EECS 470 Further review Pipeline Hazards and More
















































- Slides: 74

EECS 470 Further review: Pipeline Hazards and More Lecture 2 – Winter 2014 Slides developed in part by Profs. Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Vijaykumar, and Wenisch of Carnegie Mellon University, Purdue University, University of Michigan, University of Pennsylvania, and University of Wisconsin.

Bureaucracy & Scheduling Announcements • Get two-factor key. – Need to be able to run our tools remotely. – Log into login-twofactor. engin. umich. edu • HW 1 due Wednesday at the start of class – HW 2 also posted on Wednesday • Programming assignment 1 due Tuesday of next week (8 days) – Hand-in electronically by 9 pm • Should be reading – C. 1 -C. 3 (review) – 3. 1, 3. 4 -3. 5 (new material) 2

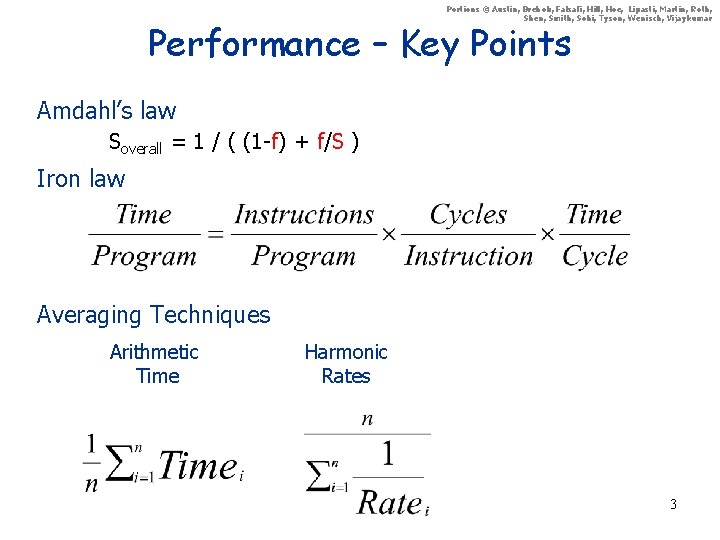
Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar Performance – Key Points Amdahl’s law Soverall = 1 / ( (1 -f) + f/S ) Iron law Averaging Techniques Arithmetic Time Harmonic Rates 3

Speedup Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar • While speedup is generally is used to explain the impact of parallel computation, we can also use it to discuss any performance improvement. r Keep in mind that if execution time stays the same, speedup is 1. r 200% speedup means that it takes half as long to do something. r So 50% “speedup” actually means it takes twice as long to do something. 4/73

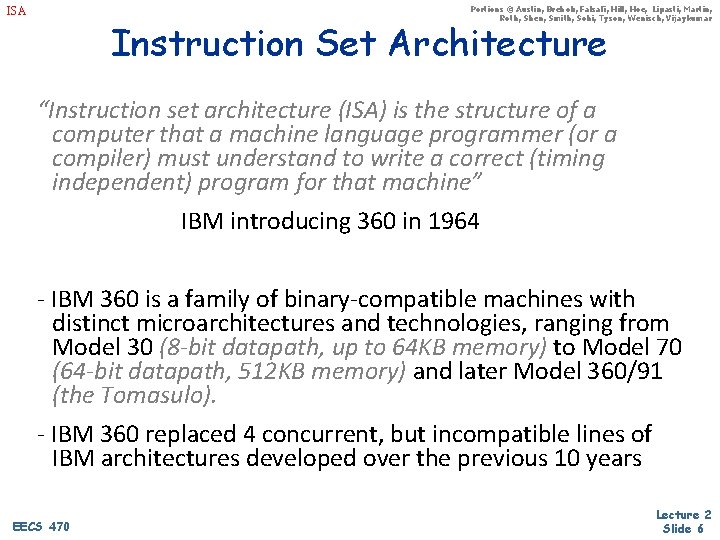
ISA Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar Instruction Set Architecture EECS 470 Lecture 2 Slide 5

Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar ISA Instruction Set Architecture “Instruction set architecture (ISA) is the structure of a computer that a machine language programmer (or a compiler) must understand to write a correct (timing independent) program for that machine” IBM introducing 360 in 1964 - IBM 360 is a family of binary-compatible machines with distinct microarchitectures and technologies, ranging from Model 30 (8 -bit datapath, up to 64 KB memory) to Model 70 (64 -bit datapath, 512 KB memory) and later Model 360/91 (the Tomasulo). - IBM 360 replaced 4 concurrent, but incompatible lines of IBM architectures developed over the previous 10 years EECS 470 Lecture 2 Slide 6

ISA Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar ISA: A contract between HW and SW • ISA (instruction set architecture) r A well-defined hardware/software interface r The “contract” between software and hardware Functional definition of operations, modes, and storage locations supported by hardware m Precise description of how to invoke, and access them m r No guarantees regarding How operations are implemented m Which operations are fast and which are slow and when m Which operations take more power and which take less m EECS 470 Lecture 2 Slide 7

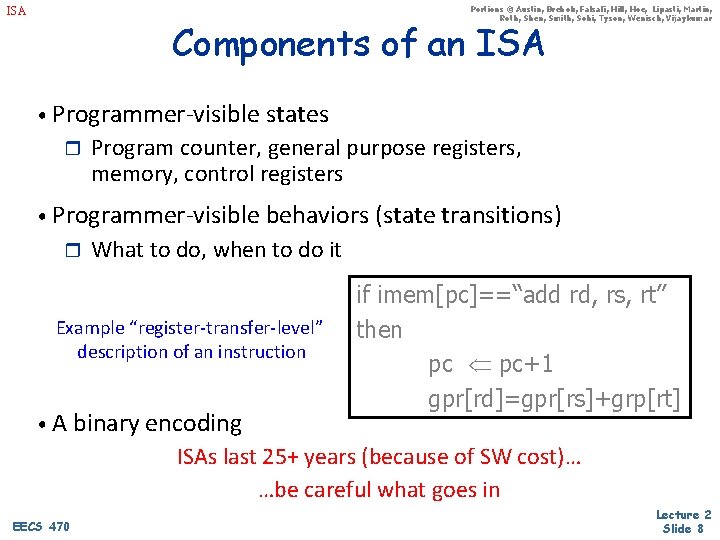
Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar ISA Components of an ISA • Programmer-visible states r Program counter, general purpose registers, memory, control registers • Programmer-visible behaviors (state transitions) r What to do, when to do it Example “register-transfer-level” description of an instruction • A binary encoding if imem[pc]==“add rd, rs, rt” then pc pc+1 gpr[rd]=gpr[rs]+grp[rt] ISAs last 25+ years (because of SW cost)… …be careful what goes in EECS 470 Lecture 2 Slide 8

