Email ynliuguet edu cn http www scholat comlyn
































- Slides: 56

数据发布中的隐私保护技术 刘忆宁 E-mail: ynliu@guet. edu. cn 主页:http: //www. scholat. com/lyn 7311












E-voting using ZKP n n n Yining Liu, Peiyong Sun, Jihong Yan, et al. An Improved Electronic Voting Scheme without a Trusted Random Number Generator, Inscrypt’ 2011, LNCS 7537, pp. 93 -101. (中国� 算机学会、中国密� 学会推荐会� ) Yining Liu, Wei Guo, Chi Cheng, Ching. Fang Hsu, Junyan Qian, Changlu Lin. A Robust Electronic Voting Scheme Against Side Channel Attack. Journal of Information Science and Engineering, vol. 32, no. 6, pp. 1471 -1486, 2016. (中国密� 学会推荐C� 期刊) Yining Liu, Quanyu Zhao. E-Voting Scheme Using Secret Sharing and KAnonymity. World Wide Web: Internet and Web Information Systems. DOI: 10. 1007/s 11280 -018 -0575 -0, 2018. (中国� 算机学会推 荐B� 期刊)

被引用情况 • 2017年 9月被图灵奖获得者R. L. Rivest教授收入专著《 Software Independence Revisited》。





E-voting 的攻击模型 n n 攻击模型包括潜信道攻击(Subliminal Channel Attack)、侧信道攻击(Side Channel Attack)。 在“Advances in Cryptographic Voting Systems”中 有如下一段话,刻画了投票协议中的信任模型与 攻击模型。 We assume that all voters are potential adversaries when it comes to coercion. We note that, in any scheme, a voter may take a photo of her ballot using a camera-phone: in Hong Kong in 2004, mainland Chinese residents were asked by authorities to have their relatives mail them camera-phone pictures of their ballot. This is the side-channel attack

Bingo Voting n n http: //en. wikipedia. org/wiki/Bingo_voting “Bingo voting: secure and coercion-free voting using a trusted random number generator, ” in Proc. VOTE-ID 2007, vol. 4896, LNCS, pp. 111 - 124. “Enhancing electronic voting machines on the example of Bingo voting, ” IEEE Transactions on Information Forensics and Security, vol. 4, pp. 745 -750, 2009. “Improving and Analysing Bingo Voting”, Ph. D thesis, University of the State of Baden-Wuerttemberg, 2012.

主要的 具 n n n Pedersen’s Commitment Zero Knowledge Proof Secret Sharing

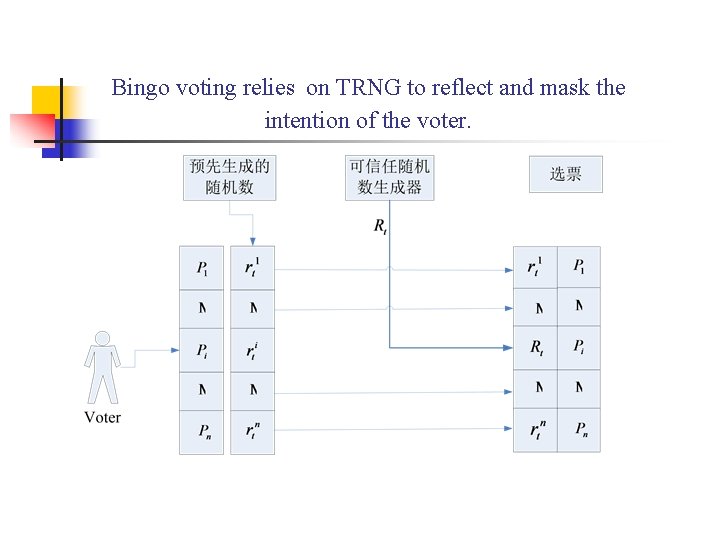
Bingo voting relies on TRNG to reflect and mask the intention of the voter.

