EMAIL Electronic mail layout 1 What is email









![space and special characters "(), : ; <>@[] are allowed with restrictions they are space and special characters "(), : ; <>@[] are allowed with restrictions they are](https://slidetodoc.com/presentation_image_h2/94cb3e5b5b50d87ada66741ca3b967ae/image-13.jpg)
























- Slides: 54

E-MAIL Electronic mail

layout 1. What is email & email address? 2. History of email. 3. Email provider? 4. How to Create gmail? 5. What is captcha? 6. Email protocols. 7. Email system. 8. Email features. 9. Email advanteges. 10. Email disadvanteges. 11. Fact about email.

WHAT IS E-MAIL? ? 1. Email is a service which allows us to send the message in electronic mode with the help of the internet. 2. It’s a modern method of transmitting data, text files, digital photos, and audio and video files from one computer to another over the internet.

HISTORY OF E-MAIL 1. e-mail is Invented by Ray Tomlinson, email first use in the 1960 2. Email operates with Internet. Some early email systems required the author and the recipient to both be online at the same time, in common

But Today's email systems are based on a store-and -forward model. Email servers accept, forward, deliver, and store messages. Neither the users nor their computers are required to be online

V. A. Shiva Ayyadurai He is notable for his controversial claim to be the "inventor of email", [6] based on the electronic mail software called "EMAIL" he study as a New Jersey high school student in the late 1970 s.

As for the "@" symbol, Tomlinson spoke about his choice to use it in email addresses The primary reason was that it made sense. The @ sign didn't appear in names so there would be no ambiguity about where the separation between login name and host name occurred Ray Tomlinson is universally credited as the creator of email as part of a program for ARPANET in 1971. Meanwhile in 1978, a 14 -year-old boy, Shiva Ayyadurai began his work on an email system for the University of Medicine and Dentistry of New Jersey. His task was to emulate the paper-based interoffice mail system electronically

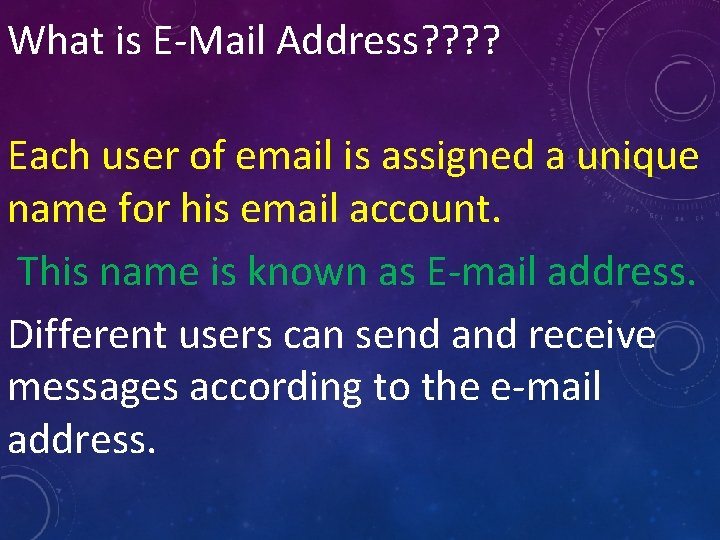
What is E-Mail Address? ? Each user of email is assigned a unique name for his email account. This name is known as E-mail address. Different users can send and receive messages according to the e-mail address.

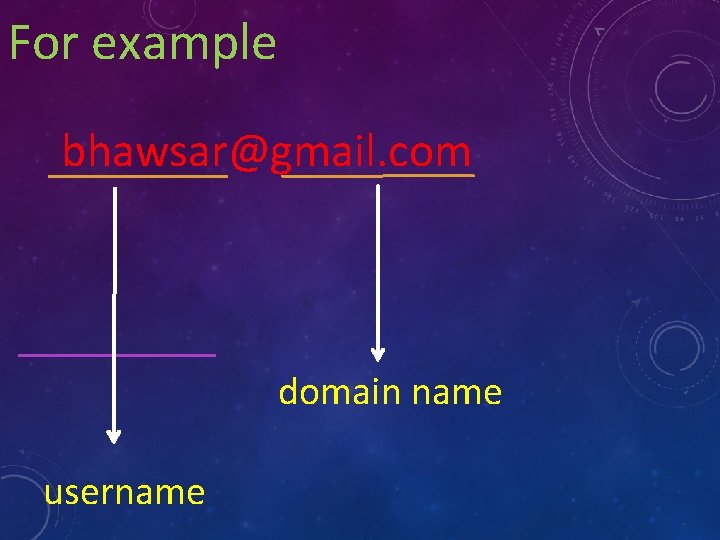
E-mail is generally of the form username@domainname where the user name may be up to 64 characters long and the domain may have a maximum of 255 characters.

