Electronic Engineering Mobile and Wireless Networking Lecture 21

Electronic Engineering Mobile and Wireless Networking Lecture 21 Dr. Xinbing Wang 1

Overview of the Course Part 1: Wireless communication systems (Chapter 1) – Flexibility to support roaming – Limitations: Geographical coverage, transmission rate, and transmission errors Part 2: Wireless communication technology – Radio propagation (Chapter 5) – Spread spectrum (Chapter 7) Part 3: Current wireless systems – Cellular network architecture (Chapter 10) – Mobile IP (Chapter 12) – Wireless LAN (Chapter 11/13/14) Part 4: Other wireless networks – – Ad hoc networks (Reading materials) Sensor networks (Reading materials) Wireless PAN (Chapter 15) Satellite systems (Chapter 9) Part 5: Wireless Security Electronic Engineering Dr. Xinbing Wang 2

Security in Wireless Networks Wireless security issues General topics on security Layered security solutions Security solutions in wireless networks – Security in UMTS – Security in Mobile IP networks – WLANs: WEP Secure AODV for mobile ad hoc networks Electronic Engineering Dr. Xinbing Wang 3

Security Principles Authentication Access control and authorization Nonrepudiation – A user/process be identifiable and accountable for its actions in a manner that prohibits the user or process from denying its involvement at a late date. Privacy and confidentiality – – – To protect information from unauthorized disclosure. A very tricky and contentious issue ( be anonymous and confidential). Cryptography, steganography, digital watermarking. Integrity – To verify the accuracy of what is sent or delivered and that the process/component has not been altered in some way (often, take for granted). Auditing: to review the activities to ensure that whatever was performed was appropriate for the given entity. Electronic Engineering Dr. Xinbing Wang 4

WLAN: Wired Equivalent Privacy (WEP) Protocol As its name, the goal of WEP is to provide a level of privacy that is equivalent to a wired LAN. The WEP algorithm is used – To protect wireless networks from eavesdropping. – To prevent unauthorized access to wireless networks. WEP replies on a default set of keys that are shared between wireless devices and APs. – A client with the correct key can communicate with any AP on the wireless network; without the key, a link-level connection request is rejected. – If it is configured to do so, the wireless devices and APs will also encrypt data before transmitting it, and an integrity check ensures that packets are not modified in transit. Electronic Engineering Dr. Xinbing Wang 5
Authentication Frame Based on an RSA RC 4 (stream cipher) algorithm, this simple WEP algorithm has following properties – Reasonably strong: a brute force attack on this algorithm is difficult because every frame is sent with an initialization vector (IV), which restarts the Pseudo. Random Number Generator (PRNG) for each frame. – Self-synchronizing: like in any LANs, the wireless stations work in a connectionless environment where packets may get lost. The WEP algorithm resynchronizes at each message. Electronic Engineering Dr. Xinbing Wang 6
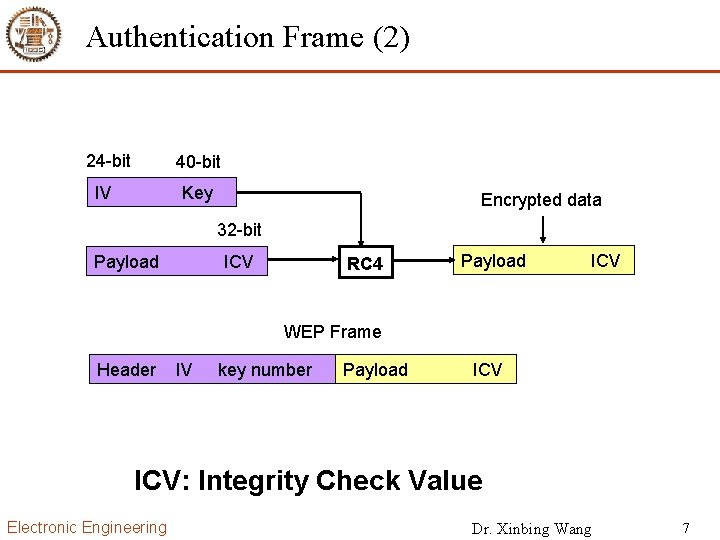
Authentication Frame (2) 24 bit 40 bit IV Key Encrypted data 32 bit Payload ICV RC 4 Payload ICV WEP Frame Header IV key number Payload ICV: Integrity Check Value Electronic Engineering Dr. Xinbing Wang 7

