Efficient Memory Shadowing for 64 bit Architectures Qin

Efficient Memory Shadowing for 64 -bit Architectures Qin Zhao (MIT) Derek Bruening (VMware) Saman Amarasinghe (MIT) ISMM 2010, Toronto, Canada June 6, 2010
Dynamic Program Analysis • Understand Program Behavior – – Optimization Debugging Security Memory management • Shadow Memory Tools – Maintain meta-data for every memory location – Update meta-data on every memory operation ISMM, Toronto, Canada, 6/6/2010 2
![Examples • Memory Error Detection – Mem. Check [VEE’ 07] – Purify [USENIX’ 92] Examples • Memory Error Detection – Mem. Check [VEE’ 07] – Purify [USENIX’ 92]](http://slidetodoc.com/presentation_image_h2/d32b6595b83df18b46f44f4b74ee55ee/image-3.jpg)
Examples • Memory Error Detection – Mem. Check [VEE’ 07] – Purify [USENIX’ 92] – Dr. Memory • Dynamic Information Flow Tracking – LIFT [MICRO’ 39] – Taint. Trace [ISCC’ 06] • Multi-threaded Program Analysis – Eraser [TCS’ 97] – Helgrind • Memory Usage Analysis – CETS [ISMM’ 10] – Staleness ISMM, Toronto, Canada, 6/6/2010 3
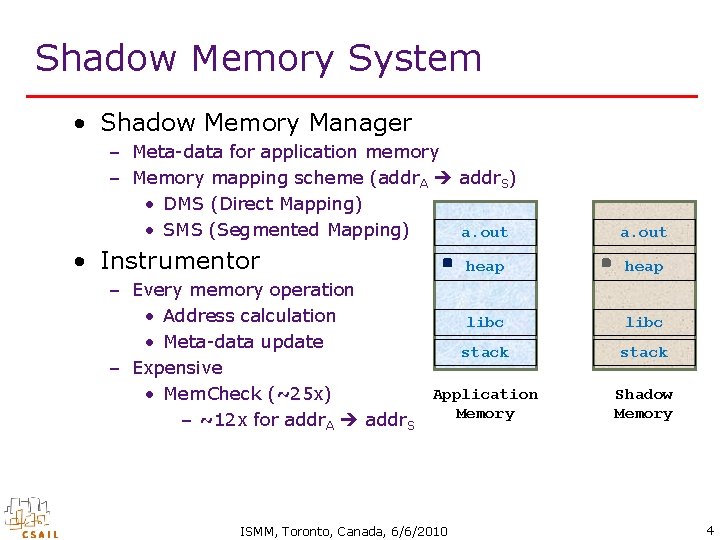
