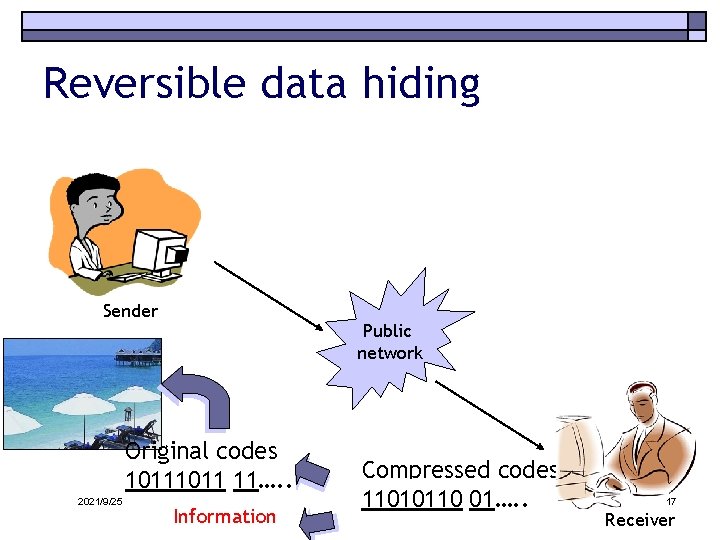
Reversible data hiding Sender Public network Original codes 1011 11…. . 2021/9/25 Information Compressed codes: 11010110 1011 01…. . 11…. . 17 Receiver

Reversible data hiding o o The similarity property of adjacent areas Declustering n o Put dissimilar codewords into the same cluster Embedding n Cartesian product 2021/9/25 18
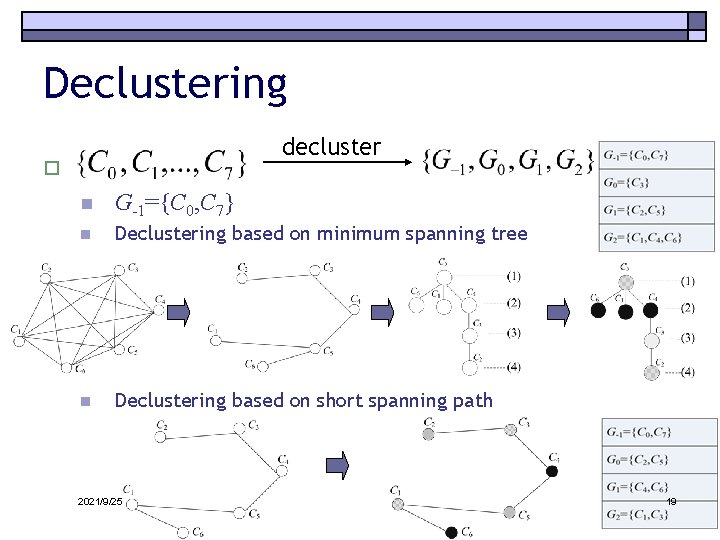
Declustering decluster o n G-1={C 0, C 7} n Declustering based on minimum spanning tree n Declustering based on short spanning path 2021/9/25 19
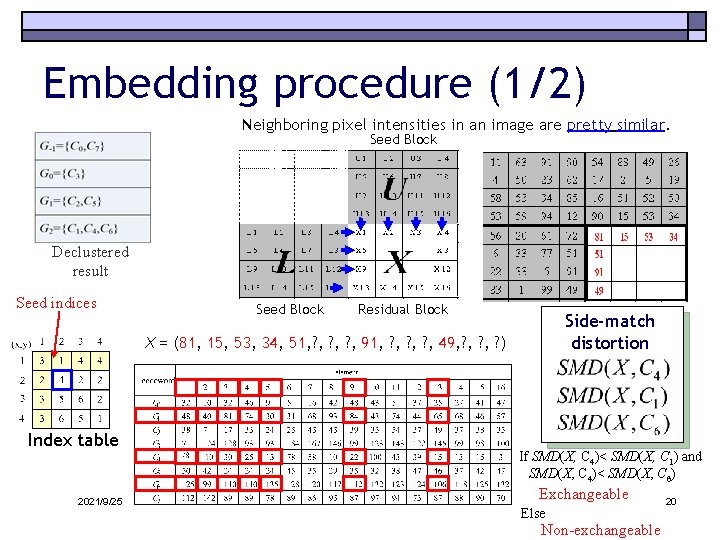
Embedding procedure (1/2) Neighboring pixel intensities in an image are pretty similar. Seed Block Declustered result Seed indices Seed Block Residual Block Side-match distortion X = (81, 15, 53, 34, 51, ? , ? , 91, ? , ? , 49, ? , ? ) Index table 2021/9/25 If SMD(X, C 4)< SMD(X, C 1) and SMD(X, C 4)< SMD(X, C 6) Exchangeable Else Non-exchangeable 20
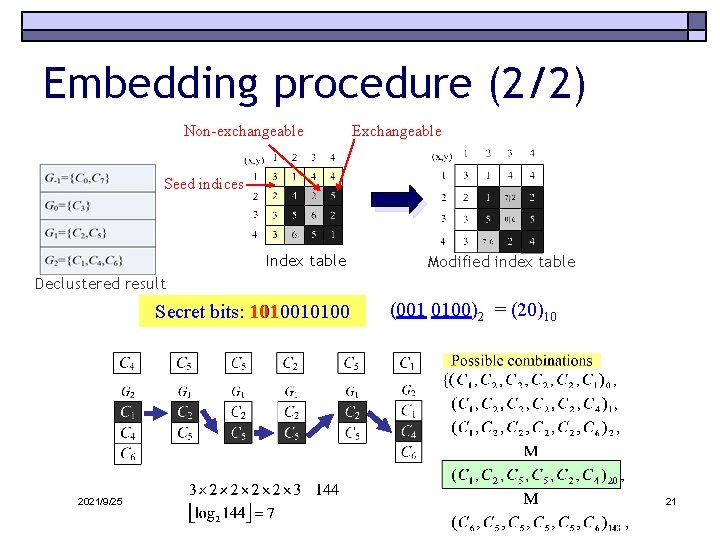
Embedding procedure (2/2) Non-exchangeable Exchangeable Seed indices Index table Modified index table Declustered result Secret bits: 1010010100 2021/9/25 (001 0100)2 = (20)10 21
