Effectiveness of Distance Decreasing Attacks Against Impulse Radio






![Synchronization Error Ratio Preamble: Early detection 4 d. B ARX SNR [d. B] 26 Synchronization Error Ratio Preamble: Early detection 4 d. B ARX SNR [d. B] 26](https://slidetodoc.com/presentation_image/42a3a7cad7c2b1ccccf2c7d6d5ce905e/image-26.jpg)
![Synchronization Error Ratio Preamble: Late commit 4 d. B HRX SNR [d. B] 27 Synchronization Error Ratio Preamble: Late commit 4 d. B HRX SNR [d. B] 27](https://slidetodoc.com/presentation_image/42a3a7cad7c2b1ccccf2c7d6d5ce905e/image-27.jpg)
![Packet Error Ratio Payload: Early detection 1. 7 d. B ARX SNR [d. B] Packet Error Ratio Payload: Early detection 1. 7 d. B ARX SNR [d. B]](https://slidetodoc.com/presentation_image/42a3a7cad7c2b1ccccf2c7d6d5ce905e/image-28.jpg)
![Packet Error Ratio Payload: Late commit 4 d. B HRX SNR [d. B] 29 Packet Error Ratio Payload: Late commit 4 d. B HRX SNR [d. B] 29](https://slidetodoc.com/presentation_image/42a3a7cad7c2b1ccccf2c7d6d5ce905e/image-29.jpg)




- Slides: 38

Effectiveness of Distance Decreasing Attacks Against Impulse Radio Ranging Manuel Flury, Marcin Poturalski, Panos Papadimitratos, Jean-Pierre Hubaux, Jean-Yves Le Boudec Laboratory for Computer Communications and Applications, EPFL, Switzerland Third ACM Conference on Wireless Network Security (Wi. Sec `10) March 23, 2010

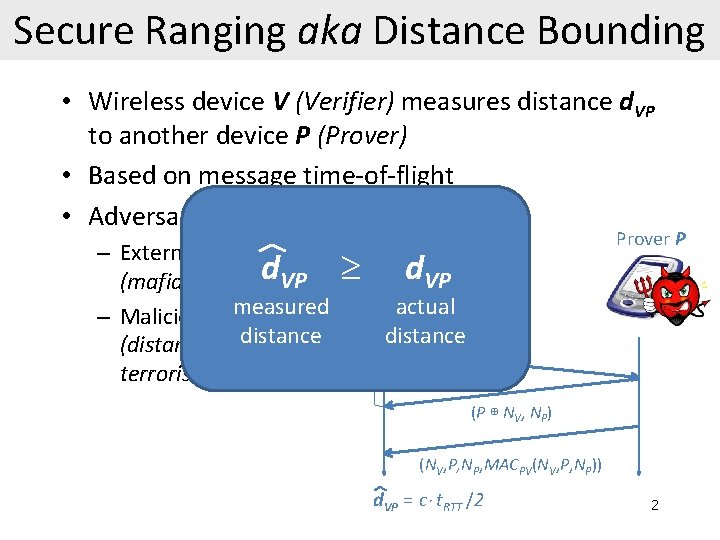
Secure Ranging aka Distance Bounding • Wireless device V (Verifier) measures distance d. VP to another device P (Prover) • Based on message time-of-flight • Adversarial setting: Verifier V Prover P – External attacks d. VP (mafia fraud) d. VP measured actual – Malicious prover distance (distance anddistance terrorist frauds) t. RTT NV (P ⊕ NV, NP) (NV, P, NP, MACPV(NV, P, NP)) d. VP = c t. RTT /2 2

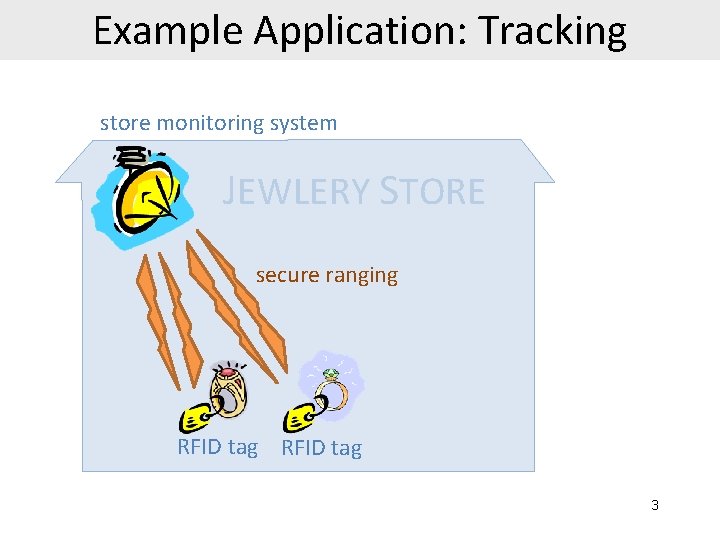
Example Application: Tracking store monitoring system JEWLERY STORE secure ranging RFID tag 3