Access Control List Access control list can provide a minimal level of security. – It is based on the Ethernet MAC addresses of the clients. – This list consists of the MAC addresses of all of its clients and only the clients whose MAC addresses are listed can access. Electronic Engineering Dr. Xinbing Wang 8

Using the WEP There are two methods specified in IEEE 802. 11 for using the WEP. – A station or an AP can decrypt packets enciphered with any of four keys (provided through a window). – To use key-mapping table where each unique MAC address can have separate keys. The use of a separate key for each client mitigates the cryptographic attacks found by others. The disadvantage is that all of these keys should be configured manually on each device or AP. Electronic Engineering Dr. Xinbing Wang 9

Weakness in WEP is weak against the following attacks (RC 4 and IV) – Active attacks that inject new traffic from unauthorized mobile stations The attack knows the exact plain text for one encrypted message. – Active attacks to decrypt traffic based on fooling the APs. The attacker fools the AP: it makes a guess about the header of the packet; not the packet’s content. All he/she needs to do is to guess the destination address. Electronic Engineering Dr. Xinbing Wang 10

Weakness in WEP (2) – Passive attacks to decrypt traffic based on statistical analysis. An eavesdropper can intercept all wireless traffic until an IV collision occurs. By using XOR of two plain text messages, the attacker can obtain the same IV value. – Dictionary-building attacks which allow real-time automated decryption of traffic after some analysis. Once the plain text for the packet is known, the attacker can compare the RC 4 key stream generated by the IV. The latter can be used to decrypt all other packets that utilize the same IV. Electronic Engineering Dr. Xinbing Wang 11

Security in Ad hoc Networks Liabilities in Ad Hoc Networks – – – Limited physical security Lack of infrastructure and authorization facilities Security protocols for wired networks cannot work for ad hoc networks Volatile network topology makes it hard to detect malicious nodes Intrinsic mutual trust vulnerable to attacks Electronic Engineering Dr. Xinbing Wang 12