Shadow Memory System • Shadow Memory Manager – Meta-data for application memory – Memory mapping scheme (addr. A addr. S) • DMS (Direct Mapping) • SMS (Segmented Mapping) a. out • Instrumentor heap – Every memory operation • Address calculation libc • Meta-data update stack – Expensive Application • Mem. Check (~25 x) Memory – ~12 x for addr. A addr. S ISMM, Toronto, Canada, 6/6/2010 a. out heap libc stack Shadow Memory 4
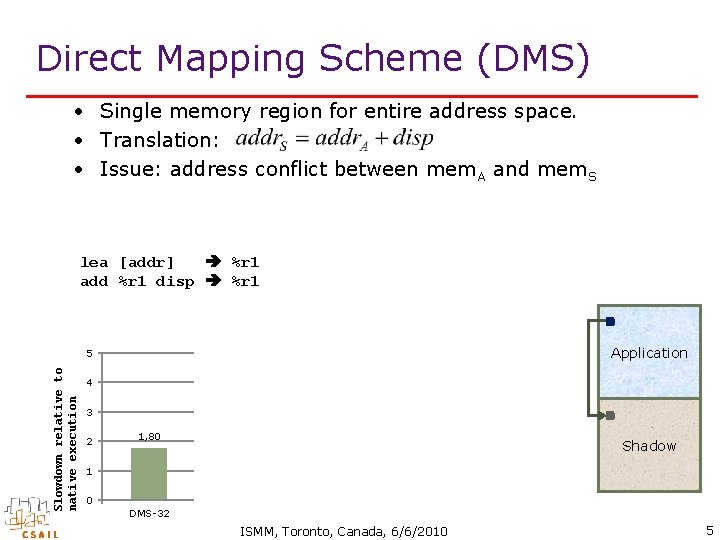
Direct Mapping Scheme (DMS) • Single memory region for entire address space. • Translation: • Issue: address conflict between mem. A and mem. S lea [addr] %r 1 add %r 1 disp %r 1 Slowdown relative to native execution 5 4, 67 Application 4 3 2 2, 40 1, 80 Shadow 1 0 DMS-32 SMS-32 DMS-64 SMS-64 ISMM, Toronto, Canada, 6/6/2010 5
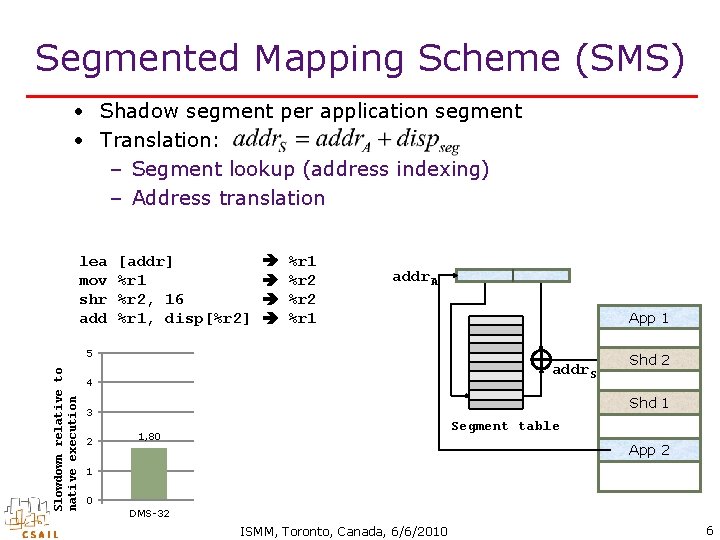
Segmented Mapping Scheme (SMS) • Shadow segment per application segment • Translation: – Segment lookup (address indexing) – Address translation lea mov shr add [addr] %r 1 %r 2, 16 %r 1, disp[%r 2] %r 1 %r 2 %r 1 addr. A App 1 Slowdown relative to native execution 5 4, 67 addr. S 4 Shd 1 3 2 Shd 2 2, 40 Segment table 1, 80 App 2 1 0 DMS-32 SMS-32 DMS-64 SMS-64 ISMM, Toronto, Canada, 6/6/2010 6
