Efficient Asymmetric Secure i SCSI Murthy Andukuri 4292006


- Slides: 34

Efficient Asymmetric Secure i. SCSI Murthy Andukuri 4/29/2006 Murthy Si. SCSI 1

Outline of the talk l l l l Goals of the project Motivation for the project Current options for security Proposed scheme Three components : i. SCSI. IPsec, UML Design and Implementation Results Lessons learnt, Future work, Conclusions 4/29/2006 Murthy Si. SCSI 2

Goals l l A dual-key asymmetric cryptographic enhancement of IPsec to reduce total IPsec processing time and enhance data security for remote storage using i. SCSI. Demonstrate use of virtual test beds running UML to develop networking software. 4/29/2006 Murthy Si. SCSI 3

Motivation l Remote storage • NAS – Network Attached Storage • Roots in File server • NFS, CIFS • SAN – Storage Area Network • FCIP, i. FCP, i. SCSI (All SCSI Based) l i. SCSI is the Focus of the project - • Smart, inexpensive, No special hardware 4/29/2006 Murthy Si. SCSI 4

Storage Security Considerations l Importance of storage security • Need for end-to-end security. Possible • currently. Using Applications to secure data can leave gaps. l IPsec provides standardized security l Available options to achieve storage security as well • It addresses security in transmission 4/29/2006 Murthy Si. SCSI 5

Related Work l l l RFC 3723 - Securing Block Storage Protocols over IP Microsoft, Cisco, Intel – all have implementations of i. SCSI Initiator and Target. Available hardware implementations of i. SCSI + IPsec combined hardware – Astute Networks – SA 1000 Super. HBA for example. 4/29/2006 Murthy Si. SCSI 6

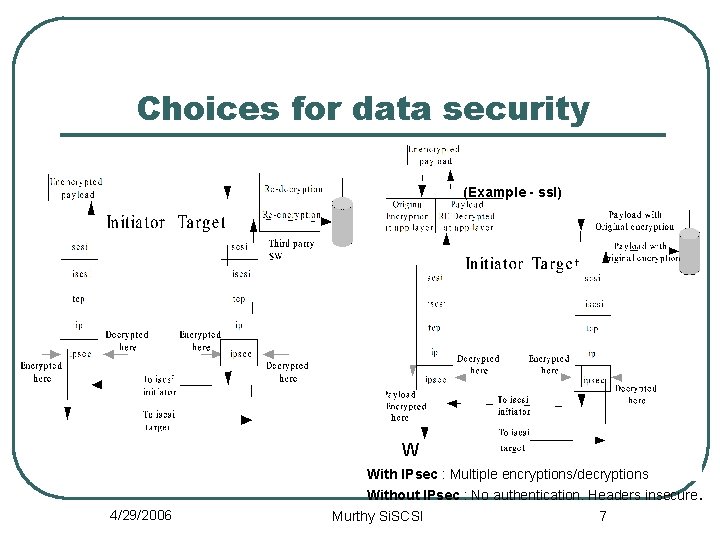
Choices for data security (Example - ssl) W With IPsec : Multiple encryptions/decryptions Without IPsec : No authentication. Headers insecure. 4/29/2006 Murthy Si. SCSI 7

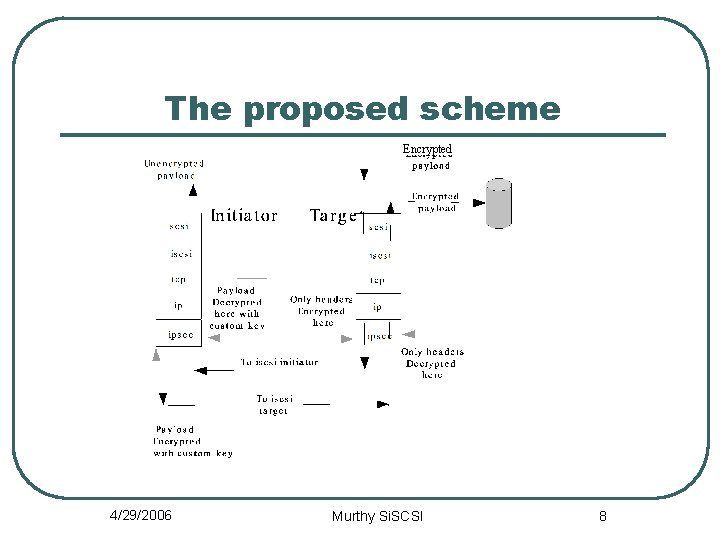
The proposed scheme Encrypted 4/29/2006 Murthy Si. SCSI 8