For example bhawsar@gmail. com domain name username

User name: The user name of the email address may use any of these ASCII characters: Uppercase and lowercase letters A to Z and a to z; digits 0 to 9; printable characters others than letters and digit !#$%&'*+-/=? ^_`{|}~;

dot. , provided that it is not the first or last character unless quoted, and provided also that it does not appear consecutively unless quoted e. g. hitesh. . bhavsar@example. com is not allowed but “arun. . yadav"@example. com is allowed
![space and special characters are allowed with restrictions they are space and special characters "(), : ; <>@[] are allowed with restrictions they are](https://slidetodoc.com/presentation_image_h2/94cb3e5b5b50d87ada66741ca3b967ae/image-13.jpg)
space and special characters "(), : ; <>@[] are allowed with restrictions they are only allowed inside a quoted string, as described in the paragraph below, and in addition, a backslash or double-quote must be preceded by a backslash

comments are allowed with parentheses at either end of the user name; e. g. arun. yadav(comment)@ex. com and (comment)arun. yadav@ex. com are both equivalent to arun. yadav@example. com.

THE USERNAME AND THE DOMAIN NAME ARE SEPARATED BY @ SYMBOL. E-MAIL ADDRESSES ARE NOT CASE SENSITIVE. SPACES ARE NOT ALLOWED IN E-MAIL ADDRESS.

E-mail Providers “SENDING MESS GES” Email users create and send messages from individual computers using commercial programs:


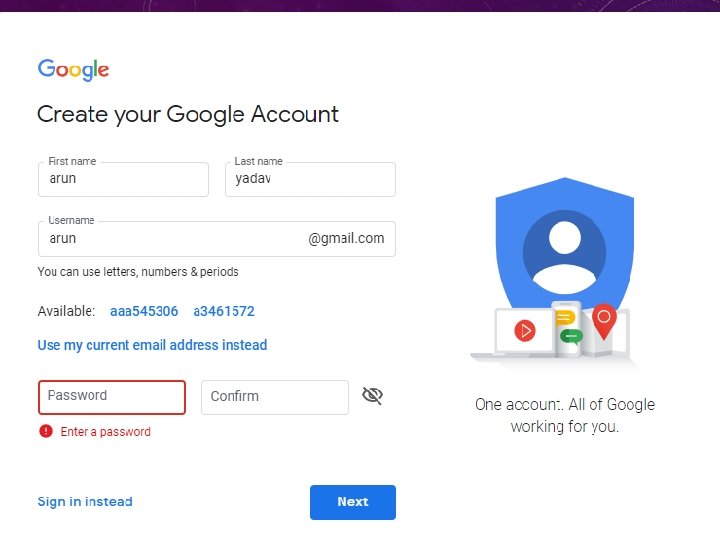
Creating Email Account There are various email service provider available such as Gmail, hotmail, ymail, rediff mail etc. Here we will learn how to create an account using Gmail. Open gmail. com and click create an account. Now a form will appear. Fill your details here and click Next Step.


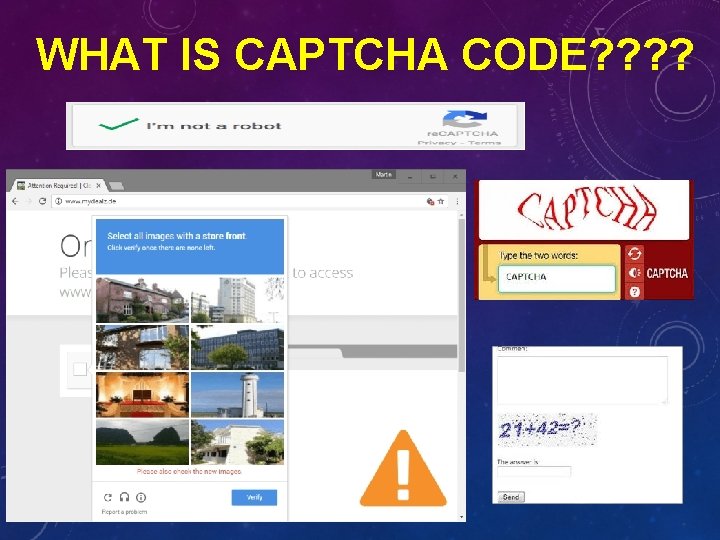
WHAT IS CAPTCHA CODE? ?