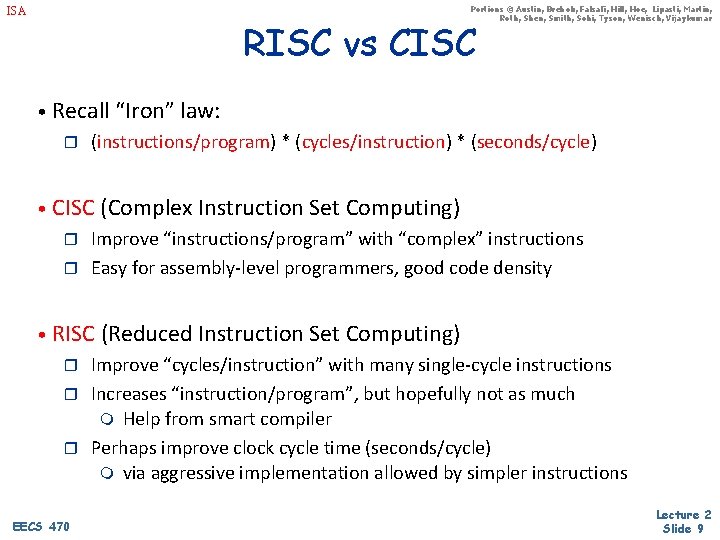
Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar ISA RISC vs CISC • Recall “Iron” law: r (instructions/program) * (cycles/instruction) * (seconds/cycle) • CISC (Complex Instruction Set Computing) r Improve “instructions/program” with “complex” instructions r Easy for assembly-level programmers, good code density • RISC (Reduced Instruction Set Computing) r Improve “cycles/instruction” with many single-cycle instructions r Increases “instruction/program”, but hopefully not as much m Help from smart compiler r Perhaps improve clock cycle time (seconds/cycle) m via aggressive implementation allowed by simpler instructions EECS 470 Lecture 2 Slide 9

Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar ISA What Makes a Good ISA? • Programmability r Easy to express programs efficiently? • Implementability r r Easy to design high-performance implementations? More recently m m m Easy to design low-power implementations? Easy to design high-reliability implementations? Easy to design low-cost implementations? • Compatibility Easy to maintain programmability (implementability) as languages and programs (technology) evolves? r x 86 (IA 32) generations: 8086, 286, 386, 486, Pentium. II, Pentium. III, Pentium 4, … r EECS 470 Lecture 2 Slide 10

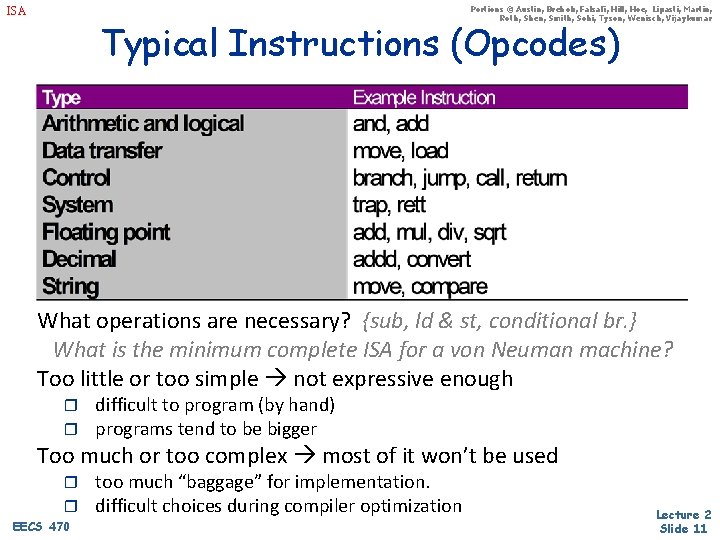
Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar ISA Typical Instructions (Opcodes) What operations are necessary? {sub, ld & st, conditional br. } What is the minimum complete ISA for a von Neuman machine? Too little or too simple not expressive enough r r difficult to program (by hand) programs tend to be bigger Too much or too complex most of it won’t be used r r EECS 470 too much “baggage” for implementation. difficult choices during compiler optimization Lecture 2 Slide 11

Basic Pipelining Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar Basic Pipelining 12

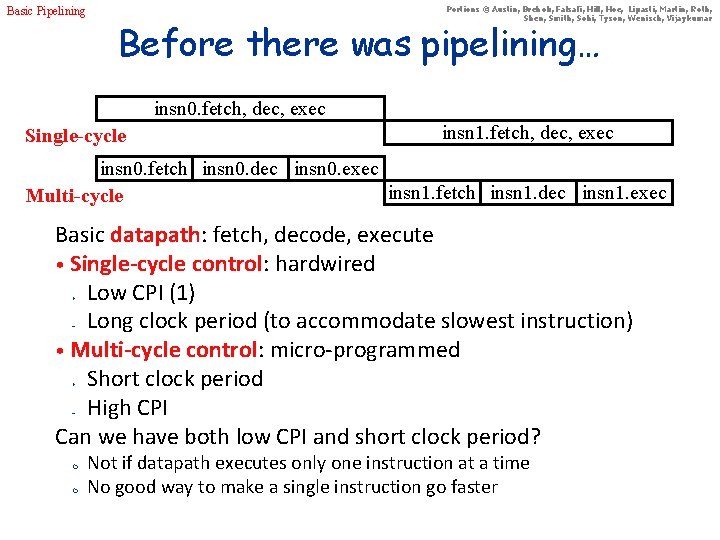
Basic Pipelining Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar Before there was pipelining… insn 0. fetch, dec, exec Single-cycle insn 1. fetch, dec, exec insn 0. fetch insn 0. dec insn 0. exec insn 1. fetch insn 1. dec insn 1. exec Multi-cycle Basic datapath: fetch, decode, execute • Single-cycle control: hardwired Low CPI (1) Long clock period (to accommodate slowest instruction) • Multi-cycle control: micro-programmed Short clock period High CPI Can we have both low CPI and short clock period? + – m m Not if datapath executes only one instruction at a time No good way to make a single instruction go faster

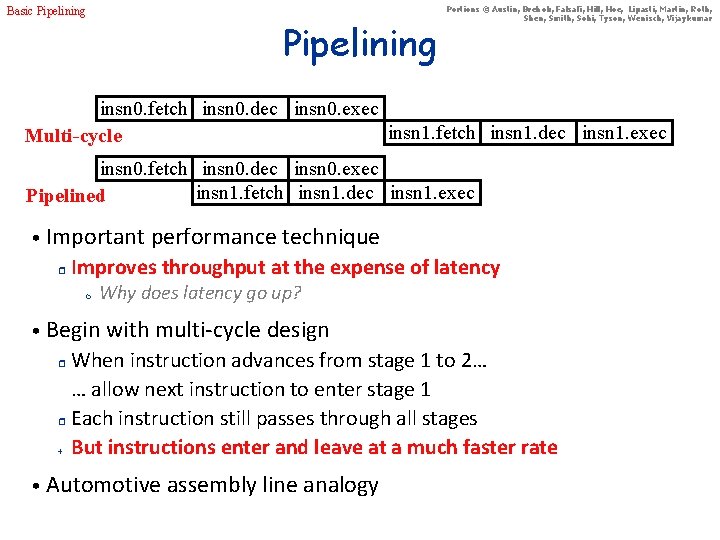
Basic Pipelining Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar insn 0. fetch insn 0. dec insn 0. exec insn 1. fetch insn 1. dec insn 1. exec Multi-cycle insn 0. fetch insn 0. dec insn 0. exec insn 1. fetch insn 1. dec insn 1. exec Pipelined • Important performance technique r Improves throughput at the expense of latency m Why does latency go up? • Begin with multi-cycle design When instruction advances from stage 1 to 2… … allow next instruction to enter stage 1 r Each instruction still passes through all stages + But instructions enter and leave at a much faster rate r • Automotive assembly line analogy