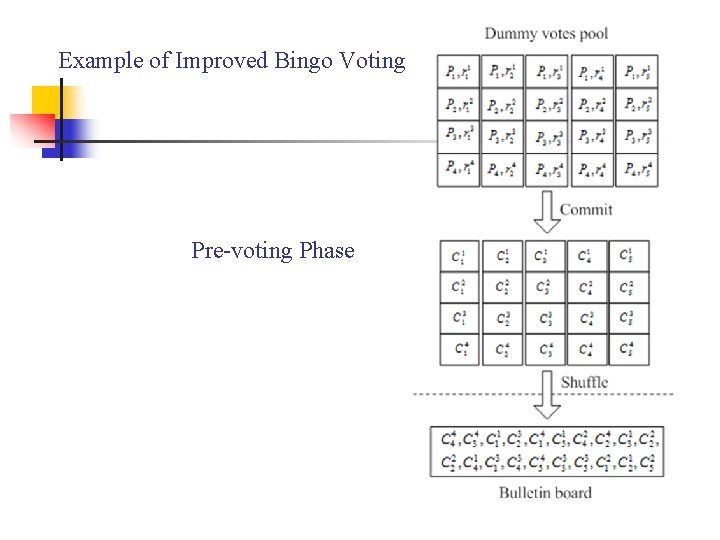
Example of Improved Bingo Voting Pre-voting Phase