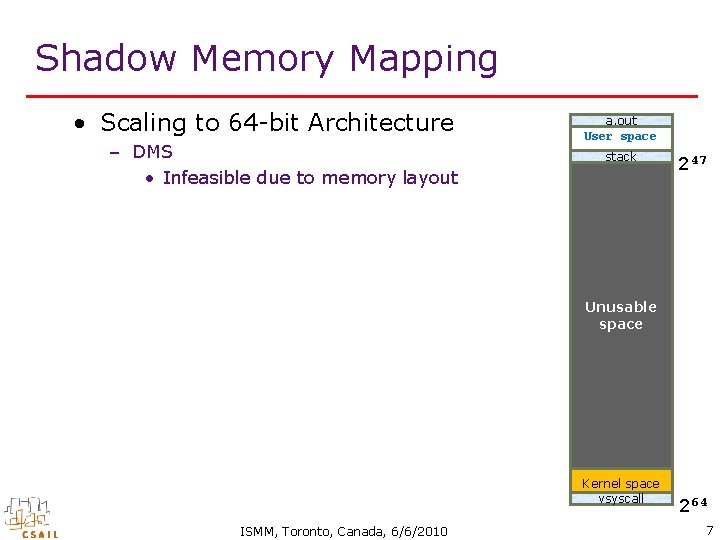
Shadow Memory Mapping • Scaling to 64 -bit Architecture – DMS • Infeasible due to memory layout a. out User space stack 247 Unusable space Kernel space vsyscall ISMM, Toronto, Canada, 6/6/2010 264 7
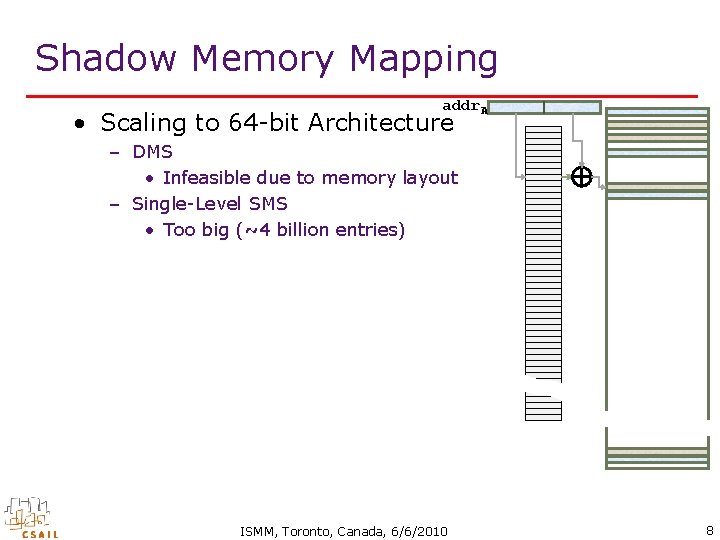
Shadow Memory Mapping addr. A • Scaling to 64 -bit Architecture – DMS • Infeasible due to memory layout – Single-Level SMS • Too big (~4 billion entries) ISMM, Toronto, Canada, 6/6/2010 8
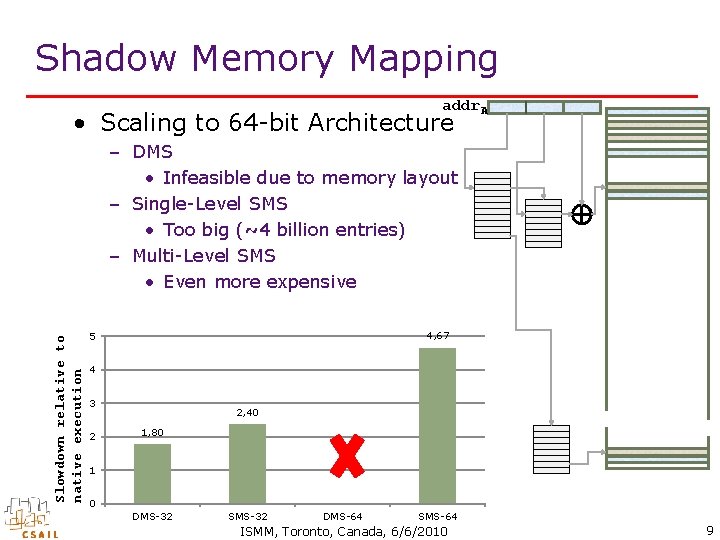
Shadow Memory Mapping addr. A • Scaling to 64 -bit Architecture Slowdown relative to native execution – DMS • Infeasible due to memory layout – Single-Level SMS • Too big (~4 billion entries) – Multi-Level SMS • Even more expensive 4, 67 5 4 3 2 2, 40 1, 80 1 0 DMS-32 SMS-32 DMS-64 SMS-64 ISMM, Toronto, Canada, 6/6/2010 9
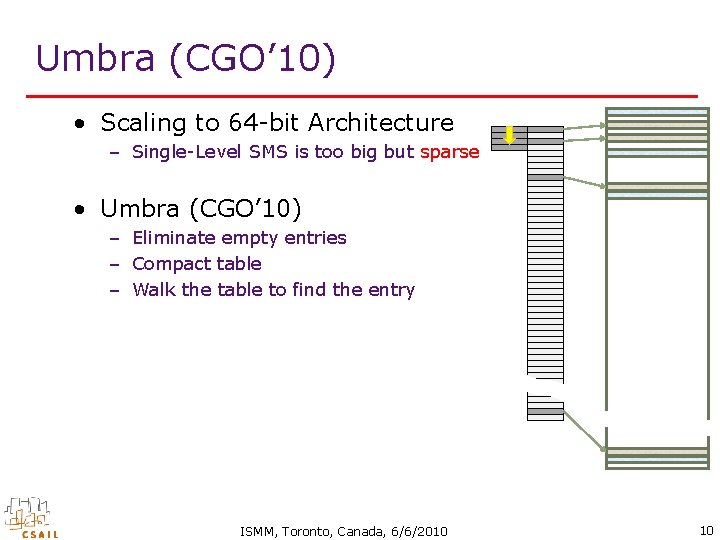
Umbra (CGO’ 10) • Scaling to 64 -bit Architecture – Single-Level SMS is too big but sparse • Umbra (CGO’ 10) – Eliminate empty entries – Compact table – Walk the table to find the entry ISMM, Toronto, Canada, 6/6/2010 10