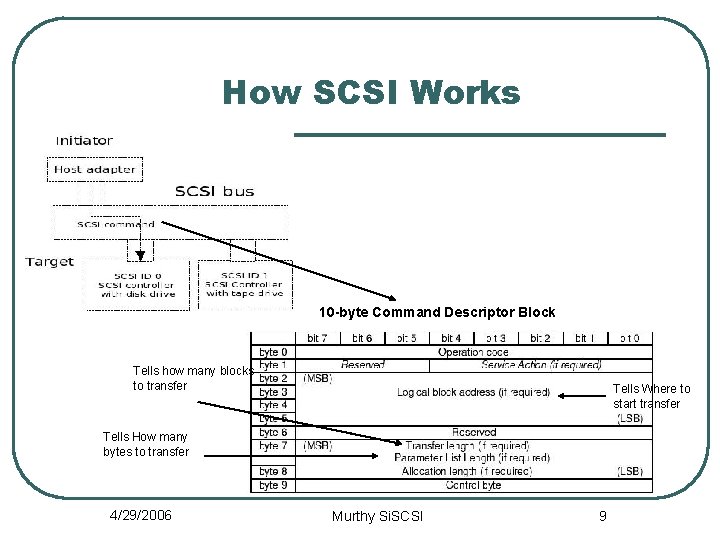
How SCSI Works 10 -byte Command Descriptor Block Tells how many blocks to transfer Tells Where to start transfer Tells How many bytes to transfer 4/29/2006 Murthy Si. SCSI 9

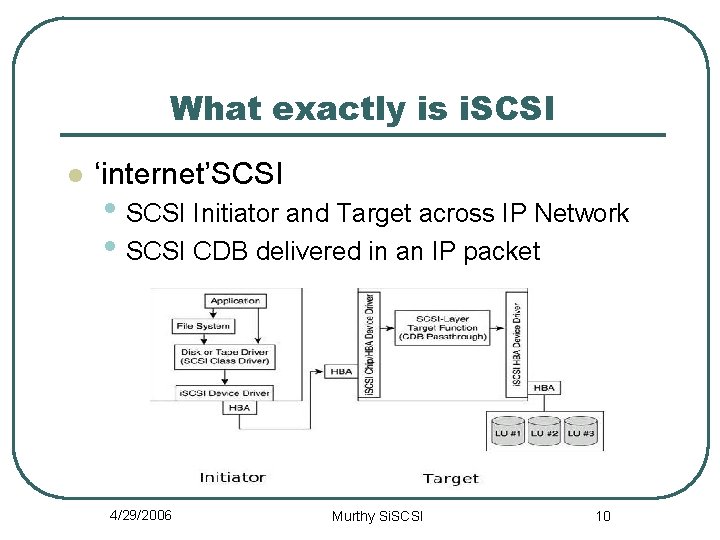
What exactly is i. SCSI l ‘internet’SCSI • SCSI Initiator and Target across IP Network • SCSI CDB delivered in an IP packet 4/29/2006 Murthy Si. SCSI 10

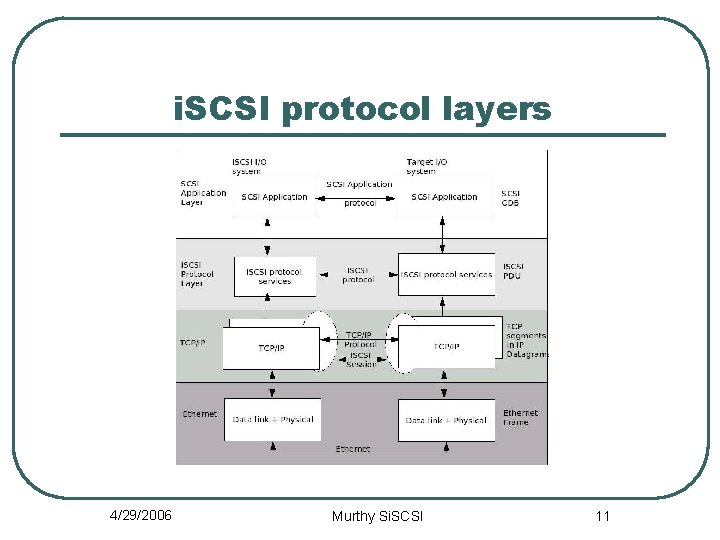
i. SCSI protocol layers 4/29/2006 Murthy Si. SCSI 11

