Electronic Payment Systems 20 763 Lecture 8 Smart






- Slides: 44

Electronic Payment Systems 20 -763 Lecture 8 Smart and Stored-Value Cards

Outline • • Smart card types Operating systems Wireless cards Card manufacture and issuance Security Octopus Mondex Mobile systems 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

e. Payment by Smart Card • Objective: replace cash • Cash is expensive to make and use – – Printing, replacement Anti-counterfeiting measures Transportation Security • Cash is inconvenient – not machine-readable – humans carry limited amount – risk of loss, theft • Additional smart card benefits 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

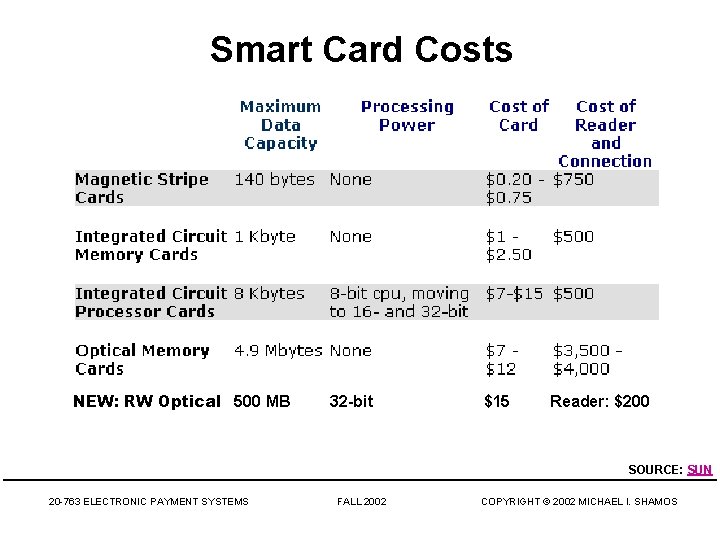
Smart Cards • Magnetic stripe – 140 bytes, cost $0. 20 -0. 75 • Memory cards – 1 -4 KB memory, no processor, cost $1. 00 -2. 50 • Optical memory cards – 4 megabytes read-only (CD-like), $7 -12 • Microprocessor cards – Imbedded microprocessor • (OLD) 8 -bit processor, 16 KB ROM, 512 bytes RAM • Equivalent power to IBM XT PC • 32 -bit processors now available 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Smart Card Costs NEW: RW Optical 500 MB 32 -bit $15 Reader: $200 SOURCE: SUN 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

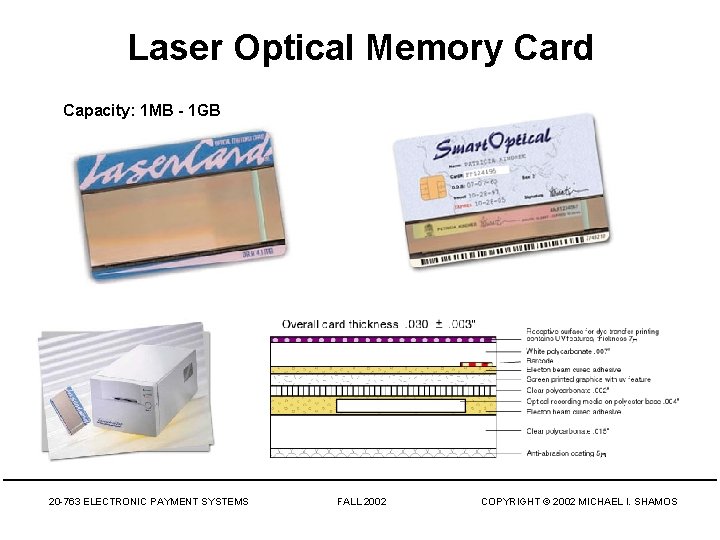
Laser Optical Memory Card Capacity: 1 MB - 1 GB 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

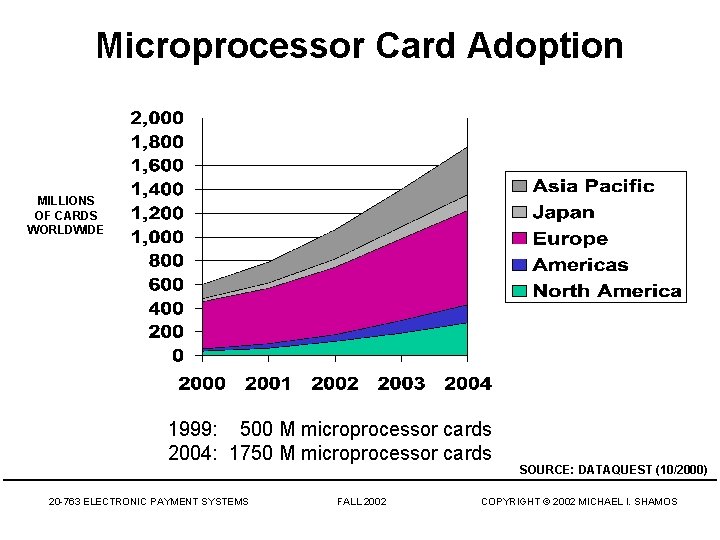
Microprocessor Card Adoption MILLIONS OF CARDS WORLDWIDE 1999: 500 M microprocessor cards 2004: 1750 M microprocessor cards 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 SOURCE: DATAQUEST (10/2000) COPYRIGHT © 2002 MICHAEL I. SHAMOS

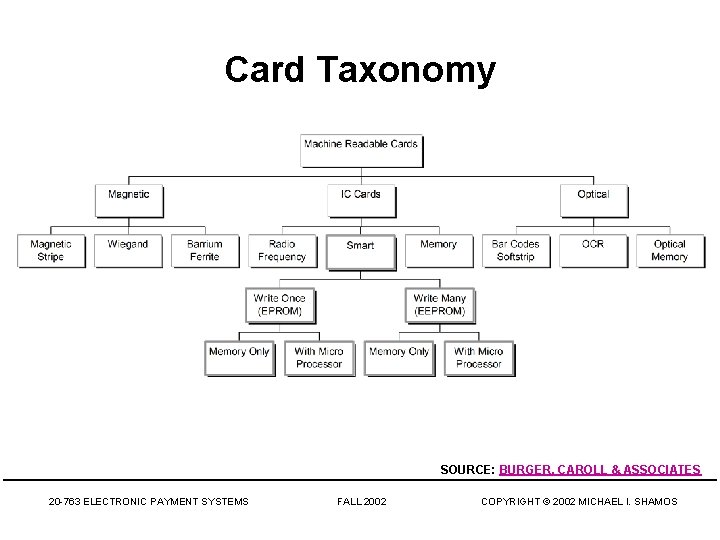
Card Taxonomy SOURCE: BURGER, CAROLL & ASSOCIATES 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