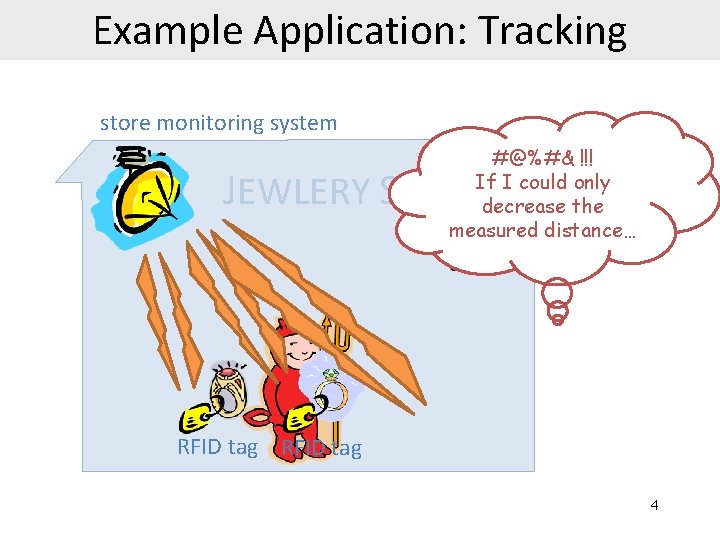
Example Application: Tracking store monitoring system #@%#& !!! If I could only decrease the measured distance… JEWLERY STORE RFID tag 4

Other Application Examples • Tracking: – assets in warehouse – inmates – hospital assets, personnel, patients – animals – military personnel and equipment –… • • RFID access control RFID micropayments Secure localization … 5

Physical Layer Attacks • Decrease the measured distance by exploiting physical layer redundancy J. Clulow, G. P. Hancke, M. G. Kuhn, and T. Moore. So near and yet so far: Distance-bounding attacks in wireless networks. ESAS 2006 • Physical layer and receiver specific – RFID (ISO 14443 A) and WSN PHYs G. P. Hancke, M. G. Kuhn. Attacks on time-of-flight distance bounding channels. Wi. Sec 2008 • Other physical layers? 6

Impulse Radio UWB • IR-UWB ranging capabilities: – high precision (sub meter) – copes well with multipath propagation transmitted signal received signal sampled signal (energy detector receiver) • IEEE 802. 15. 4 a standard 7

Our contribution • Distance-decreasing relay attack against: – IEEE 802. 15. 4 a standard – Energy detector receiver • Distance decrease of up to 140 m* • Attack success rate can be made arbitrarily high • Components (early detection and late commit) can be used individually by a malicious prover 8 * IEEE 802. 15. 4 a mandatory modes

Protocol Assumptions • Rapid bit exchange: – Transmission of single bits – Instantaneous reply Verifier V Prover P c 1 We assume – Challenging to c 2 implement no rapid bit exchange – Not compatible with IEEE cn 802. 15. 4 a . . . r 1 . . . r 2 rn 9

Protocol Assumptions • Several-bit-long ranging messages • Sufficient if V and P are honest • With full duplex transmission can cope with malicious prover* • Compatible with IEEE 802. 15. 4 a Verifier V Prover P NV t. RTT * Kasper Bonne Rasmussen, Srdjan Capkun. Location Privacy of Distance Bounding Protocols. CCS 2008 NP (NV, P, NP, MACPV(NV, P, NP)) 10

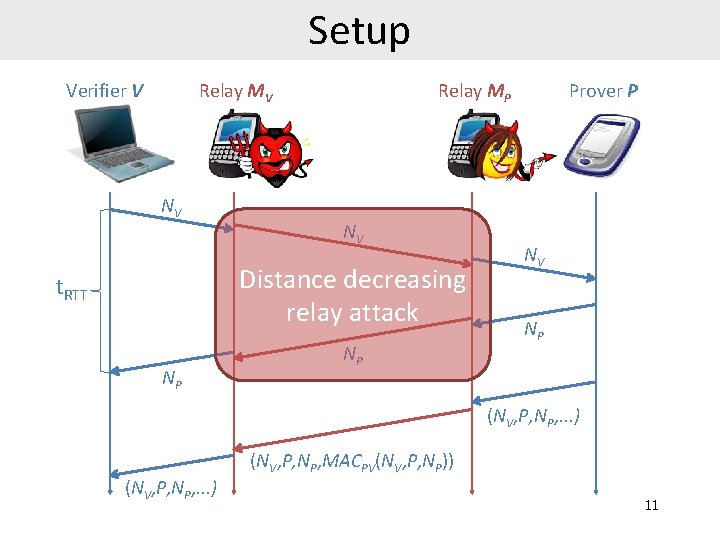
Setup Relay MV Verifier V NV Relay MP NV Distance decreasing relay attack t. RTT NP NP Prover P NV NP (NV, P, NP, . . . ) (NV, P, NP, MACPV(NV, P, NP)) 11

