EEE 449 Computer Networks The Data Link Layer


























- Slides: 58

EEE 449 Computer Networks The Data Link Layer Part 3: Error Control En. Mohd Nazri Mahmud MPhil (Cambridge, UK) BEng (Essex, UK) nazriee@eng. usm. my Room 2. 14 Semester 1 2011 -2012

Error Control & Detection • detection and correction of errors such as: – lost frames – damaged frames • common techniques use: – error detection – positive acknowledgment – retransmission after timeout – negative acknowledgement & retransmission Semester 1 2009 -2010 Copyright USM

Error detection • Parity Check • CRC Semester 1 2009 -2010 Copyright USM

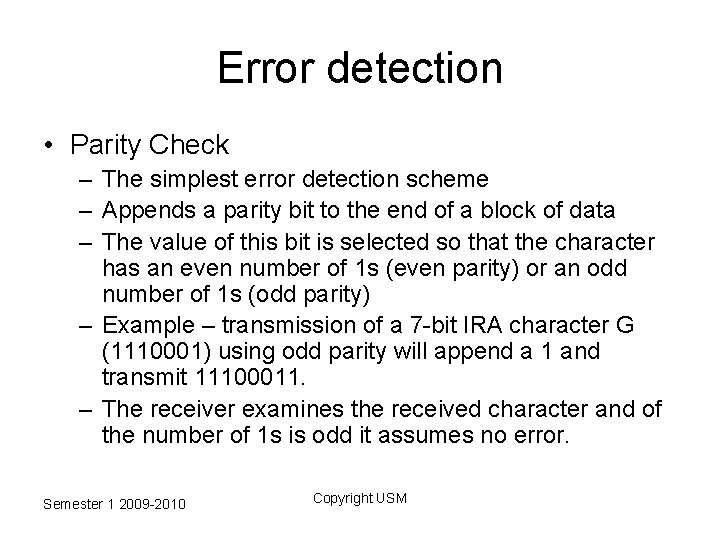
Error detection • Parity Check – The simplest error detection scheme – Appends a parity bit to the end of a block of data – The value of this bit is selected so that the character has an even number of 1 s (even parity) or an odd number of 1 s (odd parity) – Example – transmission of a 7 -bit IRA character G (1110001) using odd parity will append a 1 and transmit 11100011. – The receiver examines the received character and of the number of 1 s is odd it assumes no error. Semester 1 2009 -2010 Copyright USM

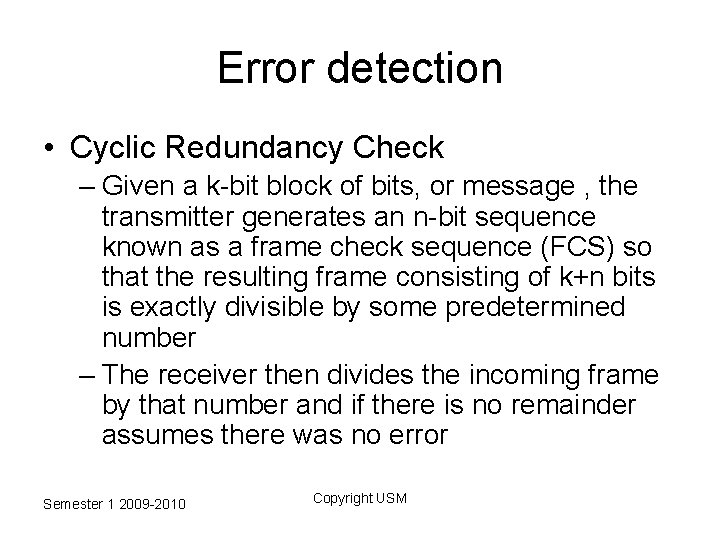
Error detection • Cyclic Redundancy Check – Given a k-bit block of bits, or message , the transmitter generates an n-bit sequence known as a frame check sequence (FCS) so that the resulting frame consisting of k+n bits is exactly divisible by some predetermined number – The receiver then divides the incoming frame by that number and if there is no remainder assumes there was no error Semester 1 2009 -2010 Copyright USM

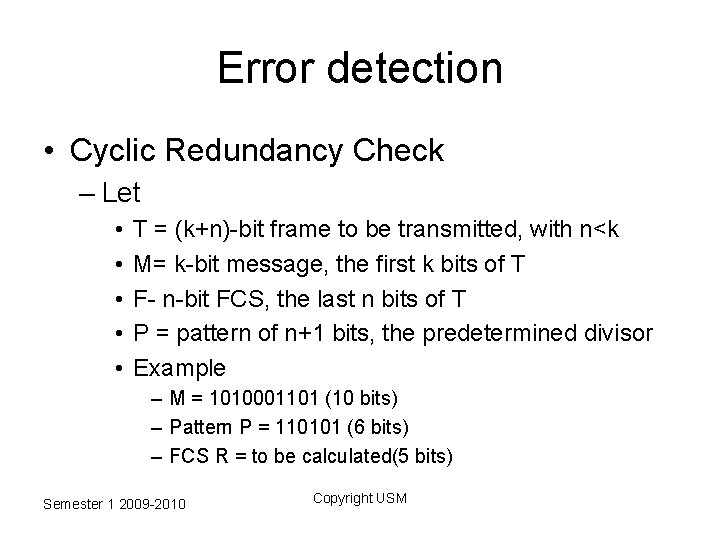
Error detection • Cyclic Redundancy Check – Let • • • T = (k+n)-bit frame to be transmitted, with n<k M= k-bit message, the first k bits of T F- n-bit FCS, the last n bits of T P = pattern of n+1 bits, the predetermined divisor Example – M = 1010001101 (10 bits) – Pattern P = 110101 (6 bits) – FCS R = to be calculated(5 bits) Semester 1 2009 -2010 Copyright USM

Error detection • Cyclic Redundancy Check • Example – M = 1010001101 (10 bits) – Pattern P = 110101 (6 bits) – FCS R = to be calculated(5 bits ie n=5) – – – Operations are carried out in modulo-2 arithmetic The message is multiplied by 2 n ie=(25) giving 101000110100000 The product is divided by P giving remainder or 01110 The remainder is added to 2 n. M to give T = 101000110101110 At the receiver the received frame is divided by P, if there is no remainder, it assumes no error. – The pattern P is chosen to be one bit longer than the desired FCS and the exact bit pattern chosen depends on the types of errors expected Semester 1 2009 -2010 Copyright USM