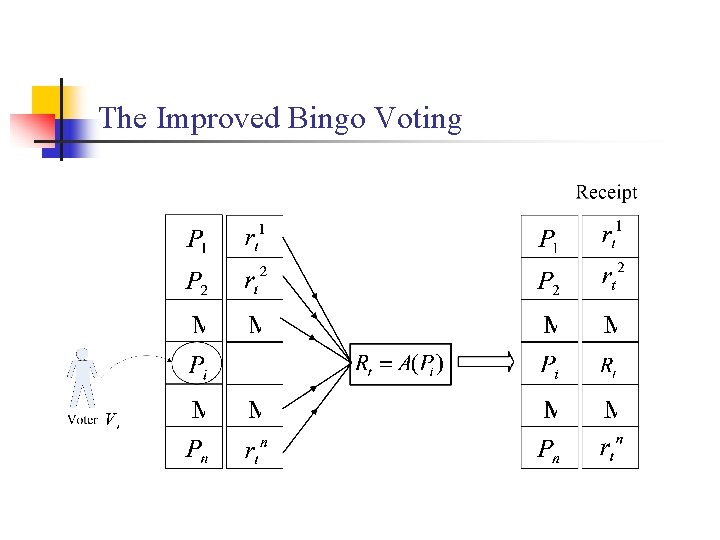
The Improved Bingo Voting

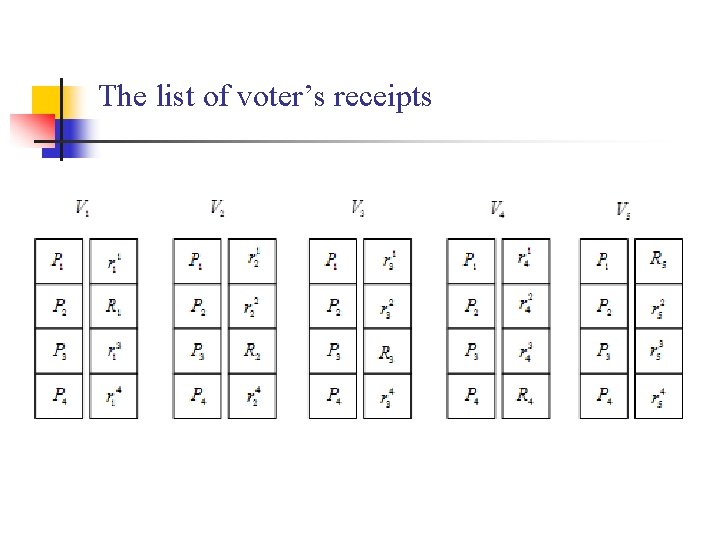
The list of voter’s receipts

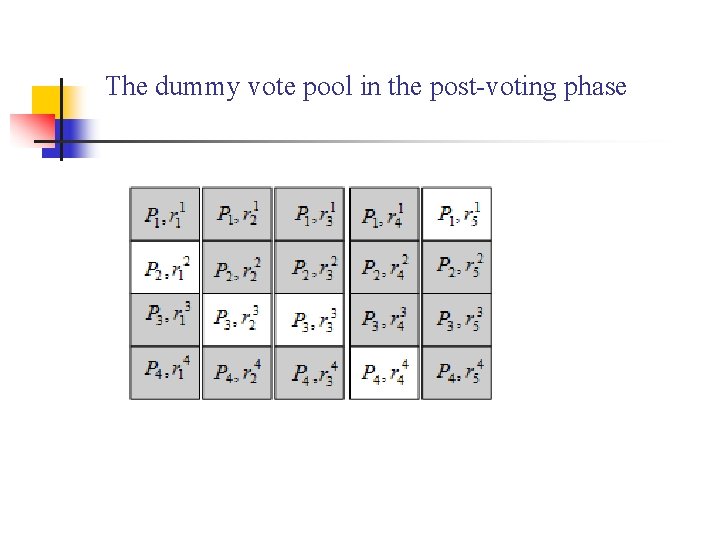
The dummy vote pool in the post-voting phase

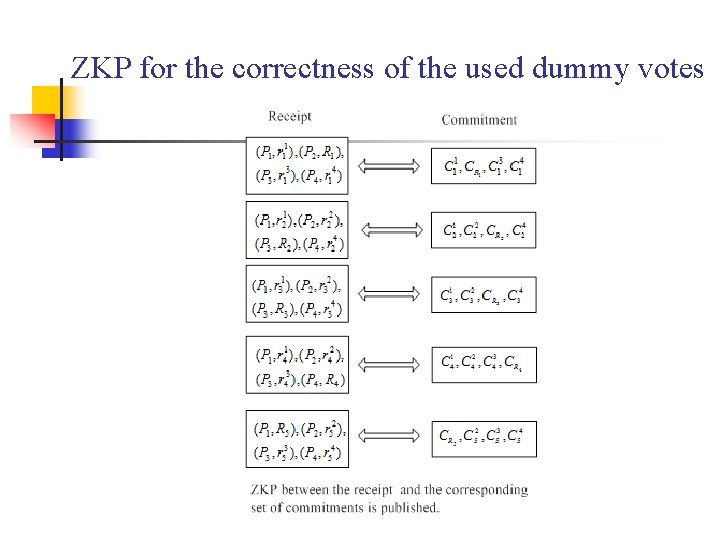
ZKP for the correctness of the used dummy votes

数据聚合研究 n n n Yining Liu, Gao Liu, Chi Cheng, Zhe Xia, Jian Shen. A Privacy. Preserving Health Data Aggregation Scheme, KSII Transactions on Internet and Information Systems. Vol. 10, no. 8, pp. 3852 -3864, 2016. Yining Liu, Wei Guo, Chun-I Fan, Liang Chang, Chi Cheng. A Practical Privacy-Preserving Data Aggregation (3 PDA) Scheme for Smart Grid, IEEE Transactions on Industrial Informatics, DOI: 10. 1109/TII. 2018. 2809672, 2018. Jingcheng Song, Yining Liu, Jun Shao, Chunming Tang. A Dynamic Membership Data Aggregation (DMDA) Protocol for Smart Grid. Submitted to IEEE Systems Journal (Minor revision)


