Electronic Payments Epayment methods Credit cards Electronic funds



- Slides: 12

Electronic Payments • E-payment methods – Credit cards – Electronic funds transfer (EFT) – E-payments • • Smart cards Digital cash and script Digital checks E-billing – All have the ability to transfer payment from one person or party to another

Electronic Payments (cont. ) • Four parts involved in epayments – – Issuer Customer/payer/buyer Merchant/payee/seller Regulator • Key issue of trust must be addressed – Privacy – Authentication and authorization – Integrity – Nonrepudiation

Electronic Payments (cont. ) Crucial factors in determining which method of e-payment achieves widespread acceptance – Independence – Interoperability and portability – Security – Anonymity – Divisibility – Ease of use – Transaction fees

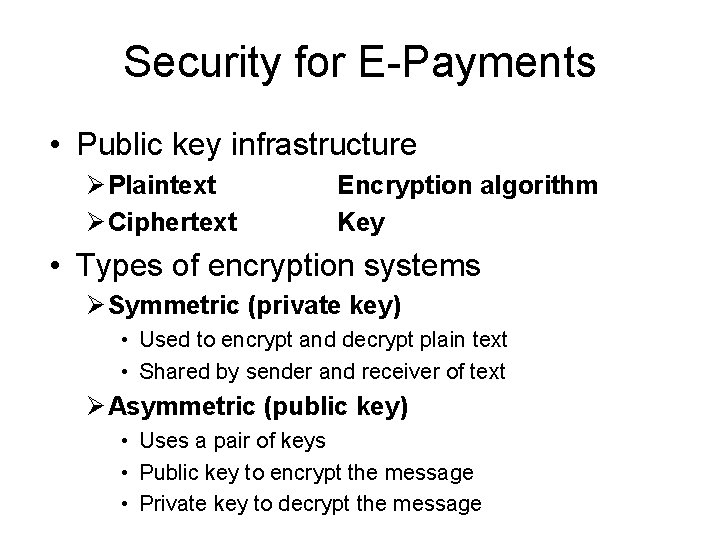
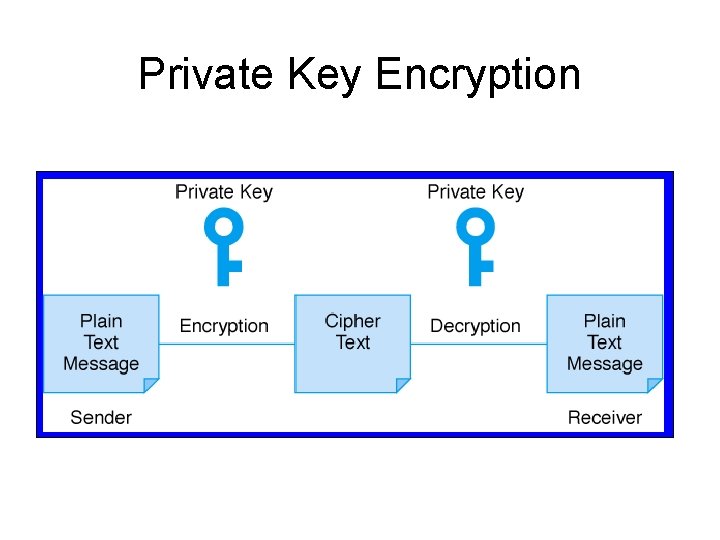
Security for E-Payments • Public key infrastructure Ø Plaintext Ø Ciphertext Encryption algorithm Key • Types of encryption systems Ø Symmetric (private key) • Used to encrypt and decrypt plain text • Shared by sender and receiver of text Ø Asymmetric (public key) • Uses a pair of keys • Public key to encrypt the message • Private key to decrypt the message

Private Key Encryption

Public Key Encryption • Size of key • RSA algorithm • Speed of Key • Rijndael algorithm

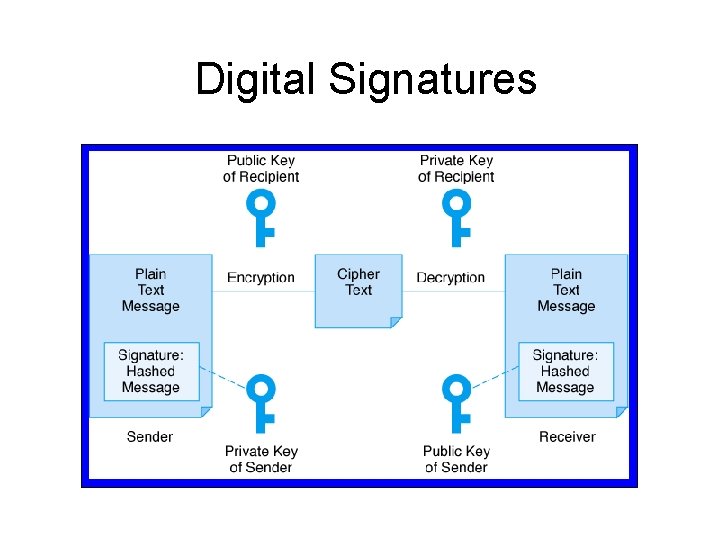
Security for E-Payments (cont. ) • Digital Signatures: authenticity and nondenial – Analogous to handwritten signature – Based on public keys – Used to: • Authenticate the identity of the sender of a message or document • Ensure the original content of the electronic message or document is unchanged

