Email Security SMIME 1 IT 352 Network Security












- Slides: 22

Email Security SMIME 1 IT 352 | Network Security |Najwa Al. Ghamdi

Email Protocol Overview 1. Simple Mail Transfer Protocol (SMTP) – It is an Internet standard for e-mail transmission across Internet Protocol (IP) networks. – Through this protocol , a mail sender communicates with a mail receiver by issuing command strings and supplying necessary data over a TCP connection. 2 IT 352 | Network Security |Najwa Al. Ghamdi

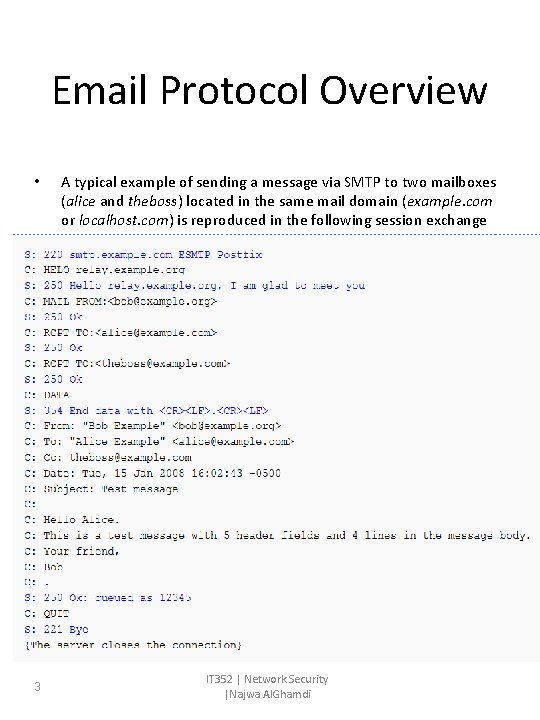
Email Protocol Overview • 3 A typical example of sending a message via SMTP to two mailboxes (alice and theboss) located in the same mail domain (example. com or localhost. com) is reproduced in the following session exchange IT 352 | Network Security |Najwa Al. Ghamdi

Email Protocol Overview SMTP Drawbacks 1. SMTP cannot transmit text data that includes national language characters because these are represented by 8 -bit codes with values of 128 decimal or higher, and SMTP is limited to 7 -bit ASCII. 2. SMTP servers may reject mail message over a certain size. 3. SMTP gateways that translate between ASCII to EBCDIC suffer translation problems. 4 IT 352 | Network Security |Najwa Al. Ghamdi

Email Protocol Overview 2. Multipurpose Internet Mail Extensions (MIME) – is an Internet standard that extends the format of email to support: 1. Text in character sets other than ASCII 2. Non-text attachments 3. Message bodies with multiple parts • MIME's use has grown beyond describing the content of email to describe content type in general including for the web. • SMTP/MIME email l Email is transmitted via SMTP in MIME format. 5 IT 352 | Network Security |Najwa Al. Ghamdi

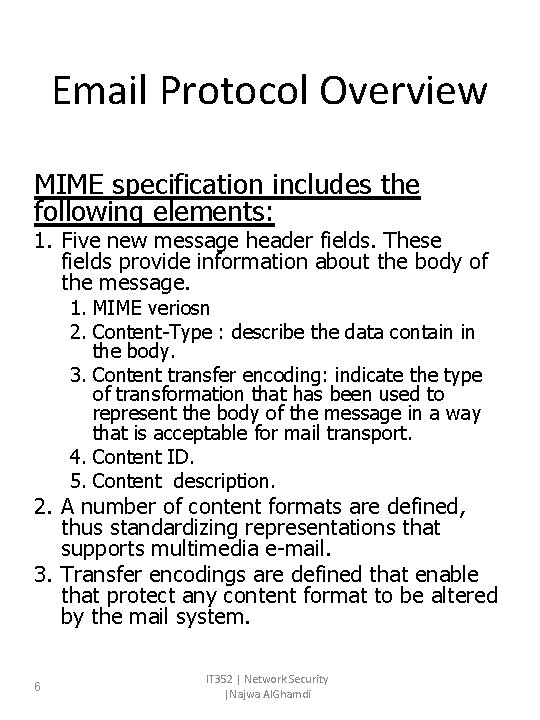
Email Protocol Overview MIME specification includes the following elements: 1. Five new message header fields. These fields provide information about the body of the message. 1. MIME veriosn 2. Content-Type : describe the data contain in the body. 3. Content transfer encoding: indicate the type of transformation that has been used to represent the body of the message in a way that is acceptable for mail transport. 4. Content ID. 5. Content description. 2. A number of content formats are defined, thus standardizing representations that supports multimedia e-mail. 3. Transfer encodings are defined that enable that protect any content format to be altered by the mail system. 6 IT 352 | Network Security |Najwa Al. Ghamdi