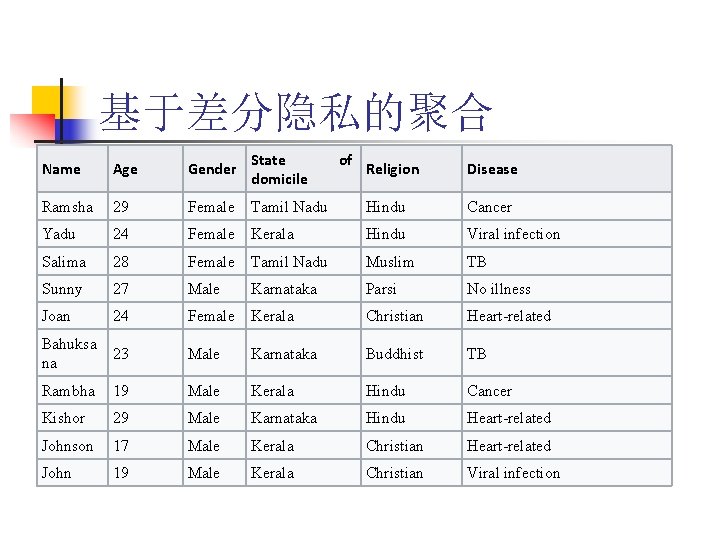
基于差分隐私的聚合 Name Age Gender State domicile Ramsha 29 Female Yadu 24 Salima of Religion Disease Tamil Nadu Hindu Cancer Female Kerala Hindu Viral infection 28 Female Tamil Nadu Muslim TB Sunny 27 Male Karnataka Parsi No illness Joan 24 Female Kerala Christian Heart-related Bahuksa 23 na Male Karnataka Buddhist TB Rambha 19 Male Kerala Hindu Cancer Kishor 29 Male Karnataka Hindu Heart-related Johnson 17 Male Kerala Christian Heart-related John 19 Male Kerala Christian Viral infection

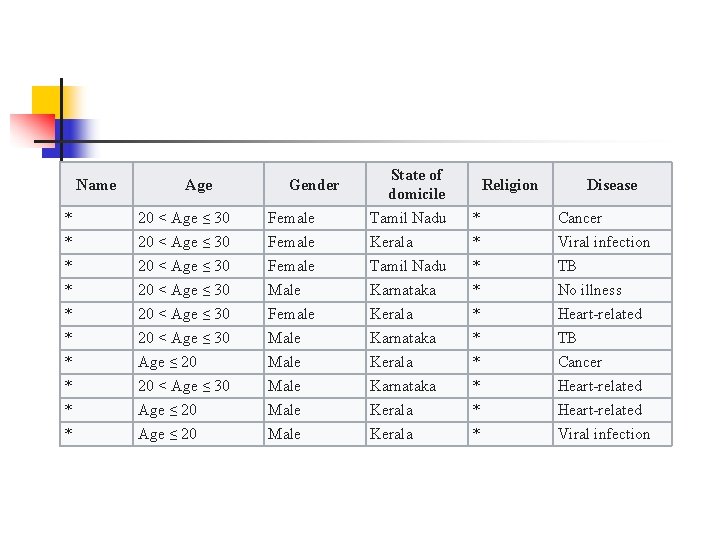
Name Age Gender State of domicile Religion Disease * 20 < Age ≤ 30 Female Tamil Nadu * Cancer * 20 < Age ≤ 30 Female Kerala * Viral infection * 20 < Age ≤ 30 Female Tamil Nadu * TB * 20 < Age ≤ 30 Male Karnataka * No illness * 20 < Age ≤ 30 Female Kerala * Heart-related * 20 < Age ≤ 30 Male Karnataka * TB * Age ≤ 20 Male Kerala * Cancer * 20 < Age ≤ 30 Male Karnataka * Heart-related * Age ≤ 20 Male Kerala * Viral infection