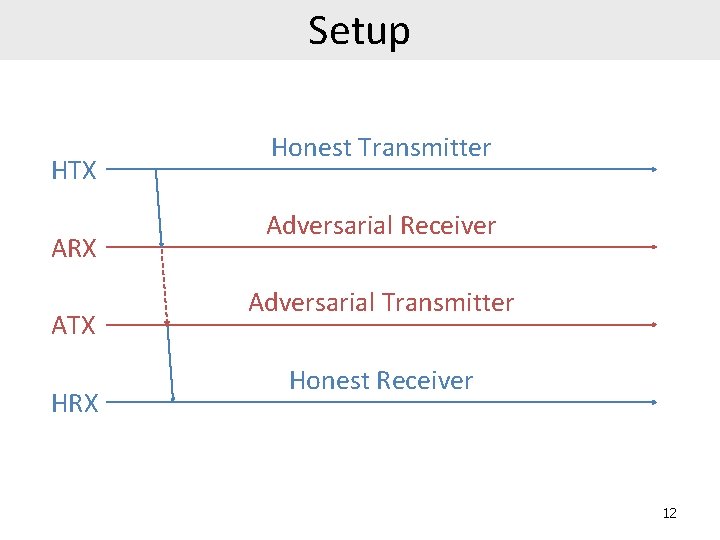
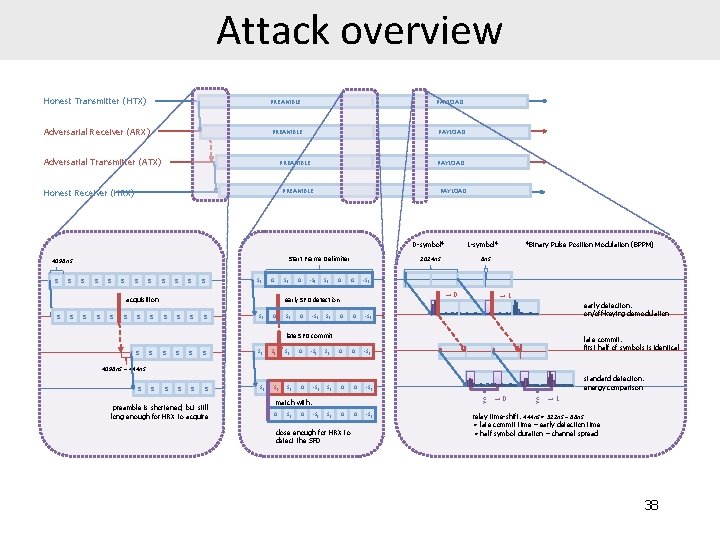
Setup HTX ARX ATX HRX Honest Transmitter Adversarial Receiver Adversarial Transmitter Honest Receiver 12

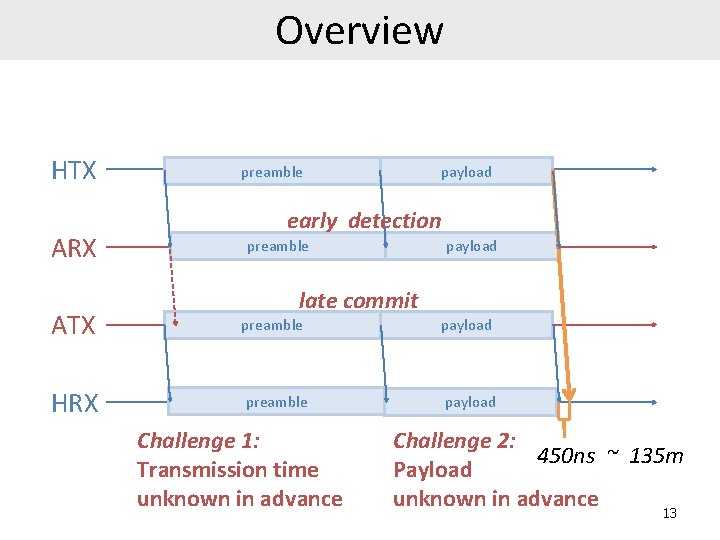
Overview HTX ARX preamble payload early detection preamble payload late commit ATX preamble payload HRX preamble payload Challenge 1: Transmission time unknown in advance Challenge 2: 450 ns ~ 135 m Payload unknown in advance 13

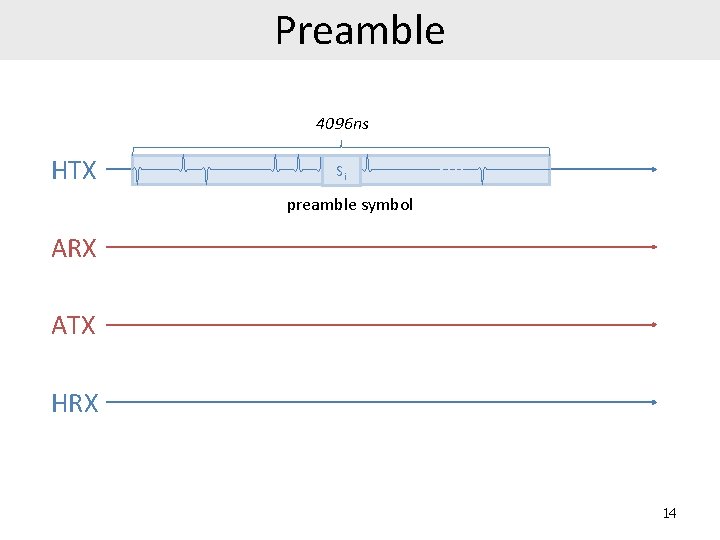
Preamble 4096 ns HTX Si preamble symbol ARX ATX HRX 14