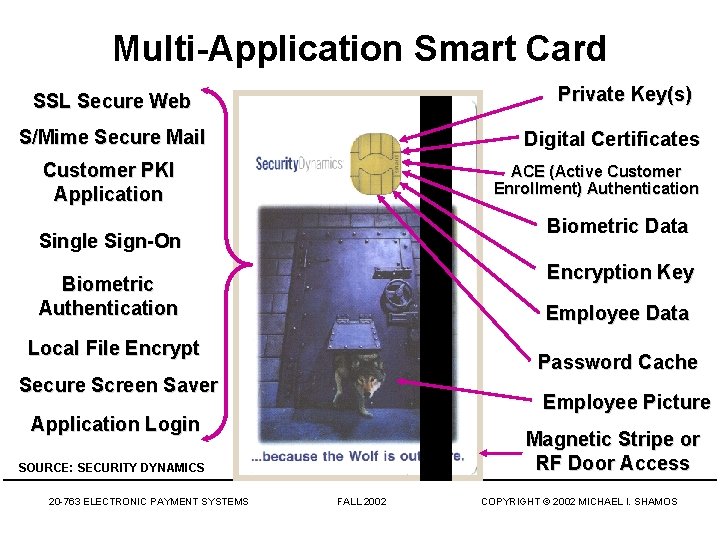
Multi-Application Smart Card Private Key(s) SSL Secure Web S/Mime Secure Mail Digital Certificates Customer PKI Application ACE (Active Customer Enrollment) Authentication Biometric Data Single Sign-On Encryption Key Biometric Authentication Employee Data Local File Encrypt Password Cache Secure Screen Saver Employee Picture Application Login Magnetic Stripe or RF Door Access SOURCE: SECURITY DYNAMICS 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

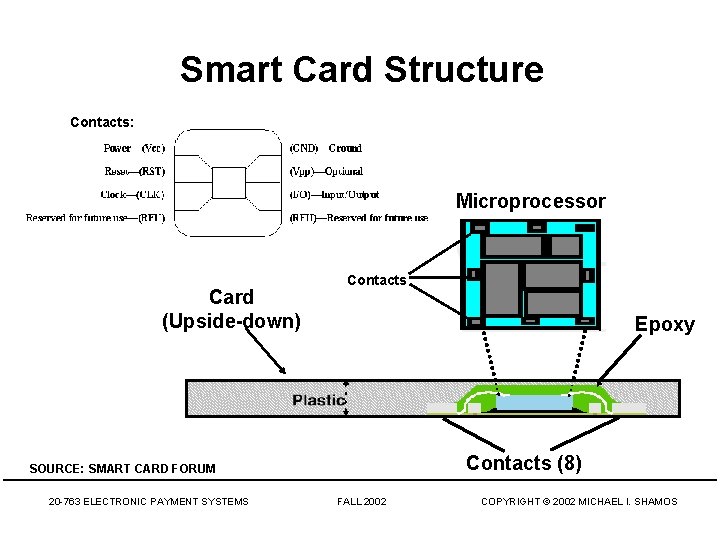
Smart Card Structure Contacts: Microprocessor Card (Upside-down) Contacts Epoxy Contacts (8) SOURCE: SMART CARD FORUM 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

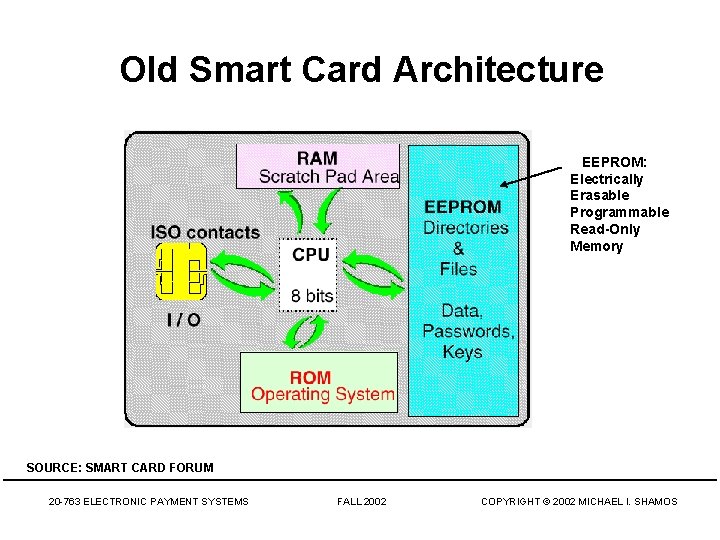
Old Smart Card Architecture EEPROM: Electrically Erasable Programmable Read-Only Memory SOURCE: SMART CARD FORUM 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

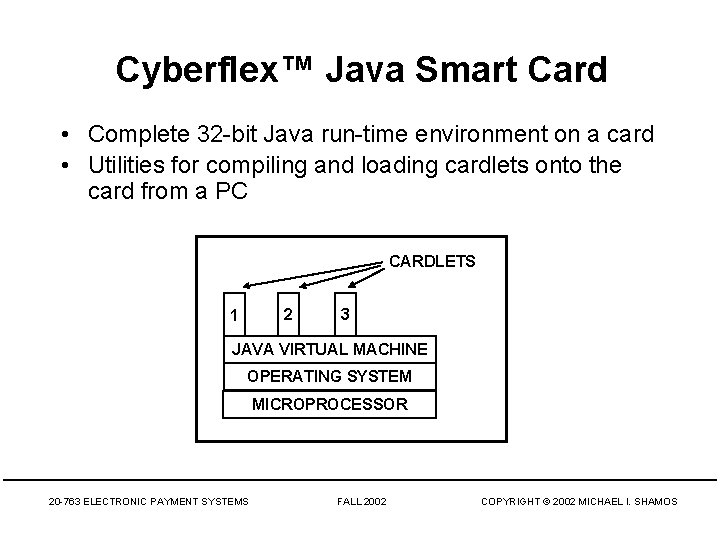
Cyberflex™ Java Smart Card • Complete 32 -bit Java run-time environment on a card • Utilities for compiling and loading cardlets onto the card from a PC CARDLETS 2 1 3 JAVA VIRTUAL MACHINE OPERATING SYSTEM MICROPROCESSOR 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