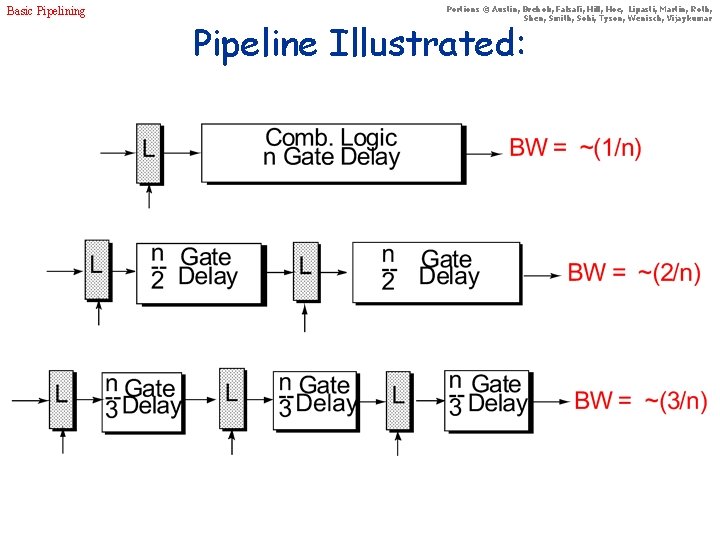
Basic Pipelining Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar Pipeline Illustrated:

Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar Basic Pipelining 370 Processor Pipeline Review Fetch Decode Execute Memory (Write-back) +1 PC I-cache Reg File Tpipeline = Tbase / 5 ALU D-cache

Basic Pipelining Portions © Austin, Brehob, Falsafi, Hill, Hoe, Lipasti, Martin, Roth, Shen, Smith, Sohi, Tyson, Wenisch, Vijaykumar Basic Pipelining • Data hazards r What are they? r How do you detect them? r How do you deal with them? • Micro-architectural changes r Pipeline depth r Pipeline width • Forwarding ISA (minor point) • Control hazards (time allowing) 17

Basic Pipelining Fetch Decode Execute Memory WB M U X 1 + PC+1 R 0 R 2 Register file Inst mem target 0 eq? R 1 reg. A reg. B instruction PC + R 3 val. A R 4 R 5 R 6 val. B R 7 offset M U X A L U ALU result mdata Data memory data dest val. B Bits 0 -2 Bits 16 -18 Bits 22 -24 IF/ ID M U X dest op op op EX/ Mem/ WB ID/ EX M U X 18

Basic Pipelining Fetch Decode Execute Memory WB M U X 1 + PC+1 R 0 M U X target 0 eq? R 1 reg. A reg. B R 2 Register file Inst mem instruction PC + R 3 val. A R 4 R 5 R 6 val. B R 7 offset M U X A L U ALU result mdata Data memory data dest val. B IF/ ID dest op op op EX/ Mem/ WB ID/ EX M U X 19

Basic Pipelining Fetch Decode Execute Memory WB M U X 1 + PC+1 R 0 M U X data target 0 eq? R 1 reg. A reg. B R 2 Register file Inst mem instruction PC + R 3 val. A R 4 R 5 R 6 val. B R 7 offset M U X A L U ALU result mdata M U X Data memory val. B IF/ ID op op op fwd fwd EX/ Mem/ WB ID/ EX 20

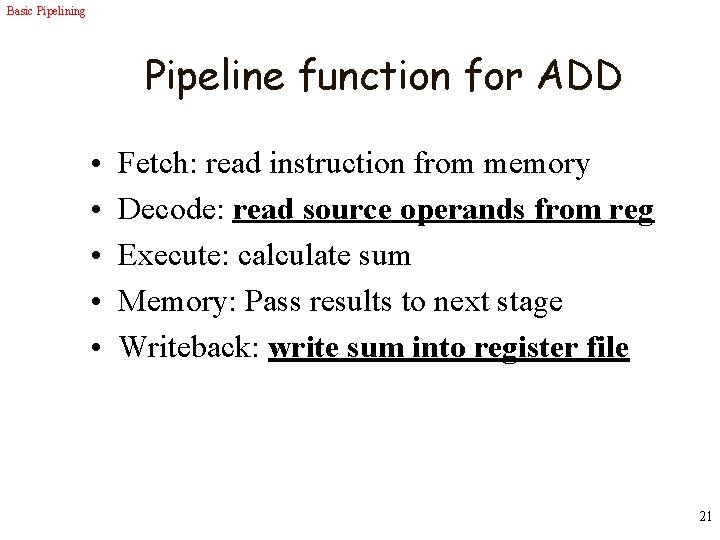
Basic Pipelining Pipeline function for ADD • • • Fetch: read instruction from memory Decode: read source operands from reg Execute: calculate sum Memory: Pass results to next stage Writeback: write sum into register file 21

Pipelining & Data Hazards add 1 2 3 nand 3 4 5 time add nand fetch decode fetch execute memory writeback decode memory writeback execute If not careful, you will read the wrong value of R 3 22

Pipelining & Data Hazards Three approaches to handling data hazards • Avoidance – Make sure there are no hazards in the code • Detect and Stall – If hazards exist, stall the processor until they go away. • Detect and Forward – If hazards exist, fix up the pipeline to get the correct value (if possible) 23

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward Handling data hazards: avoid all hazards • Assume the programmer (or the compiler) knows about the processor implementation. – Make sure no hazards exist. • Put noops between any dependent instructions. add 1 noop nand 3 2 3 write R 3 in cycle 5 4 5 read R 3 in cycle 6 24

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward Problems with this solution • Old programs (legacy code) may not run correctly on new implementations – Longer pipelines need more noops • Programs get larger as noops are included – Especially a problem for machines that try to execute more than one instruction every cycle – Intel EPIC: Often 25% - 40% of instructions are noops • Program execution is slower – CPI is one, but some I’s are noops 25

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward Handling data hazards: detect and stall • Detection: – Compare reg. A with previous Dest. Regs • 3 bit operand fields – Compare reg. B with previous Dest. Regs • 3 bit operand fields • Stall: – Keep current instructions in fetch and decode – Pass a noop to execute 26

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of Cycle 1 M U X 1 + PC+1 0 R 1 14 R 2 7 R 3 10 + target R 0 M U X data Register file Inst mem add 1 2 3 PC reg. A reg. B eq? val. A R 4 R 5 R 6 val. B R 7 offset M U X A L U ALU result mdata M U X Data memory val. B op IF/ ID ID/ EX op op EX/ Mem/ WB 27

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of Cycle 2 M U X 1 + PC+1 0 R 1 14 R 2 7 R 3 10 + target R 0 M U X 3 data Register file Inst mem nand 3 4 5 PC reg. A reg. B eq? 14 R 5 R 6 7 R 7 3 M U X A L U ALU result mdata M U X Data memory val. B add IF/ ID ID/ EX op op EX/ Mem/ WB 28

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 3 M U X Inst mem PC+1 Hazard detection nand 3 4 5 PC + 3 M U X reg. A reg. B 3 data 0 R 1 14 R 2 7 R 3 10 + target R 0 Register file 1 eq? 14 R 5 R 6 7 R 7 3 M U X A L U ALU result mdata M U X Data memory val. B add IF/ ID ID/ EX op op EX/ Mem/ WB 29

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward Hazard detected compare 3 reg. A compare reg. B REG file 3 IF/ ID ID/ EX 30

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward 1 Hazard detected compare 0 011 reg. A reg. B 011 3 31