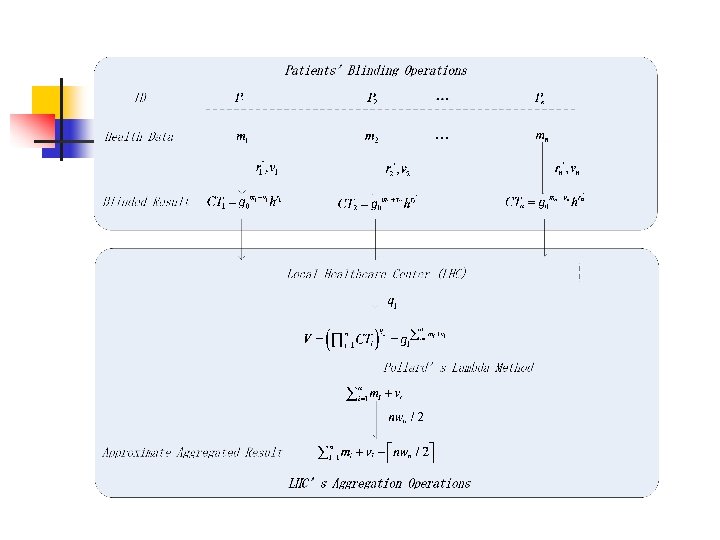
n n 基于差分� 私的数据聚合 A Privacy-Preserving Health Data Aggregation Scheme, KSII Transactions on Internet and Information Systems. Vol. 10, no. 8, pp. 3852 -3864, 2016.