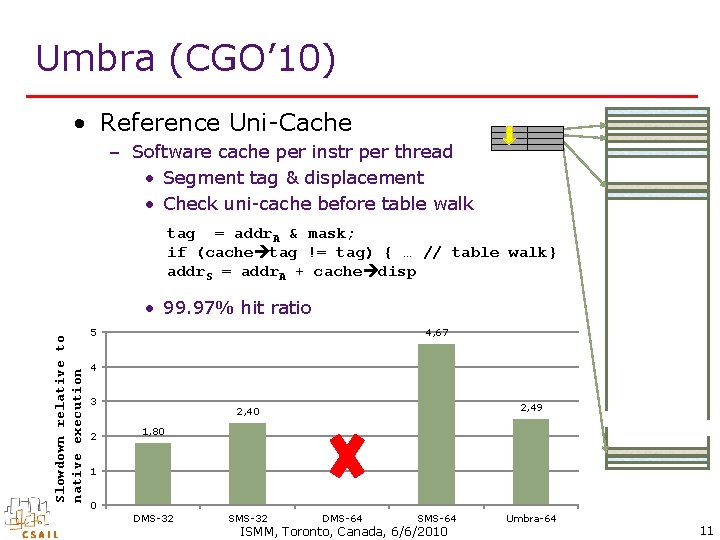
Umbra (CGO’ 10) • Reference Uni-Cache – Software cache per instr per thread • Segment tag & displacement • Check uni-cache before table walk tag = addr. A & mask; if (cache tag != tag) { … // table walk} addr. S = addr. A + cache disp Slowdown relative to native execution • 99. 97% hit ratio 4, 67 5 4 3 2 2, 49 2, 40 1, 80 1 0 DMS-32 SMS-32 DMS-64 SMS-64 ISMM, Toronto, Canada, 6/6/2010 Umbra-64 11

EMS 64: Key Idea • Umbra tag = addr. A & mask; if (cache tag != tag) { … // table walk (0. 03%)} addr. S = addr. A + cache disp • EMS 64 – Speculatively use a disp without check – Smart shadow memory placement • Notified by memory access violation fault for incorrect displacement ISMM, Toronto, Canada, 6/6/2010 12
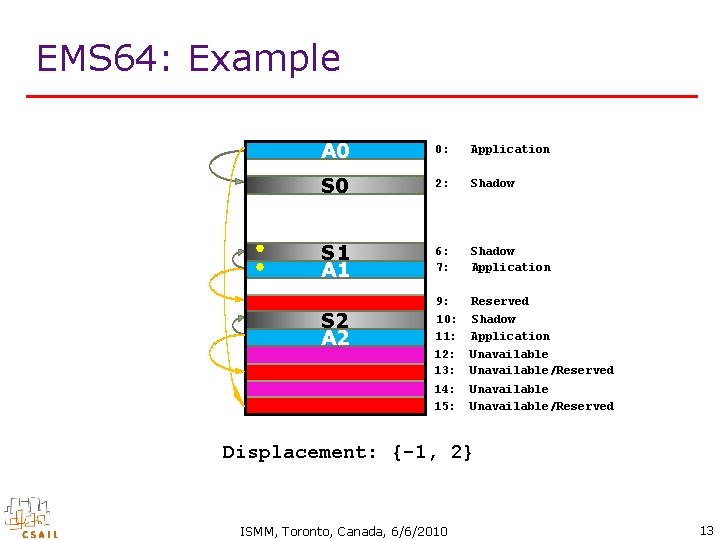
EMS 64: Example A 0 0: Application S 0 2: Shadow S 1 A 1 6: 7: Shadow Application 9: 10: 11: Reserved Shadow Application 12: 13: Unavailable/Reserved 14: 15: Unavailable/Reserved S 2 A 2 Displacement: {-1, 2} ISMM, Toronto, Canada, 6/6/2010 13
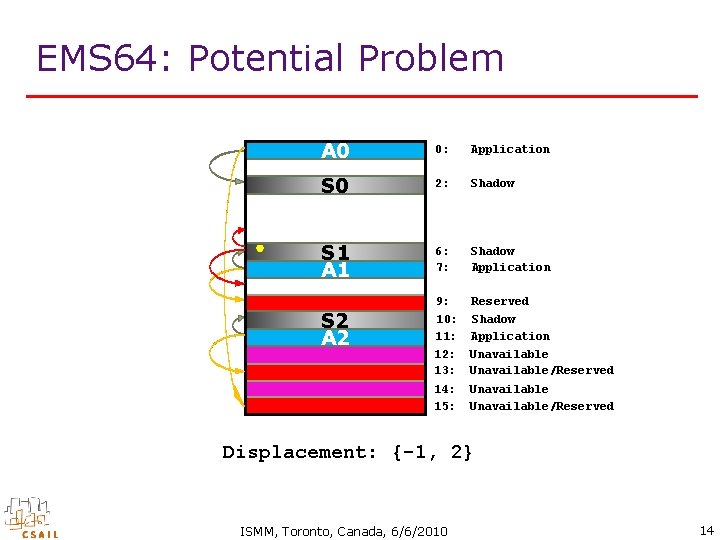