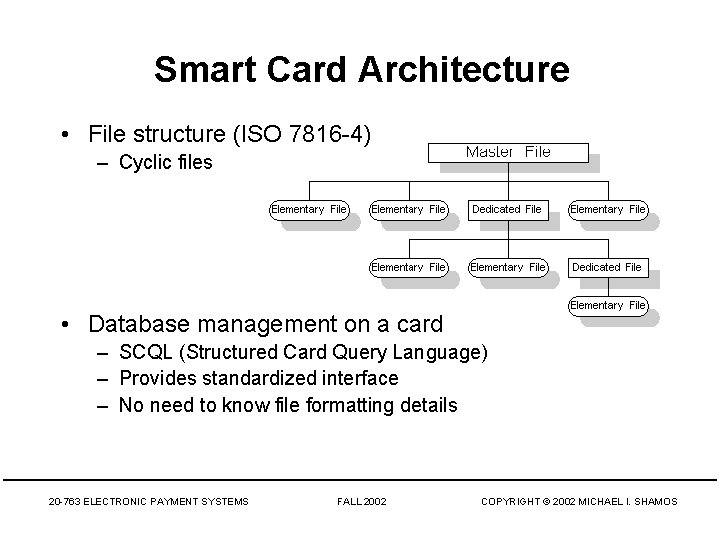
Smart Card Architecture • File structure (ISO 7816 -4) – Cyclic files • Database management on a card – SCQL (Structured Card Query Language) – Provides standardized interface – No need to know file formatting details 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Contactless Cards • Communicates by radio – Power supplied by reader – Data rate 106 Kb/sec – Read 2. 5 ms, write 9 ms – 8 Kb EEPROM, unlimited read, 100, 000 writes – Effective range: 10 cm, signals encrypted – Lifetime: 2 years (data retention 10 years) – Two-way authentication, nonces, secret keys – Anticollision mechanism for multiple cards – Unique card serial number SOURCE: GEMPLUS 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

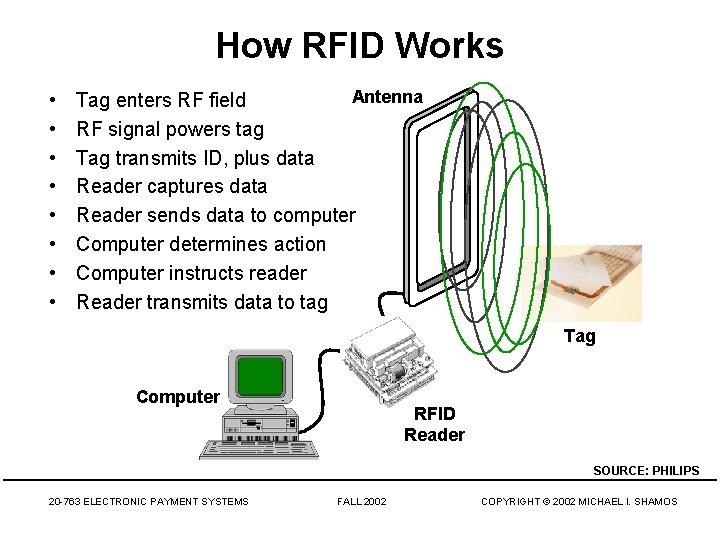
How RFID Works • • Antenna Tag enters RF field RF signal powers tag Tag transmits ID, plus data Reader captures data Reader sends data to computer Computer determines action Computer instructs reader Reader transmits data to tag Tag Computer RFID Reader SOURCE: PHILIPS 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

RFID 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS SOURCE: SANJAY SARMA

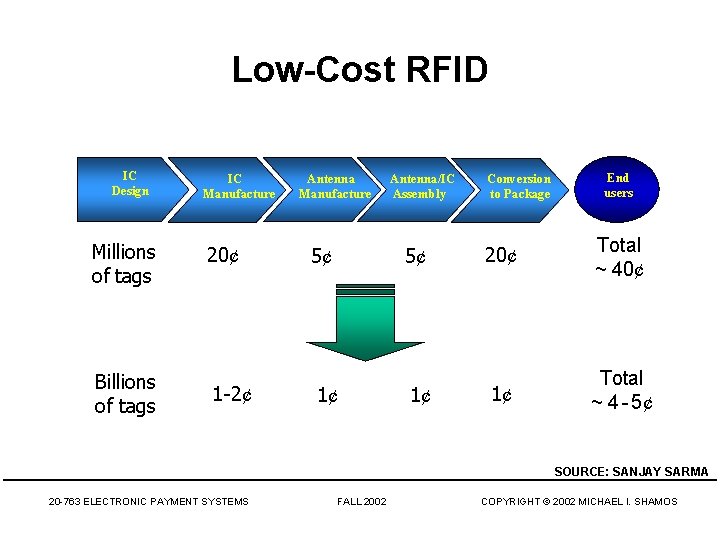
Low-Cost RFID IC Design Millions of tags Billions of tags IC Manufacture 20¢ 1 -2¢ Antenna Manufacture 5¢ Antenna/IC Assembly 5¢ 1¢ 1¢ Conversion to Package End users 20¢ Total ~ 40¢ 1¢ Total ~ 4 - 5¢ SOURCE: SANJAY SARMA 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