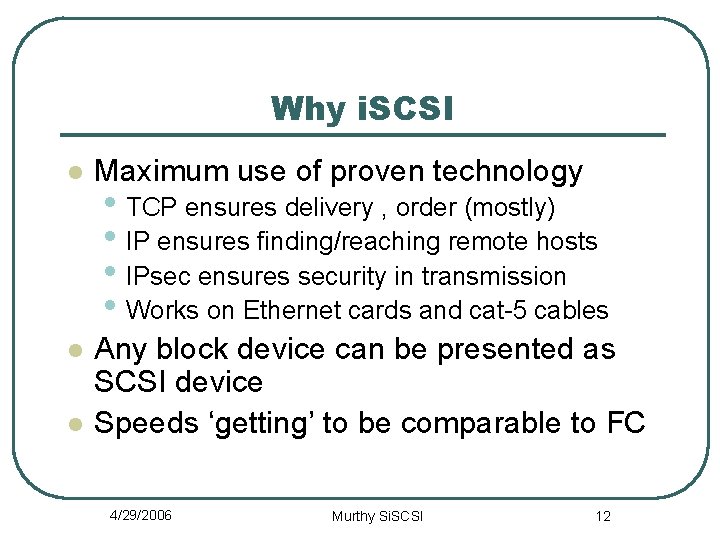
Why i. SCSI l Maximum use of proven technology l Any block device can be presented as SCSI device Speeds ‘getting’ to be comparable to FC l • TCP ensures delivery , order (mostly) • IP ensures finding/reaching remote hosts • IPsec ensures security in transmission • Works on Ethernet cards and cat-5 cables 4/29/2006 Murthy Si. SCSI 12

How i. SCSI works l l PDU (Protocol Data Unit) is the basic unit of communication i. SCSI payload is made of PDU header followed by Data. Several PDU types (called opcodes) based on the source. Fixed length PDU header 4/29/2006 Murthy Si. SCSI 13

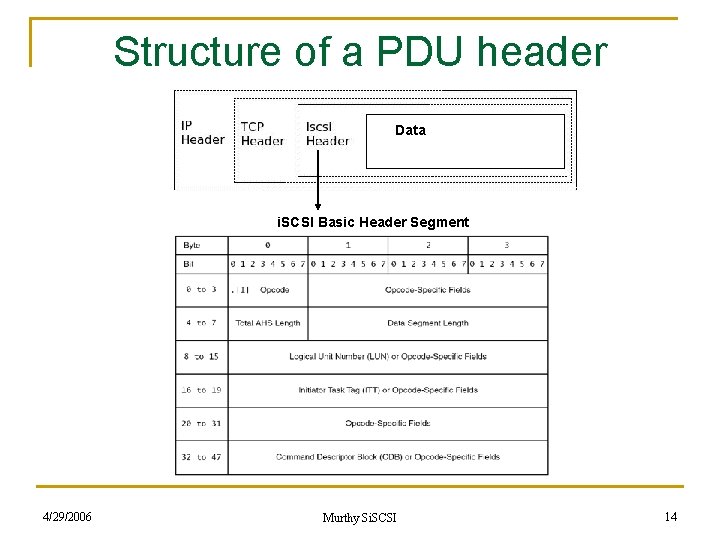
Structure of a PDU header Data i. SCSI Basic Header Segment 4/29/2006 Murthy Si. SCSI 14

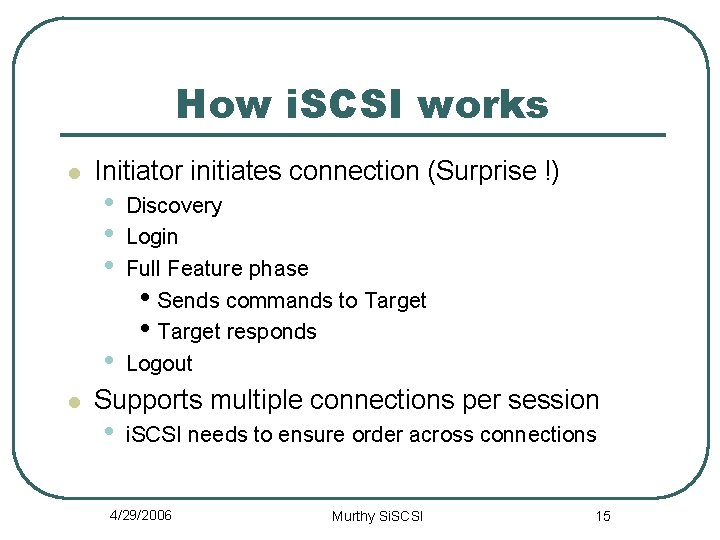
How i. SCSI works l Initiator initiates connection (Surprise !) • • l Discovery Login Full Feature phase • Sends commands to Target • Target responds Logout Supports multiple connections per session • i. SCSI needs to ensure order across connections 4/29/2006 Murthy Si. SCSI 15