Handling data hazards: detect and stall the pipeline until ready Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward • Detection: – Compare reg. A with previous Dest. Reg • 3 bit operand fields – Compare reg. B with previous Dest. Reg • 3 bit operand fields • Stall: Keep current instructions in fetch and decode Pass a noop to execute 32

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 3 en 1 PC Inst mem 2 nand 3 4 5 en + 1 Hazard 3 M U X R 0 R 1 reg. A reg. B 3 data R 2 Register file M U X R 3 R 4 R 5 R 6 0 14 7 10 11 + target eq? 14 7 R 7 M U X A L U ALU result mdata M U X Data memory val. B add IF/ ID ID/ EX EX/ Mem/ WB 33

Handling data hazards: detect and stall the pipeline until ready Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward • Detection: – Compare reg. A with previous Dest. Reg • 3 bit operand fields – Compare reg. B with previous Dest. Reg • 3 bit operand fields • Stall: – Keep current instructions in fetch and decode – Pass a noop to execute 34

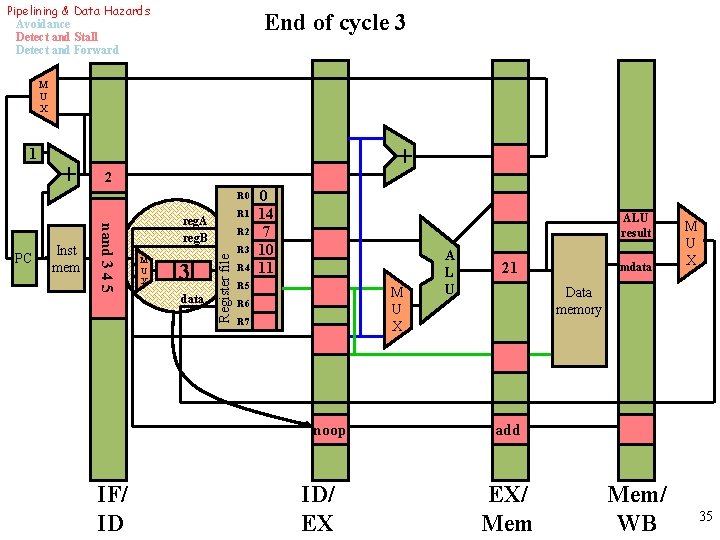
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of cycle 3 M U X 1 + + 2 R 0 M U X 3 data R 2 Register file Inst mem nand 3 4 5 PC R 1 reg. A reg. B R 3 R 4 0 14 7 10 11 ALU result R 5 M U X R 6 R 7 noop IF/ ID ID/ EX A L U 21 mdata M U X Data memory add EX/ Mem/ WB 35

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 4 en 1 PC Inst mem 2 Hazard nand 3 4 5 en + + 3 M U X R 0 R 1 reg. A reg. B 3 data R 2 Register file M U X R 3 R 4 0 14 7 10 11 ALU result R 5 M U X R 6 R 7 noop IF/ ID ID/ EX A L U 21 mdata M U X Data memory add EX/ Mem/ WB 36

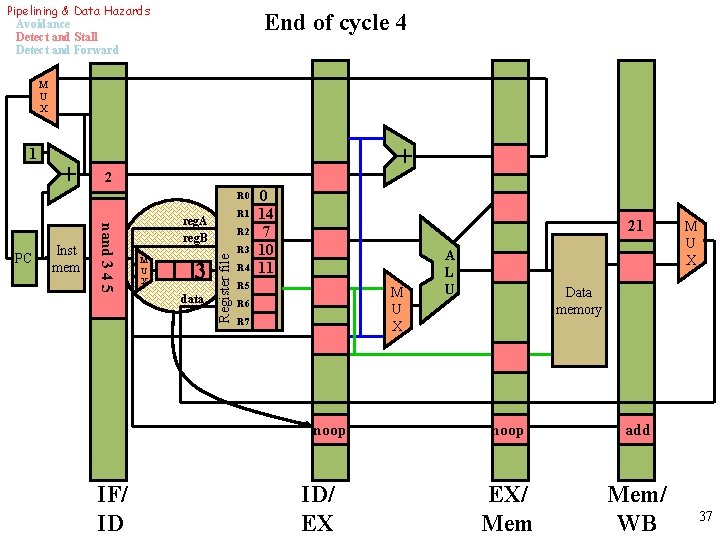
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of cycle 4 M U X 1 + + 2 R 0 M U X 3 data R 2 Register file Inst mem nand 3 4 5 PC R 1 reg. A reg. B R 3 R 4 0 14 7 10 11 21 R 5 M U X R 6 R 7 noop IF/ ID ID/ EX A L U M U X Data memory noop add EX/ Mem/ WB 37

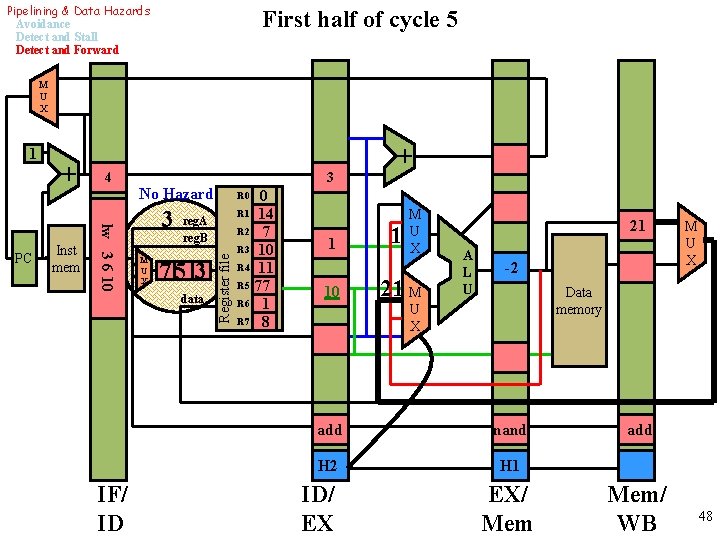
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 5 M U X Inst mem 2 nand 3 4 5 PC + + No Hazard R 0 3 R 1 M U X reg. A reg. B 3 data R 2 Register file 1 R 3 R 4 0 14 7 10 11 21 R 5 M U X R 6 R 7 noop IF/ ID ID/ EX A L U M U X Data memory noop add EX/ Mem/ WB 38