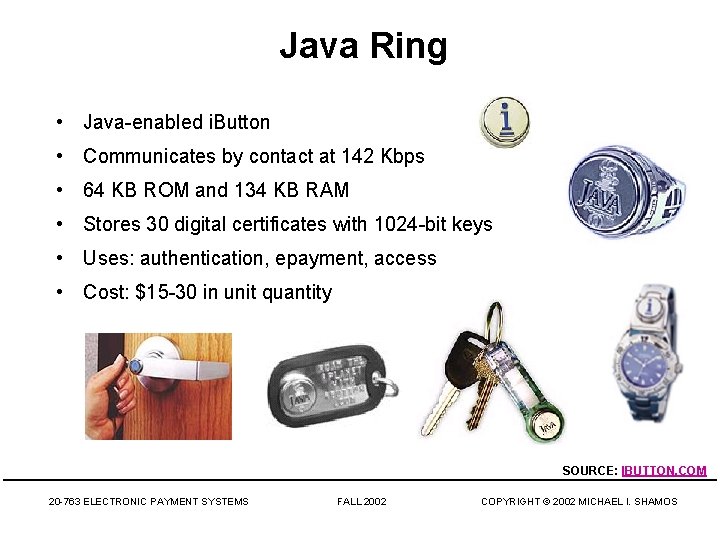
Java Ring • Java-enabled i. Button • Communicates by contact at 142 Kbps • 64 KB ROM and 134 KB RAM • Stores 30 digital certificates with 1024 -bit keys • Uses: authentication, epayment, access • Cost: $15 -30 in unit quantity SOURCE: IBUTTON. COM 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

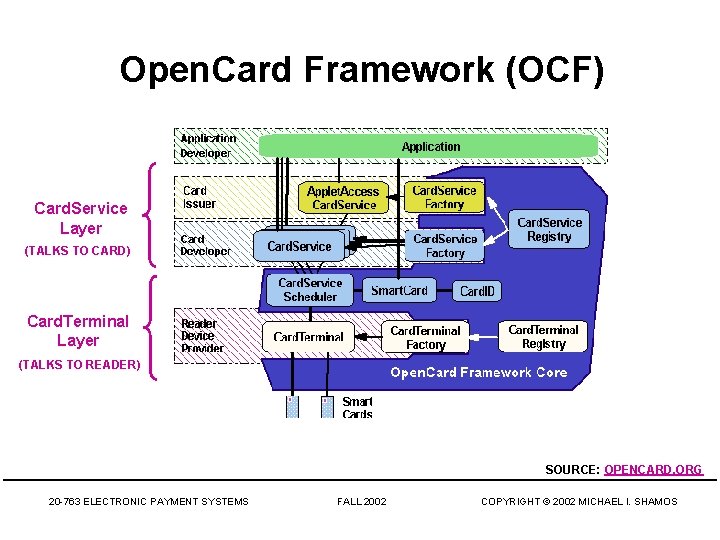
Open. Card Framework (OCF) Card. Service Layer (TALKS TO CARD) Card. Terminal Layer (TALKS TO READER) SOURCE: OPENCARD. ORG 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

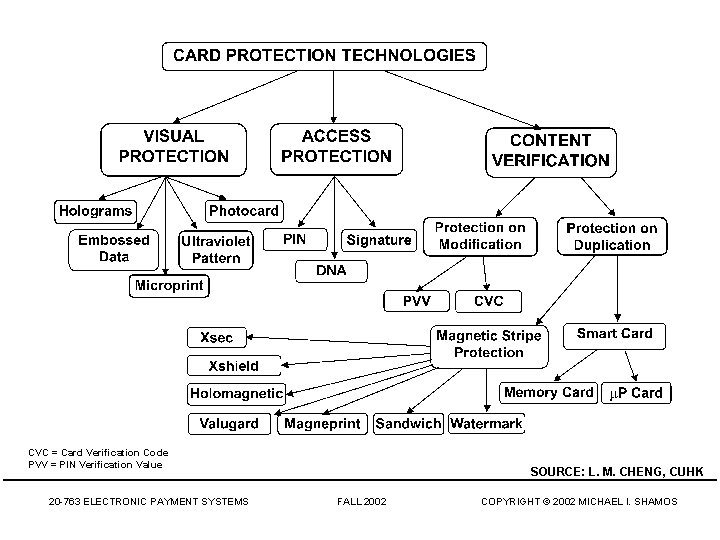
CVC = Card Verification Code PVV = PIN Verification Value 20 -763 ELECTRONIC PAYMENT SYSTEMS SOURCE: L. M. CHENG, CUHK FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

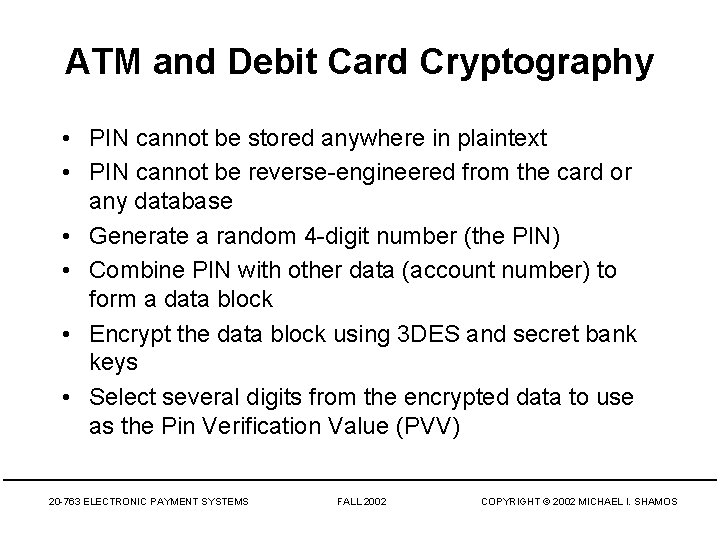
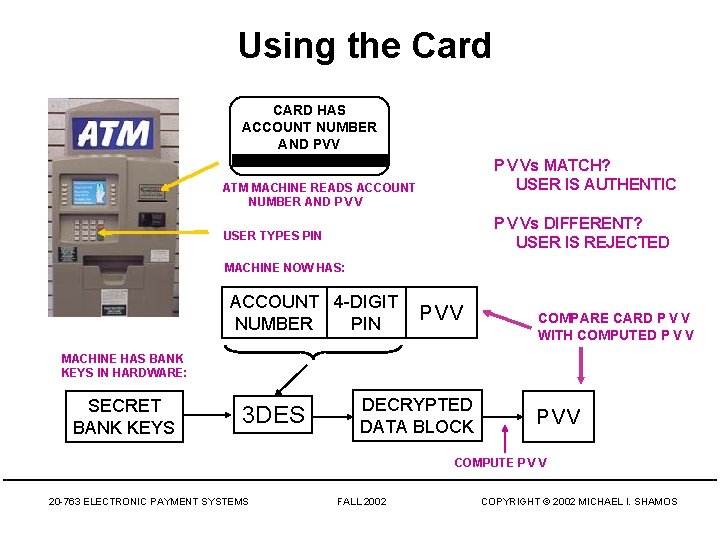
ATM and Debit Card Cryptography • PIN cannot be stored anywhere in plaintext • PIN cannot be reverse-engineered from the card or any database • Generate a random 4 -digit number (the PIN) • Combine PIN with other data (account number) to form a data block • Encrypt the data block using 3 DES and secret bank keys • Select several digits from the encrypted data to use as the Pin Verification Value (PVV) 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