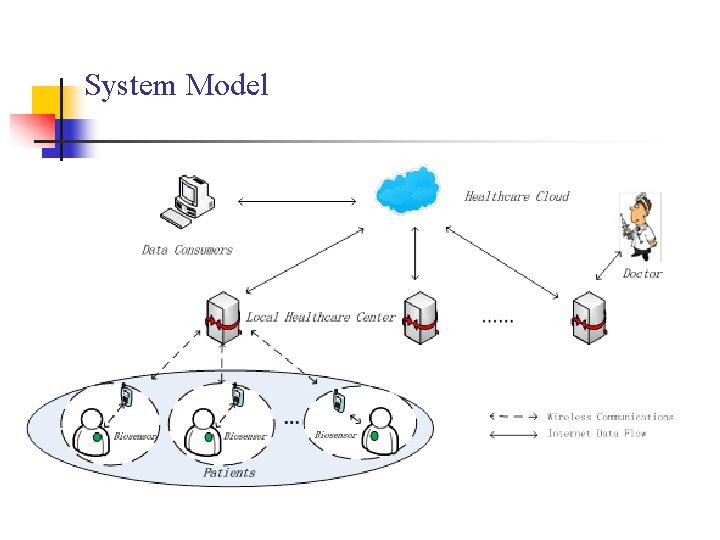
System Model

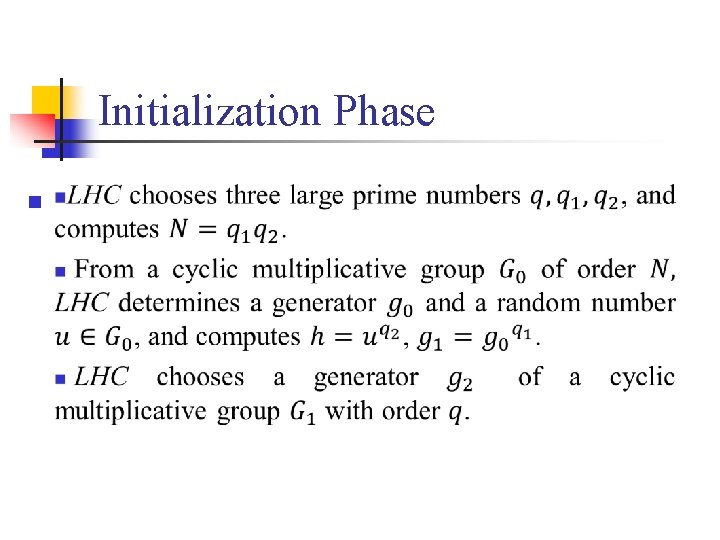
Initialization Phase n

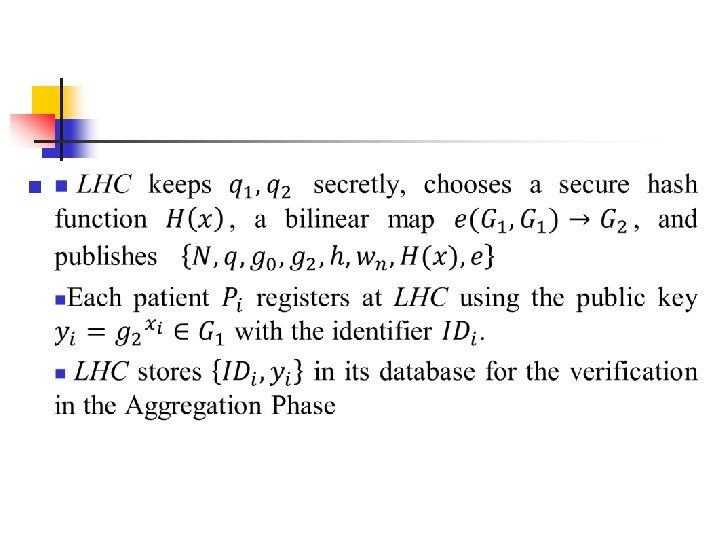
n

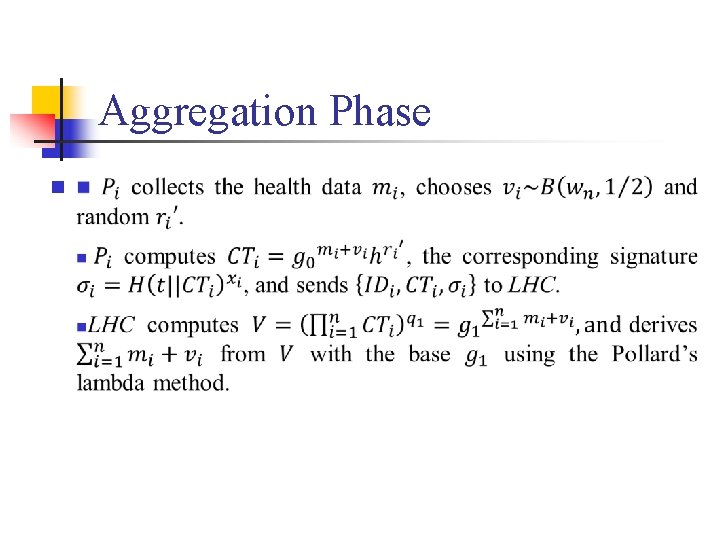
Aggregation Phase n


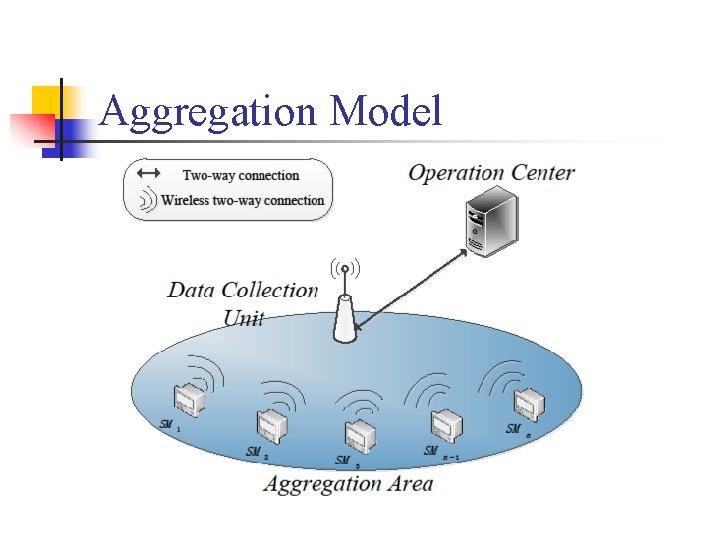
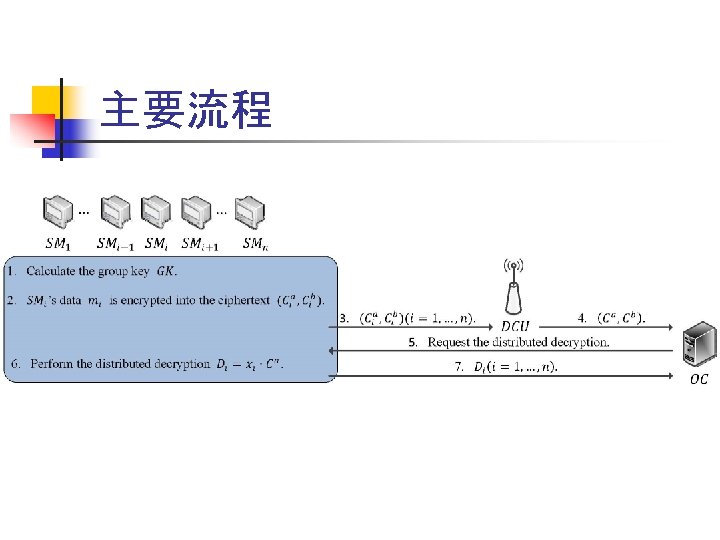
n n 基于虚� 聚合域的数据聚合 A Practical Privacy-Preserving Data Aggregation (3 PDA) Scheme for Smart Grid, IEEE Transactions on Industrial Informatics, DOI: 10. 1109/TII. 2018. 2809672

