Email and DNS Hacking 1 Overview Email Hacking










- Slides: 15

Email and DNS Hacking 1

Overview Email Hacking - Technology - Attacks - Phishing/Spearphishing/Whaling DNS Hacking - Technology - Attacks - Flux 2

Email Here is the program you’ve been waiting for. VIP@XXX. COM Trusted Colleague A postcard written in pencil, with trusted cargo attached 3

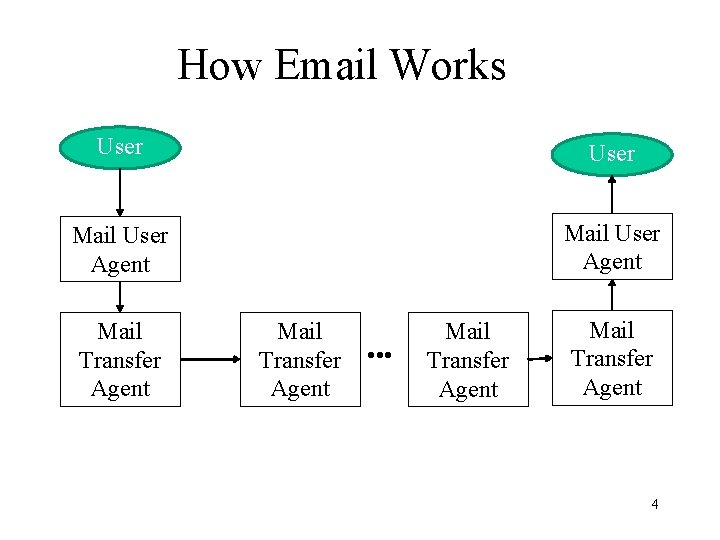
How Email Works User Mail User Agent Mail Transfer Agent • • • Mail Transfer Agent 4

Simple Mail Transfer Protocol • • TCP/25 by default Transfer-agent based Text Protocol Single connection, multiple messages (maybe) • Easily forged S: 220 smtp. example. com ESMTP Postfix C: HELO relay. example. org S: 250 Hello relay. example. org, I am glad to meet you C: MAIL FROM: <bob@example. org> S: 250 Ok C: RCPT TO: <alice@example. com> S: 250 Ok C: RCPT TO: <theboss@example. com> S: 250 Ok C: DATA S: 354 End data with <CR><LF> C: From: "Bob Example" <bob@example. org> C: To: Alice Example <alice@example. com> C: Date: Tue, 15 Jan 2008 16: 02: 43 -0500 C: Subject: Test message C: Hello Alice. C: Your friend, Bob C: . S: 250 Ok: queued as 12345 C: QUIT S: 221 Bye {The server closes the connection} 5

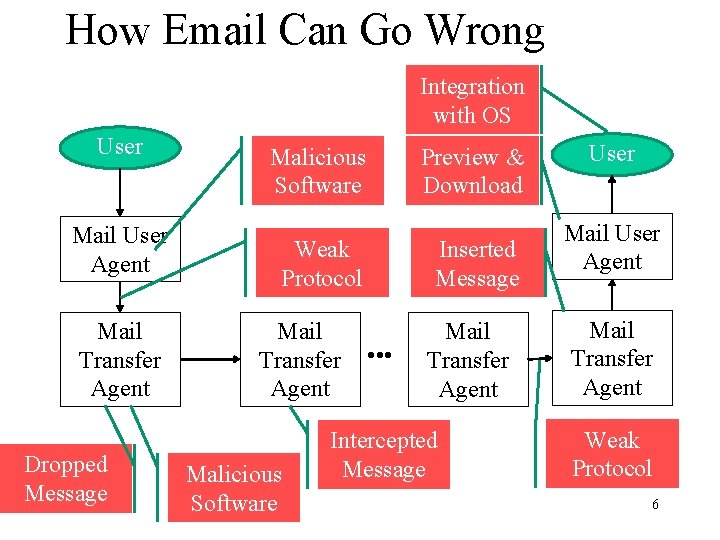
How Email Can Go Wrong Integration with OS User Mail User Agent Mail Transfer Agent Dropped Message Malicious Software Preview & Download Weak Protocol Mail Transfer Agent Malicious Software Inserted Message • • • Mail Transfer Agent Intercepted Message User Mail User Agent Mail Transfer Agent Weak Protocol 6

Attacking Email Fool User Propagate Mail User Agent Mail Transfer Agent Subvert Flood Subvert Mail User Agent Compromise Attach Mail Transfer Agent Extract • • • Mail Transfer Agent Insert Hijack 7

Social Engineering • Exploit trust relationships between people • Exploit service climate • Exploit business methods 8