Error detection • Cyclic Redundancy Check – Polynomial treatment of the CRC • Express all values as polynomials in a dummy variable X with binary coefficients • The coefficients correspond to the bits in the binary number • For example for a message M = 1010001101 in polynomial form is X 9 + X 7 + X 3 + X 2 + 1 and pattern P= 110101 as X 5 + X 4 +X 2 + 1 • Modulo-2 arithmetic is used again Semester 1 2009 -2010 Copyright USM

Error detection • Cyclic Redundancy Check – 4 versions of pattern, P are widely used – CRC-12 system is used for transmission of streams of 6 -bit characters and generates a 12 -bit FCS – Both CRC-16 and CRC-CCITT are popular for 8 -bit characters with 16 -bit FCS. Semester 1 2009 -2010 Copyright USM

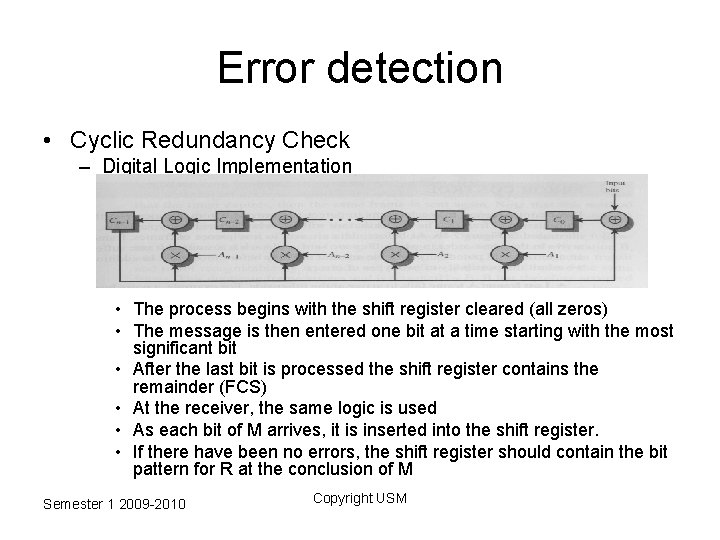
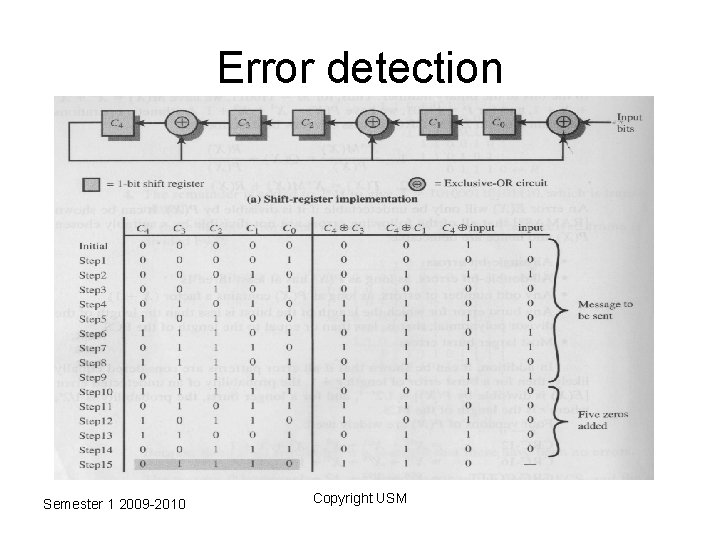
Error detection • Cyclic Redundancy Check – Digital Logic Implementation • The CRC process can be implemented as individual circuit consisting of EX-OR gates and a shift register Semester 1 2009 -2010 Copyright USM

Error detection • Cyclic Redundancy Check – Digital Logic Implementation • The register contains n bits (equal to the length of the FCS) • There are up to n EX-OR gates • The presence or absence of a gate corresponds to the presence or absence of a term in the divisor polynomial, P(X) excluding the Xn term Semester 1 2009 -2010 Copyright USM

Error detection • Cyclic Redundancy Check – Digital Logic Implementation • The process begins with the shift register cleared (all zeros) • The message is then entered one bit at a time starting with the most significant bit • After the last bit is processed the shift register contains the remainder (FCS) • At the receiver, the same logic is used • As each bit of M arrives, it is inserted into the shift register. • If there have been no errors, the shift register should contain the bit pattern for R at the conclusion of M Semester 1 2009 -2010 Copyright USM

Error detection • Cyclic Redundancy Check – Digital Logic Implementation • At the receiver, the same logic is used • As each bit of M arrives, it is inserted into the shift register. • If there have been no errors, the shift register should contain the bit pattern for R at the conclusion of M • The transmitted bits of R now begin to arrive and the effect is to zero out the register so that at the conclusion of reception, the register contains all 0 s Semester 1 2009 -2010 Copyright USM

Error detection • Cyclic Redundancy Check – Digital Logic Implementation • For example for message M = 1010001101 and divisor P = 110101 Semester 1 2009 -2010 Copyright USM

Error detection Semester 1 2009 -2010 Copyright USM

Error Control : Automatic Repeat Request (ARQ) • collective name for such error control mechanisms, including: – stop and wait – go back N – selective reject (selective retransmission) Semester 1 2009 -2010 Copyright USM

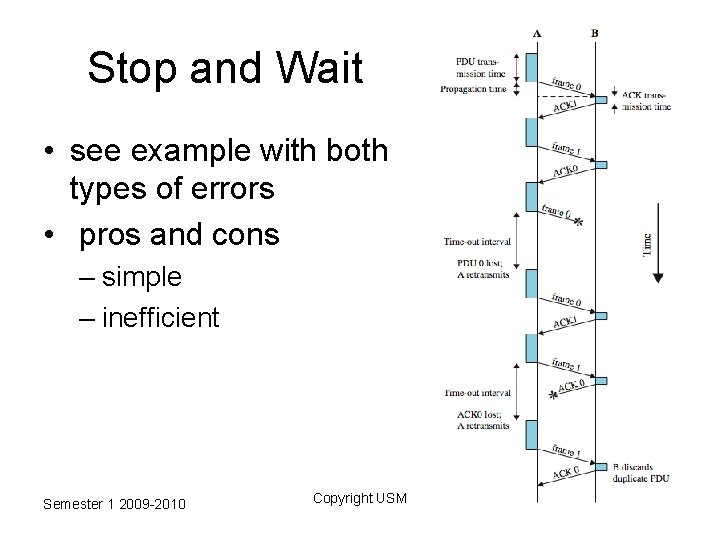
Stop and Wait • source transmits single frame • wait for ACK • if received frame damaged, discard it – transmitter has timeout – if no ACK within timeout, retransmit • if ACK damaged, transmitter will not recognize it – transmitter will retransmit – receive gets two copies of frame – use alternate numbering and ACK 0 / ACK 1 Semester 1 2009 -2010 Copyright USM