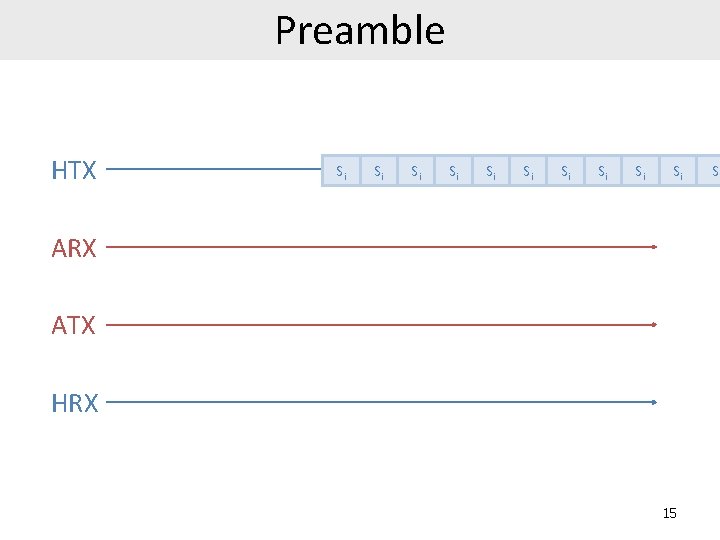
Preamble HTX Si Si Si ARX ATX HRX 15 Si

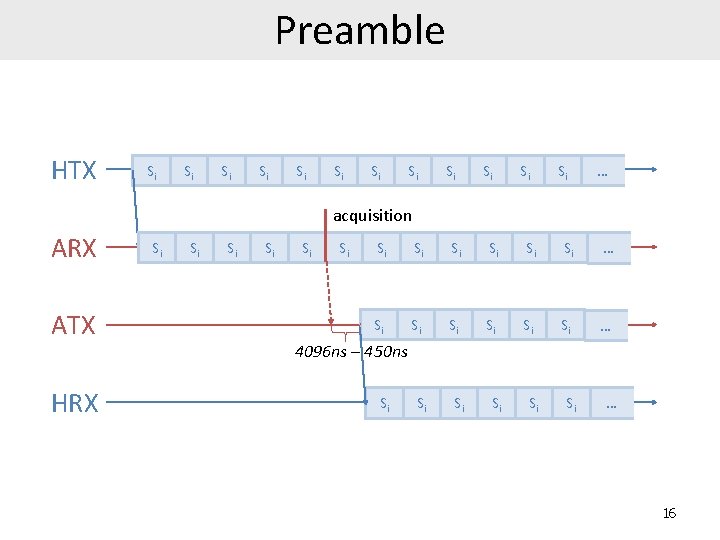
Preamble HTX Si Si Si … acquisition ARX ATX HRX Si Si Si … Si Si Si … 4096 ns – 450 ns Si Si Si … 16

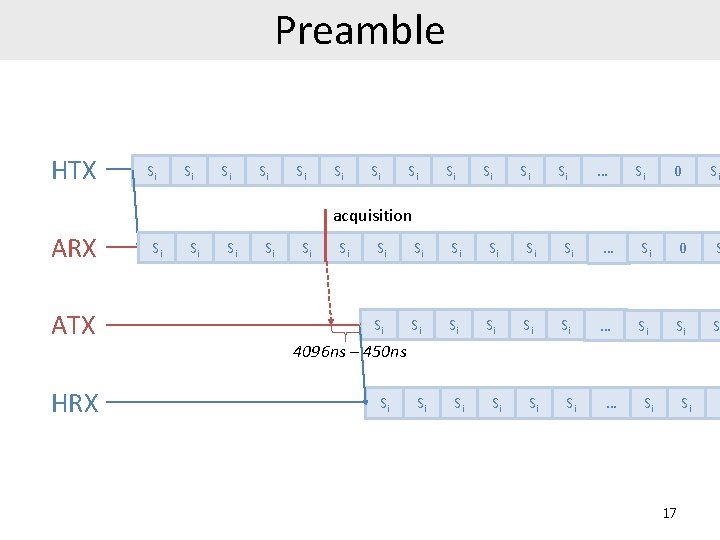
Preamble HTX Si Si Si … Si 0 Si acquisition ARX ATX HRX Si Si Si … Si 0 S Si Si Si … Si Si S 4096 ns – 450 ns Si Si Si … Si Si 17 S