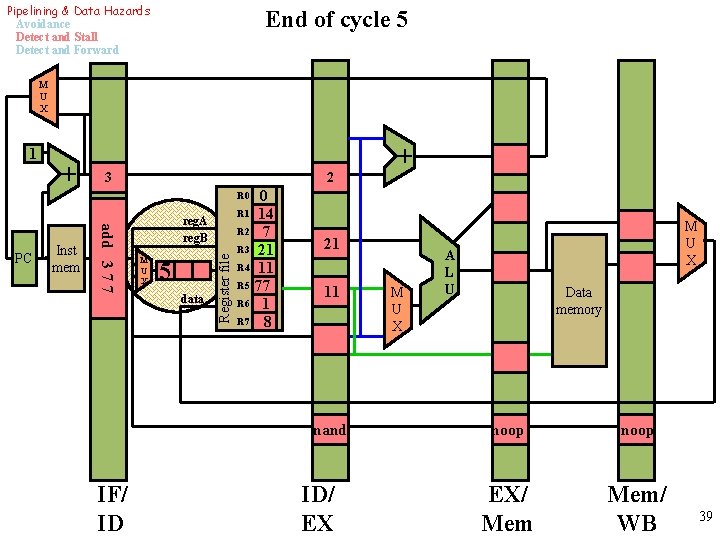
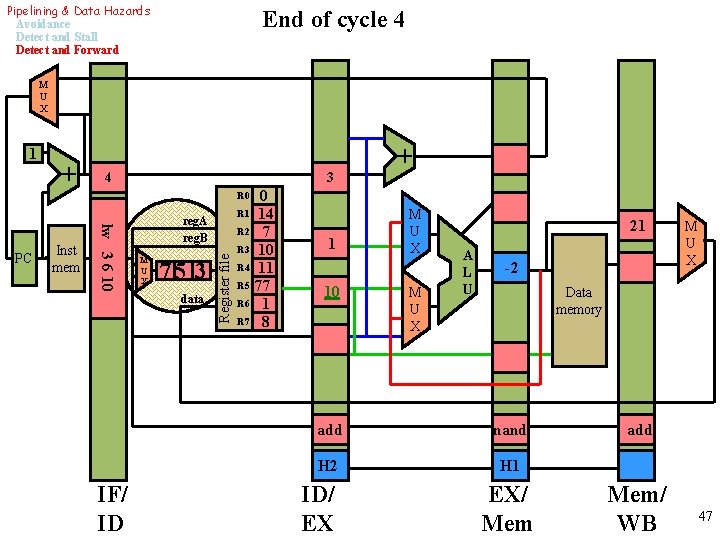
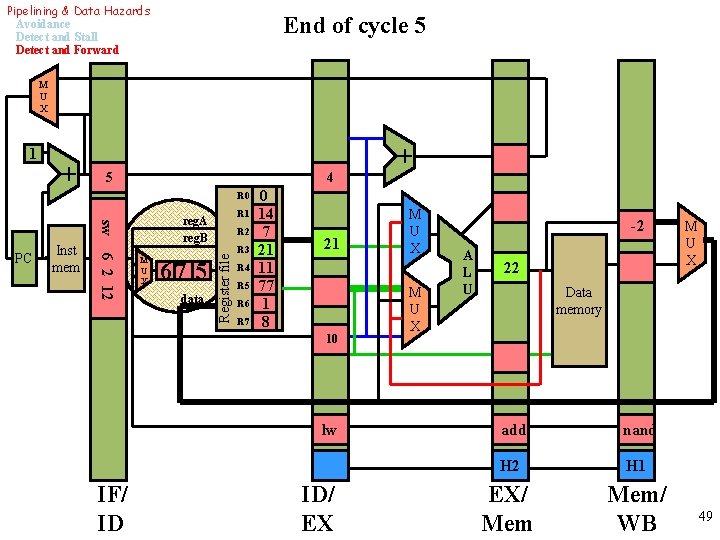
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of cycle 5 M U X 1 + 3 2 0 R 1 14 R 2 7 R 3 21 R 4 11 R 5 77 R 6 1 R 7 8 + R 0 M U X 5 data Register file Inst mem add 3 7 7 PC reg. A reg. B 21 11 nand IF/ ID ID/ EX M U X A L U Data memory noop EX/ Mem/ WB 39

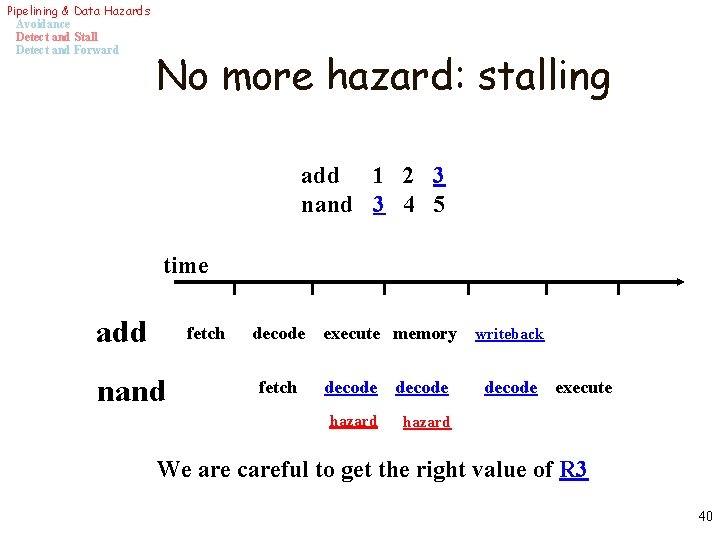
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward No more hazard: stalling add 1 2 3 nand 3 4 5 time add fetch nand decode fetch execute memory decode hazard writeback decode execute We are careful to get the right value of R 3 40

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward Problems with detect and stall • CPI increases every time a hazard is detected! • Is that necessary? Not always! – Re-route the result of the add to the nand • nand no longer needs to read R 3 from reg file • It can get the data later (when it is ready) • This lets us complete the decode this cycle – But we need more control to remember that the data that we aren’t getting from the reg file at this time will be found elsewhere in the pipeline at a later cycle. 41

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward Handling data hazards: detect and forward • Detection: same as detect and stall – Except that all 4 hazards are treated differently • i. e. , you can’t logical-OR the 4 hazard signals • Forward: – New datapaths to route computed data to where it is needed – New Mux and control to pick the right data 42

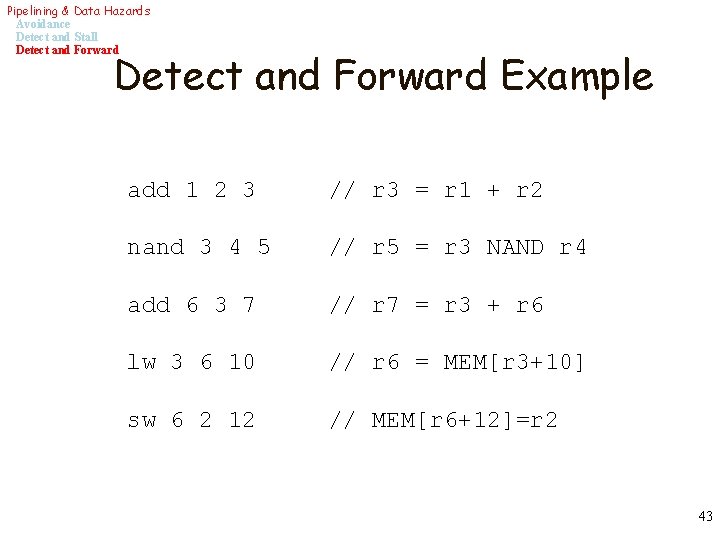
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward Example add 1 2 3 // r 3 = r 1 + r 2 nand 3 4 5 // r 5 = r 3 NAND r 4 add 6 3 7 // r 7 = r 3 + r 6 lw 3 6 10 // r 6 = MEM[r 3+10] sw 6 2 12 // MEM[r 6+12]=r 2 43