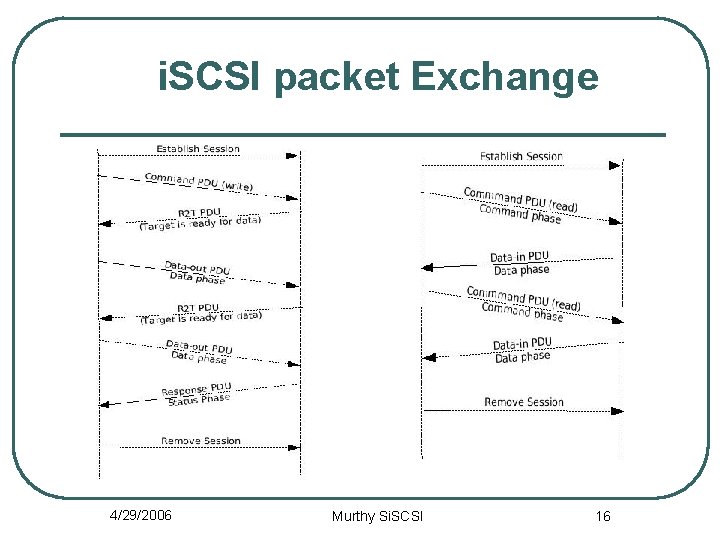
i. SCSI packet Exchange 4/29/2006 Murthy Si. SCSI 16

IPsec l l l Security integrated into network stack • • Secures ALL traffic between hosts Inherent in IPV 6, Supported for IPV 4 Consists of 3 protocols • • • IKE – For Dynamic Key management ESP – For Encryption and authentication AH – Authentication only Tunnel Mode or Transport mode • Transport mode chosen in the project 4/29/2006 Murthy Si. SCSI 17

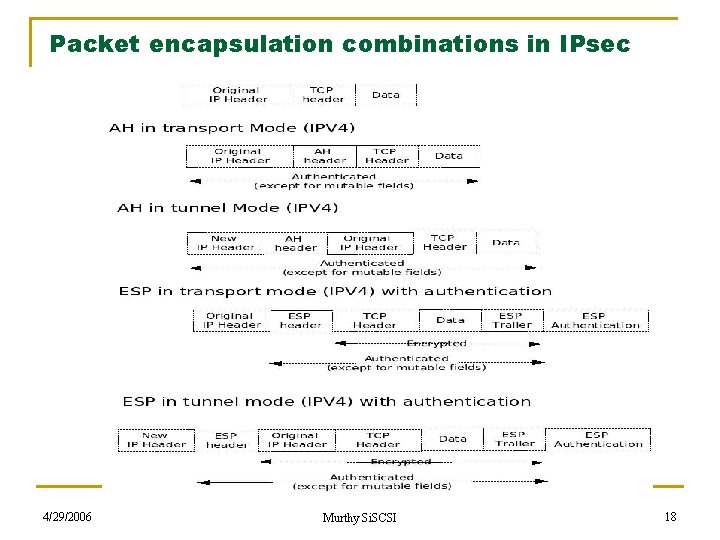
Packet encapsulation combinations in IPsec 4/29/2006 Murthy Si. SCSI 18

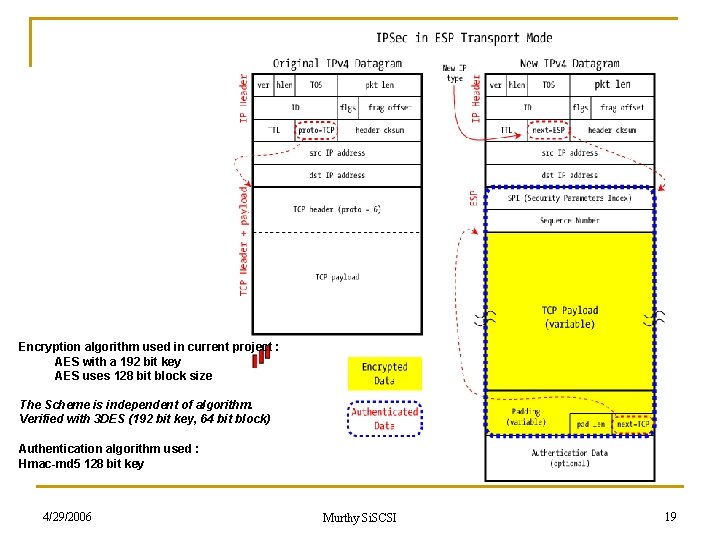
Encryption algorithm used in current project : AES with a 192 bit key AES uses 128 bit block size The Scheme is independent of algorithm. Verified with 3 DES (192 bit key, 64 bit block) Authentication algorithm used : Hmac-md 5 128 bit key 4/29/2006 Murthy Si. SCSI 19