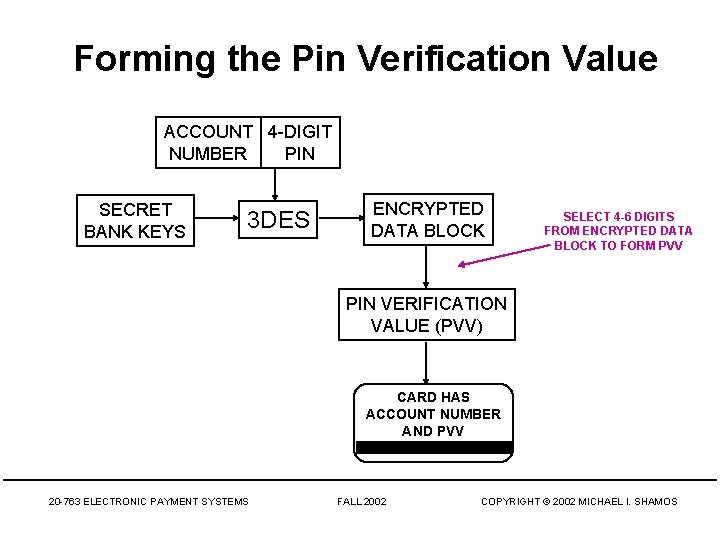
Forming the Pin Verification Value ACCOUNT 4 -DIGIT NUMBER PIN SECRET BANK KEYS 3 DES ENCRYPTED DATA BLOCK SELECT 4 -6 DIGITS FROM ENCRYPTED DATA BLOCK TO FORM PVV PIN VERIFICATION VALUE (PVV) CARD HAS ACCOUNT NUMBER AND PVV 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Using the Card CARD HAS ACCOUNT NUMBER AND PVV P V Vs MATCH? USER IS AUTHENTIC ATM MACHINE READS ACCOUNT NUMBER AND P V Vs DIFFERENT? USER IS REJECTED USER TYPES PIN MACHINE NOW HAS: ACCOUNT 4 -DIGIT NUMBER PIN P V V COMPARE CARD P V V WITH COMPUTED P V V MACHINE HAS BANK KEYS IN HARDWARE: SECRET BANK KEYS 3 DES DECRYPTED DATA BLOCK P V V COMPUTE P V V 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Credit Card Fraud Stealing — A legal card may be stolen and used in ATMs or EPOSs. l Altering and re-embossing a genuine card, modifying visual features. l Skimming or altering data on the magnetic stripe, e. g. expiration date or credit limit, stored value. · Copying data from a genuine card to another online — “white plastic fraud” · Counterfeiting — “color plastic fraud” — encoding information from one card to another card off-line l SOURCE: L. M. CHENG, CUHK 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

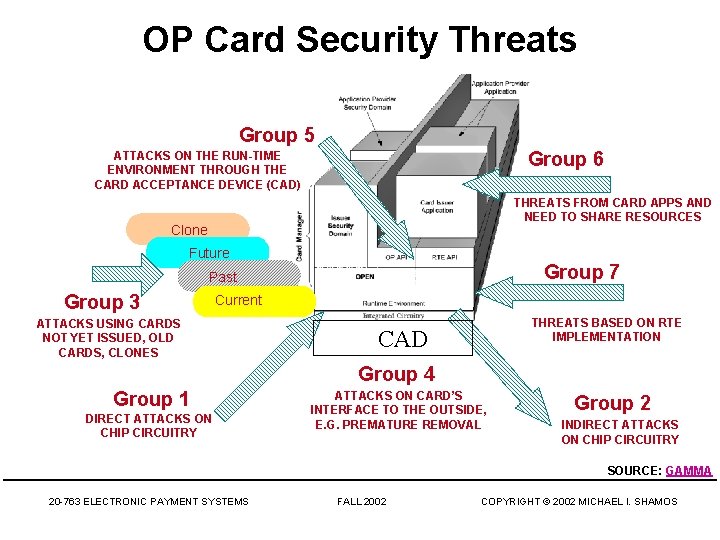
OP Security Assumptions • OP card is merely a component • Need to trust: – back-office systems – cryptographic key management – card/chip operating environment (COE) – off-card security procedures (actors and roles) • There are vulnerabilities the OP card cannot protect itself against SOURCE: GAMMA 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

OP Card Security Threats Group 5 Group 6 ATTACKS ON THE RUN-TIME ENVIRONMENT THROUGH THE CARD ACCEPTANCE DEVICE (CAD) THREATS FROM CARD APPS AND NEED TO SHARE RESOURCES Clone Future Group 7 Past Group 3 Current ATTACKS USING CARDS NOT YET ISSUED, OLD CARDS, CLONES THREATS BASED ON RTE IMPLEMENTATION CAD Group 4 Group 1 DIRECT ATTACKS ON CHIP CIRCUITRY ATTACKS ON CARD’S INTERFACE TO THE OUTSIDE, E. G. PREMATURE REMOVAL Group 2 INDIRECT ATTACKS ON CHIP CIRCUITRY SOURCE: GAMMA 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