Exploits Allowed by Existing Protocols Attacks using modification Attacks using impersonation Attacks using fabrication Other forms of attacks Electronic Engineering Dr. Xinbing Wang 13
Attacks using Modification Cause redirection of network traffic and Denial of Service (Do. S) attacks by – Altering the protocol fields in routing messages – Injecting routing messages into the network with falsified values in these fields. Electronic Engineering Dr. Xinbing Wang 14
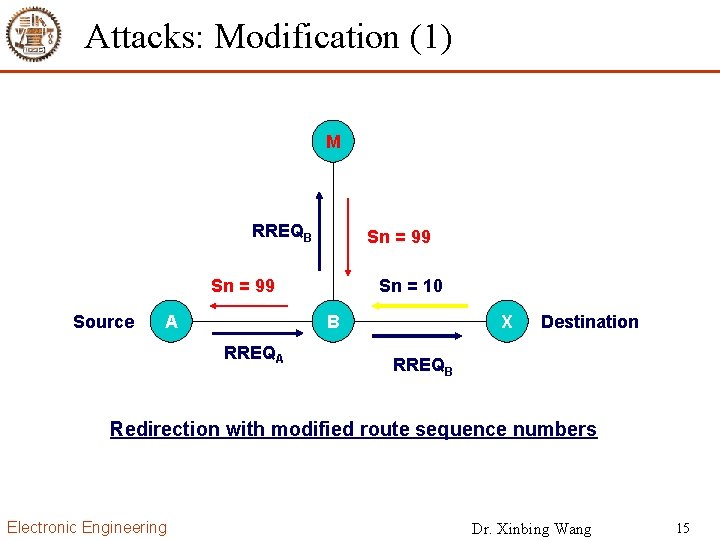
Attacks: Modification (1) M RREQB Sn = 99 Source A Sn = 10 B RREQA X Destination RREQB Redirection with modified route sequence numbers Electronic Engineering Dr. Xinbing Wang 15
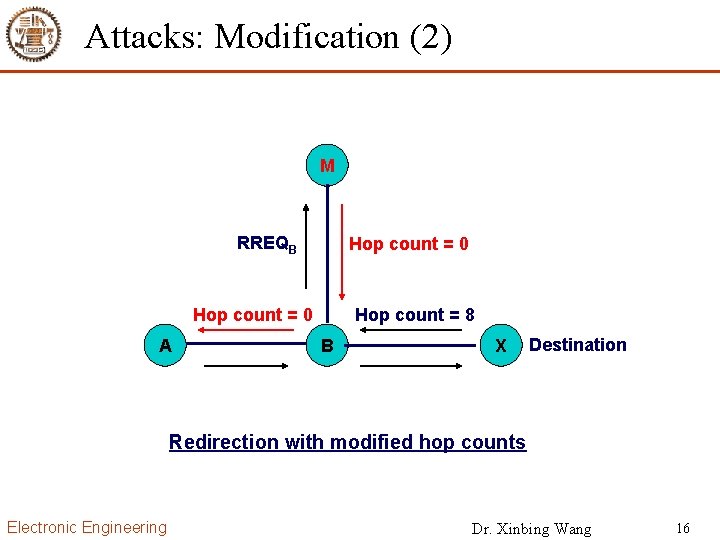
Attacks: Modification (2) M RREQB Hop count = 0 Source A Hop count = 8 B RREQA X Destination RREQB Redirection with modified hop counts Electronic Engineering Dr. Xinbing Wang 16
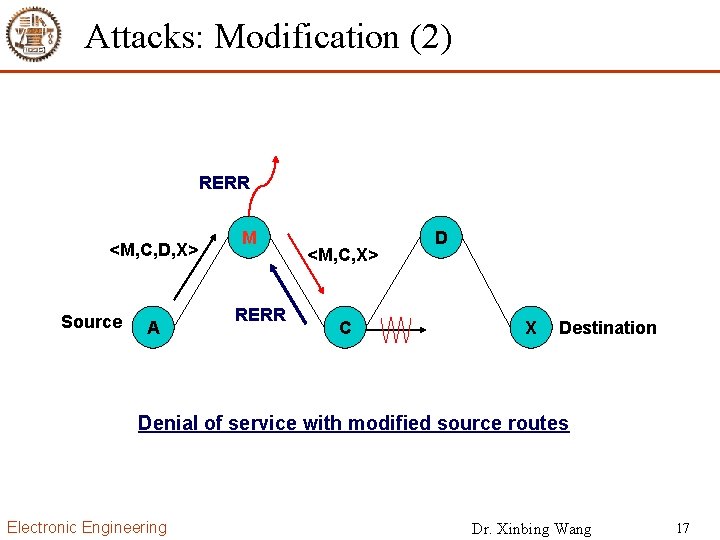
Attacks: Modification (2) RERR <M, C, D, X> Source A M RERR <M, C, X> C D X Destination Denial of service with modified source routes Electronic Engineering Dr. Xinbing Wang 17
Attacks: Impersonation Current ad hoc routing protocols do not authenticate source IP addresses By masquerading as another node (spoofing), a malicious node can launch many attacks in a network Spoofing is readily combined with modification attacks to create loops in routes Electronic Engineering Dr. Xinbing Wang 18
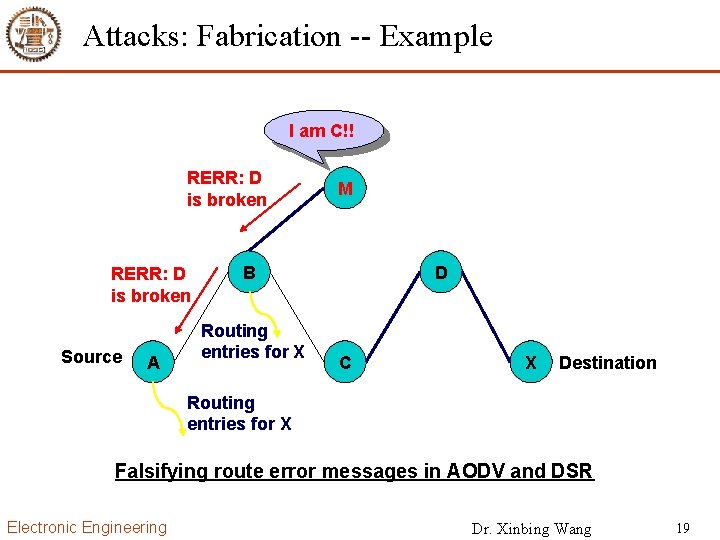
Attacks: Fabrication -- Example I am C!! RERR: D is broken Source A M B Routing entries for X D C X Destination Routing entries for X Falsifying route error messages in AODV and DSR Electronic Engineering Dr. Xinbing Wang 19
Attacks: Fabrication in DSR Route Cache Poisoning in DSR – Exploit promiscuous listening to poison route caches – By broadcasting spoofed packets with source routes to X via itself – Neighbouring nodes that overhear the packet transmission may add the route to their route cache Electronic Engineering Dr. Xinbing Wang 20