Stop and Wait • see example with both types of errors • pros and cons – simple – inefficient Semester 1 2009 -2010 Copyright USM

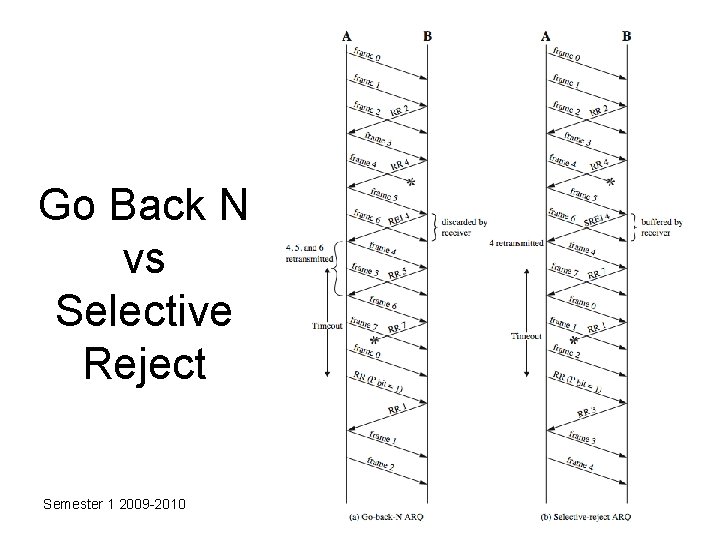
Go Back N • based on sliding window • if no error, ACK as usual • use window to control number of outstanding frames • if error, reply with rejection – discard that frame and all future frames until error frame received correctly – transmitter must go back and retransmit that frame and all subsequent frames Semester 1 2009 -2010 Copyright USM

Go Back N - Handling • Damaged Frame – error in frame i so receiver rejects frame i – transmitter retransmits frames from i • Lost Frame – frame i lost and either • transmitter sends i+1 and receiver gets frame i+1 out of seq and rejects frame i • or transmitter times out and send ACK with P bit set which receiver responds to with ACK i – transmitter then retransmits frames from i Semester 1 2009 -2010 Copyright USM

Go Back N - Handling • Damaged Acknowledgement – receiver gets frame i, sends ack (i+1) which is lost – acks are cumulative, so next ack (i+n) may arrive before transmitter times out on frame i – if transmitter times out, it sends ack with P bit set – can be repeated a number of times before a reset procedure is initiated • Damaged Rejection – reject for damaged frame is lost – handled as for lost frame when transmitter times out Semester 1 2009 -2010 Copyright USM

Selective Reject • also called selective retransmission • only rejected frames are retransmitted • subsequent frames are accepted by the receiver and buffered • minimizes retransmission • receiver must maintain large enough buffer • more complex logic in transmitter • hence less widely used • useful for satellite links with long propagation delays Semester 1 2009 -2010 Copyright USM

Go Back N vs Selective Reject Semester 1 2009 -2010 Copyright USM

Protocol case studies • HDLC • MAC for IEEE 802. 3 (The Ethernet) • IEEE 802. 11 (Wi. Fi)

Data Link Control Protocol: High Level Data Link Control (HDLC) • an important data link control protocol • specified as ISO 33009, ISO 4335 • station types: – Primary - controls operation of link – Secondary - under control of primary station – Combined - issues commands and responses • link configurations – Unbalanced - 1 primary, multiple secondary – Balanced - 2 combined stations Semester 1 2011 -2012

HDLC Transfer Modes • Normal Response Mode (NRM) – unbalanced config, primary initiates transfer – used on multi-drop lines, eg host + terminals • Asynchronous Balanced Mode (ABM) – balanced config, either station initiates transmission, has no polling overhead, widely used • Asynchronous Response Mode (ARM) – unbalanced config, secondary may initiate transmit without permission from primary, rarely used Semester 1 2011 -2012

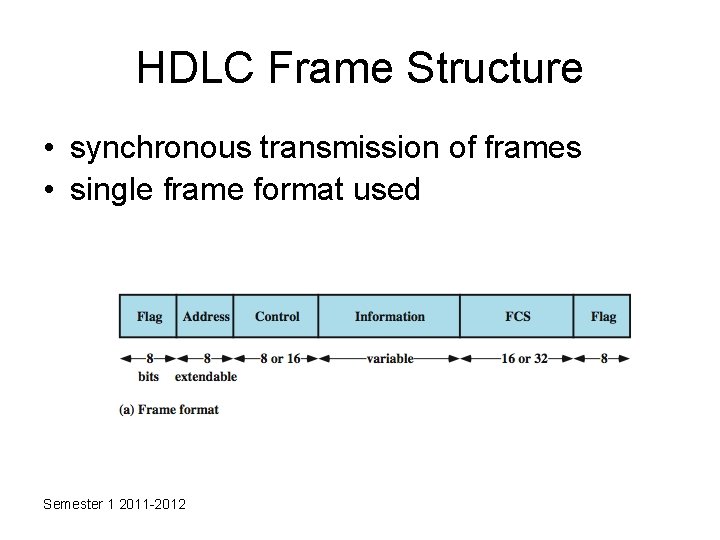
HDLC Frame Structure • synchronous transmission of frames • single frame format used Semester 1 2011 -2012

Flag Fields and Bit Stuffing • delimit frame at both ends with 01111110 seq • receiver hunts for flag sequence to synchronize • bit stuffing used to avoid confusion with data containing flag seq 01111110 – – – 0 inserted after every sequence of five 1 s if receiver detects five 1 s it checks next bit if next bit is 0, it is deleted (was stuffed bit) if next bit is 1 and seventh bit is 0, accept as flag if sixth and seventh bits 1, sender is indicating abort Semester 1 2011 -2012