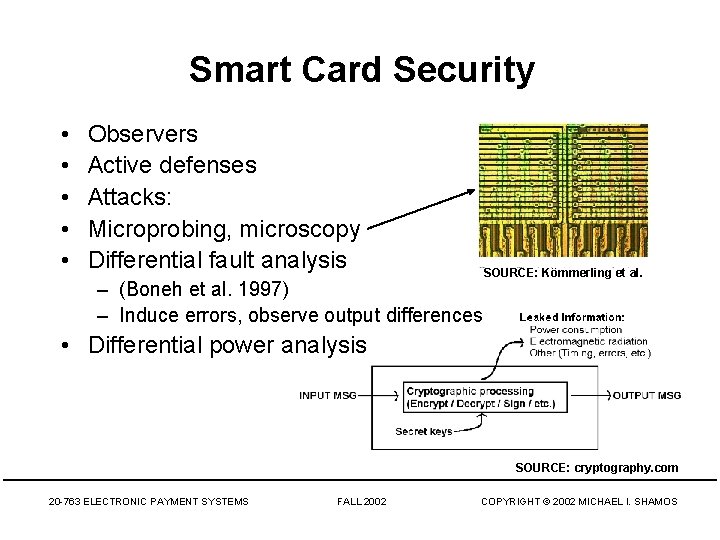
Smart Card Security • • • Observers Active defenses Attacks: Microprobing, microscopy Differential fault analysis – (Boneh et al. 1997) – Induce errors, observe output differences SOURCE: Kömmerling et al. • Differential power analysis SOURCE: cryptography. com 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

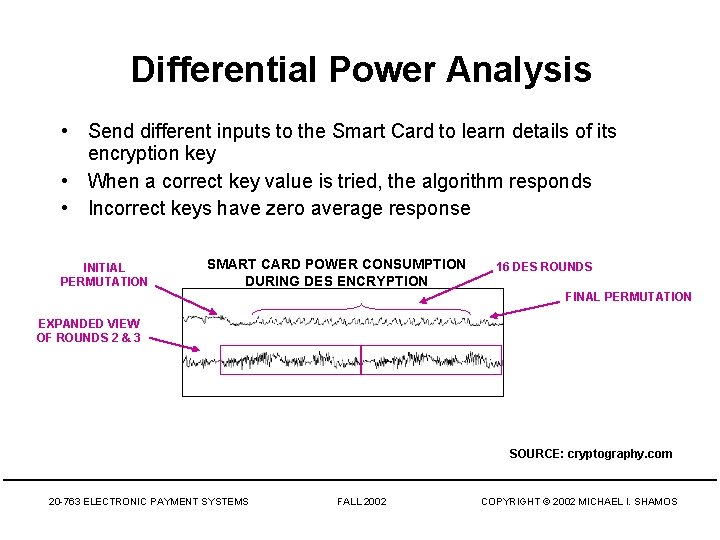
Differential Power Analysis • Send different inputs to the Smart Card to learn details of its encryption key • When a correct key value is tried, the algorithm responds • Incorrect keys have zero average response INITIAL PERMUTATION SMART CARD POWER CONSUMPTION DURING DES ENCRYPTION 16 DES ROUNDS FINAL PERMUTATION EXPANDED VIEW OF ROUNDS 2 & 3 SOURCE: cryptography. com 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

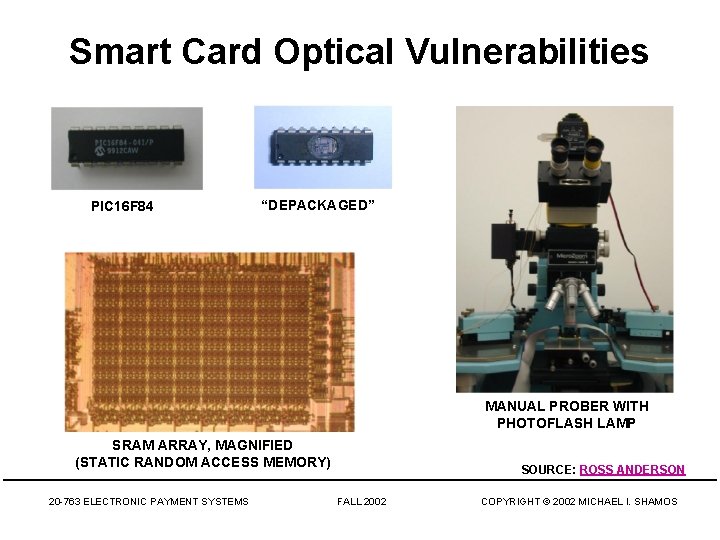
Smart Card Optical Vulnerabilities PIC 16 F 84 “DEPACKAGED” MANUAL PROBER WITH PHOTOFLASH LAMP SRAM ARRAY, MAGNIFIED (STATIC RANDOM ACCESS MEMORY) 20 -763 ELECTRONIC PAYMENT SYSTEMS SOURCE: ROSS ANDERSON FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

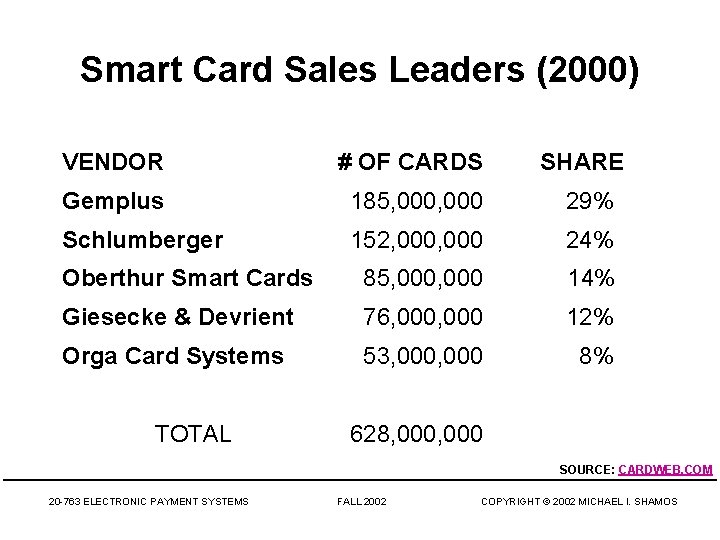
Smart Card Sales Leaders (2000) VENDOR # OF CARDS SHARE Gemplus 185, 000 29% Schlumberger 152, 000 24% Oberthur Smart Cards 85, 000 14% Giesecke & Devrient 76, 000 12% Orga Card Systems 53, 000 8% TOTAL 628, 000 SOURCE: CARDWEB. COM 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Octopus • Transaction time < 300 milliseconds • Transaction fees: HK$0. 02 + 0. 75% – $10 transaction costs $0. 095 (0. 95%) • Applications – – – Transit Telephones Road tolls Point-of-sale Access control • Anonymous / personalized • How does money get to service providers? – Net settlement system operated by Creative Star 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

