EEL 5718 Computer Communications Transport Layer Protocols Transport







- Slides: 29

EEL 5718 Computer Communications Transport Layer Protocols

Transport Protocol • Task: Reliable message delivery from end node to another end node via a subnet • Transport service is end to end protocol between two systems on the same network

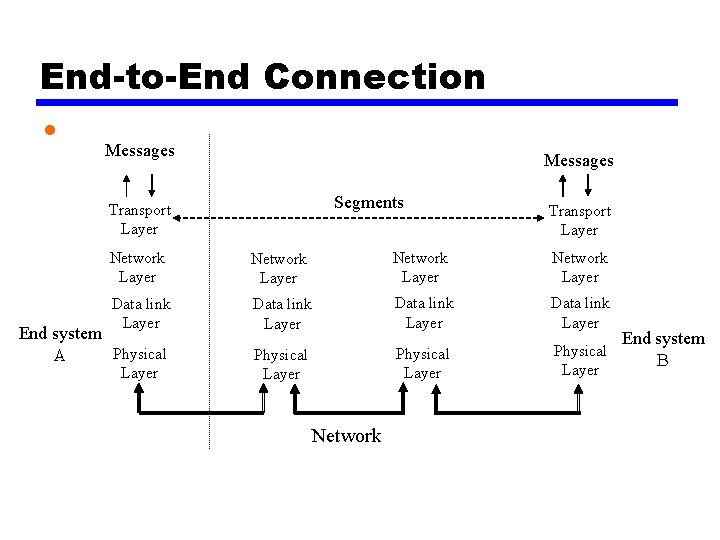
End-to-End Connection • Messages Segments Transport Layer Network Layer Data link Layer Physical Layer End system Physical A Network End system B

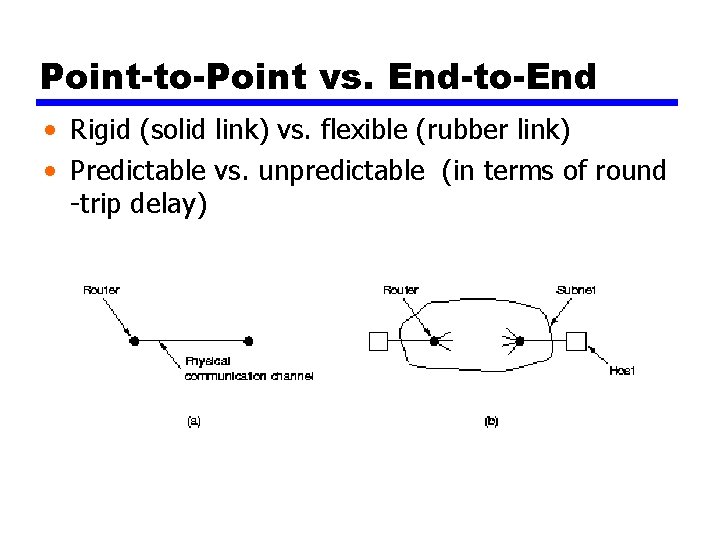
Point-to-Point vs. End-to-End • Rigid (solid link) vs. flexible (rubber link) • Predictable vs. unpredictable (in terms of round -trip delay)

End-to-end Quality of Service (Qo. S) • A set of qualitative and quantitative measures that define an acceptable level of performance – – – – – Reliability: error rate Setup time Delay and delay variations (jitters) Throughput Priority Protection Resilience Security More

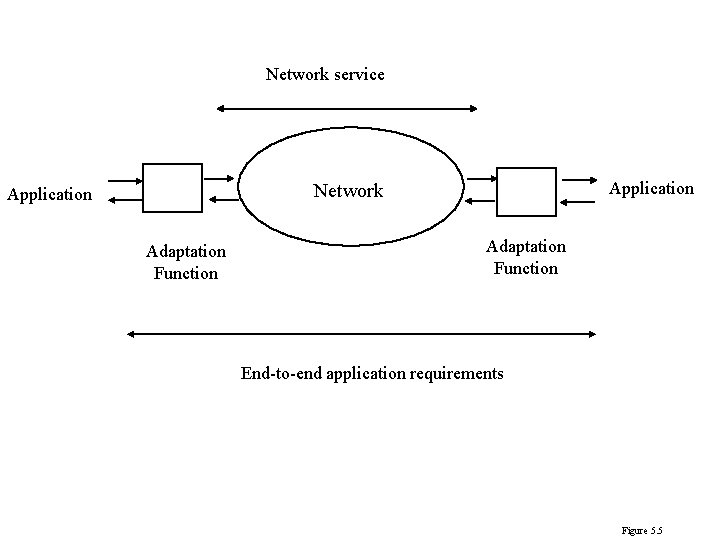
Network service Application Network Application Adaptation Function End-to-end application requirements Figure 5. 5