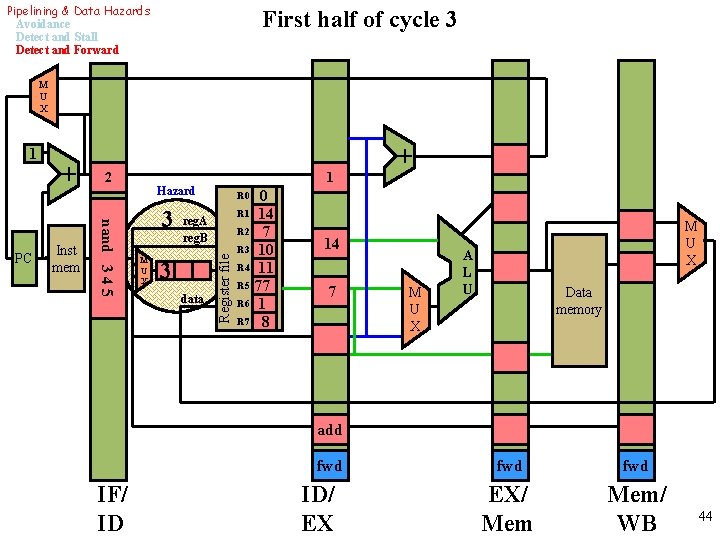
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 3 M U X Inst mem 2 nand 3 4 5 PC + 1 Hazard 3 M U X reg. A reg. B 3 data 0 R 1 14 R 2 7 R 3 10 R 4 11 R 5 77 R 6 1 R 7 8 + R 0 Register file 1 14 7 M U X A L U Data memory add fwd IF/ ID ID/ EX fwd EX/ Mem/ WB 44

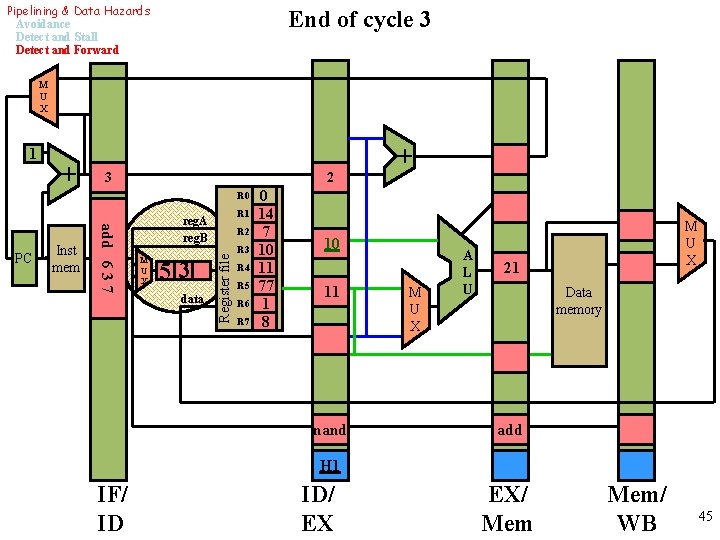
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of cycle 3 M U X 1 + 3 2 R 0 M U X 53 data R 2 Register file Inst mem add 6 3 7 PC R 1 reg. A reg. B R 3 R 4 R 5 R 6 R 7 0 14 7 10 11 77 1 8 + 10 11 nand M U X A L U M U X 21 Data memory add H 1 IF/ ID ID/ EX EX/ Mem/ WB 45

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 4 M U X Inst mem 3 add 6 3 7 PC + R 0 R 1 reg. A reg. B M U X 3 53 data + 2 New Hazard R 2 Register file 1 R 3 R 4 R 5 R 6 R 7 0 14 7 10 11 77 1 8 21 M U X 10 11 nand 11 M U X A L U M U X 21 Data memory add H 1 IF/ ID ID/ EX EX/ Mem/ WB 46

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of cycle 4 M U X 1 + 4 3 0 R 1 14 R 2 7 R 3 10 R 4 11 R 5 77 R 6 1 R 7 8 + R 0 M U X 75 3 data IF/ ID Register file Inst mem lw 3 6 10 PC reg. A reg. B 1 10 M U X 21 A L U -2 Data memory add nand H 2 H 1 ID/ EX M U X EX/ Mem add Mem/ WB 47

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 5 M U X Inst mem 4 lw 3 6 10 PC + No Hazard 3 M U X 75 3 0 R 1 14 R 2 7 R 3 10 R 4 11 R 5 77 R 6 1 R 7 8 + R 0 reg. A reg. B data IF/ ID 3 Register file 1 1 10 1 M U X 21 M 21 A L U -2 Data memory U X add nand H 2 H 1 ID/ EX M U X EX/ Mem add Mem/ WB 48

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of cycle 5 M U X 1 + 5 4 R 0 6 2 12 Inst mem M U X 67 5 data R 2 Register file sw PC R 1 reg. A reg. B R 3 R 4 R 5 R 6 R 7 0 14 7 21 11 77 1 8 21 10 lw IF/ ID ID/ EX + M U X -2 A L U 22 M U X Data memory add nand H 2 H 1 EX/ Mem/ WB 49

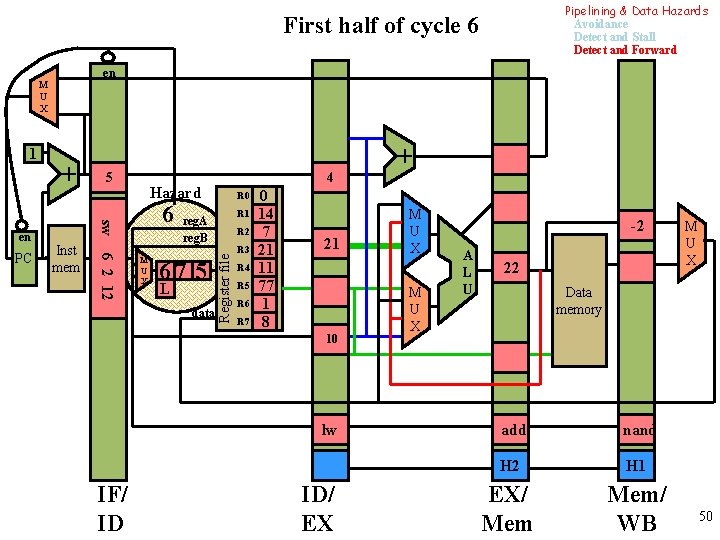
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 6 en 1 Inst mem 6 2 12 PC 5 4 Hazard 6 sw en + M U X R 0 R 1 reg. A reg. B 67 5 L data R 2 Register file M U X R 3 R 4 R 5 R 6 R 7 0 14 7 21 11 77 1 8 21 10 lw IF/ ID ID/ EX + M U X -2 A L U 22 M U X Data memory add nand H 2 H 1 EX/ Mem/ WB 50

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of cycle 6 M U X 1 + + 5 R 0 6 2 12 Inst mem M U X 67 data R 2 Register file sw PC R 1 reg. A reg. B R 3 R 4 R 5 R 6 R 7 0 14 7 21 11 -2 1 8 M U X noop 22 A L U 31 M U X Data memory lw add H 2 IF/ ID ID/ EX EX/ Mem/ WB 51