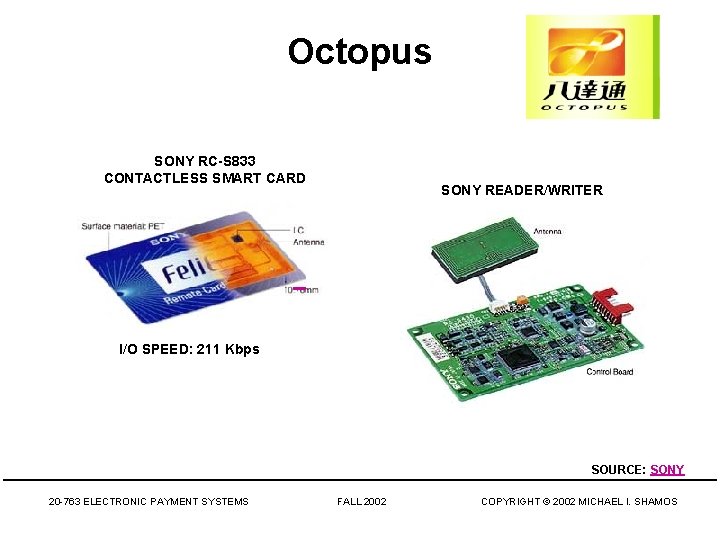
Octopus SONY RC-S 833 CONTACTLESS SMART CARD SONY READER/WRITER I/O SPEED: 211 Kbps SOURCE: SONY 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

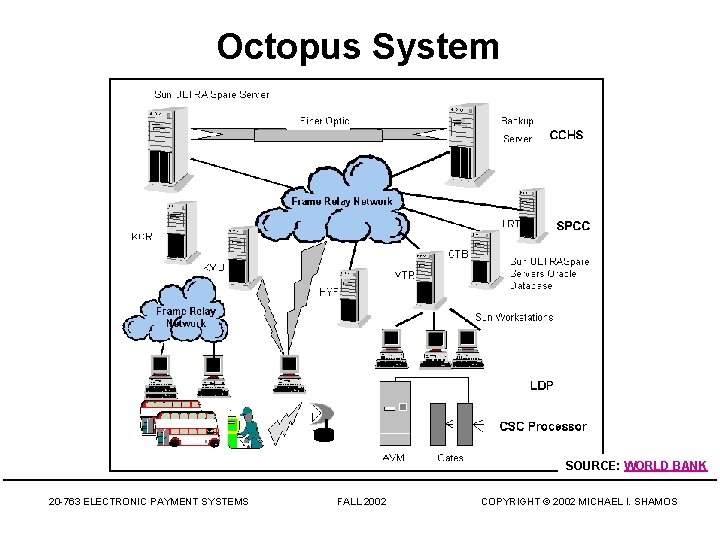
Octopus System SOURCE: WORLD BANK 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

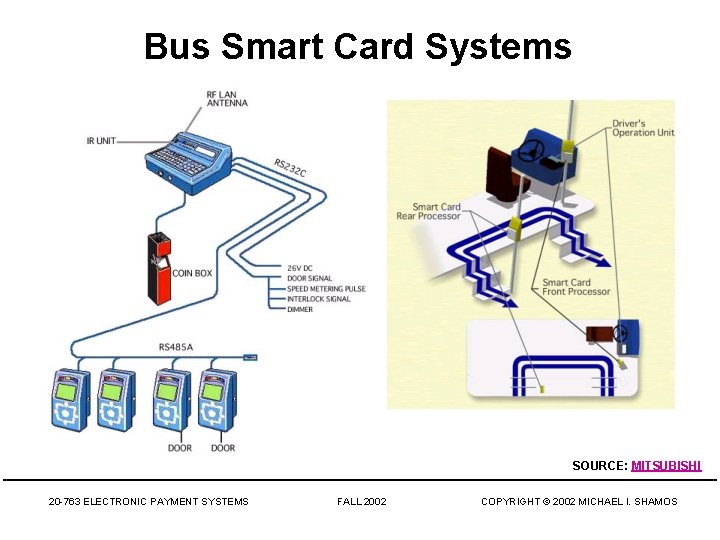
Bus Smart Card Systems SOURCE: MITSUBISHI 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

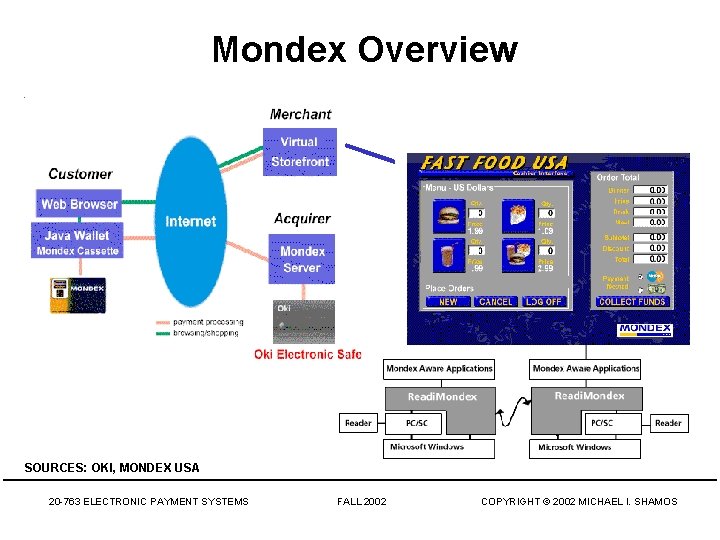
Mondex • • • Subsidiary of Master. Card Smart-card-based, stored-value card (SVC) Nat. West (National Westminister Bank, UK) et al. Secret chip-to-chip transfer protocol Value is not in strings alone; must be on Mondex card Loaded through ATM – ATM does not know transfer protocol; connects with secure device at bank • Spending at merchants having a Mondex value transfer terminal 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Mondex Overview SOURCES: OKI, MONDEX USA 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Mondex Security • Active and dormant security software – Security methods constantly changing – ITSEC E 6 level (military) • VTP (Value Transfer Protocol) – – Globally unique card numbers Globally unique transaction numbers Challenge-response user identification Digital signatures • MULTOS operating system – firewalls on the chip 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