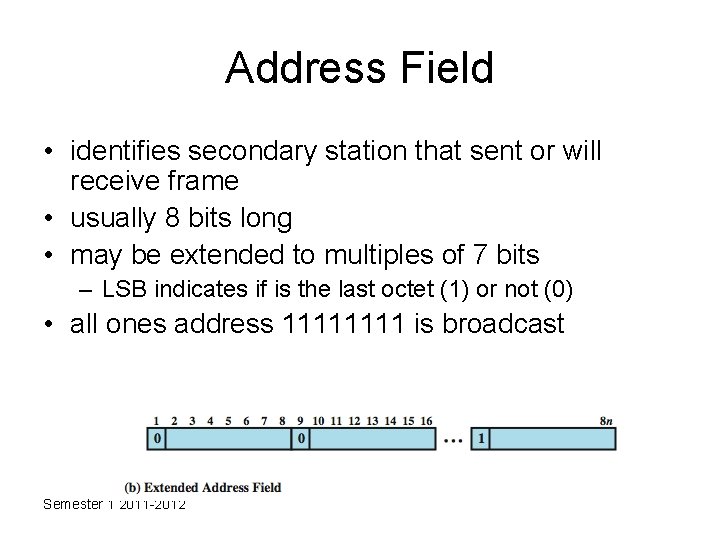
Address Field • identifies secondary station that sent or will receive frame • usually 8 bits long • may be extended to multiples of 7 bits – LSB indicates if is the last octet (1) or not (0) • all ones address 1111 is broadcast Semester 1 2011 -2012

Control Field • different for different frame type – Information - data transmitted to user (next layer up) • Flow and error control piggybacked on information frames – Supervisory - ARQ when piggyback not used – Unnumbered - supplementary link control • first 1 -2 bits of control field identify frame type Semester 1 2011 -2012

Control Field • use of Poll/Final bit depends on context • in command frame is P bit set to 1 to solicit (poll) response from peer • in response frame is F bit set to 1 to indicate response to soliciting command • seq number usually 3 bits – can extend to 8 bits as shown below Semester 1 2011 -2012

Information & FCS Fields • Information Field – in information and some unnumbered frames – must contain integral number of octets – variable length • Frame Check Sequence Field (FCS) – used for error detection – either 16 bit CRC or 32 bit CRC Semester 1 2011 -2012

HDLC Operation • consists of exchange of information, supervisory and unnumbered frames • have three phases – initialization • by either side, set mode & seq – data transfer • with flow and error control • using both I & S-frames (RR, RNR, REJ, SREJ) – disconnect • when ready or fault noted Semester 1 2011 -2012

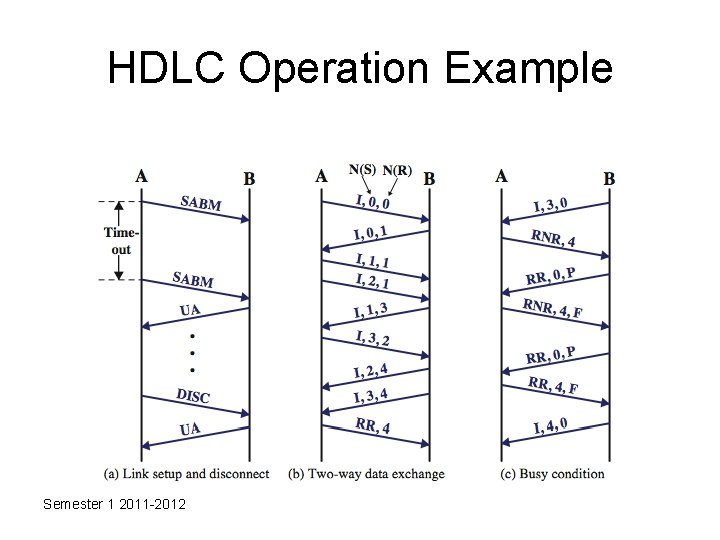
HDLC Operation Example Semester 1 2011 -2012

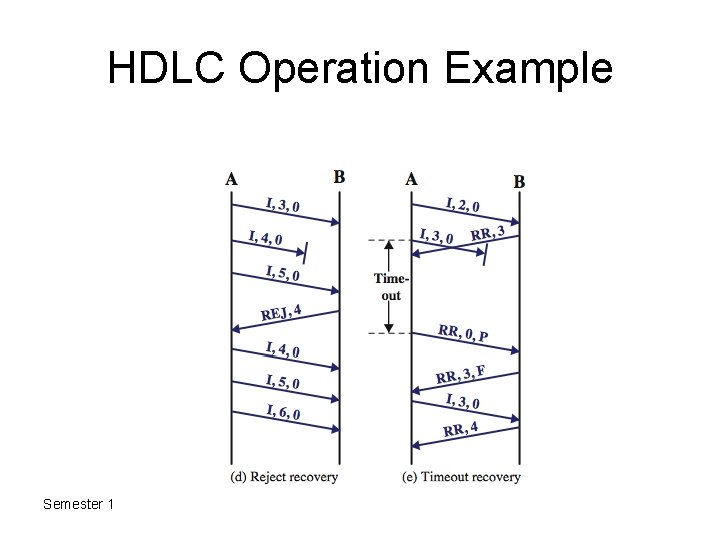
HDLC Operation Example Semester 1 2011 -2012

MAC for IEEE 802. 3 Wired LAN • Ethernet: IEEE 802. 3 Local Area Network (LAN) protocols • Ethernet protocols refer to the family of local-area network (LAN) covered by the IEEE 802. 3. • Access to the shared medium is controlled by Carrier-Sense Multiple Access/Collision Detection (CSMA/CD) protocol.

MAC for IEEE 802. 3 Wired LAN • The MAC sub-layer has two primary responsibilities: – Data encapsulation, including frame assembly before transmission, and frame parsing/error detection during and after reception – Media access control, including initiation of frame transmission and recovery from transmission failure

MAC for IEEE 802. 3 Wired LAN • • Each Ethernet-equipped computer operates independently of all other stations on the network: there is no central controller To send data a station first listens to the channel, and when the channel is idle the station transmits data in the form of an Ethernet frame, or packet After each frame transmission, all stations on the network must contend equally for the next frame transmission opportunity. The medium access control mechanism is based on a system called Carrier Sense Multiple Access with Collision Detection (CSMA/CD). As each Ethernet frame is sent onto the shared signal channel, all Ethernet interfaces look at the destination address If the destination address of the frame matches with the interface address, the frame will be read entirely and be delivered to the networking software running on that computer All other network interfaces will stop reading the frame when they discover that the destination address does not match their own address.