Issues in Transport Protocol • Issues to be addressed – Handling arbitrary message sizes è Segmentation/reassembly – Reliability and sequencing è ARQ protocols – Pacing and flow control è Sliding window control è Congestion control – Timing: sequence numbering or time-stamping – Addressing – Privacy, integrity, and authentication

Addressing • Target user specified by: – User identification è Usually a host, port number è Port represents a particular transport service (TS) user – Transport entity identification (e. g. , TCP, UDP) – Host address è An attached network device è In an internet, a global internet address – Network number • Address=<galaxy><star><planet><country>< network><host><port>

Finding Addresses • Four methods – Know address ahead of time è e. g. collection of network device stats: device ID – Well known addresses – Name server or directory server – Sending process request to well known address è Address Resolution Protocol (ARP)

Multiplexing • Multiple users employ the same network connection • User identified by port number or service access point (SAP) • May also multiplex with respect to network services used – e. g. , multiplexing a single virtual X. 25 circuit to a number of transport service user è X. 25 charges per virtual circuit connection time

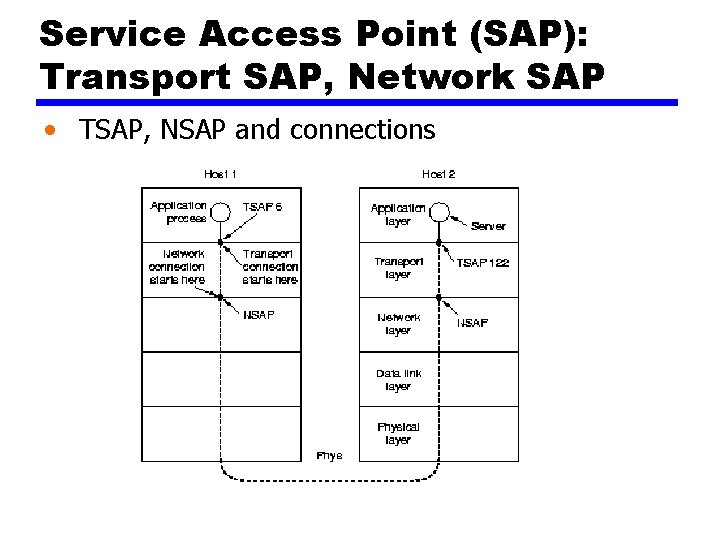
Service Access Point (SAP): Transport SAP, Network SAP • TSAP, NSAP and connections

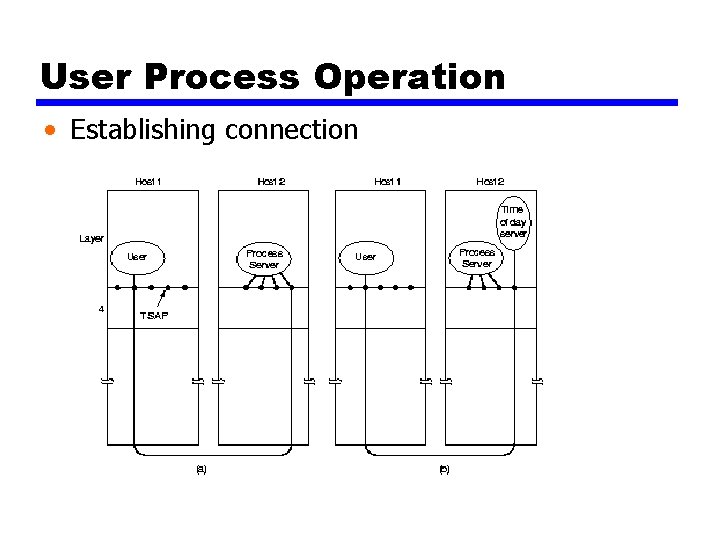
User Process Operation • Establishing connection