EMS 64: Potential Problem A 0 0: Application S 0 2: Shadow S 1 A 1 6: 7: Shadow Application 9: 10: 11: Reserved Shadow Application 12: 13: Unavailable/Reserved 14: 15: Unavailable/Reserved S 2 A 2 Displacement: {-1, 2} ISMM, Toronto, Canada, 6/6/2010 14
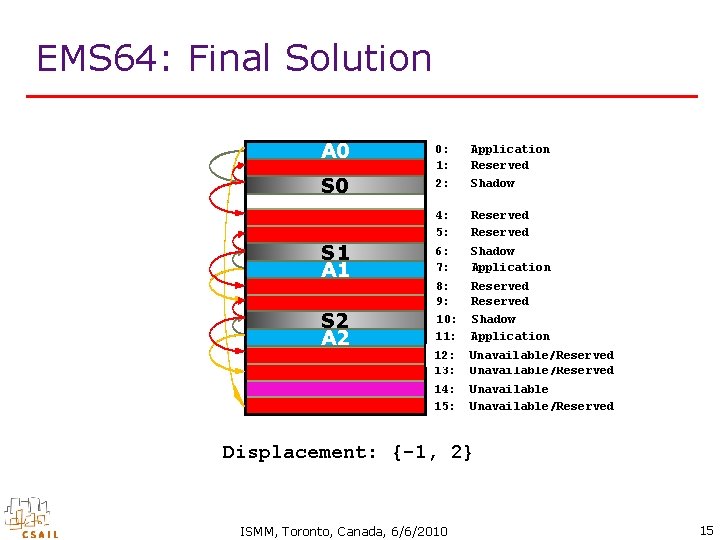
EMS 64: Final Solution A 0 0: 1: Application Reserved S 0 2: Shadow 4: 5: Reserved 6: 7: Shadow Application 8: 9: 10: 11: Reserved Shadow Application 12: 13: Unavailable/Reserved 14: 15: Unavailable/Reserved S 1 A 1 S 2 A 2 Displacement: {-1, 2} ISMM, Toronto, Canada, 6/6/2010 15

Slot Finding Problem • Given n slots: – k Application slots – x Empty slots – y Reserved slots • Find k S-slots. Ai Application slot Si Shadow slot Ei Empty slot Ri Reserved slot – For each slot A , there is one associated slot S with displacement di where di = Si - Ai. – For each slot Ai and each existing displacement dj where di≠dj, slot ((Ai + dj) mod n) is an R-slot or an E-slot. – For each slot S and any existing valid displacement di slot, slot ((S + di) mod n) is an R-slot or an E-slot. i A 0 A 1 E 0 S E 1 S R E 12 R E 23 E 4 R 0 ISMM, Toronto, Canada, 6/6/2010 16
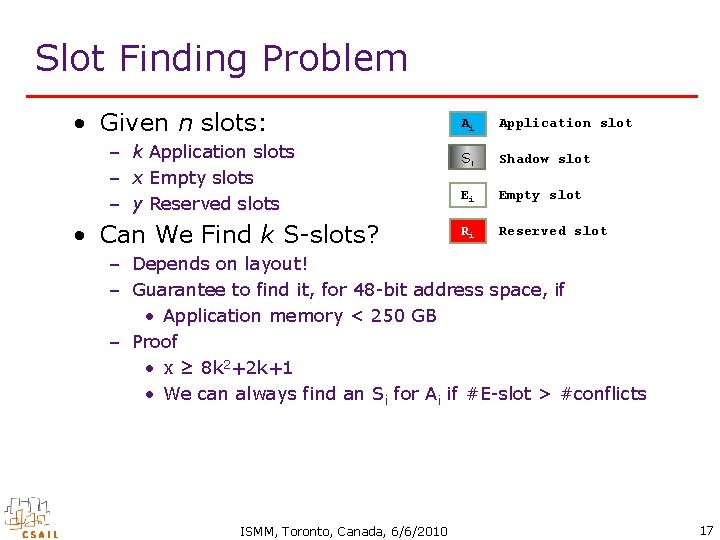
