EEC484584 Computer Networks Lecture 6 Wenbing Zhao wenbingieee

EEC-484/584 Computer Networks Lecture 6 Wenbing Zhao wenbing@ieee. org Fall Semester 2007 EEC-484/584: Computer Networks
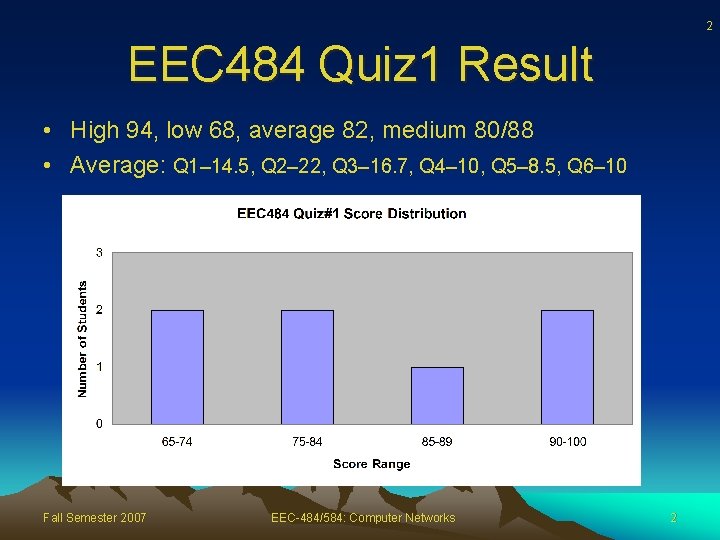
2 EEC 484 Quiz 1 Result • High 94, low 68, average 82, medium 80/88 • Average: Q 1– 14. 5, Q 2– 22, Q 3– 16. 7, Q 4– 10, Q 5– 8. 5, Q 6– 10 Fall Semester 2007 EEC-484/584: Computer Networks 2
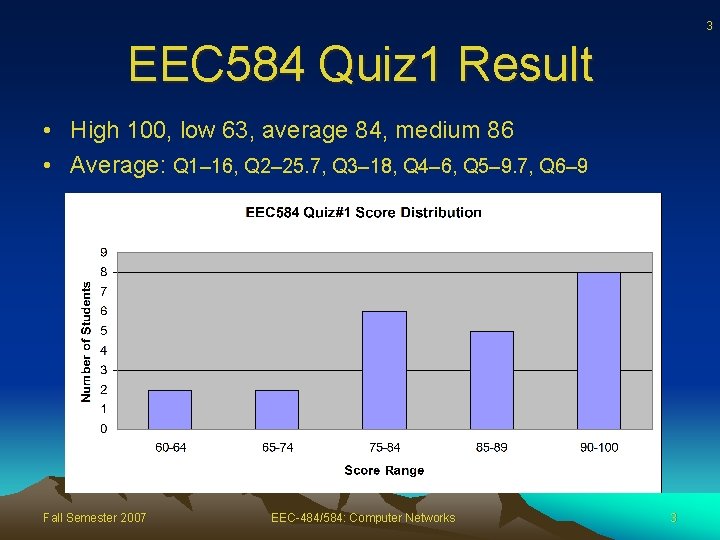
3 EEC 584 Quiz 1 Result • High 100, low 63, average 84, medium 86 • Average: Q 1– 16, Q 2– 25. 7, Q 3– 18, Q 4– 6, Q 5– 9. 7, Q 6– 9 Fall Semester 2007 EEC-484/584: Computer Networks 3
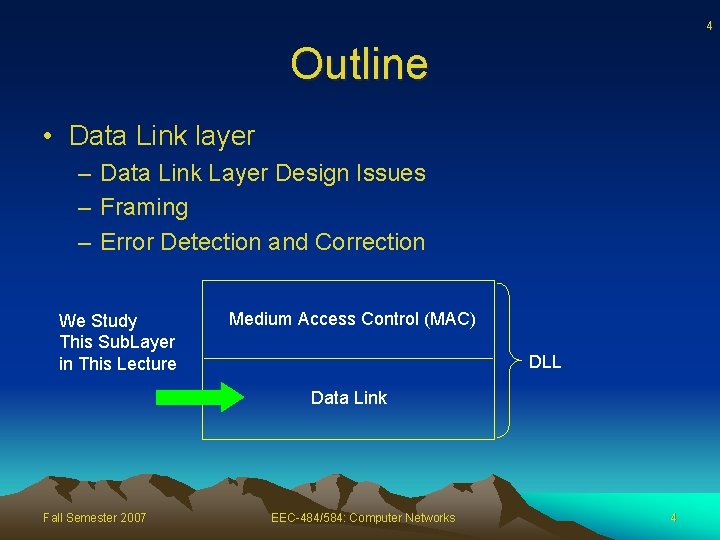
4 Outline • Data Link layer – Data Link Layer Design Issues – Framing – Error Detection and Correction We Study This Sub. Layer in This Lecture Medium Access Control (MAC) DLL Data Link Fall Semester 2007 EEC-484/584: Computer Networks 4
5 Data Link Layer Design Issues • Services Provided to the Network Layer – Point-to-point, source-to-destination • Framing – Physical bit stream divided up into frames • Error Control – Acknowledgements (acks), retransmission, duplicate suppression • Flow Control – Throttle sender so sends no faster than receiver can receive them Fall Semester 2007 EEC-484/584: Computer Networks 5