Experimental results (1/9) o 512× 512 test images Baboon Barbara Boat 2021/9/25 22 Lena Pepper Tiffany
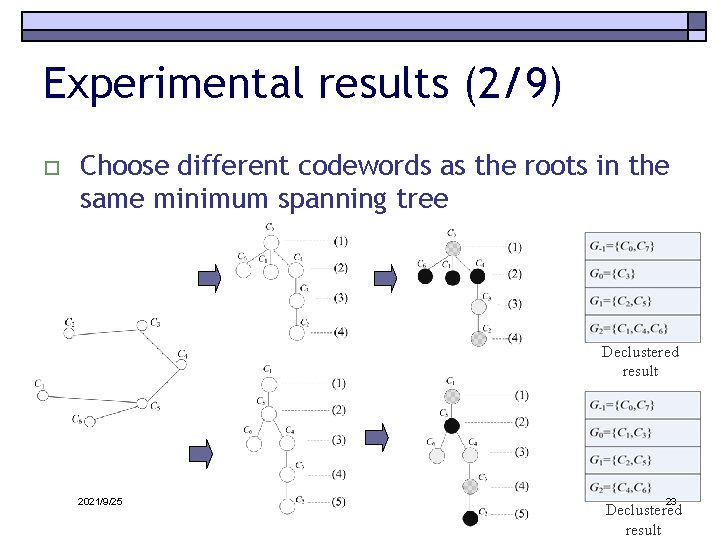
Experimental results (2/9) o Choose different codewords as the roots in the same minimum spanning tree Declustered result 2021/9/25 23 Declustered result
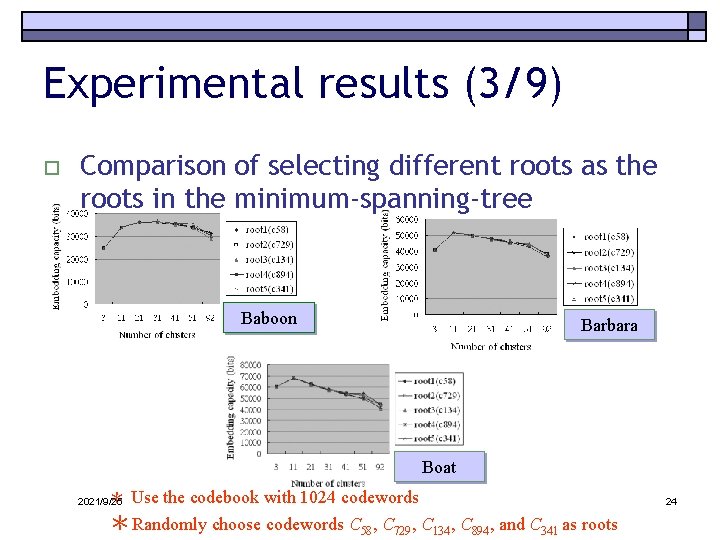
Experimental results (3/9) o Comparison of selecting different roots as the roots in the minimum-spanning-tree Baboon Barbara Boat * Use the codebook with 1024 codewords 2021/9/25 *Randomly choose codewords C 58, C 729, C 134, C 894, and C 341 as roots 24
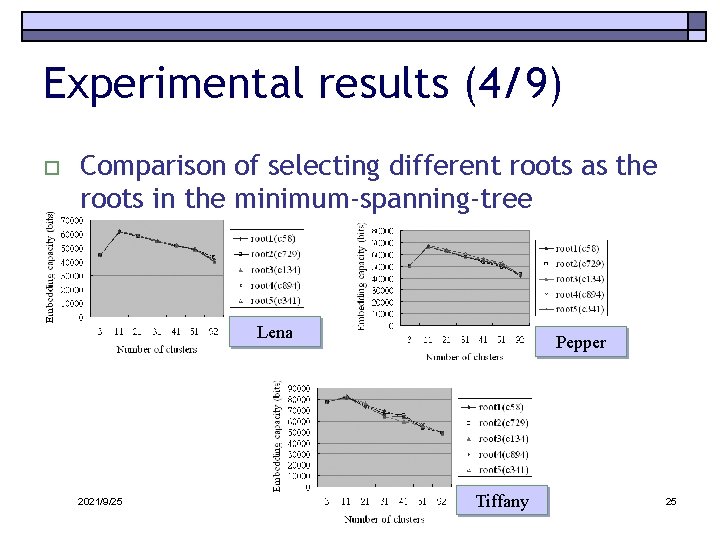
Experimental results (4/9) o Comparison of selecting different roots as the roots in the minimum-spanning-tree Lena 2021/9/25 Pepper Tiffany 25
Experimental results (5/9) o Declustering n n The minimum-spanning-tree algorithm The short-spanning-path algorithm 2021/9/25 26
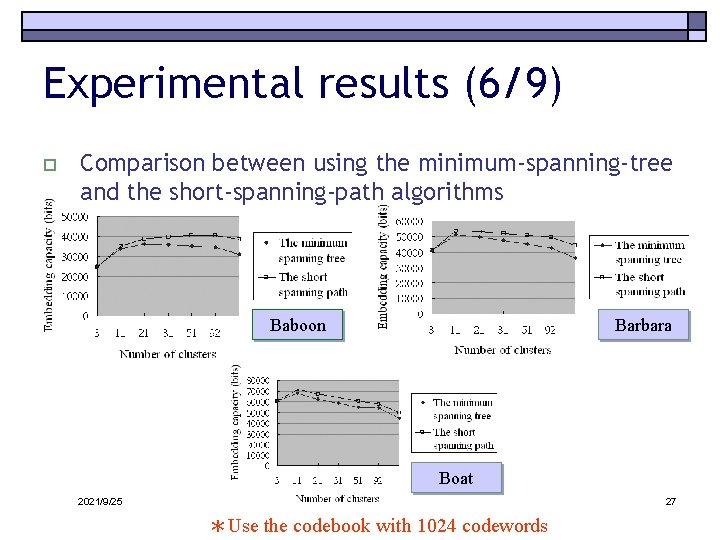