Security for E-Payments (cont. ) • Digital Signatures: authenticity and nondenial (cont. ) – Benefits: • Portable • Cannot be easily repudiated or imitated • Can be time stamped

Digital Signatures

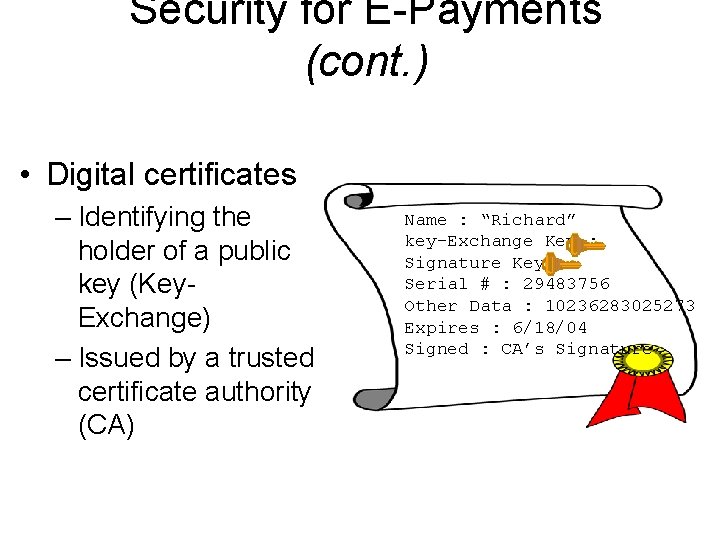
Security for E-Payments (cont. ) • Digital certificates – Identifying the holder of a public key (Key. Exchange) – Issued by a trusted certificate authority (CA) Name : “Richard” key-Exchange Key : Signature Key : Serial # : 29483756 Other Data : 10236283025273 Expires : 6/18/04 Signed : CA’s Signature

Security for E-Payments (cont. ) • Secure socket layer/transport layer security – Secure socket layer (SLL)—handle on Web browser, utilizing CAs and data encryption • Encryption • Digital certificates • Digital signatures – In 1996 SSL was standardized and named transport layer security (TSL) – Operates at TCP/IP layer (base layer for Internet) – IPSec—secure version of IP protocol

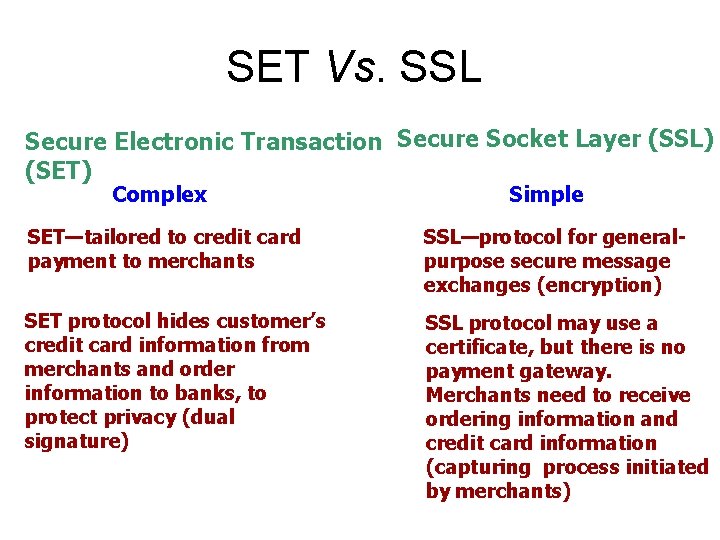
SET Vs. SSL Secure Electronic Transaction Secure Socket Layer (SSL) (SET) Complex Simple SET—tailored to credit card payment to merchants SSL—protocol for generalpurpose secure message exchanges (encryption) SET protocol hides customer’s credit card information from merchants and order information to banks, to protect privacy (dual signature) SSL protocol may use a certificate, but there is no payment gateway. Merchants need to receive ordering information and credit card information (capturing process initiated by merchants)