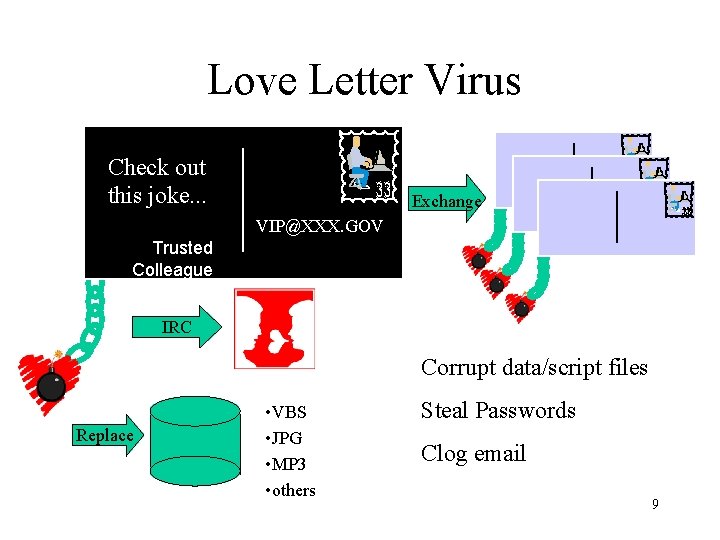
Love Letter Virus Check out this joke. . . Exchange VIP@XXX. GOV Trusted Colleague IRC Corrupt data/script files Replace • VBS • JPG • MP 3 • others Steal Passwords Clog email 9

Phishing example? Date: Tue, 20 Sep 2005 03: 06: 03 -0700 (PDT) From: Countrywide countrywide@email. countrywide. com To: tjs@cert. org Subject: Important Customer Correspondence [Image: "height="] [Image: "Countrywide - Full Speectrum Lending Division"] [Image: "1 -866 -227 -4118"] [Image: "height="] [Image: "If you could use some extra cash, Countrywide could make it easy. "] [Image: "Click Here to Get Started"] [Image: "height="] Dear Timothy, We can help customers get cash from the available equity they've built up in their homes by refinancing their mortgages ? and with the trend in rising home values, we estimate your home's equity may have increased to as much as $43, 867. 00. (much more…) Phone number appears legit, current mortgage holder Note typographical errors (Speectrum, empty images, etc. ) Big payoff offered Closer look: embedded domains doesn’t match from domain (m 0. net, r. delivery. net, not countrywide. com, all same ISP (Digital Impact)) 10

Domain Name System • More than just hostname → IP • Query hierarchy of nameservers – Local nameserver (resolver): answer from cache or preloaded resolutions, may do recursive queries – Authoritative nameserver: answer based on domains it covers, or recurse – Root nameserver: answer top-level, delegate, or generate errors 11

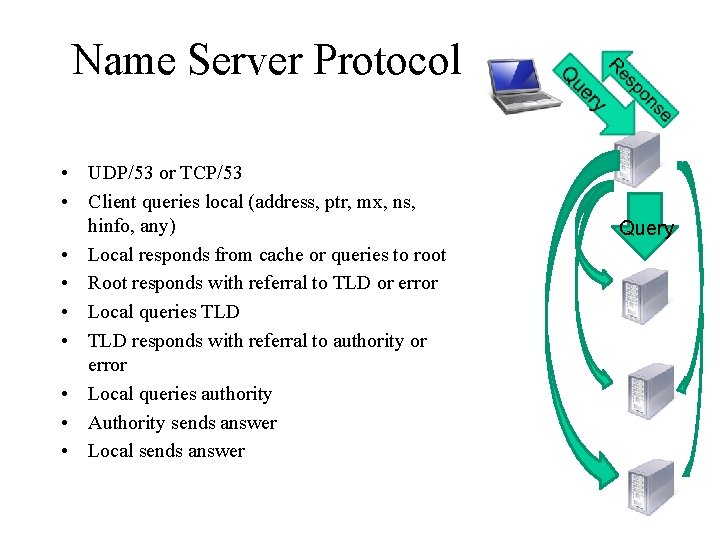
Name Server Protocol • UDP/53 or TCP/53 • Client queries local (address, ptr, mx, ns, hinfo, any) • Local responds from cache or queries to root • Root responds with referral to TLD or error • Local queries TLD • TLD responds with referral to authority or error • Local queries authority • Authority sends answer • Local sends answer Query 12

Where DNS Can Go Wrong • Client Side – – – Cache Poisoning False Response False Domains Compromise Tunneling • Server Side – Flooding – False Response – Compromise 13

Flux • Why would a domain change its resolution? • Why would a domain change frequently? • Why would a domain change transiently? 14

Summary • • • Common and needed protocols Many, many vulnerabilities Many, many attacks Some systematic solutions (encryption) Trust 15