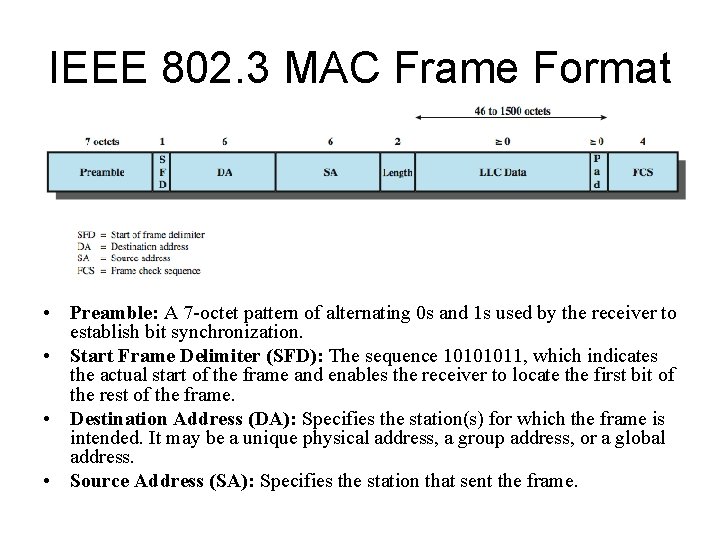
IEEE 802. 3 MAC Frame Format • Preamble: A 7 -octet pattern of alternating 0 s and 1 s used by the receiver to establish bit synchronization. • Start Frame Delimiter (SFD): The sequence 10101011, which indicates the actual start of the frame and enables the receiver to locate the first bit of the rest of the frame. • Destination Address (DA): Specifies the station(s) for which the frame is intended. It may be a unique physical address, a group address, or a global address. • Source Address (SA): Specifies the station that sent the frame.

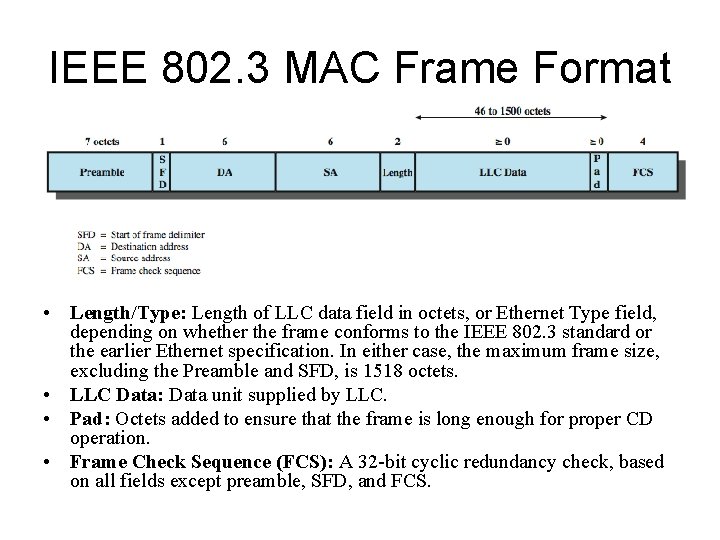
IEEE 802. 3 MAC Frame Format • Length/Type: Length of LLC data field in octets, or Ethernet Type field, depending on whether the frame conforms to the IEEE 802. 3 standard or the earlier Ethernet specification. In either case, the maximum frame size, excluding the Preamble and SFD, is 1518 octets. • LLC Data: Data unit supplied by LLC. • Pad: Octets added to ensure that the frame is long enough for proper CD operation. • Frame Check Sequence (FCS): A 32 -bit cyclic redundancy check, based on all fields except preamble, SFD, and FCS.

IEEE 802. 11 MAC • • For reliable data delivery, access control and security 802. 11 physical layer unreliable – noise, interference, and other propagation effects result in loss of frames – even with error-correction codes, frames may not successfully be received • IEEE 802. 11 includes a frame exchange protocol – When a station receives a data frame from another station, it returns an acknowledgment (ACK) frame to the source station – If the source does not receive an ACK within a short period of time, either because its data frame was damaged or because the returning ACK was damaged, the source retransmits the frame. • can use four-frame exchange for better reliability – a source first issues a Request to Send (RTS) frame to the destination. The destination then responds with a Clear to Send (CTS). – After receiving the CTS, the source transmits the data frame, and the destination responds with an ACK. – The RTS alerts all stations that are within reception range of the source that an exchange is under way; these stations refrain from transmission in order to avoid a collision between two frames transmitted at the same time – the CTS alerts all stations that are within reception range of the destination that an exchange is under way.

IEEE 802. 11 MAC • For access control – distributed access protocols, distribute the decision to transmit over all the nodes using a carrier sense mechanism – centralized access protocols, which involve regulation of transmission by a centralized decision maker • a MAC algorithm called DFWMAC (distributed foundation wireless MAC) that provides a distributed access control mechanism with an optional centralized control built on top of that.

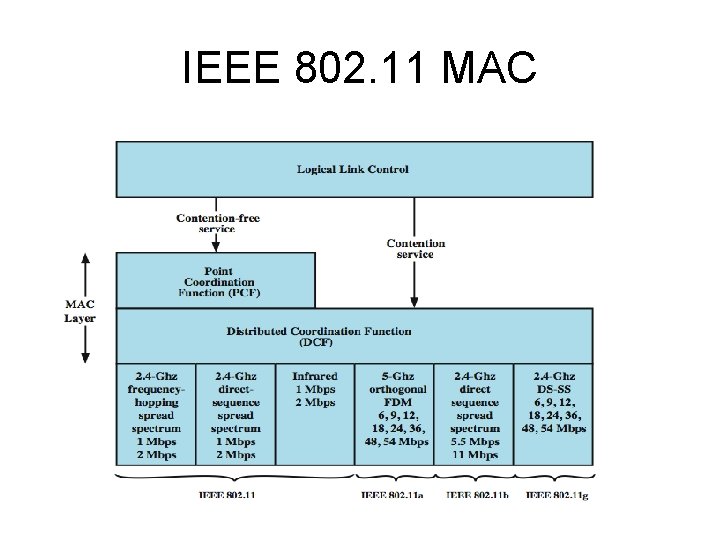
IEEE 802. 11 MAC

IEEE 802. 11 MAC • The lower sublayer of the MAC layer is the distributed coordination function (DCF). • DCF uses a contention algorithm to provide access to all traffic. Ordinary asynchronous traffic directly uses DCF. • The point coordination function (PCF) is a centralized MAC algorithm used to provide contention-free service. • PCF is built on top of DCF and exploits features of DCF to assure access for its users.