Experimental results (6/9) o Comparison between using the minimum-spanning-tree and the short-spanning-path algorithms Baboon Barbara Boat 2021/9/25 27 *Use the codebook with 1024 codewords
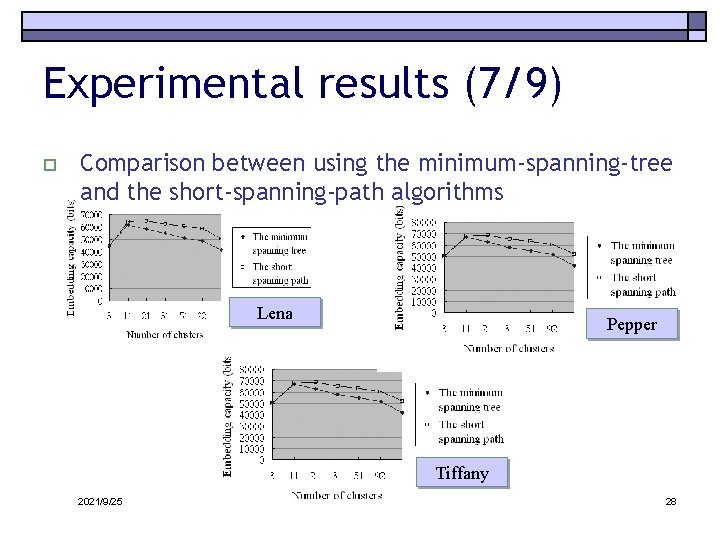
Experimental results (7/9) o Comparison between using the minimum-spanning-tree and the short-spanning-path algorithms Lena Pepper Tiffany 2021/9/25 28
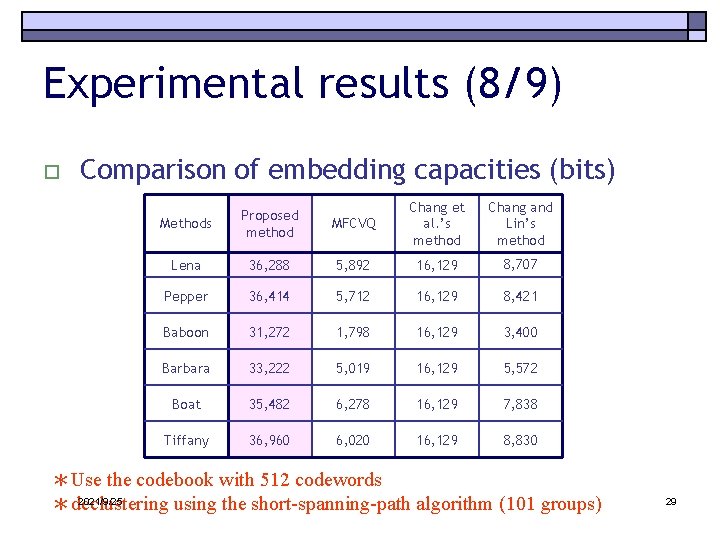
Experimental results (8/9) o Comparison of embedding capacities (bits) MFCVQ Chang et al. ’s method Chang and Lin’s method 36, 288 5, 892 16, 129 8, 707 Pepper 36, 414 5, 712 16, 129 8, 421 Baboon 31, 272 1, 798 16, 129 3, 400 Barbara 33, 222 5, 019 16, 129 5, 572 Boat 35, 482 6, 278 16, 129 7, 838 Tiffany 36, 960 6, 020 16, 129 8, 830 Methods Proposed method Lena *Use the codebook with 512 codewords 2021/9/25 *declustering using the short-spanning-path algorithm (101 groups) 29
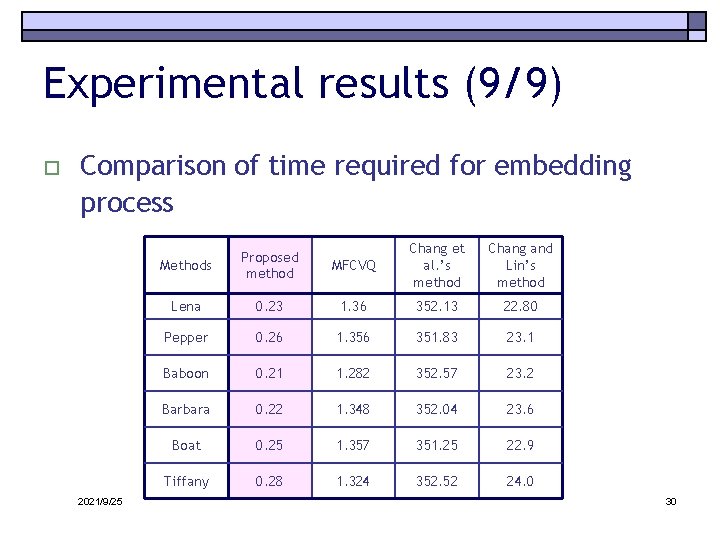
Experimental results (9/9) o Comparison of time required for embedding process 2021/9/25 MFCVQ Chang et al. ’s method Chang and Lin’s method 0. 23 1. 36 352. 13 22. 80 Pepper 0. 26 1. 356 351. 83 23. 1 Baboon 0. 21 1. 282 352. 57 23. 2 Barbara 0. 22 1. 348 352. 04 23. 6 Boat 0. 25 1. 357 351. 25 22. 9 Tiffany 0. 28 1. 324 352. 52 24. 0 Methods Proposed method Lena 30

Conclusions o To hide multiple, relatively-large secret images into a relatively-small cover image n o We have proposed an image hiding method with twocodebook combination and three-phase block matching To develop a reversible hiding with high capacity for VQ domain n n We have proposed two declustering methods We have applied the similarity property of adjacent areas in a natural image and Cartesian product 2021/9/25 31

Future Research Directions (1/2) o Reversible data hiding n n n o Restore the Original cover images after extracting the secret data Need no extra data Enhance the embedding capacity Design the data hiding methods to other image formats n Binary and color images 2021/9/25 32

Future Research Directions (2/2) o Develop the hiding schemes using other compressed codes n JPEG, JPEG 2000, and BTC (block truncation coding) compressed codes 2021/9/25 33
Thanks for your attention. . . MSN lab

2021/9/25 35
- Slides: 35