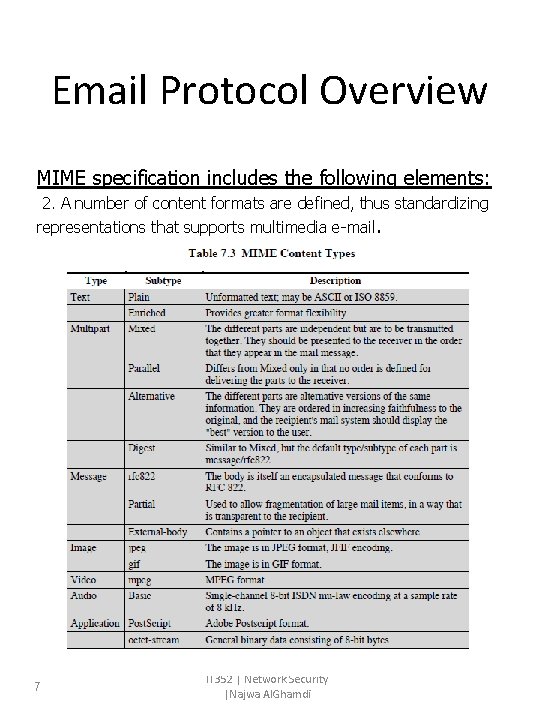
Email Protocol Overview MIME specification includes the following elements: 2. A number of content formats are defined, thus standardizing representations that supports multimedia e-mail. 7 IT 352 | Network Security |Najwa Al. Ghamdi

Example of multipart message From: Nathaniel Borenstein <nsb@bellcore. com> To: Ned Freed ned@innosoft. com Subject: Sample message MIME-Version: 1. 0 Content-type: multipart/mixed; boundary=“ simple boundary“ This is the preamble. It is to be ignored, though it is a handy place for mail composers to include an explanatory note to non-MIME conformant readers. --simple boundary This is implicitly typed plain ASCII text. It does NOT end with a linebreak. --simple boundary Content-type: text/plain; charset=us-ascii This is explicitly typed plain ASCII text. It DOES end with a linebreak. --simple boundary-- This is the epilogue. It is also to be ignored. 8 IT 352 | Network Security |Najwa Al. Ghamdi

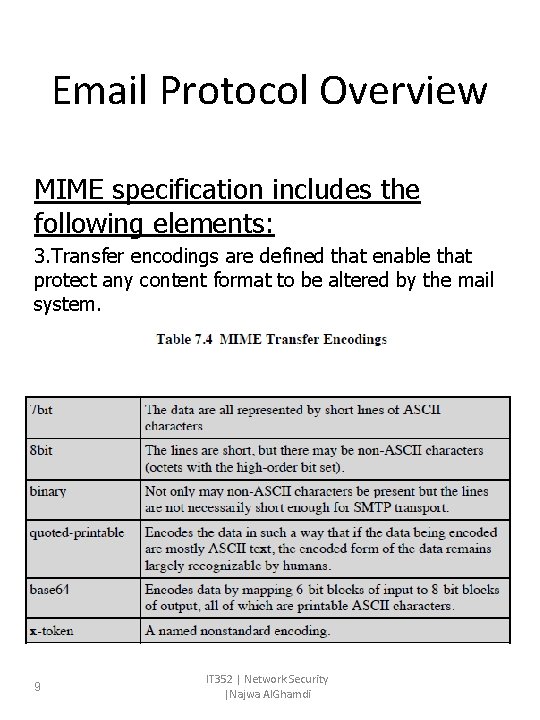
Email Protocol Overview MIME specification includes the following elements: 3. Transfer encodings are defined that enable that protect any content format to be altered by the mail system. 9 IT 352 | Network Security |Najwa Al. Ghamdi