Aggregation Model


主要 具 n n n Lifted El. Gamal encryption system Pollard's lambda algorithm Batch verification of short signatures


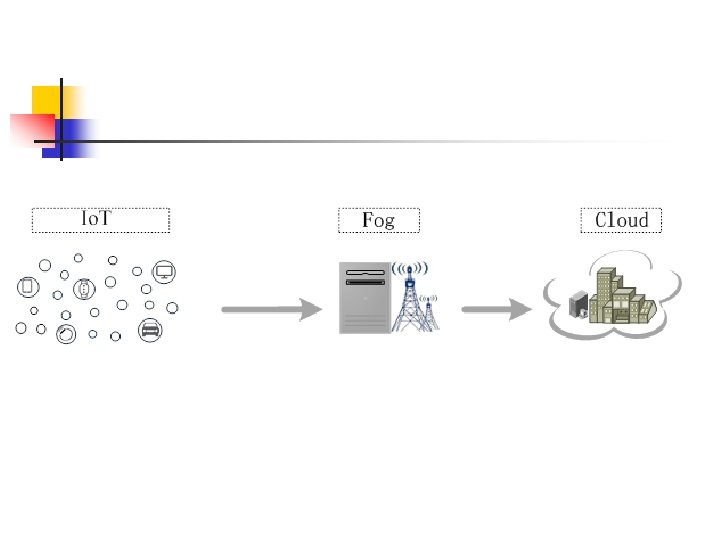
保持原始性的数据收集协议 n n Privacy-preserving data collection for mobile phone sensing tasks. ISPEC 2018. LNCS 11125, pp. 506 -518, 2018. Privacy-preserving raw data collection without trusted authority for Io. T. Accepted by Computer Networks.