Flow Control • Longer transmission delay between transport entities compared with actual transmission time – Delay in communication of flow control info • Variable transmission delay – Difficult to use timeouts • Flow may be controlled because: – The receiving user can not keep up – The receiving transport entity can not keep up • Results in buffer filling up (buffer overflow)

Flow Control (Cont) • Do nothing – Segments that overflow are discarded – Sending transport entity will fail to get ACK and will retransmit: time-out • Refuse further segments – Clumsy – Multiplexed connections are controlled on aggregate flow

Flow Control (Cont) • Use fixed sliding window protocol – Incorporated in ARQ as well as congestion control – Works well on reliable network è Failure to receive ACK is taken as flow control indication – Does not work well on unreliable network è Can not distinguish between lost segment and flow control • Use credit schemes – Successful delivery (positive ack) will lead to more packet deliveries • Will discuss more in next chapter

Establishment and Termination • • Allow each end to know the other exists Negotiation of optional parameters (for Qo. S) Triggers allocation of transport entity resources By mutual agreement

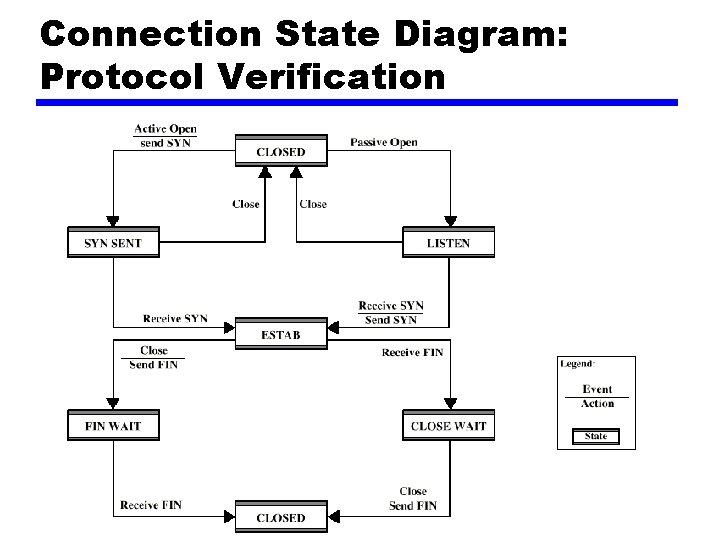
Connection State Diagram: Protocol Verification

Problems to Be Handled • • Ordered Delivery Retransmission strategy (ARQ) Duplication detection (Sequence Number) Flow control (Sliding Window) Connection establishment Connection termination Crash recovery

TCP/IP Suite • Transmission Control Protocol (TCP) – Connection oriented – RFC 793 • User Datagram Protocol (UDP) – Connectionless – RFC 768

TCP Services • Reliable communication between a pair of processes (end users) • Across variety of reliable and unreliable networks and internets • Two labeling facilities – Data stream push è TCP user can require transmission of all data up to push flag è Receiver will deliver in same manner è Avoids waiting for full buffers – Urgent data signal è Indicates urgent data is upcoming in stream è User decides how to handle it