S/MIME (Secure/Multipurpose Internet Mail Extensions) • security enhancement to MIME email • have S/MIME support in many mail agents – MS Outlook, Mozilla, Mac Mail etc

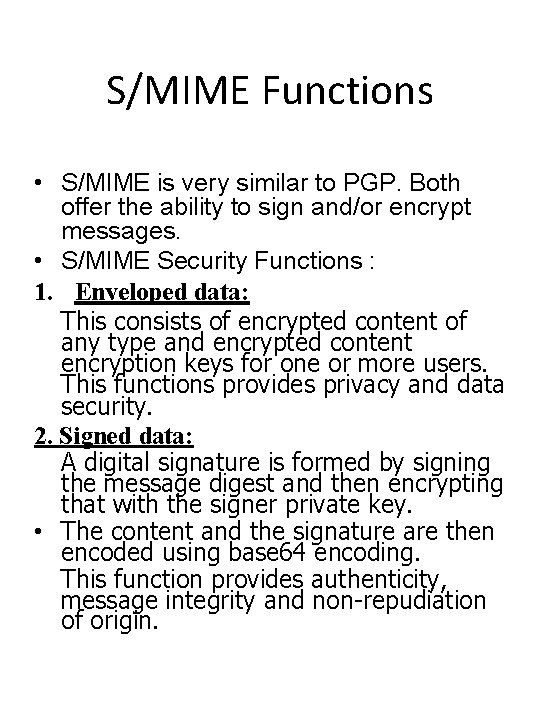
S/MIME Functions • S/MIME is very similar to PGP. Both offer the ability to sign and/or encrypt messages. • S/MIME Security Functions : 1. Enveloped data: This consists of encrypted content of any type and encrypted content encryption keys for one or more users. This functions provides privacy and data security. 2. Signed data: A digital signature is formed by signing the message digest and then encrypting that with the signer private key. • The content and the signature are then encoded using base 64 encoding. This function provides authenticity, message integrity and non-repudiation of origin.

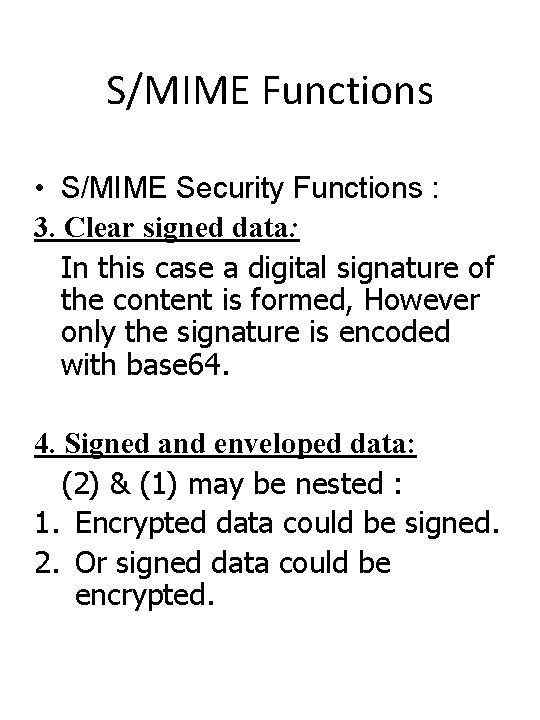
S/MIME Functions • S/MIME Security Functions : 3. Clear signed data: In this case a digital signature of the content is formed, However only the signature is encoded with base 64. 4. Signed and enveloped data: (2) & (1) may be nested : 1. Encrypted data could be signed. 2. Or signed data could be encrypted.