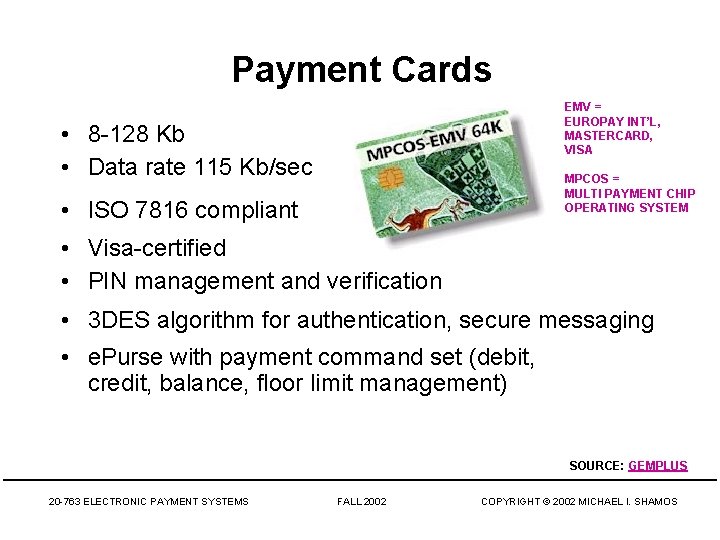
Payment Cards EMV = EUROPAY INT’L, MASTERCARD, VISA • 8 -128 Kb • Data rate 115 Kb/sec MPCOS = MULTI PAYMENT CHIP OPERATING SYSTEM • ISO 7816 compliant • Visa-certified • PIN management and verification • 3 DES algorithm for authentication, secure messaging • e. Purse with payment command set (debit, credit, balance, floor limit management) SOURCE: GEMPLUS 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

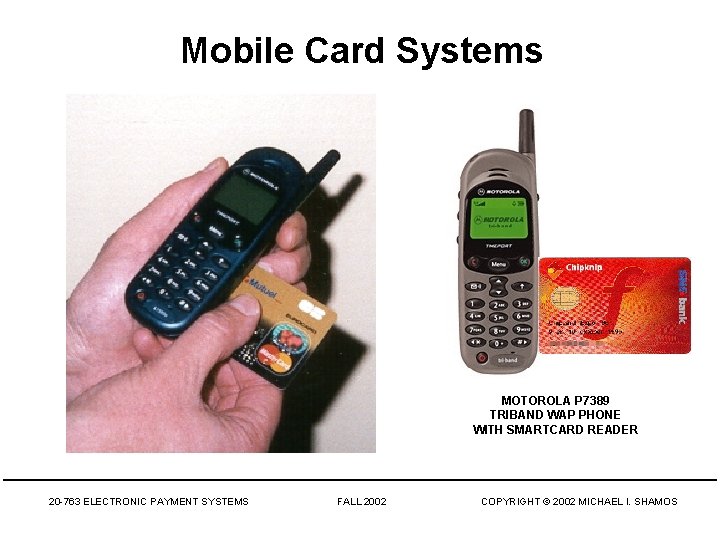
Mobile Card Systems MOTOROLA P 7389 TRIBAND WAP PHONE WITH SMARTCARD READER 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

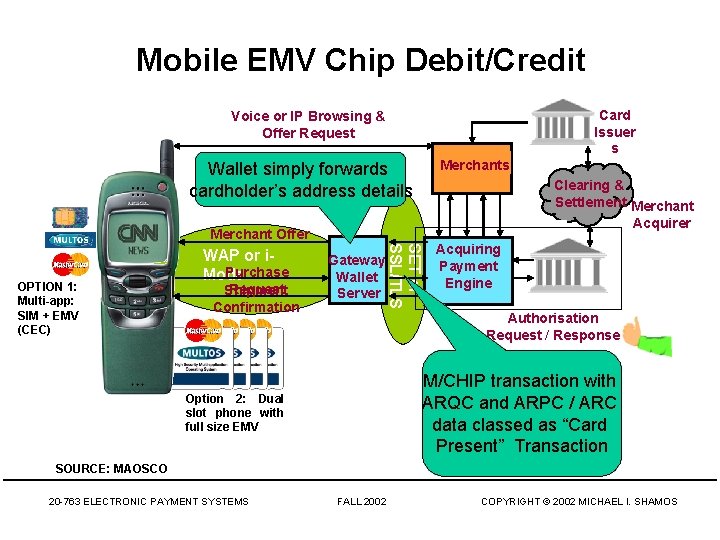
Mobile EMV Chip Debit/Credit Card Issuer s Voice or IP Browsing & Offer Request Merchants Wallet simply forwards cardholder’s address details Clearing & Settlement Merchant Acquirer Merchant Offer Request Shipment Confirmation Gateway Wallet Server SET or SSL/TLS OPTION 1: Multi-app: SIM + EMV (CEC) WAP or i. Purchase Mode Acquiring Payment Engine Authorisation Request / Response M/CHIP transaction with ARQC and ARPC / ARC data classed as “Card Present” Transaction Option 2: Dual slot phone with full size EMV SOURCE: MAOSCO 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Comparison of Payment Methods PAYMENT TYPE ADVANTAGES DISADVANTAGES Cash Anonymous, universal, Risk of theft/loss, bulky free Credit Card Almost universal High transaction cost, fraud/forgery EFTPOS Direct access to cash Must be online, security only moderate Disposable smart card Fast, private Risk of loss, limited to small amounts Personalized smart card Long useful life, security, like e. Cash Not anonymous, lack of international standards 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Major Ideas • Potential of cards is unexplored; new uses every day • Powerful microprocessors allow – cryptography – certificates, authentication – secure purses • Wireless (contactless) cards enable new business models • Huge capacity laser CD-DVD cards allow large databases of personalized information 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS

Q&A 20 -763 ELECTRONIC PAYMENT SYSTEMS FALL 2002 COPYRIGHT © 2002 MICHAEL I. SHAMOS