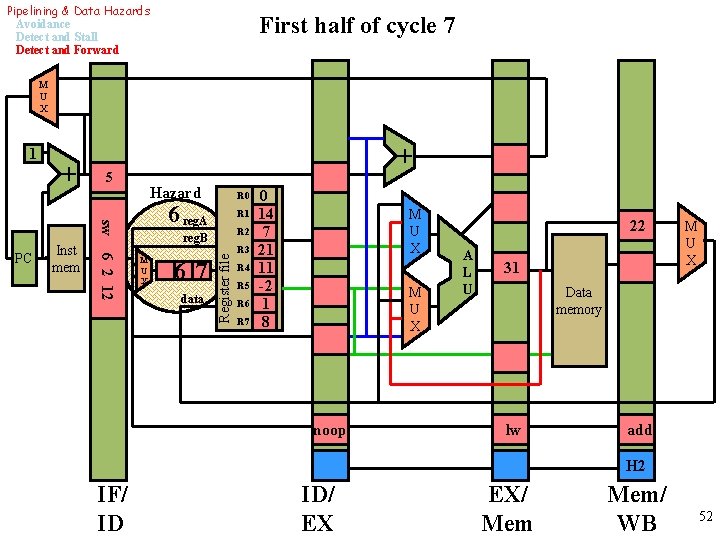
Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 7 M U X + + 5 Hazard 6 reg. A sw Inst mem 6 2 12 PC R 0 R 1 R 2 reg. B M U X 67 data Register file 1 R 3 R 4 R 5 R 6 R 7 0 14 7 21 11 -2 1 8 M U X noop 22 A L U 31 M U X Data memory lw add H 2 IF/ ID ID/ EX EX/ Mem/ WB 52

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of cycle 7 M U X 1 + 5 R 0 Inst mem M U X 6 data R 2 Register file PC R 1 reg. A reg. B R 3 R 4 R 5 R 6 R 7 0 14 7 21 11 -2 1 22 1 7 12 sw + M U X A L U 99 M U X Data memory noop lw H 3 IF/ ID ID/ EX EX/ Mem/ WB 53

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward First half of cycle 8 M U X 1 + 5 R 0 Inst mem M U X 6 data R 2 Register file PC R 1 reg. A reg. B R 3 R 4 R 5 R 6 R 7 0 14 7 21 11 -2 1 8 1 7 12 sw + 99 M U X M U 12 X A L U 99 M U X Data memory noop lw EX/ Mem/ WB H 3 IF/ ID ID/ EX 54

Pipelining & Data Hazards Avoidance Detect and Stall Detect and Forward End of cycle 8 M U X 1 + + R 0 Inst mem M U X data R 2 Register file PC R 1 reg. A reg. B R 3 R 4 R 5 R 6 R 7 0 14 7 21 11 -2 99 8 M U X A L U M U X 111 Data memory 7 sw noop H 3 IF/ ID ID/ EX EX/ Mem/ WB 55

Pipelining & Control Hazards Pipeline function for BEQ • Fetch: read instruction from memory • Decode: read source operands from reg • Execute: calculate target address and test for equality • Memory: Send target to PC if test is equal • Writeback: Nothing left to do 56

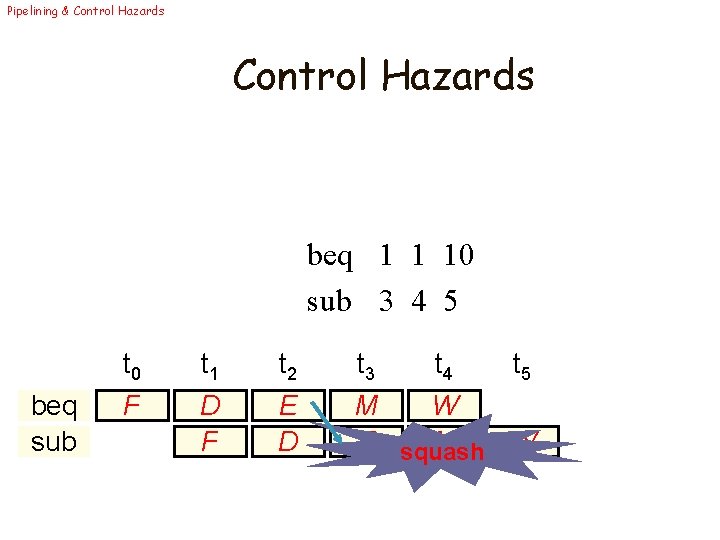
Pipelining & Control Hazards beq 1 1 10 sub 3 4 5 beq sub t 0 F t 1 D F t 2 E D t 3 t 4 t 5 M W E squash M W

Pipelining & Control Hazards Handling Control Hazards Avoidance (static) – No branches? – Convert branches to predication • Control dependence becomes data dependence Detect and Stall (dynamic) – Stop fetch until branch resolves Speculate and squash (dynamic) – Keep going past branch, throw away instructions if wrong

Pipelining & Control Hazards Avoidance Detect and Stall Speculate and Squash Avoidance Via Predication t 1 a, b t 1, PC+2 x x, #1 y n, d if (a == b) { x++; y = n / d; } sub jnz add div sub t 1 a, b add(!t 1) x x, #1 div(!t 1) y n, d sub t 1 a, b add t 2 x, #1 div t 3 n, d cmov(!t 1) x t 2 cmov(!t 1) y t 3

Pipelining & Control Hazards Avoidance Detect and Stall Speculate and Squash Handling Control Hazards: Detect & Stall Detection – In decode, check if opcode is branch or jump Stall – Hold next instruction in Fetch – Pass noop to Decode

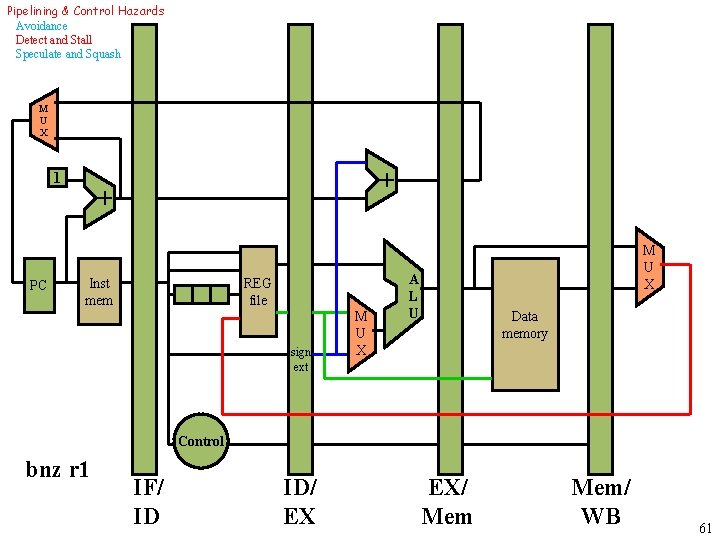
Pipelining & Control Hazards Avoidance Detect and Stall Speculate and Squash M U X 1 PC + + REG file Inst mem sign ext M U X A L U Data memory Control bnz r 1 IF/ ID ID/ EX EX/ Mem/ WB 61

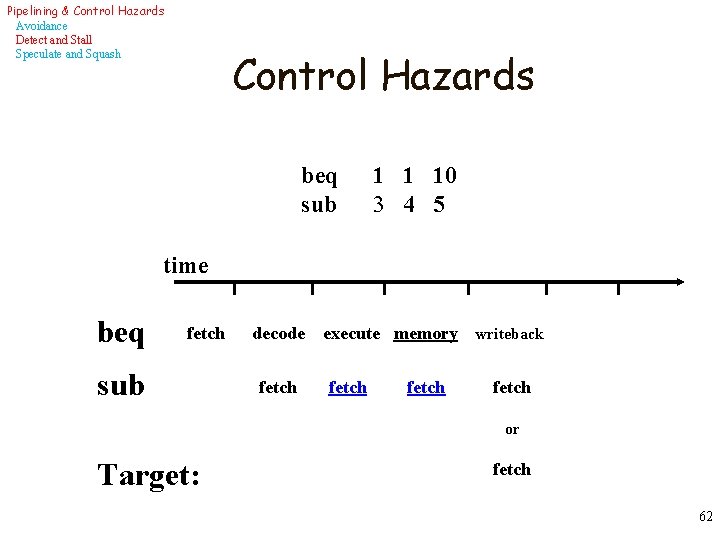
Pipelining & Control Hazards Avoidance Detect and Stall Speculate and Squash Control Hazards beq sub 1 1 10 3 4 5 time beq fetch sub decode fetch execute memory fetch writeback fetch or Target: fetch 62