Captcha Codes, Remember the good old times when the internet was run by humans and used by humans. Well, it is still run by humans but we now have robots using it too. As cool as it may sound from a science fiction point of view, it is a little dangerous for the internet. To tackle this problem, we have captcha.

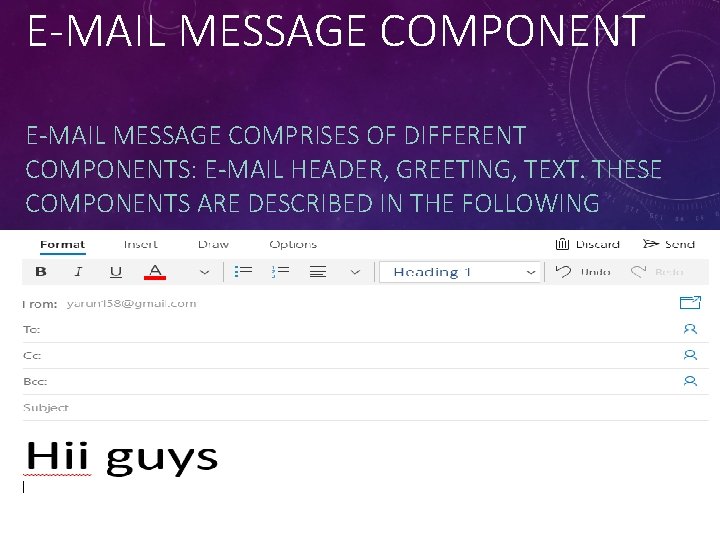
E-MAIL MESSAGE COMPONENT E-MAIL MESSAGE COMPRISES OF DIFFERENT COMPONENTS: E-MAIL HEADER, GREETING, TEXT. THESE COMPONENTS ARE DESCRIBED IN THE FOLLOWING

1. FROM • The From field indicates the sender’s address i. e. who sent the e-mail. 2. DATE • The Date field indicates the date when the e -mail was sent. 3. TO • The To field indicates the recipient’s address i. e. to whom the e-mail is sent.

4. SUBJECT The Subject field indicates the purpose of e-mail. It should be precise and to the point. 5. CC CC stands for Carbon copy. It includes those recipient addresses whom we want to keep informed but not exactly the intended recipient. 6. BCC stands for Black Carbon Copy. It is used when we do not want one or more of the recipients to know that someone else was copied on the message.

E-mail Protocols are set of rules that help the client to properly transmit the information to or from the mail server. we will discuss various protocols such as SMTP, POP, and IMAP. SMTP stands for Simple Mail Transfer Protocol. It was first proposed in 1982. It is a standard protocol used for sending e-mail efficiently and reliably over the internet.

SMTP Key Points: • SMTP is application level protocol • SMTP is text based protocol.

• It handles exchange of messages between e-mail servers over TCP/IP network. • Apart from transferring e-mail, SMPT also provides notification regarding incoming mail. • When you send e-mail, your e-mail client sends it to your e-mail server which further contacts the recipient mail server using SMTP client. • These SMTP commands specify the sender’s and receiver’s e-mail address, along with the message to be send.

• The exchange of commands between servers is carried out without intervention of any user. • In case, message cannot be delivered, an error report is sent to the sender which makes SMTP a reliable protocol.

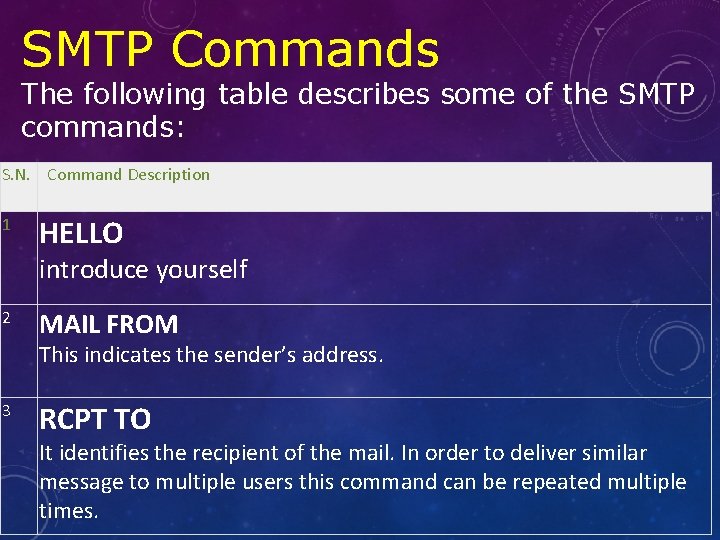
SMTP Commands The following table describes some of the SMTP commands: S. N. Command Description 1 HELLO introduce yourself 2 MAIL FROM This indicates the sender’s address. 3 RCPT TO It identifies the recipient of the mail. In order to deliver similar message to multiple users this command can be repeated multiple times.