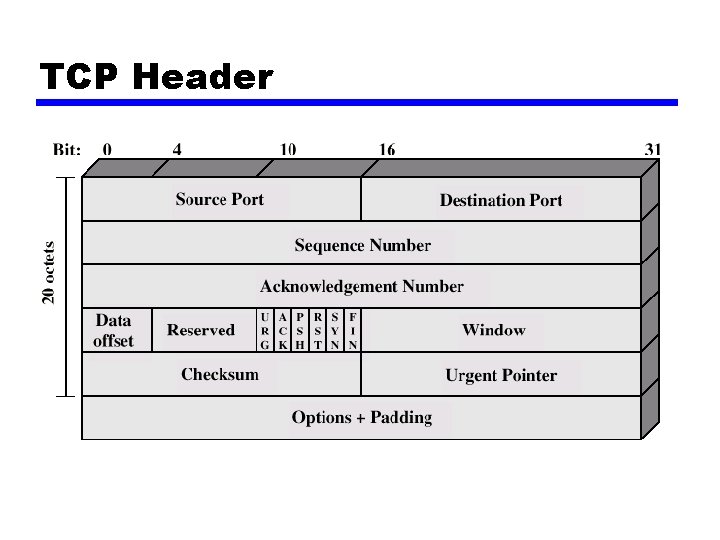
TCP Header

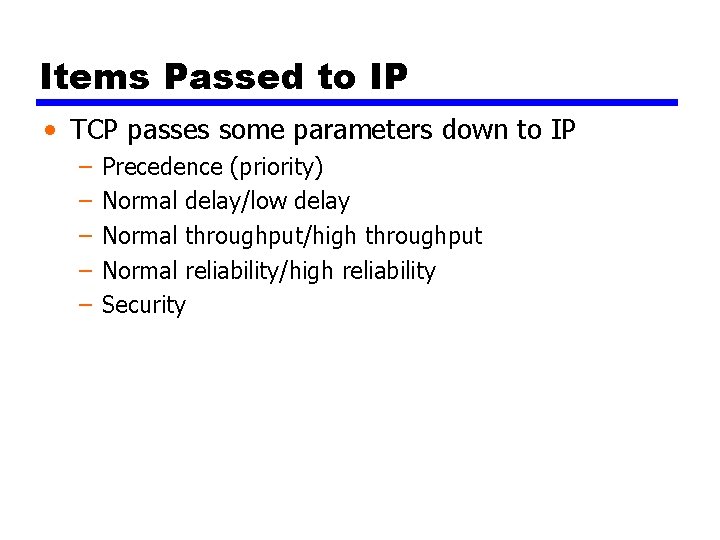
Items Passed to IP • TCP passes some parameters down to IP – – – Precedence (priority) Normal delay/low delay Normal throughput/high throughput Normal reliability/high reliability Security

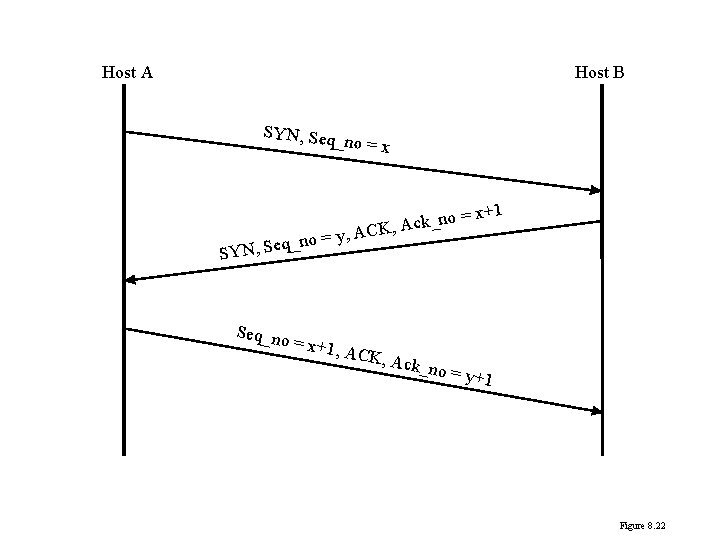
TCP Mechanisms • Connection establishment – Three way handshake – Between pair of ports – One port can connect to multiple destinations

Host A Host B SYN, Seq_ no = x q_no e S , N Y S Seq_no k c A , K , AC =y = x+1, ACK, A ck_no = = x+1 y+1 Figure 8. 22

TCP Mechanisms (cont) • Data transfer – – Logical stream of octets Flow control by credit allocation of number of octets Data buffered at transmitter and receiver Error control è Selective Repeat (SR) ARQ è Sliding window scheme is used è Time-out is adaptively estimated based on the estimation of Round-Trip-Time (RTT) (more will be discussed in congestion control)

TCP Mechanisms (cont) • Connection termination – – Graceful close TCP users issues CLOSE primitive Transport entity sets FIN flag on last segment sent Abrupt termination by ABORT primitive è Entity abandons all attempts to send or receive data è RST segment transmitted

UDP • User Datagram Protocol • RFC 768 • Connectionless service for application level procedures – Unreliable – Delivery and duplication control not guaranteed • Reduced overhead • e. g. network management (ICMP)

UDP Applicaitons • • Inward data collection Outward data dissemination Request-Response Real time application

Reading • Textbook Chapter 5, Chapter 8 • Tanenbaum, Chapter 6 • Stallings Chapter 17