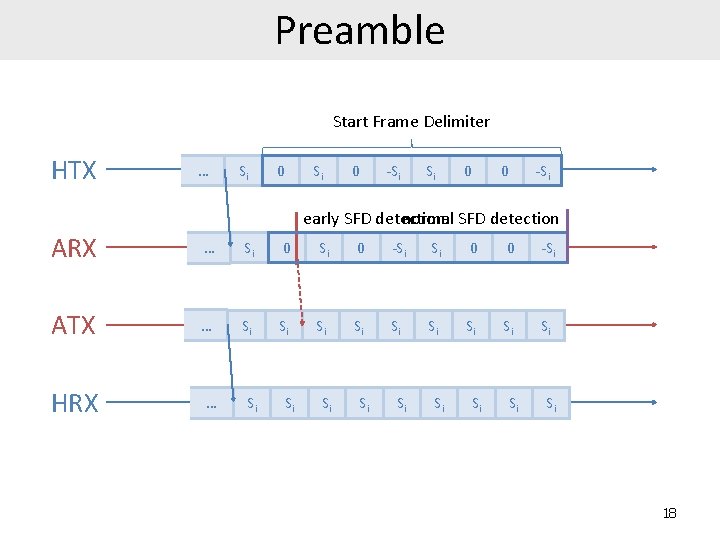
Preamble Start Frame Delimiter HTX … Si 0 -Si Si 0 0 -Si early SFD detection normal SFD detection ARX … Si 0 -Si Si 0 0 -Si ATX … Si Si Si HRX … Si Si Si 18

Preamble Start Frame Delimiter HTX … Si 0 -Si Si 0 0 -Si early SFD detection ARX … Si 0 -Si Si 0 0 -Si late SFD commit ATX HRX … … Si Si Si 0 0 -Si time-shift 450 ns 19

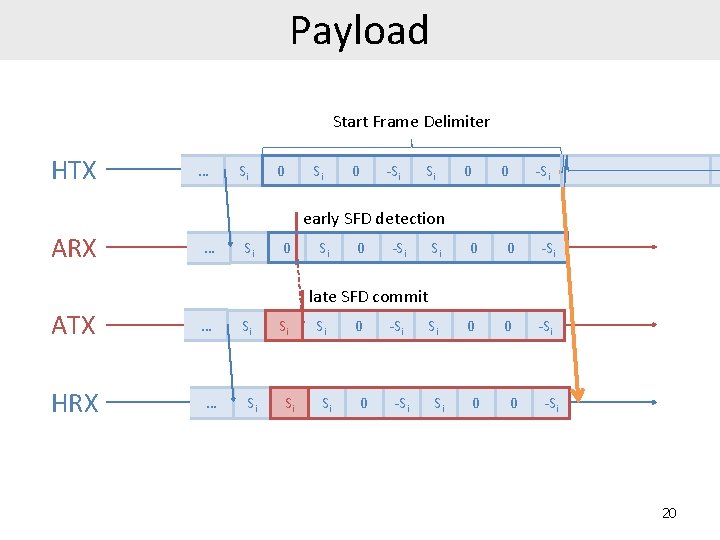
Payload Start Frame Delimiter HTX … Si 0 -Si Si 0 0 -Si early SFD detection ARX … Si 0 -Si Si 0 0 -Si late SFD commit ATX HRX … … Si Si Si 0 0 -Si 20

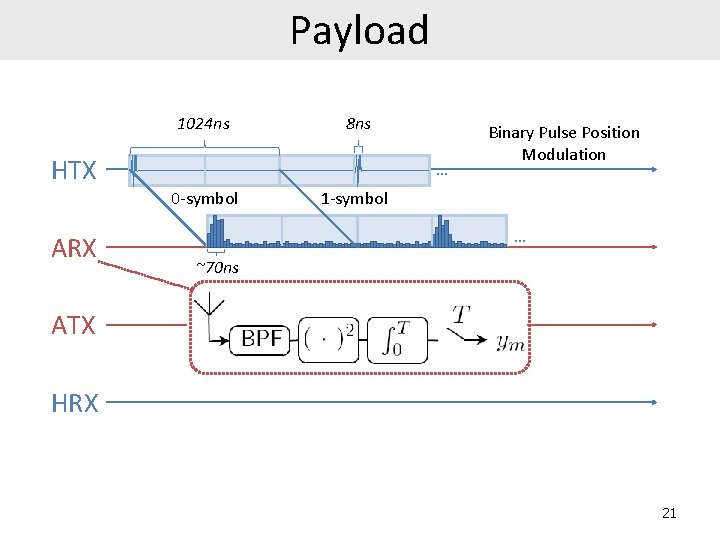
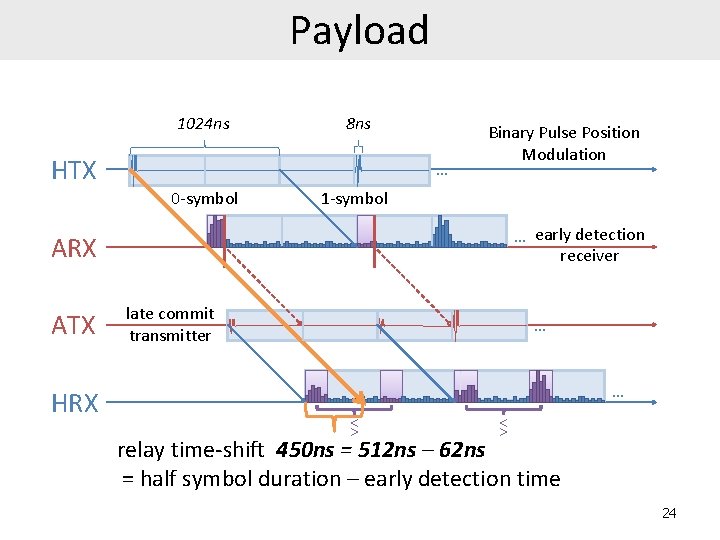
Payload 1024 ns 8 ns HTX … 0 -symbol ARX Binary Pulse Position Modulation 1 -symbol … ~70 ns ATX HRX 21