Slot Finding Problem • Given n slots: – k Application slots – x Empty slots – y Reserved slots • Can We Find k S-slots? Ai Application slot Si Shadow slot Ei Empty slot Ri Reserved slot – Depends on layout! – Guarantee to find it, for 48 -bit address space, if • Application memory < 250 GB – Proof • x ≥ 8 k 2+2 k+1 • We can always find an Si for Ai if #E-slot > #conflicts ISMM, Toronto, Canada, 6/6/2010 17
Implementation & Optimization • Implementation – Shadow memory allocation – Add signal handler – Remove reference uni-cache check lea [addr] %r 1 add %r 1, unicache disp %r 1 • Optimization – Restore uni-cache checks for instructions that access multiple segments, e. g. , references from memcpy • When number of access violation exceed 2 ISMM, Toronto, Canada, 6/6/2010 18
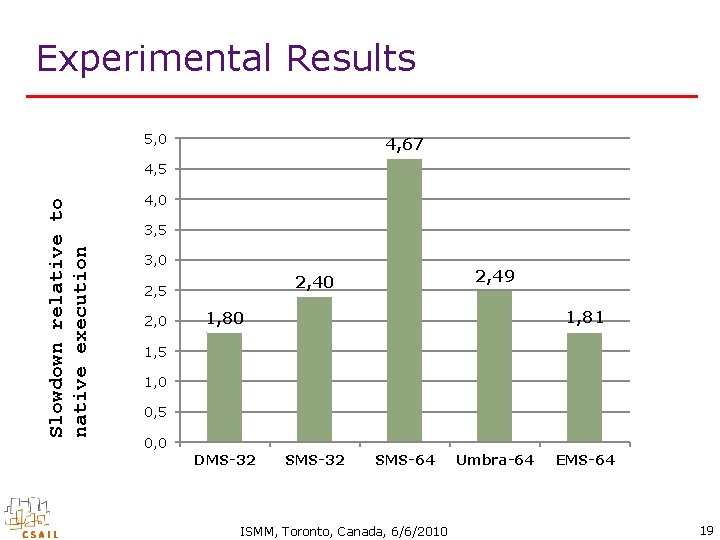
Experimental Results 5, 0 4, 67 Slowdown relative to native execution 4, 5 4, 0 3, 5 3, 0 2, 49 2, 40 2, 5 1, 81 1, 80 1, 5 1, 0 0, 5 0, 0 DMS-32 SMS-64 ISMM, Toronto, Canada, 6/6/2010 Umbra-64 EMS-64 19
Thank You • Download – http: //people. csail. mit. edu/qin_zhao/umbra/ • Q&A ISMM, Toronto, Canada, 6/6/2010 20
- Slides: 20