S/MIME Cryptographic Algorithms • digital signatures: DSS & RSA • hash functions: SHA-1 & MD 5 • session key encryption: El. Gamal & RSA • message encryption: AES, Triple. DES, RC 2/40 and others • MAC: HMAC with SHA-1

S/MIME Messages Ø A MIME entity may be an entire message or one or more of the subparts of the message. Ø S/MIME secures a MIME entity with a signature, encryption, or both to form a MIME wrapped (public-key cryptography specifications ) PKCS object Ø A PKCS Object is then treated as message content. Ø have a range of content-types: l enveloped data l signed data l clear-signed data l registration request l certificate only message

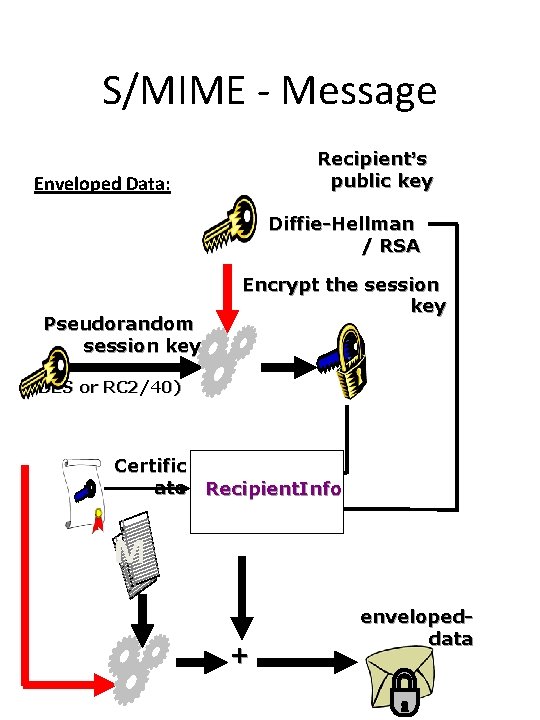
S/MIME - Message Recipient’s public key Enveloped Data: Diffie-Hellman / RSA Pseudorandom session key Encrypt the session key (3 DES or RC 2/40) Certific ate Recipient. Info M + envelopeddata

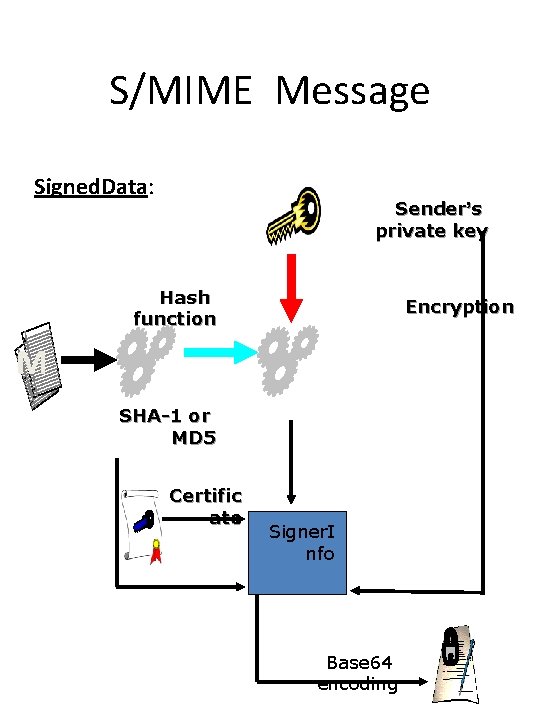
S/MIME Message Signed. Data: Sender’s private key Hash function Encryption M SHA-1 or MD 5 Certific ate Signer. I nfo Base 64 encoding

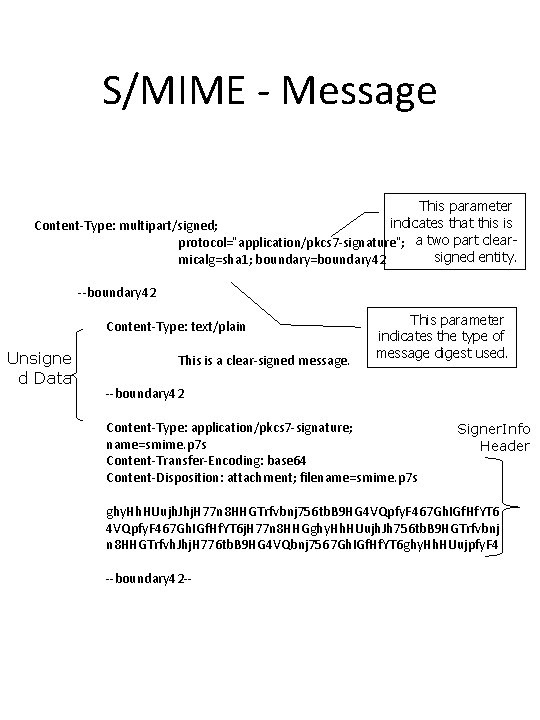
S/MIME - Message Clear signing: Ï Clear signing is achieved using the multipart content type with a signed sub-type. Two parts: § Clear text (or any MIME type) encoded in base 64. § Signed. Data.

