Election Cybersecurity 101 cybersecurity best practices and techniques

Election Cybersecurity 101 cybersecurity best practices and techniques to prevent, defeat or mitigate cyber threats 2020 IACRC Elections Conference January 9, 2020
Introduction to CDT About CDT At the Center of Democracy and Technology, we believe in the power of the internet. Whether it’s facilitating entrepreneurial endeavors, providing access to new markets and opportunities, or creating a platform for free speech, the internet empowers, emboldens, and equalizes people around the world. About Maurice Roles Deputy Director/Senior Technologist Technology Fellow (US Senate) Local Government Manager Election Volunteer Education Public Administration Political Science Cybersecurity Strategy
Overview ● Why ○ ● Even more Risk-based approach ○ ○ ○ ● Ripped from the headlines What You Can Do ○ ● Terminology Scenarios ○ ● NIST Framework Security controls Security procedures Funding ○ ○ ○ What have you done since 2016? How did you spend HAVA 2018 $$ How will you spend HAVA 2019 $$ Scenarios from 101 & 201 Experiences ○ Threats ○ ● Voter confidence Cybersecurity Basics ○ ● ● ○ Tell us how you have responded to a specific cyber incident? What information have you received from an ISAC? Have you shared any?
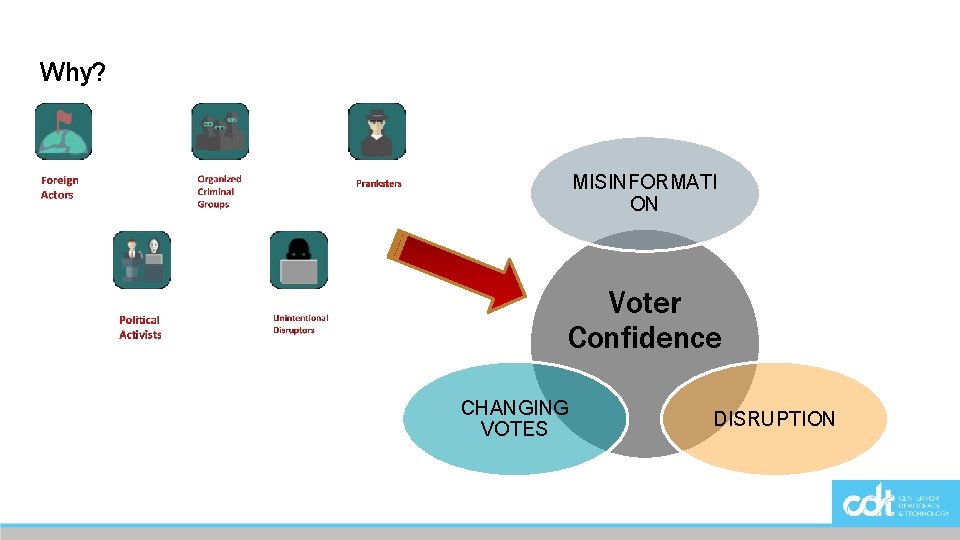
Why? MISINFORMATI ON Voter Confidence CHANGING VOTES DISRUPTION

Cybersecurity Basics Scan: Using a program to identify vulnerabilities in a system Hack: Unauthorized use or access Breach: Compromise of security that exposes data Malware (ransomware): Malicious software to compromise data or a system Phishing (spearphishing): Tricking users into providing personal information or access Denial of service (DDo. S): An attack that blocks access to information or services

Threats Ransomware Baltimore Louisiana Texas Disruption Knox County, TN Misinformation Florida “The fact that we are seeing an acceleration of attacks that are reportedly successful tells me that we have not prepared, ” said Eddie Habibi, CEO of industrial systems security company PAS Global. While many industrial systems are administered on unique systems that “require greater sophistication, ” Habibi explained, “some of these [ransomware] attacks are made on the Windows operating system that is used to run the utilities that run power plants or water utilities. Consequences of attacks on the industrial sector can be a lot more serious than on data, ” he said. (August 22, 2019)
What Can Do You? ● ● Protect access to your systems & communication channels ○ Enable two-factor authentication, password managers ○ Microsoft and Google offer advanced account protection to detect attacks to email Establish yourself as an authentic source of information ○ Join social networks (Twitter, Facebook, Snapchat) to broadcast your message using the same communication channels ○ Transition to DMARC for email and. gov for website to prevent impersonation Develop & practice emergency responses ○ Incorporate elections activities into business continuity & disaster recovery plans (test your backups) ○ Use table top exercises (TTX) to build confidence and identify gaps in procedures Identify, recruit, and train civic-minded community members with technical skills or IT support experience as technical volunteers ○ Resolve minor issues on Election Day, Assist with security-related pre-election and post-election activities

What More Can You Do? Center for Internet Security Controls (top 20 data security steps) Start with the Top 5 to build an organizational culture of

Risk-based Approach Risk = Probability x Impact ● Objective is to mitigate not eliminate risk (zero risk impossible & impractical) ○ ○ ○ ● Identify & prioritize all assets ○ ○ ○ ● Reduce impact (backups) Shift risk (insurance, partnerships) Accept risk (improbable acts) What does the organization care about? What is likely to happen? What is the worst that can happen? Continuous monitoring & reassessment ○ ○ What has changed about the threat(s)? What has changed about the organization’s priorities?

Security Procedures Administrative controls Defined & documented roles, responsibilities, policies Technical controls Defense in depth by design Physical controls Locks, seals, surveillance, chain of custody, inventory
Additional Resources Center for Democracy & Technology Election Privacy & Security Project Center for Technology & Civic Life Online Series: Cybersecurity for Election Officials DHS Cybersecurity & Infrastructure Security Agency Election Security Resources Guide Election Assistance Commission Election Security Preparedness Harvard Belfer Center Defending Digital Democracy Project Cyberscoop List of free/low-cost security products & services

Funding 2018 HAVA Security Grant $3. 4 M to Idaho 2019 Federal Appropriation $4. 3 M to Idaho 2020 Federal Grants ? ? ? to Idaho What have you been able to accomplish since 2018? What could you accomplish with additional funding in 2020?
Scenarios How do you respond? What are the risks? How can those risks be mitigated? A news report indicated that some of your optical scan ballot counting equipment has the ability for the vendor you bought it from to “remote access” the software. You thought your systems were “airgapped” and secure. A local election official has fallen prey to a spearphishing attack that has permitted nefarious actors access to the statewide voter registration database. It is unclear if any voter registration records have been changed. #Idaho. Hacked is trending on Twitter due to reports that your election night reporting website has been defaced with pro-Iran messages. Some accounts are claiming that votes have been changed.

Share Your Experiences Tell us how you have responded to a specific cyber incident? What worked? What didn’t worked? How did you improve? How has your communication with your security partners improved? What threat information have you received from SOS, ISAC, DHS, others? How was that threat information actionable by you? What threat information have you shared to SOS, ISAC, DHS, others?
63 Days Until Presidential Primary Election

Maurice Turner | Deputy Director E: maurice@cdt. org | T: @Type. MRT
- Slides: 16