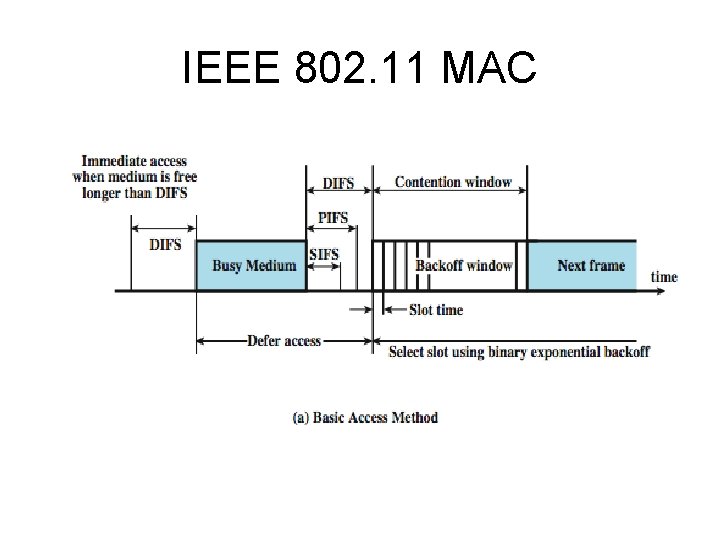
IEEE 802. 11 MAC • The DCF sublayer makes use of a simple CSMA (carrier sense multiple access) algorithm • If a station has a MAC frame to transmit, it listens to the medium. • If the medium is idle, the station may transmit; otherwise the station must wait until the current transmission is complete before transmitting. • The DCF does not include a collision detection function (i. e. , CSMA/CD) because collision detection is not practical on a wireless network. • The dynamic range of the signals on the medium is very large, so that a transmitting station cannot effectively distinguish incoming weak signals from noise and the effects of its own transmission. • To ensure the smooth and fair functioning of this algorithm, DCF includes a set of delays that amounts to a priority scheme known as an interframe space (IFS).

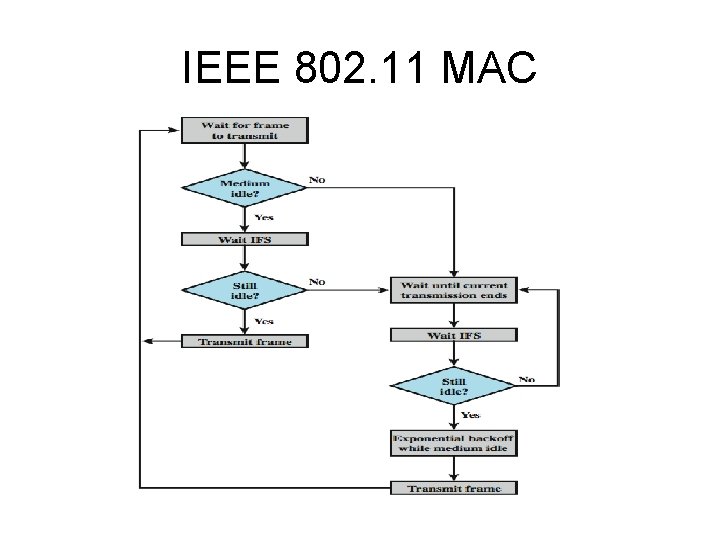
IEEE 802. 11 MAC

IEEE 802. 11 MAC The rules for CSMA access are as follows 1. A station with a frame to transmit senses the medium. If the medium is idle, it waits to see if the medium remains idle for a time equal to IFS. If so, the station may transmit immediately. 2. If the medium is busy (either because the station initially finds the medium busy or because the medium becomes busy during the IFS idle time), the station defers transmission and continues to monitor the medium until the current transmission is over. 3. Once the current transmission is over, the station delays another IFS. If the medium remains idle for this period, then the station backs off a random amount of time and again senses the medium. If the medium is still idle, the station may transmit. During the backoff time, if the medium becomes busy, the backoff timer is halted and resumes when the medium becomes idle. 4. If the transmission is unsuccessful, which is determined by the absence of an acknowledgement, then it is assumed that a collision has occurred. 5. To ensure that backoff maintains stability, binary exponential backoff is used. Repeated failed attempts to transmit result in longer and longer backoff times, which helps to smooth out the load

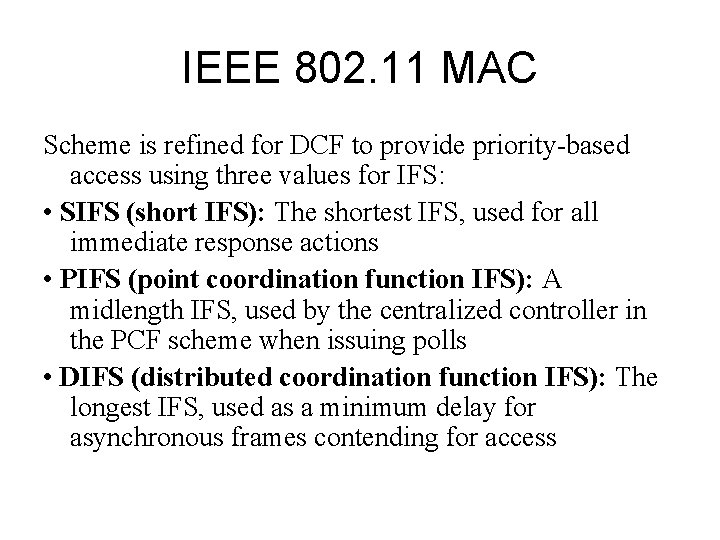
IEEE 802. 11 MAC Scheme is refined for DCF to provide priority-based access using three values for IFS: • SIFS (short IFS): The shortest IFS, used for all immediate response actions • PIFS (point coordination function IFS): A midlength IFS, used by the centralized controller in the PCF scheme when issuing polls • DIFS (distributed coordination function IFS): The longest IFS, used as a minimum delay for asynchronous frames contending for access