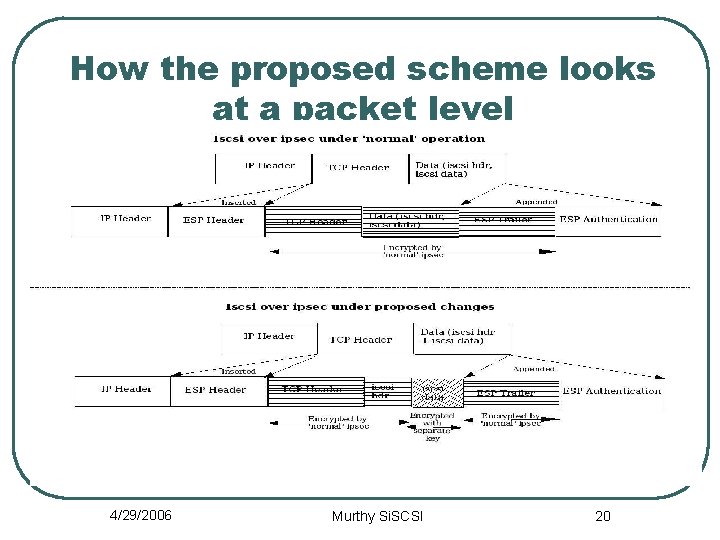
How the proposed scheme looks at a packet level 4/29/2006 Murthy Si. SCSI 20

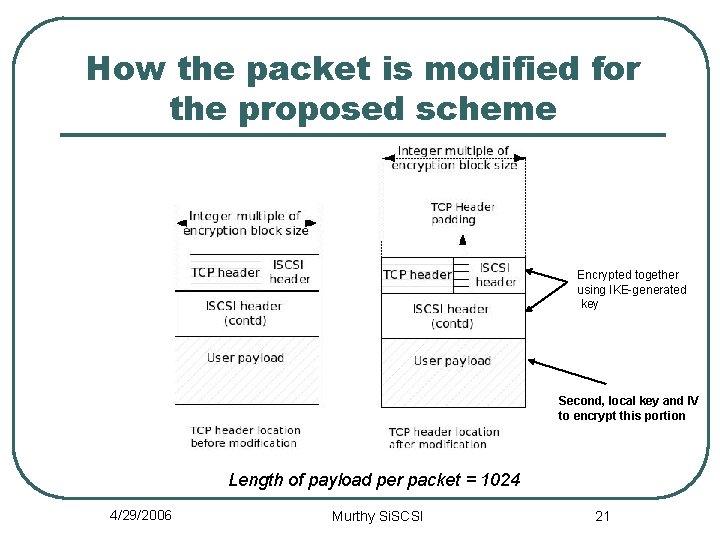
How the packet is modified for the proposed scheme Encrypted together using IKE-generated key Second, local key and IV to encrypt this portion Length of payload per packet = 1024 4/29/2006 Murthy Si. SCSI 21