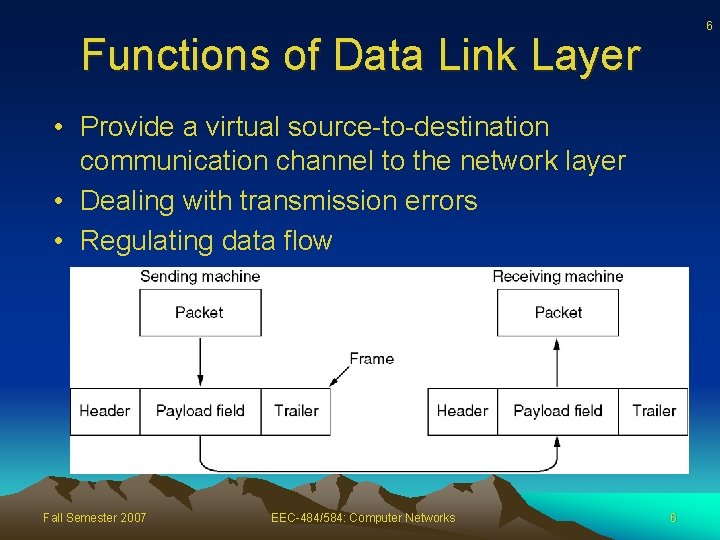
6 Functions of Data Link Layer • Provide a virtual source-to-destination communication channel to the network layer • Dealing with transmission errors • Regulating data flow Fall Semester 2007 EEC-484/584: Computer Networks 6
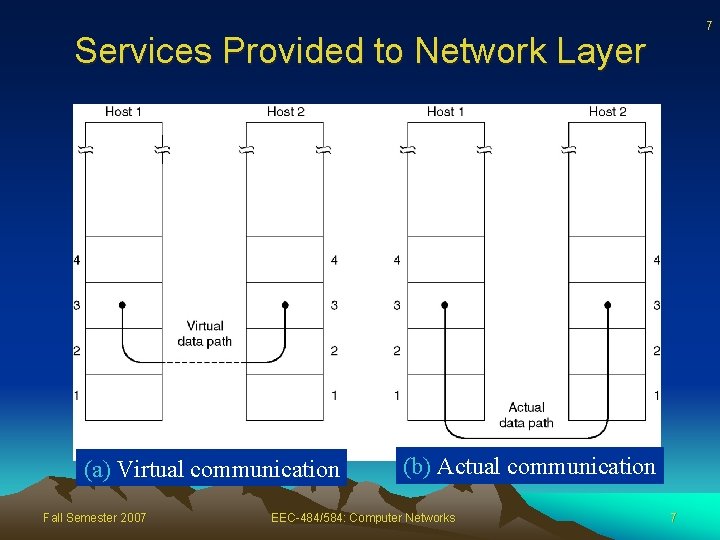
7 Services Provided to Network Layer (a) Virtual communication Fall Semester 2007 (b) Actual communication EEC-484/584: Computer Networks 7
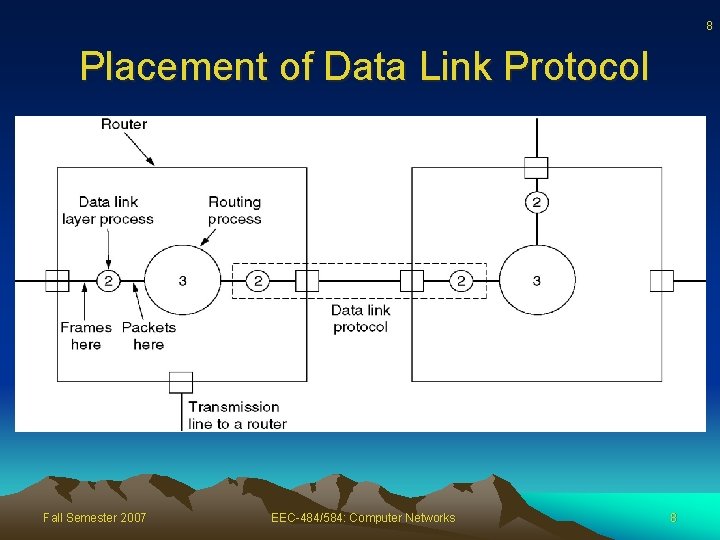
8 Placement of Data Link Protocol Fall Semester 2007 EEC-484/584: Computer Networks 8
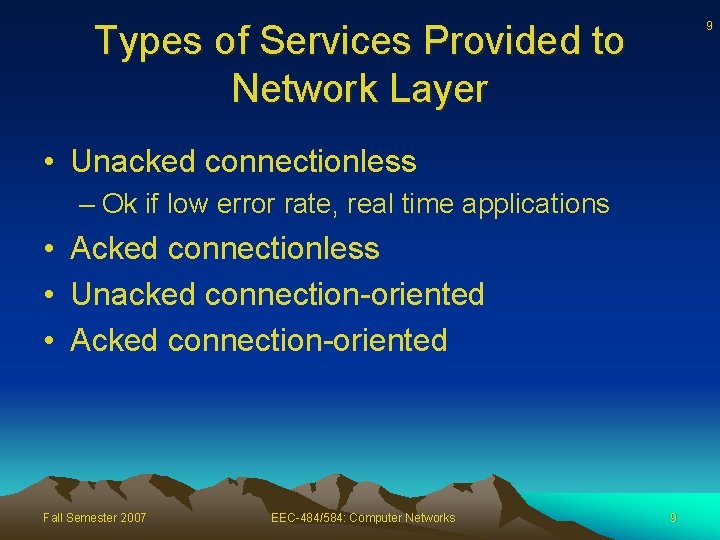
Types of Services Provided to Network Layer 9 • Unacked connectionless – Ok if low error rate, real time applications • Acked connectionless • Unacked connection-oriented • Acked connection-oriented Fall Semester 2007 EEC-484/584: Computer Networks 9
10 Framing • DL layer divides physical bit stream into frames • Checksum computed by source included in frame • Checksum recomputed by destination and checked against checksum included in the frame – Discard/recover bad frame, notify source Fall Semester 2007 EEC-484/584: Computer Networks 10