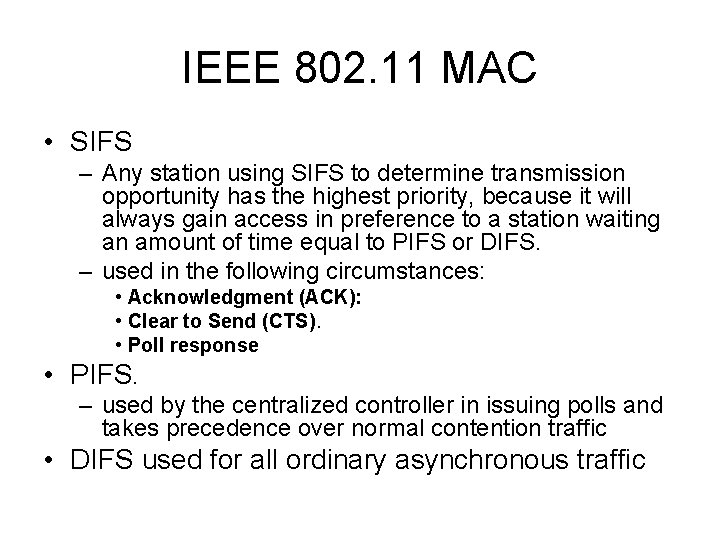
IEEE 802. 11 MAC • SIFS – Any station using SIFS to determine transmission opportunity has the highest priority, because it will always gain access in preference to a station waiting an amount of time equal to PIFS or DIFS. – used in the following circumstances: • Acknowledgment (ACK): • Clear to Send (CTS). • Poll response • PIFS. – used by the centralized controller in issuing polls and takes precedence over normal contention traffic • DIFS used for all ordinary asynchronous traffic

IEEE 802. 11 MAC

IEEE 802. 11 MAC • PCF – an alternative access method implemented on top of the DCF – The operation consists of polling by the centralized polling master (point coordinator). – The point coordinator makes use of PIFS when issuing polls. – Because PIFS is smaller than DIFS, the point coordinator can seize the medium and lock out all asynchronous traffic while it issues polls and receives responses. – stations with time-sensitive traffic are controlled by the point coordinator while remaining traffic contends for access using CSMA. – an interval known as the superframe is defined. During the first part of this interval, the point coordinator issues polls in a roundrobin fashion to all stations configured for polling. The point coordinator then idles for the remainder of the superframe, allowing a contention period for asynchronous access.

IEEE 802. 11 MAC the medium may be busy at the end of a superframe. In this case, the point coordinator must wait until the medium is idle to gain access; this results in a foreshortened superframe period for the next cycle.

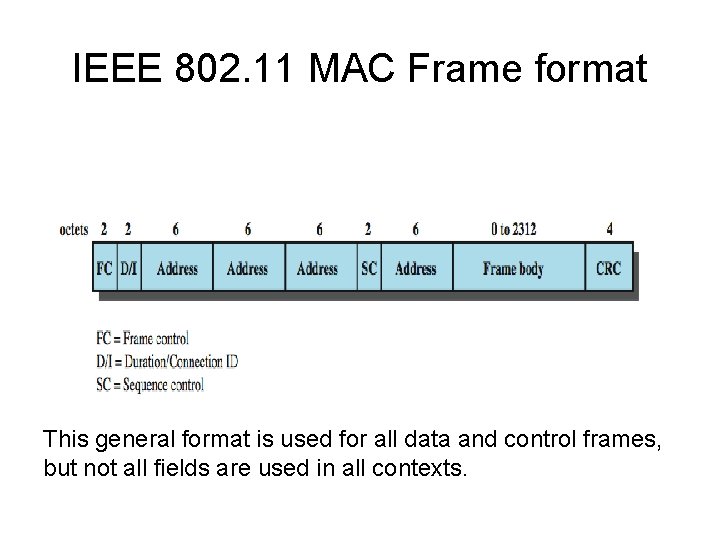
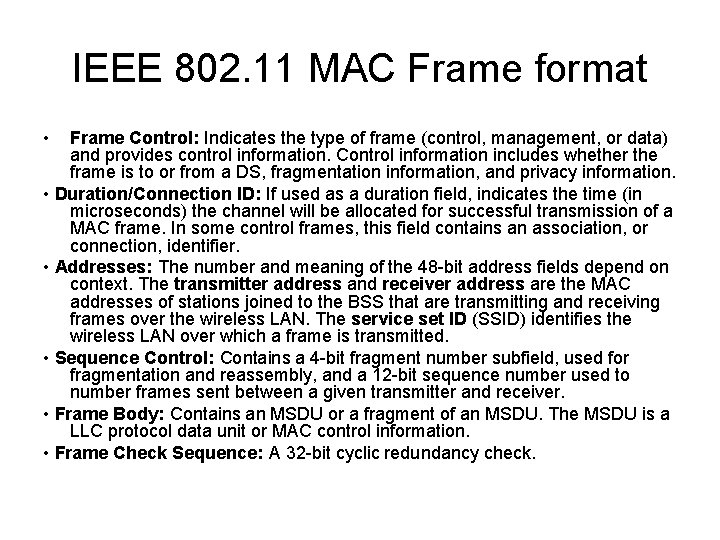
IEEE 802. 11 MAC Frame format This general format is used for all data and control frames, but not all fields are used in all contexts.

IEEE 802. 11 MAC Frame format • Frame Control: Indicates the type of frame (control, management, or data) and provides control information. Control information includes whether the frame is to or from a DS, fragmentation information, and privacy information. • Duration/Connection ID: If used as a duration field, indicates the time (in microseconds) the channel will be allocated for successful transmission of a MAC frame. In some control frames, this field contains an association, or connection, identifier. • Addresses: The number and meaning of the 48 -bit address fields depend on context. The transmitter address and receiver address are the MAC addresses of stations joined to the BSS that are transmitting and receiving frames over the wireless LAN. The service set ID (SSID) identifies the wireless LAN over which a frame is transmitted. • Sequence Control: Contains a 4 -bit fragment number subfield, used for fragmentation and reassembly, and a 12 -bit sequence number used to number frames sent between a given transmitter and receiver. • Frame Body: Contains an MSDU or a fragment of an MSDU. The MSDU is a LLC protocol data unit or MAC control information. • Frame Check Sequence: A 32 -bit cyclic redundancy check.