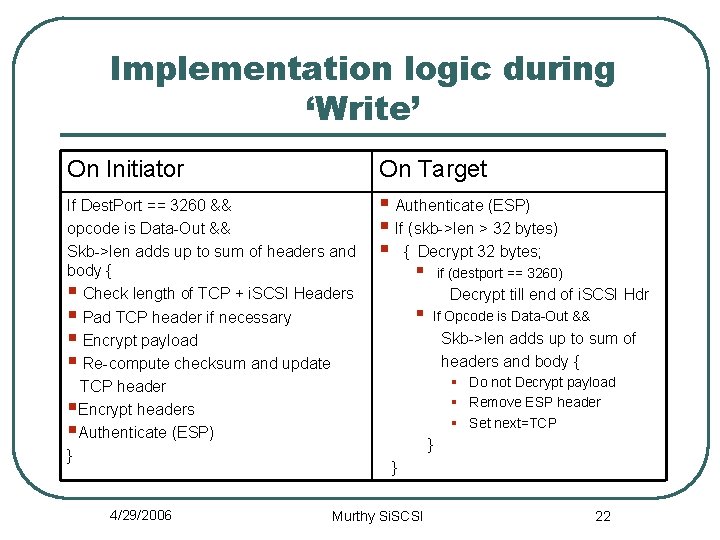
Implementation logic during ‘Write’ On Initiator If Dest. Port == 3260 && opcode is Data-Out && Skb->len adds up to sum of headers and body { § Check length of TCP + i. SCSI Headers § Pad TCP header if necessary § Encrypt payload § Re-compute checksum and update TCP header §Encrypt headers §Authenticate (ESP) } 4/29/2006 On Target § Authenticate (ESP) § If (skb->len > 32 bytes) § { Decrypt 32 bytes; § § if (destport == 3260) Decrypt till end of i. SCSI Hdr If Opcode is Data-Out && Skb->len adds up to sum of headers and body { § Do not Decrypt payload § Remove ESP header § Set next=TCP } } Murthy Si. SCSI 22

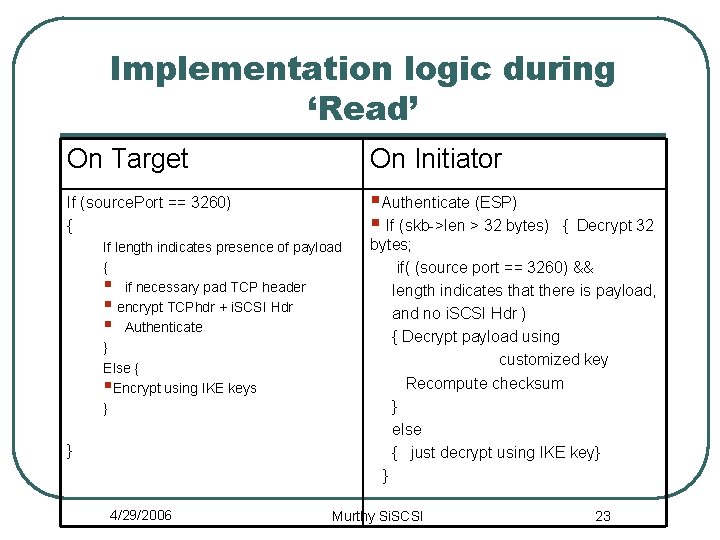
Implementation logic during ‘Read’ On Target On Initiator If (source. Port == 3260) { §Authenticate (ESP) § If (skb->len > 32 bytes) If length indicates presence of payload { § if necessary pad TCP header § encrypt TCPhdr + i. SCSI Hdr § Authenticate } Else { §Encrypt using IKE keys } } 4/29/2006 { Decrypt 32 bytes; if( (source port == 3260) && length indicates that there is payload, and no i. SCSI Hdr ) { Decrypt payload using customized key Recompute checksum } else { just decrypt using IKE key} } Murthy Si. SCSI 23

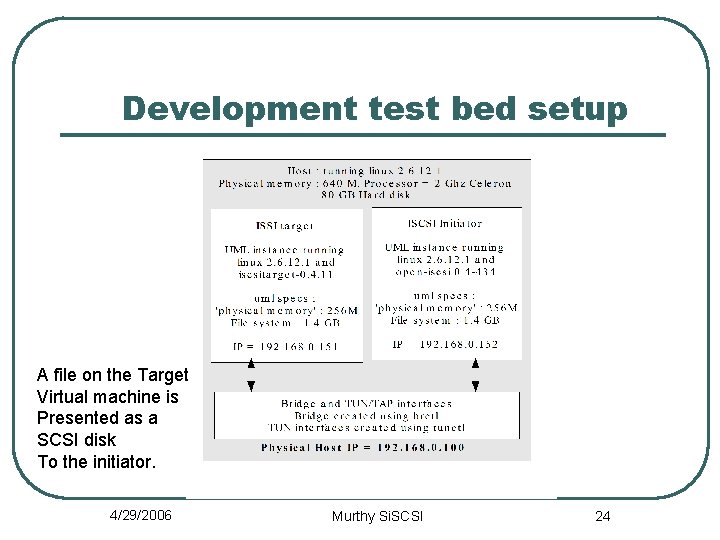
Development test bed setup A file on the Target Virtual machine is Presented as a SCSI disk To the initiator. 4/29/2006 Murthy Si. SCSI 24