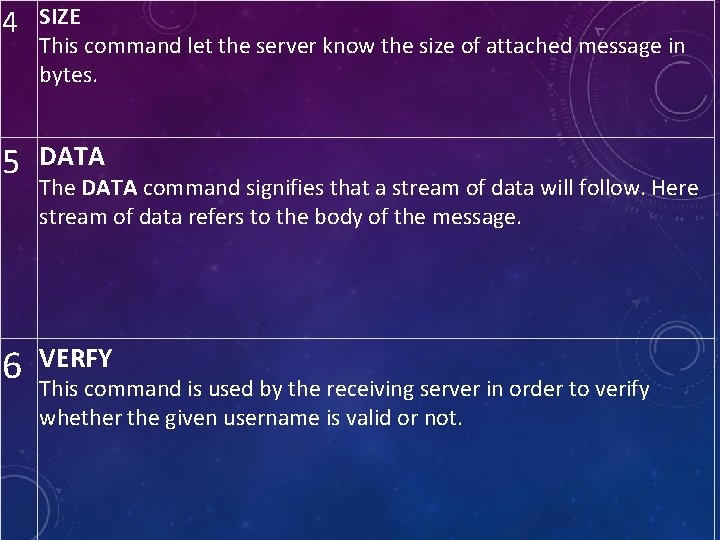
4 SIZE This command let the server know the size of attached message in bytes. 5 DATA 6 VERFY The DATA command signifies that a stream of data will follow. Here stream of data refers to the body of the message. This command is used by the receiving server in order to verify whether the given username is valid or not.

IMAP stands for Internet Mail Access Protocol. It was first proposed in 1986. There exist five versions of IMAP as follows: 1. Original IMAP 2 3. IMAP 3 4. IMAP 2 bis 5. IMAP 4

IMAP Key Points: 1. IMAP allows the client program to manipulate the e-mail message on the server without downloading them on the local computer. 2. The e-mail is hold and maintained by the remote server.

3. It enables us to take any action such as downloading, delete the mail without reading the mail. It enables us to create, manipulate and delete remote message folders called mail boxes. 4. IMAP enables the users to search the emails. 5. It allows concurrent access to multiple mailboxes on multiple mail servers.

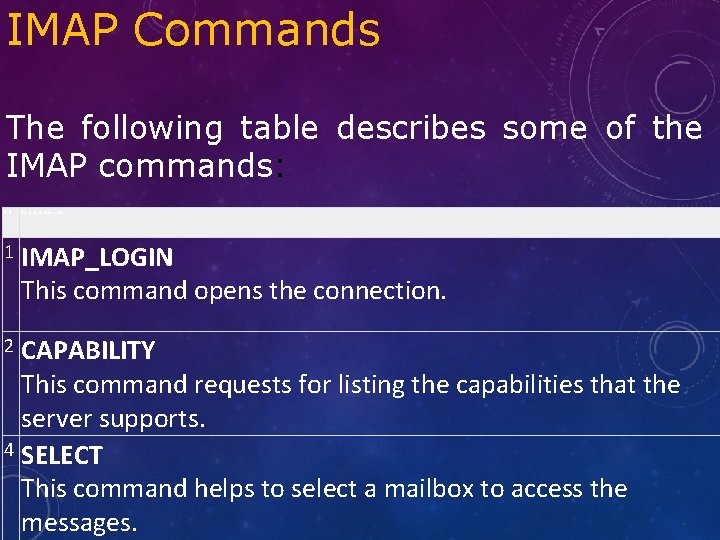
IMAP Commands The following table describes some of the IMAP commands: S. N. Command Description 1 IMAP_LOGIN This command opens the connection. CAPABILITY This command requests for listing the capabilities that the server supports. 4 SELECT This command helps to select a mailbox to access the messages. 2