使用的 具: n n n Blind signature Shuffle DDH Assumption

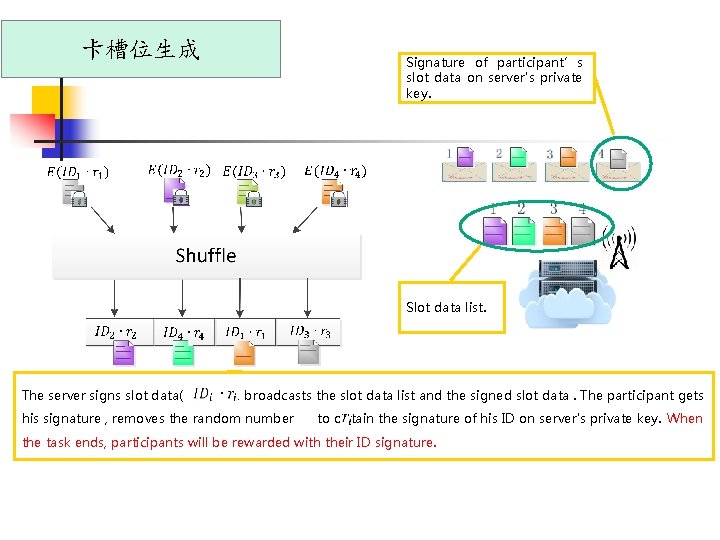
卡槽位生成 Signature of participant’s slot data on server's private key. Slot data list. The server signs slot data( ), broadcasts the slot data list and the signed slot data. The participant gets his signature , removes the random number to obtain the signature of his ID on server's private key. When the task ends, participants will be rewarded with their ID signature.

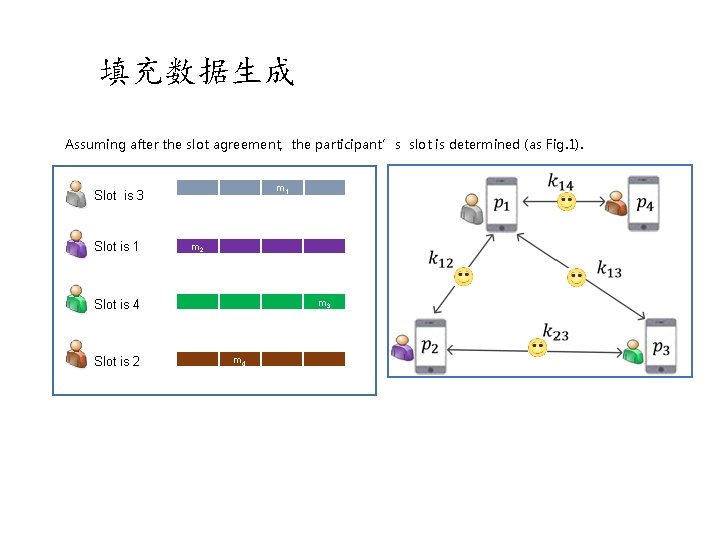
填充数据生成 Assuming after the slot agreement, the participant’s slot is determined (as Fig. 1). m 1 Slot is 3 Slot is 1 m 2 m 3 Slot is 4 Slot is 2 m 4

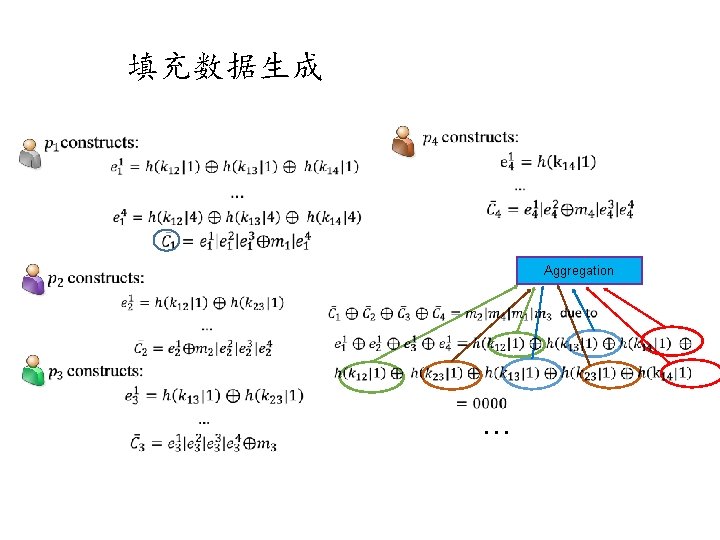
填充数据生成 Aggregation …