Virtual machines of User Mode Linux l l l Multiple Virtual machines running on a single host. Can be built with any kernel source tree with ARCH=um make option. Can be started just like an application. Multiple instances can share a root file system using Copy -On-Write (COW) layer. Can optionally access the host file system as hostfs (Helps during development). Can be networked to the host, to each other and outside world. SKA helps make it almost impossible to hack into the host. Excellent as honeypot. Can be attached to gdb and stepped-thru like any application. 4/29/2006 Murthy Si. SCSI 25

Kernel Debugging in User Mode Linux l l Debug ‘static’ kernel code by attaching to gdb. Debugging modules is a (quite) a bit more tricky. • • Run the Perl Script in a separate terminal to create a pseudo terminal Run the ‘Expect’ script in a separate terminal, to setup gdb AND instantiate a ‘screen’ session kicking off UML attached to gdb. Find above session with ‘screen –ls’. Attach to it with ‘screen –r’. Add module’s details to gdb with add-symbol-file. 4/29/2006 Murthy Si. SCSI 26

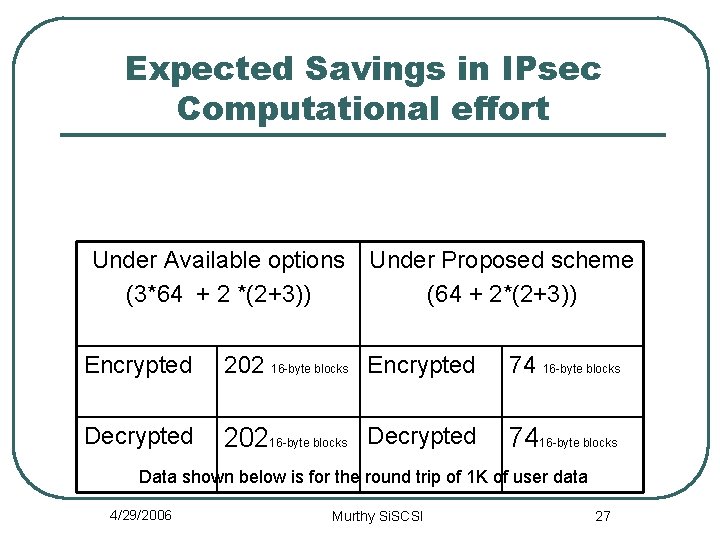
Expected Savings in IPsec Computational effort Under Available options (3*64 + 2 *(2+3)) Under Proposed scheme (64 + 2*(2+3)) Encrypted 202 16 -byte blocks Encrypted 74 16 -byte blocks Decrypted 20216 -byte blocks Decrypted 7416 -byte blocks Data shown below is for the round trip of 1 K of user data 4/29/2006 Murthy Si. SCSI 27

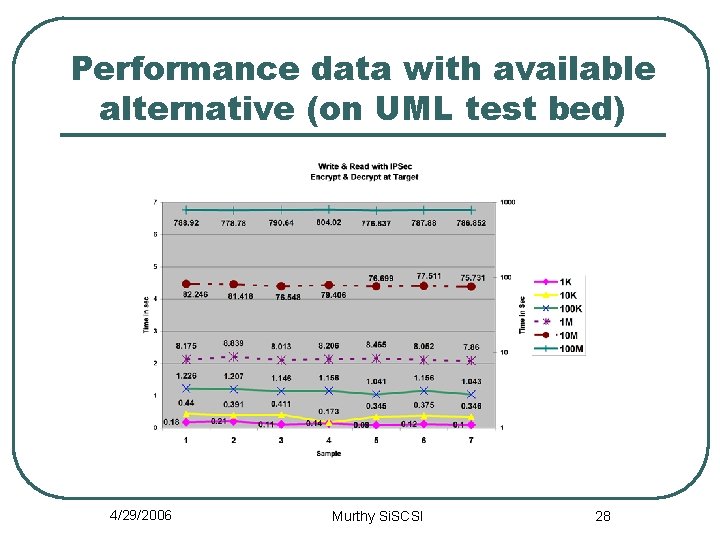
Performance data with available alternative (on UML test bed) 4/29/2006 Murthy Si. SCSI 28