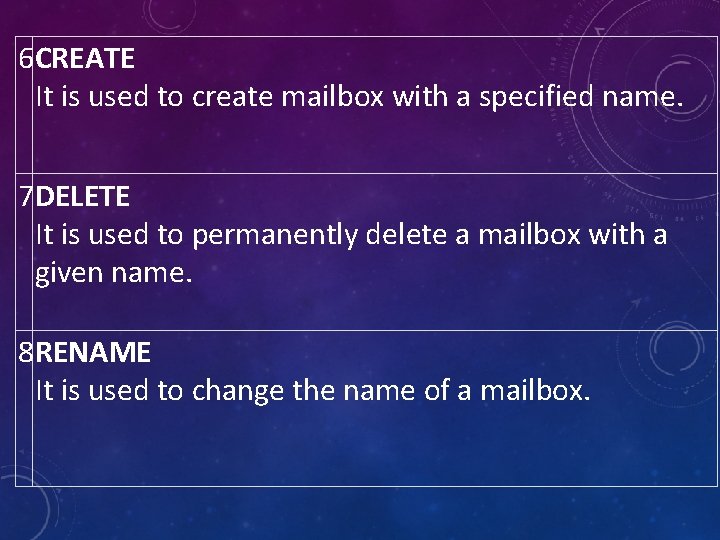
6 CREATE It is used to create mailbox with a specified name. 7 DELETE It is used to permanently delete a mailbox with a given name. 8 RENAME It is used to change the name of a mailbox.

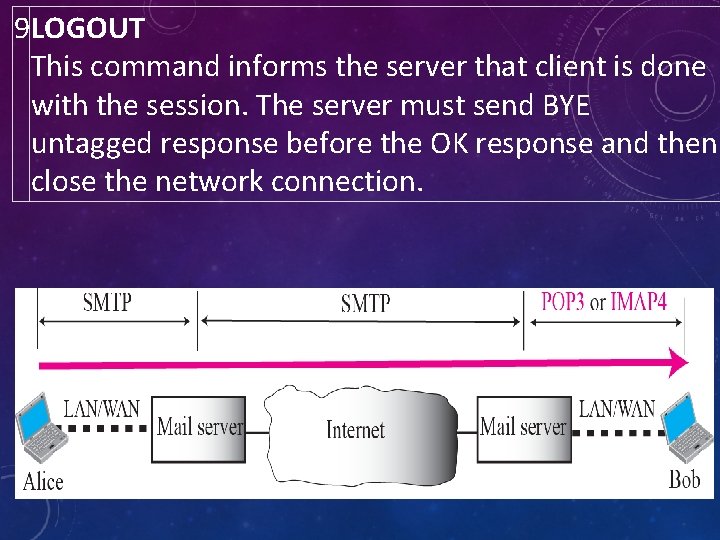
9 LOGOUT This command informs the server that client is done with the session. The server must send BYE untagged response before the OK response and then close the network connection.

POP stands for Post Office Protocol. It is generally used to support a single client. There are several versions of POP but the POP 3 is the current standard. Key Points • POP is an application standard protocol. layer internet

• Since POP supports offline access to the messages, thus requires less internet usage time. • In order to access the messaged, it is necessary to download them. • It allows only one mailbox to be created on server.

• POP does not allow search facility. • It is not suitable for accessing non mail data. • POP commands are generally abbreviated into codes of three or four letters.

POP Commands USER - enter your user ID PASS - enter your password QUIT - quit the POP 3 server LIST - list the messages and their size RETR - retrieve a message, pass it a Message number DELE - delete a message, pass it a message number


E-mail System E-mail system comprises of the following three components: 1. Mailer 2. Mail Server 3. Mailbox 1. Mailer It is also called mail program, mail application or mail client. It allows us to manage, read and compose e-mail.