11 How Does DL Layer Form Frames? • • • Insert time gaps between frames: too risky Character count Flag bytes with byte stuffing Starting and ending flags, with bit stuffing Physical layer coding violations – Example: encode 1 bit with 2 bits • 1 => 10 • 0 => 01 • Can use 00 or 11 to delimit frames Fall Semester 2007 EEC-484/584: Computer Networks 11
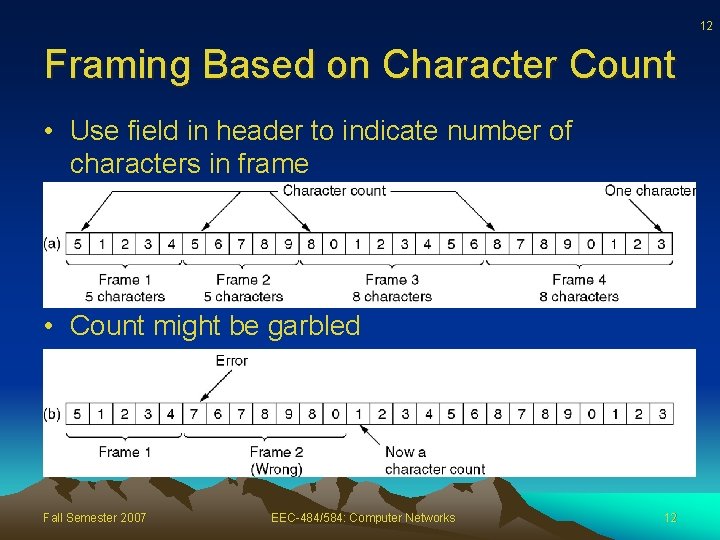
12 Framing Based on Character Count • Use field in header to indicate number of characters in frame • Count might be garbled Fall Semester 2007 EEC-484/584: Computer Networks 12
13 Framing Based on Byte Stuffing • Each frame starts and ends with a special flag byte – Problem: flag byte might appear in data – Solution: • Source inserts ESC (DL escape) before each flag byte; ESC before each ESC • Destination removes inserted ESC bytes • Disadvantage: depends on 8 -bits characters in ASCII Fall Semester 2007 EEC-484/584: Computer Networks 13
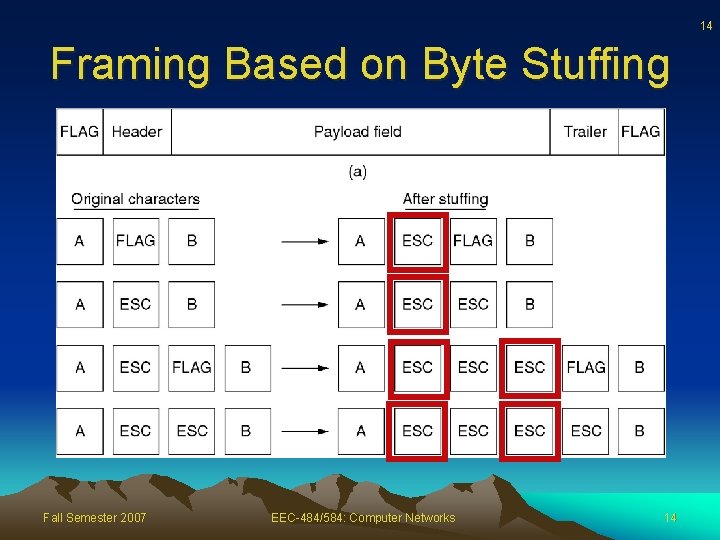
14 Framing Based on Byte Stuffing Fall Semester 2007 EEC-484/584: Computer Networks 14

