EGIIn SPIRE Pakiti EGIIn SPIRE RI261323 www egi











- Slides: 19

EGI-In. SPIRE Pakiti EGI-In. SPIRE RI-261323 www. egi. eu

Pakiti Overview • Patch monitoring • Unpatched vulnerabilities present severe security threat • Client - server architecture • In production use by EGI CSIRT • Nagios probe against WNs • https: //pakiti. egi. eu/ • Development by EGI CSIRT EGI-In. SPIRE RI-261323 www. egi. eu

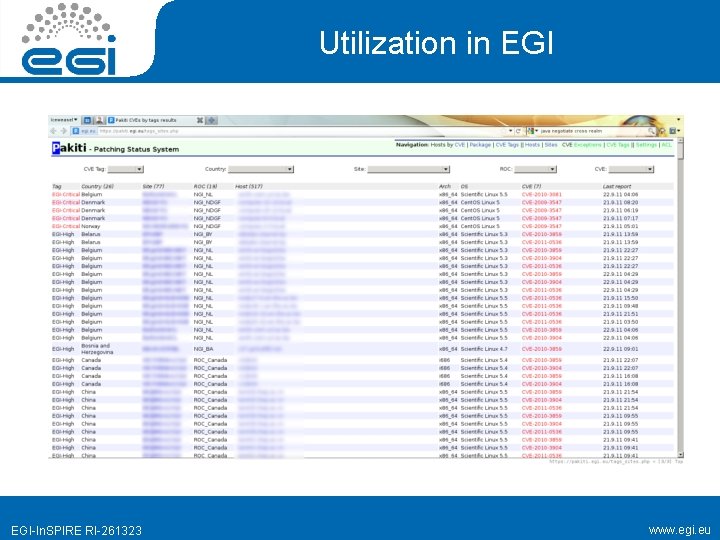
Utilization in EGI-In. SPIRE RI-261323 www. egi. eu

Excerise • Install your own Pakiti server • Collect report from a node • Identify unpatched vulnerabilities EGI-In. SPIRE RI-261323 www. egi. eu

Installation steps • • • Installation of server package Configuration of Apache Configuration of My. SQL Configuration of Pakiti server Using Pakiti client EGI-In. SPIRE RI-261323 www. egi. eu

Server package • RPM from EGI App. DB 1. rpm --import http: //pgp. mit. edu/pks/lookup? op=get&sear ch=0 x 930 D 2233 A 28 C 25 A 6 2. wget -O /etc/yum. repos. d/pakiti. repo http: //repository. egi. eu/community/software/ pakiti/pakiti 2/releases/repofiles/sl-6 i 386. repo 3. yum update 4. yum install pakiti 2 -server EGI-In. SPIRE RI-261323 www. egi. eu

Apache Configuration • Enable https and Pakiti virtual host 1. Remove default https virtual host • /etc/httpd/conf. d/ssl. conf 2. Copy Pakiti definition • cp /usr/share/doc/pakiti 2 -server 2. 1. 6/pakiti 2. apache 2 /etc/httpd/conf. d/pakiti 2. conf 3. Adapt to your preferred auth. N system 4. Check firewall configuration EGI-In. SPIRE RI-261323 www. egi. eu

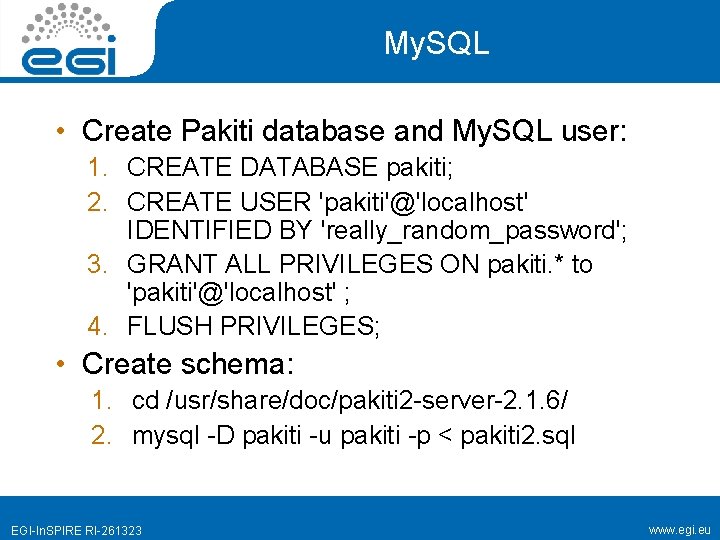
My. SQL • Create Pakiti database and My. SQL user: 1. CREATE DATABASE pakiti; 2. CREATE USER 'pakiti'@'localhost' IDENTIFIED BY 'really_random_password'; 3. GRANT ALL PRIVILEGES ON pakiti. * to 'pakiti'@'localhost' ; 4. FLUSH PRIVILEGES; • Create schema: 1. cd /usr/share/doc/pakiti 2 -server-2. 1. 6/ 2. mysql -D pakiti -u pakiti -p < pakiti 2. sql EGI-In. SPIRE RI-261323 www. egi. eu