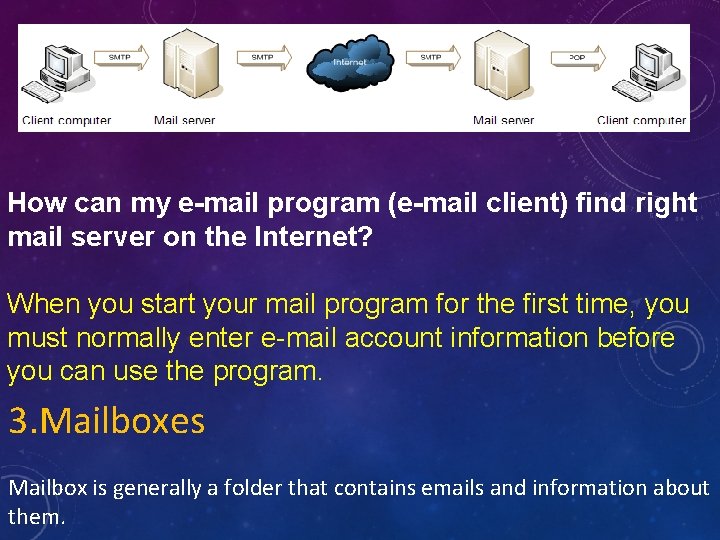
2. Mail Server A mail server (sometimes also referred to an e-mail server) is a server that handles and delivers e-mail over a network, usually over the Internet. A mail server can receive e-mails from client computers and deliver them to other mail servers. A mail server can also deliver emails to client computers. A client computer is normally the computer where you read your e-mails.

How can my e-mail program (e-mail client) find right mail server on the Internet? When you start your mail program for the first time, you must normally enter e-mail account information before you can use the program. 3. Mailboxes Mailbox is generally a folder that contains emails and information about them.


E-mail Features 1. Attachment Ability to attach file(s) along with the message is one of the most useful features of email. The attachment may be a word document, Power. Point presentation, audio/video files, or images. 2. Address Book Address book feature of a mail program allows the users to store information about the people whom they communicate regularly by sending emails.

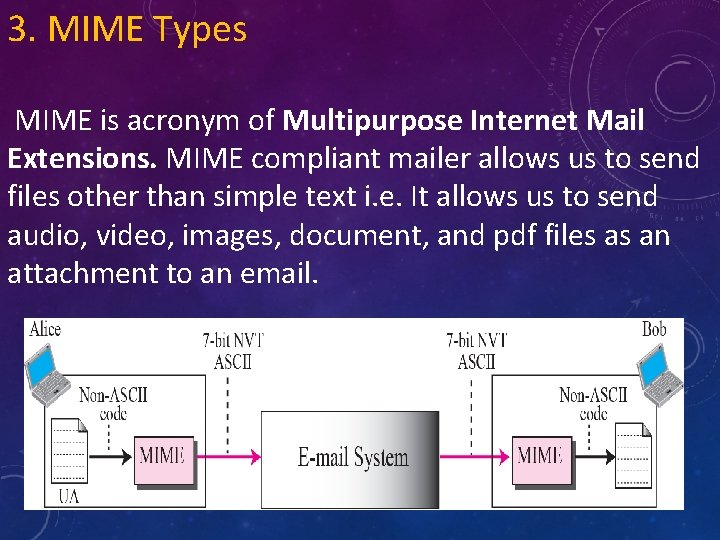
3. MIME Types MIME is acronym of Multipurpose Internet Mail Extensions. MIME compliant mailer allows us to send files other than simple text i. e. It allows us to send audio, video, images, document, and pdf files as an attachment to an email.

E-mail advateges 1. Email is cheap 2. Email is fast 3. Failure notification 4. Attachment 5. Paperless communication 6. No chance of missing

7. No time barrier to send email 8. Remained address 9. Record 10. World Access 11. Flexibility 12. Storage

E-mail disadvateges 1. Spam E-mail spamming is an act of sending Unsolicited Bulk E-mails (UBI) which one has not asked for. Email spams are the junk mails sent by commercial companies as an advertisement of their products and services. 2. Virus Some emails may incorporate with files containing malicious script which when run on your computer may lead to destroy your important data.

3. Phishing Email phishing is an activity of sending emails to a user claiming to be a legitimate enterprise. Its main purpose is to steal sensitive information such as usernames, passwords, and credit card details. Such emails contains link to websites that are infected with malware and direct the user to enter details at a fake website whose look and feels are same to legitimate one. 4. Forgery E-mail doesn’t prevent from forgery, that is, someone impersonating the sender, since sender is usually not authenticated in any way.

5. Overload Convenience of E-mail may result in a flood of mail. 6. Misdirection It is possible that you may send e-mail to an unintended recipient. 4. Junk emails are undesirable and inappropriate emails. Junk emails are sometimes referred to as spam. 5. No Response It may be frustrating when the recipient does not read the e-mail and respond on a regular basis.

E-Mail Facts 1. The total number of email users worldwide will increase up to 2. 9 billion by 2019. 2. Almost 2. 7 million emails are sent per second 3. People spend 5. 4 hours/day checking email 4. 60 percent of email is spam