Pipelining & Control Hazards Avoidance Detect and Stall Speculate and Squash Problems with Detect & Stall CPI increases on every branch Are these stalls necessary? Not always! – Branch is only taken half the time – Assume branch is NOT taken • Keep fetching, treat branch as noop • If wrong, make sure bad instructions don’t complete

Pipelining & Control Hazards Avoidance Detect and Stall Speculate and Squash Handling Control Hazards: Speculate & Squash Speculate “Not-Taken” – Assume branch is not taken Squash – Overwrite opcodes in Fetch, Decode, Execute with noop – Pass target to Fetch

Pipelining & Control Hazards Avoidance Detect and Stall Speculate and Squash M U X 1 + + equal REG file sign ext beq IF/ ID Data memory noop beq Control M U X A L U noop sub beq sub add nand Inst mem noop add PC M U X ID/ EX EX/ Mem/ WB

Pipelining & Control Hazards Avoidance Detect and Stall Speculate and Squash Problems with Speculate & Squash Always assumes branch is not taken Can we do better? Yes. – Predict branch direction and target! – Why possible? Program behavior repeats. More on branch prediction to come. . .

Pipelining & Control Hazards Branch Delay Slot (MIPS, SPARC) branch: next: target: t 0 t 1 t 2 t 3 t 4 t 5 F D F E M W Squash D E M F W - Instruction in delay slot executes even on taken branch: delay: target: i: j: F D F beq 1, 2, tgt add 3, 4, 5 E D F M E D W M E W M What can we put here? W

Improving pipeline performance • Add more stages • Widen pipeline 68/61

Improving pipeline performance Adding pipeline stages • Pipeline frontend – Fetch, Decode • Pipeline middle – Execute • Pipeline backend – Memory, Writeback 69

Improving pipeline performance Adding stages to fetch, decode • Delays hazard detection • No change in forwarding paths • No performance penalty with respect to data hazards 70

Improving pipeline performance Adding stages to execute • Check for structural hazards – ALU not pipelined – Multiple ALU ops completing at same time • Data hazards may cause delays – If multicycle op hasn't computed data before the dependent instruction is ready to execute • Performance penalty for each stall 71

Improving pipeline performance Adding stages to memory, writeback • Instructions ready to execute may need to wait longer for multi-cycle memory stage • Adds more pipeline registers – Thus more source registers to forward • More complex hazard detection • Wider muxes • More control bits to manage muxes 72

Improving pipeline performance Wider pipelines fetch decode execute mem WB More complex hazard detection • 2 X pipeline registers to forward from • 2 X more instructions to check • 2 X more destinations (muxes) • Need to worry about dependent instructions in the same stage 73

Making forwarding explicit • add r 1 r 2, EX/Mem ALU result – Include direct mux controls into the ISA – Hazard detection is now a compiler task – New micro-architecture leads to new ISA • Is this why this approach always seems to fail? (e. g. , simple VLIW, Motorola 88 k) – Can reduce some resources • Eliminates complex conflict checkers 74
 More more more i want more more more more we praise you
More more more i want more more more more we praise you More more more i want more more more more we praise you
More more more i want more more more more we praise you Eecs 470
Eecs 470 Eecs470
Eecs470 Umich eecs 470
Umich eecs 470 Non linear pipeline processor
Non linear pipeline processor Data hazards
Data hazards Scalar pipeline vs superscalar pipeline
Scalar pipeline vs superscalar pipeline 470 クラスルール
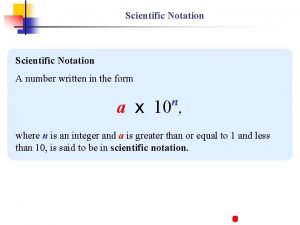
470 クラスルール 470 in scientific notation
470 in scientific notation Cs 470
Cs 470 Cs 470
Cs 470 Davies meyer construction
Davies meyer construction Cmpt 470 sfu
Cmpt 470 sfu 470 399
470 399 Mathisfun standard deviation
Mathisfun standard deviation 470 12
470 12 470/12
470/12 Log 470
Log 470 Human history becomes more and more a race
Human history becomes more and more a race Difference between further and furthermore
Difference between further and furthermore Tension in elastic string
Tension in elastic string Havering college of further and higher education
Havering college of further and higher education Definition of an extended metaphor
Definition of an extended metaphor Simplification of force and moment system
Simplification of force and moment system Further mechanics 1 unit test 1 momentum and impulse
Further mechanics 1 unit test 1 momentum and impulse 5 apples in a basket riddle
5 apples in a basket riddle The more you study the more you learn
The more you study the more you learn Aspire not to have more but to be more
Aspire not to have more but to be more Newtons 1law
Newtons 1law Knowing more remembering more
Knowing more remembering more The more i give to thee the more i have
The more i give to thee the more i have More choices more chances
More choices more chances Further study design
Further study design Abeam behind or further aft, astern or toward the stern.
Abeam behind or further aft, astern or toward the stern. Dr frost further kinematics
Dr frost further kinematics Not for distribution confidential
Not for distribution confidential This is to certify further
This is to certify further Further applications of integration
Further applications of integration Further applications of integration
Further applications of integration Time series further maths
Time series further maths English for further studies
English for further studies Further applications of integration
Further applications of integration Writing a letter asking for information
Writing a letter asking for information Sell or process further
Sell or process further Shropshireda
Shropshireda Further applications of integration
Further applications of integration Non comparative scaling
Non comparative scaling Further applications of integration
Further applications of integration Further applications of integration
Further applications of integration Further education support service
Further education support service For details please contact
For details please contact Slip trip fall hazards
Slip trip fall hazards Demolition hazards and control measures
Demolition hazards and control measures Excavation hazards and controls
Excavation hazards and controls Physical hazards
Physical hazards Understanding hazards and risks
Understanding hazards and risks Chapter review motion part a vocabulary review answer key
Chapter review motion part a vocabulary review answer key Ap gov review final exam review
Ap gov review final exam review Nader amin-salehi
Nader amin-salehi Inclusion criteria examples
Inclusion criteria examples Narrative review vs systematic review
Narrative review vs systematic review Multifunctional arithmetic pipeline
Multifunctional arithmetic pipeline Unifunction and multifunction pipeline
Unifunction and multifunction pipeline Pipeline and vector processing
Pipeline and vector processing Pipeline and vector processing
Pipeline and vector processing Pipeline and hazardous materials administration
Pipeline and hazardous materials administration Hazard of hand tools
Hazard of hand tools Pinotubo
Pinotubo What kind of hazard
What kind of hazard Drivers ed signs
Drivers ed signs Example of biological hazard
Example of biological hazard Radiation hazards
Radiation hazards What is physical hazards
What is physical hazards Mobile scaffold accident
Mobile scaffold accident