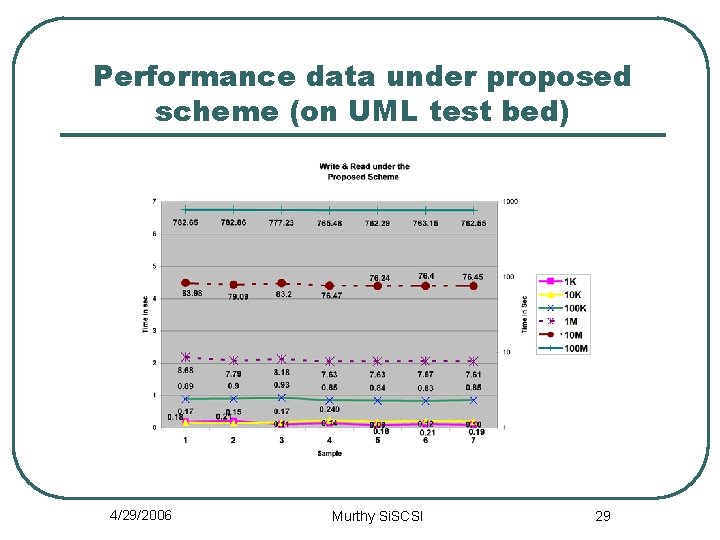
Performance data under proposed scheme (on UML test bed) 4/29/2006 Murthy Si. SCSI 29

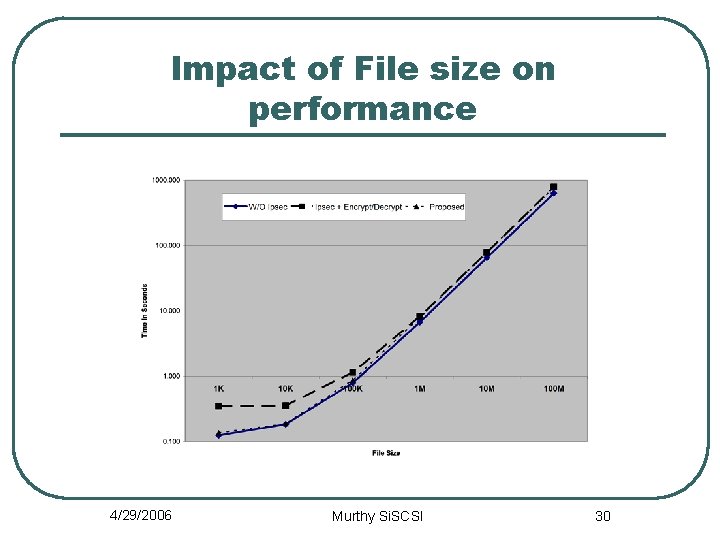
Impact of File size on performance 4/29/2006 Murthy Si. SCSI 30

Lessons Learnt l l l i. SCSI Initiator and Target (Apps and modules) need to built on host machine and installed into UML rootfs. Take care to point to right kernel tree. UML Kernel support for iscsi_transport needs to be configured as a module and not static. Debugging modules (Linux and i. SCSI) inside UML proved very tricky. TCP checksum needs to be recomputed in IPSec after segmented encryption on initiator. Also after decryption of data that has been read back. The payload length is held very dearly by i. SCSI layer (Both initiator and target). Trying to tweak the length in IP layer doesn’t work ! 4/29/2006 Murthy Si. SCSI 31

Future Efforts • l l l Expand to include arbitrary file sizes Include in an IPsec + i. SCSI TOE User interface, /Proc system based enhancements to improve flexibility, security Ability to mark packets using netfilter hacks. Expand IPsec key generation mechanism to include i. SCSI With some modifications, the same scheme can be used to encrypt with application layer SW and NOT Re-encrypt/decrypt at IPsec. 4/29/2006 Murthy Si. SCSI 32

Conclusions l l An asymmetric IPsec protocol enhancement was developed for improving the security and performance of remote online backup systems. Demonstrated how UML can be used to facilitate kernel/networking software. development. An invention disclosure was filed with University of Colorado Tech Transfer Office. A paper to be submitted to ICNP conference. 4/29/2006 Murthy Si. SCSI 33

Benefits of the scheme l Addresses gaps in storage security, expected to improve performance and eliminate need for multiple tools to provide security. l Cuts hardware costs. CPU/TOE on the Target need not be as fast as those on Initiator. Or can be used to process more requests. l Flexibility – The scheme can be used with any Encryption and Authentication scheme supported by IPsec. l The scheme does not weaken other security measures. l The idea of the scheme probably can be applied to SSL tunneling. 4/29/2006 Murthy Si. SCSI 34