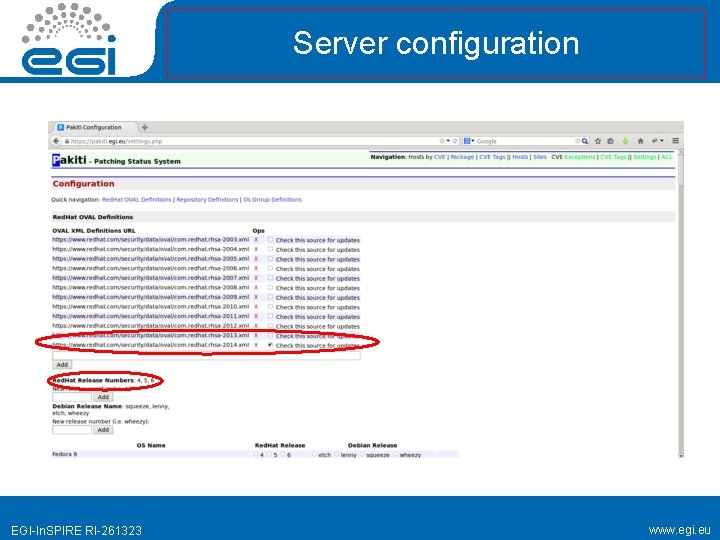
Pakiti server • Update mysql password/username: 1. /etc/pakiti 2 -server. conf • Browse to https: //server/ and adapt Settings (top right) 1. http: //www. redhat. com/security/data/oval/co m. redhat. rhsa-2014. xml 2. Release 4, 5, 6 EGI-In. SPIRE RI-261323 www. egi. eu

Server configuration EGI-In. SPIRE RI-261323 www. egi. eu

Putting it together • Install Pakiti client 1. yum install pakiti 2 -client-manual • Configure the client • /usr/share/doc/pakiti 2 -client-manual 2. 1. 6/pakiti 2 -client 1. SERVERS="localhost: 443“ 2. #CA_PATH="/etc/ssl/certs/" • Run the client and check the results EGI-In. SPIRE RI-261323 www. egi. eu

EGI-In. SPIRE Central Log Collecting EGI-In. SPIRE RI-261323 www. egi. eu

Motivation • Logs can point to an attack and vector • Attackers wipe logs once they have root access • Having logs stored locally doesn’t scale • A single point where to analyse data • Local logs are not trustworthy EGI-In. SPIRE RI-261323 www. egi. eu

Solutions • syslog, former default logging system • replaced by rsyslog (syslog clients can send to rsyslog) • syslog-ng (OSE and Premium Edition, additional plugins under proprietary license) • Commercial solutions • splunk (volume based licensing/can get expensive) EGI-In. SPIRE RI-261323 www. egi. eu

Rsyslog Server • Decide whether secure channel is required • TLS is supported • Decide what directory structure is needed • Make sure you have free space on storage • Enable monitoring of the server • Rsyslog is well documented EGI-In. SPIRE RI-261323 www. egi. eu

Rsyslog client • Decide what message to send out • Find out security requirements 1. $Default. Netstream. Driver. CAFile /etc/ssl/certs/Add. Trust_External_Root. pem 2. $Default. Netstream. Driver gtls 3. $Action. Send. Stream. Driver. Mode 1 4. $Action. Send. Stream. Driver. Auth. Mode x 509/certvalid # server is NOT authenticated 5. *. * @@(o)147. 251. 252. 199: 10514 EGI-In. SPIRE RI-261323 www. egi. eu

Processing Collected Data • Usual tools like grep, etc. • Files are available from /var/log/remote-hosts • More volumes data needs advanced tools • Indexing, filtering • Elastic. Search, Kibana • Processing logs using cloud tools • http: //home. zcu. cz/~bodik/metasw/esbegitf/ EGI-In. SPIRE RI-261323 www. egi. eu

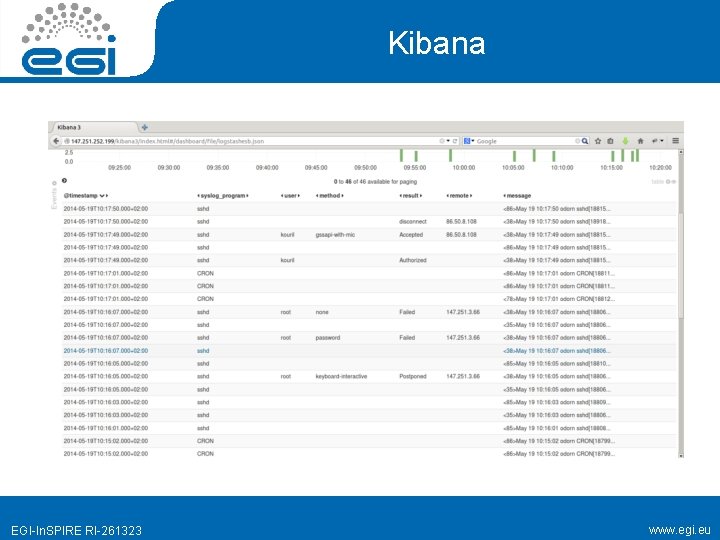
Kibana EGI-In. SPIRE RI-261323 www. egi. eu

Excercise • Configure your client to log remotely • 147. 251. 252. 199 is provided as a VO server • Check the log contents • Files • ssh cf@147. 251. 252. 199 • /var/log/remote-hosts • Kibana: • http: //147. 251. 252. 199/kibana 3/index. html#/dash board/file/logstashesb. json EGI-In. SPIRE RI-261323 www. egi. eu

