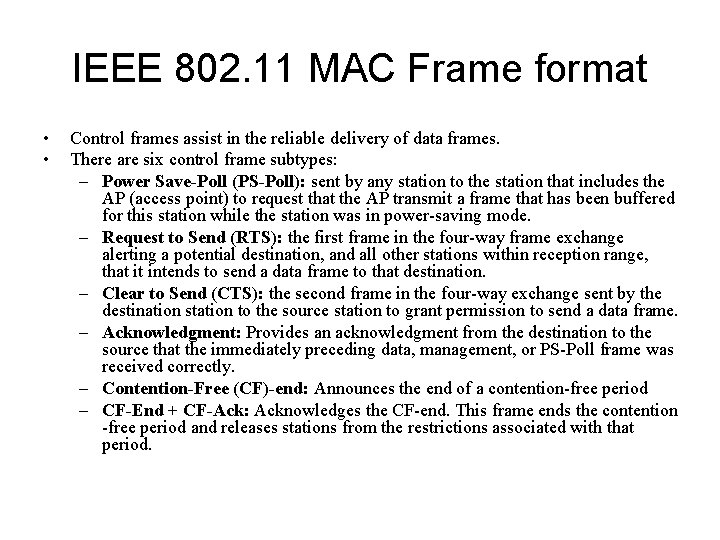
IEEE 802. 11 MAC Frame format • • Control frames assist in the reliable delivery of data frames. There are six control frame subtypes: – Power Save-Poll (PS-Poll): sent by any station to the station that includes the AP (access point) to request that the AP transmit a frame that has been buffered for this station while the station was in power-saving mode. – Request to Send (RTS): the first frame in the four-way frame exchange alerting a potential destination, and all other stations within reception range, that it intends to send a data frame to that destination. – Clear to Send (CTS): the second frame in the four-way exchange sent by the destination station to the source station to grant permission to send a data frame. – Acknowledgment: Provides an acknowledgment from the destination to the source that the immediately preceding data, management, or PS-Poll frame was received correctly. – Contention-Free (CF)-end: Announces the end of a contention-free period – CF-End + CF-Ack: Acknowledges the CF-end. This frame ends the contention -free period and releases stations from the restrictions associated with that period.

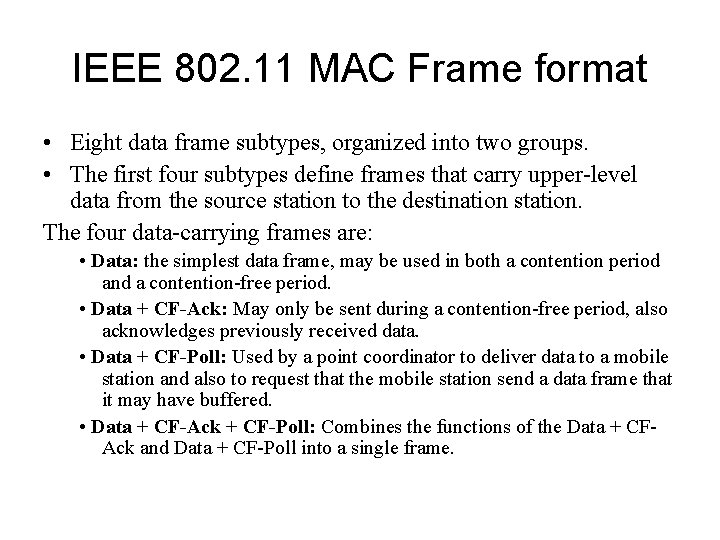
IEEE 802. 11 MAC Frame format • Eight data frame subtypes, organized into two groups. • The first four subtypes define frames that carry upper-level data from the source station to the destination station. The four data-carrying frames are: • Data: the simplest data frame, may be used in both a contention period and a contention-free period. • Data + CF-Ack: May only be sent during a contention-free period, also acknowledges previously received data. • Data + CF-Poll: Used by a point coordinator to deliver data to a mobile station and also to request that the mobile station send a data frame that it may have buffered. • Data + CF-Ack + CF-Poll: Combines the functions of the Data + CFAck and Data + CF-Poll into a single frame.

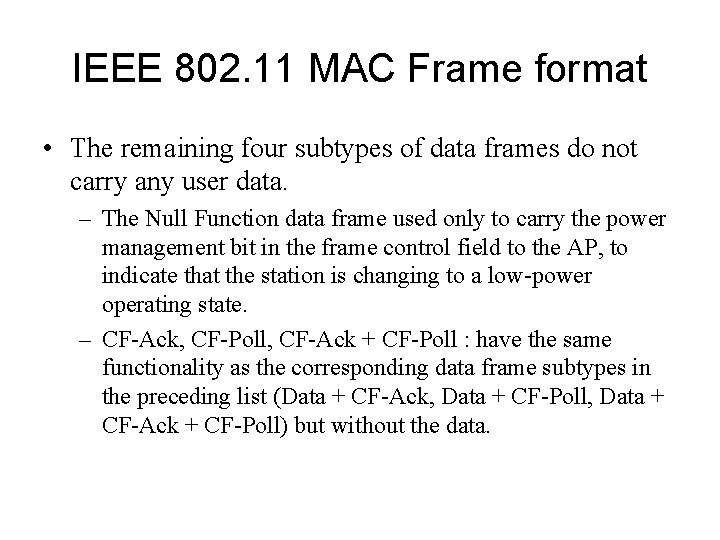
IEEE 802. 11 MAC Frame format • The remaining four subtypes of data frames do not carry any user data. – The Null Function data frame used only to carry the power management bit in the frame control field to the AP, to indicate that the station is changing to a low-power operating state. – CF-Ack, CF-Poll, CF-Ack + CF-Poll : have the same functionality as the corresponding data frame subtypes in the preceding list (Data + CF-Ack, Data + CF-Poll, Data + CF-Ack + CF-Poll) but without the data.

IEEE 802. 11 MAC Frame format • Management frames – used to manage communications between stations and APs – such as management of associations • requests, response, reassociation, dissociation, and authentication