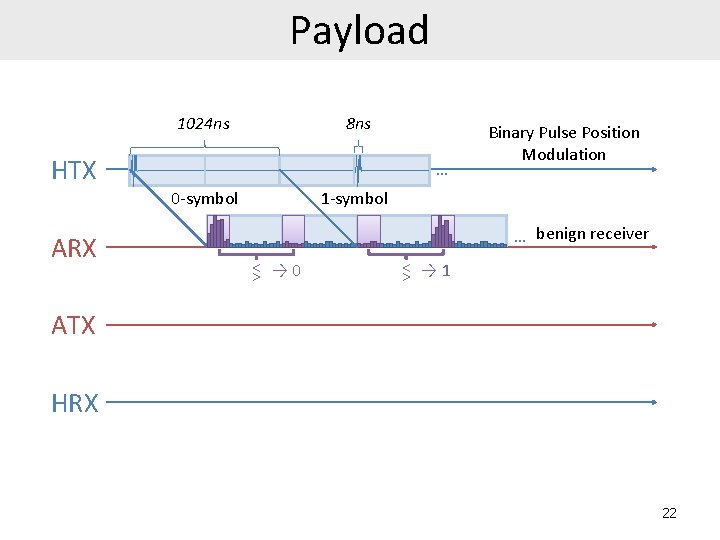
Payload 1024 ns 8 ns HTX … 0 -symbol ARX Binary Pulse Position Modulation 1 -symbol … benign receiver >< → 0 >< → 1 ATX HRX 22

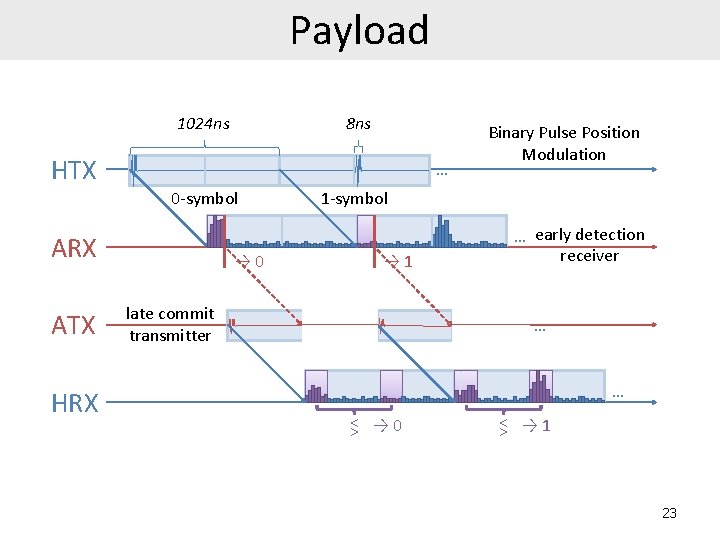
Payload 1024 ns 8 ns HTX … 0 -symbol ARX ATX HRX → 0 Binary Pulse Position Modulation 1 -symbol → 1 late commit transmitter … early detection receiver … … >< → 0 >< → 1 23

Payload 1024 ns 8 ns HTX … 0 -symbol Binary Pulse Position Modulation 1 -symbol … early detection receiver ARX ATX HRX late commit transmitter … … >< >< relay time-shift 450 ns = 512 ns – 62 ns = half symbol duration – early detection time 24