SAODV An extension of the AODV routing protocol Providing security features like integrity, authentication and non repudiation Each node has a signature key pair from a suitable asymmetric cryptosystem Each node is capable of securely verifying the association between the address of a given ad hoc node and the public key of that node Electronic Engineering Dr. Xinbing Wang 21

SAODV: Digital Signature Used to protect the integrity of the non mutable data in RREQ and RREP messages Sign everything but the Hop Count of the AODV message and the Hash from the SAODV extension When a node receives a routing message, it will verify the signature before any other action Electronic Engineering Dr. Xinbing Wang 22

SAODV: Hash Chains Used to authenticate the hop count of RREQ and RREP messages Ensures that the hop count has not been decremented by an attacker Is formed by applying a one-way hash function repeatedly to a seed Electronic Engineering Dr. Xinbing Wang 23

SAODV: Route Errors Route errors have a big amount of mutable information Every node uses digital signatures to sign the whole message Any neighbor that receives it verifies the signature Electronic Engineering Dr. Xinbing Wang 24

Security Analysis: SAODV (1) The digital signature serves as proof of validity of the information contained in the routing message Thus, formation of loops by malicious nodes through spoofing is prevented – Able to detect that the malicious nodes are sending out false messages. Electronic Engineering Dr. Xinbing Wang 25

Security Analysis: SAODV (2) A node attempting to transmit false RERR messages will not succeed – Digital signature will reveal that it is not on the route and hence is not supposed to send a RERR. Sequence number in the RREQs and RREPs also protected by the digital signature. – Any modifications to the sequence number will invalidate the message Electronic Engineering Dr. Xinbing Wang 26
Security Analysis: SAODV (3) The hop authenticator implemented using hash chains reduces the ability of a malicious node for mounting an attack by modifying the hop count A malicious node could still perform a limited attack by not incrementing the hop count before forwarding the message. – Can solve by implementing a forward-secure signature scheme. – Results in a loss in efficiency Electronic Engineering Dr. Xinbing Wang 27

Summary SAODV is able to handle all attacks using modification, fabrication or impersonation However, it is unable to cope with wormhole attacks. Electronic Engineering Dr. Xinbing Wang 28
- Slides: 28