S/MIME - Message This parameter indicates that this is Content-Type: multipart/signed; protocol=“application/pkcs 7 -signature”; a two part clearsigned entity. micalg=sha 1; boundary=boundary 42 --boundary 42 Content-Type: text/plain Unsigne d Data This is a clear-signed message. This parameter indicates the type of message digest used. --boundary 42 Content-Type: application/pkcs 7 -signature; name=smime. p 7 s Content-Transfer-Encoding: base 64 Content-Disposition: attachment; filename=smime. p 7 s Signer. Info Header ghy. Hh. HUujh. Jhj. H 77 n 8 HHGTrfvbnj 756 tb. B 9 HG 4 VQpfy. F 467 Gh. IGf. Hf. YT 6 j. H 77 n 8 HHGghy. Hh. HUujh. Jh 756 tb. B 9 HGTrfvbnj n 8 HHGTrfvh. Jhj. H 776 tb. B 9 HG 4 VQbnj 7567 Gh. IGf. Hf. YT 6 ghy. Hh. HUujpfy. F 4 --boundary 42 --

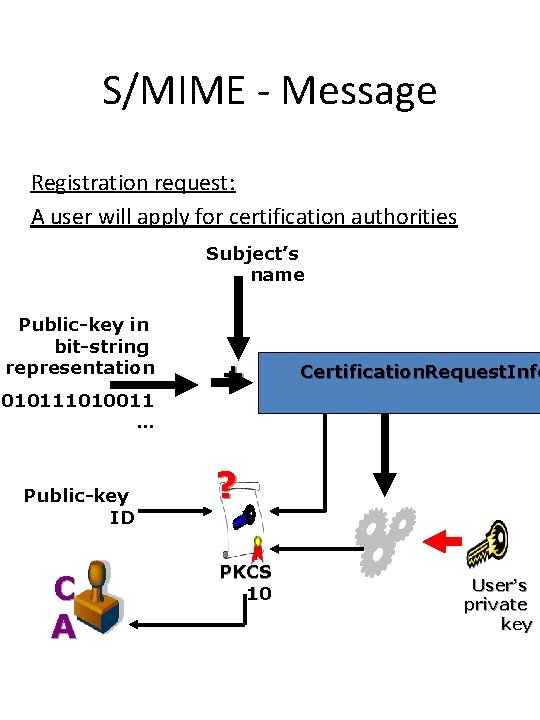
S/MIME - Message Registration request: A user will apply for certification authorities Subject’s name Public-key in bit-string representation 010111010011 … Public-key ID C A + Certification. Request. Info ? PKCS 10 User’s private key

S/MIME - Message Certificate-only message: Ï Used to transport certificates. Ï contains only certificates or a certificate revocation list (CRL). Ï Sent in response to a registration request.

S/MIME - Message Creating a Certificates-only Message: Step 1: The certificates are made available to the CMS generating process which creates a CMS object of type signed. Data. Step 2: The CMS signed. Data object is enclosed in an application/pkcs 7 -mime MIME entity. Ï The smime-type parameter for a certs-only message is "certs-only". Ï The file extension for this type of message is ". p 7 c".

S/MIME Certificate Processing • S/MIME uses X. 509 v 3 certificates • The key-management scheme used by S/MIME is in some ways managed using a hybrid of a strict X. 509 CA hierarchy & PGP’s web of trust • each client has a list of trusted CA’s certs • and own public/private key pairs & certs • certificates must be signed by trusted CA’s