Attack Performance • Evaluation with physical layer simulations • IEEE 802. 15. 4 a, with: – 128 bit packets – residential NLOS channel model • based on IR channel measurement campaigns – LPRF mode (mandatory parameters) 25
![Synchronization Error Ratio Preamble Early detection 4 d B ARX SNR d B 26 Synchronization Error Ratio Preamble: Early detection 4 d. B ARX SNR [d. B] 26](https://slidetodoc.com/presentation_image/42a3a7cad7c2b1ccccf2c7d6d5ce905e/image-26.jpg)
Synchronization Error Ratio Preamble: Early detection 4 d. B ARX SNR [d. B] 26
![Synchronization Error Ratio Preamble Late commit 4 d B HRX SNR d B 27 Synchronization Error Ratio Preamble: Late commit 4 d. B HRX SNR [d. B] 27](https://slidetodoc.com/presentation_image/42a3a7cad7c2b1ccccf2c7d6d5ce905e/image-27.jpg)
Synchronization Error Ratio Preamble: Late commit 4 d. B HRX SNR [d. B] 27
![Packet Error Ratio Payload Early detection 1 7 d B ARX SNR d B Packet Error Ratio Payload: Early detection 1. 7 d. B ARX SNR [d. B]](https://slidetodoc.com/presentation_image/42a3a7cad7c2b1ccccf2c7d6d5ce905e/image-28.jpg)
Packet Error Ratio Payload: Early detection 1. 7 d. B ARX SNR [d. B] 28
![Packet Error Ratio Payload Late commit 4 d B HRX SNR d B 29 Packet Error Ratio Payload: Late commit 4 d. B HRX SNR [d. B] 29](https://slidetodoc.com/presentation_image/42a3a7cad7c2b1ccccf2c7d6d5ce905e/image-29.jpg)
Packet Error Ratio Payload: Late commit 4 d. B HRX SNR [d. B] 29

Probability of attack success Overall attack success >99% attack success probability with SNR 4 d. B (ARX) and 6 d. B (HRX) greater than for benign operation Easily achievable: • High gain antenna • Increase transmision power Early detection SNR adversarial. Late commit SNR • Move devices closer (ARX) to victim devices (HRX) 30

Application example: Tracking ? ? ? jail relay 31

Countermeasures • Decrease payload symbol length – Our attack gains half of symbol duration – Non-mandatory IEEE 802. 15. 4 a modes with payload symbol length 32 ns (11 m) • Disadvantages: – Shorter symbols result in worse multi-user interference tolerance – With very short symbols, inter-symbol interference becomes an issue J. Clulow, G. P. Hancke, M. G. Kuhn, and T. Moore. So near and yet so far: Distance-bounding attacks in wireless networks. ESAS 2006 32

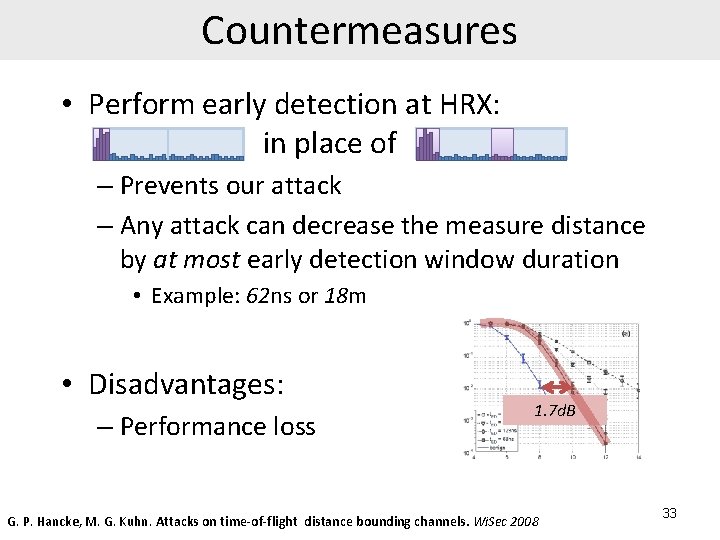
Countermeasures • Perform early detection at HRX: in place of – Prevents our attack – Any attack can decrease the measure distance by at most early detection window duration • Example: 62 ns or 18 m • Disadvantages: – Performance loss 1. 7 d. B G. P. Hancke, M. G. Kuhn. Attacks on time-of-flight distance bounding channels. Wi. Sec 2008 33

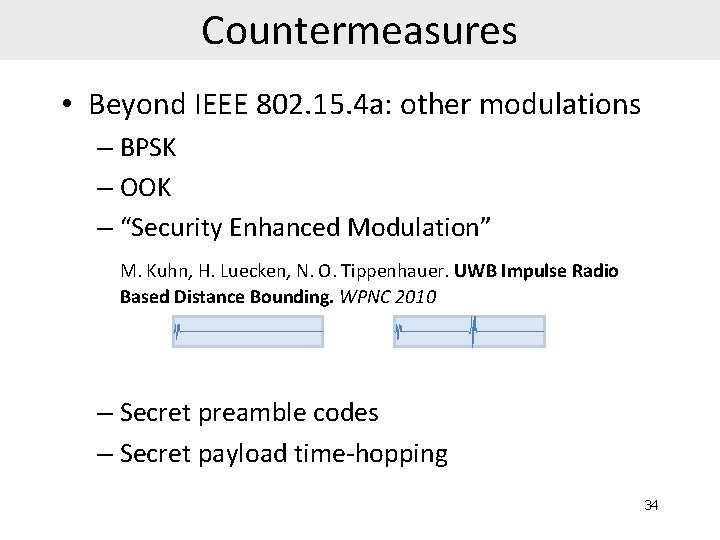
Countermeasures • Beyond IEEE 802. 15. 4 a: other modulations – BPSK – OOK – “Security Enhanced Modulation” M. Kuhn, H. Luecken, N. O. Tippenhauer. UWB Impulse Radio Based Distance Bounding. WPNC 2010 – Secret preamble codes – Secret payload time-hopping 34

Conclusion • IR-UWB standard IEEE 802. 15. 4 a is vulnerable to a distance-decreasing relay attack – 140 m distance decrease against energy-detection receivers* – Attack enabled by BPPM (de)modulation • Attack performance – 99% success rate at minor SNR cost (few d. B) – Success rate can be made arbitrarily high 35 * IEEE 802. 15. 4 a mandatory modes

Ongoing work • Countermeasures • Attack with a coherent receiver – Exploits the specifics of the convolutional code used in IEEE 802. 15. 4 a – Additional 75 m distance-decrease • New physical layer attack against ranging – Malicious interference disrupting To. A estimation – Less effective and precise, but easy to mount M. Poturalski, M. Flury, P. Papadimitratos, J-P. Hubaux, J-Y. Le Boudec. The Cicada Attack: Degradation and Denial of Service in IR Ranging. (under submission) 36

To learn more… http: //lca. epfl. ch/projects/snd marcin. poturalski@epfl. ch 37

Attack overview Honest Transmitter (HTX) PREAMBLE PAYLOAD Adversarial Receiver (ARX) PREAMBLE PAYLOAD Adversarial Transmitter (ATX) PREAMBLE PAYLOAD PREAMBLE Honest Receiver (HRX) PAYLOAD 0 -symbol* Start Frame Delimiter 4096 ns Si Si Si Si 0 Si acquisition Si Si 0 -Si Si 0 -Si → 0 early SFD detection Si Si Si 0 -Si Si *Binary Pulse Position Modulation (BPPM) 8 ns 1024 ns 0 1 -symbol* 0 0 -Si → 1 early detection: on/off-keying demodulation late SFD commit Si Si Si 0 -Si Si late commit: first half of symbols is identical 4096 ns – 444 ns Si Si Si preamble is shortened, but still long enough for HRX to acquire Si Si Si 0 -Si Si 0 0 < → 0 > match with: 0 Si 0 standard detection: energy comparison -Si Si 0 close enough for HRX to detect the SFD 0 -Si < → 1 > relay time-shift: 444 ns = 512 ns – 68 ns = late commit time – early detection time = half symbol duration – channel spread 38
 Conventional radio system
Conventional radio system The ratio of input distance to output distance
The ratio of input distance to output distance Difference between distance and displacement
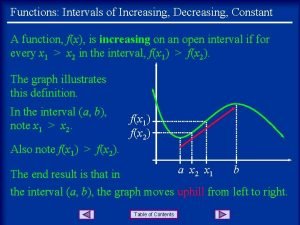
Difference between distance and displacement What is interval of increase
What is interval of increase Increasing and decreasing piecewise functions
Increasing and decreasing piecewise functions Graphing transformations
Graphing transformations Lesson 4 increasing and decreasing functions
Lesson 4 increasing and decreasing functions Decreasing response time almost always
Decreasing response time almost always Periodic relationships
Periodic relationships Comparative modifiers examples
Comparative modifiers examples Drag truss
Drag truss Removable and nonremovable discontinuity
Removable and nonremovable discontinuity Ordinary language means
Ordinary language means Decreasing metallic character
Decreasing metallic character Strictly increasing and decreasing functions
Strictly increasing and decreasing functions How to find the percent decrease
How to find the percent decrease Identify the end behavior
Identify the end behavior Money supply and interest rate
Money supply and interest rate Order of increasing first ionization energy
Order of increasing first ionization energy First fit decreasing algorithm
First fit decreasing algorithm Increasing at a decreasing rate
Increasing at a decreasing rate Increasing and decreasing intervals
Increasing and decreasing intervals Lesson 5 increasing and decreasing functions
Lesson 5 increasing and decreasing functions Classify each decreasing function as having a slope
Classify each decreasing function as having a slope First fit decreasing bin packing
First fit decreasing bin packing How to find increasing and decreasing intervals on a graph
How to find increasing and decreasing intervals on a graph Increasing and decreasing recipes
Increasing and decreasing recipes Decreasing turnover time operating room
Decreasing turnover time operating room A single countermeasure is sufficient for sqli attacks
A single countermeasure is sufficient for sqli attacks Neur ips
Neur ips Attacks on bilingualism represent an ethnocentric
Attacks on bilingualism represent an ethnocentric Deauth attack
Deauth attack Chapter 4 vulnerability assessment and mitigating attacks
Chapter 4 vulnerability assessment and mitigating attacks Security attacks services and mechanisms
Security attacks services and mechanisms Layer 2 security
Layer 2 security Icd x anxiety disorders
Icd x anxiety disorders Hijacking attacks
Hijacking attacks Mika juuti
Mika juuti The most complex part of tls is the __________.
The most complex part of tls is the __________.