15 Framing Based on Bit Stuffing • Each frame begins and ends with special bit patterns, 01111110 (in fact, a flag byte) • When source’s data contains 11111, stuff 0 • When destination receives 111110, deletes 0 • Advantages: – Allows arbitrary number of bits per frame – Allows arbitrary number of bits per character Fall Semester 2007 EEC-484/584: Computer Networks 15
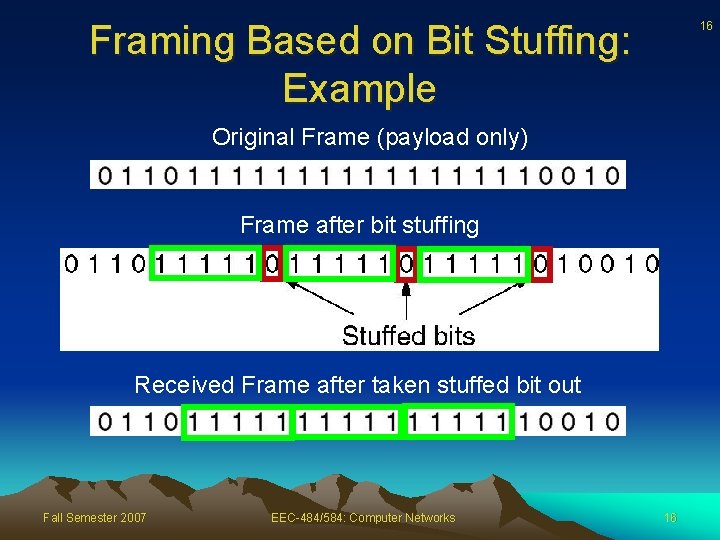
Framing Based on Bit Stuffing: Example 16 Original Frame (payload only) Frame after bit stuffing Received Frame after taken stuffed bit out Fall Semester 2007 EEC-484/584: Computer Networks 16
17 Error Detection and Correction • Causes of errors – Transmission errors on phone lines due to thermal noise – Data transmission errors due to impulse noise – Signals are separated, distorted, recombined – Crosstalk between physically adjacent wires – Compression and decompression – Receiver out of synch with sender • Errors usually occur in bursts Fall Semester 2007 EEC-484/584: Computer Networks 17
18 Error-Correcting Codes • n-bit codeword – an n-bit unit containing data and check bits – m bits of data, r bits redundant/check bits (n = m+r) • How to measure the differences between two codewords (num of different bits) – Using exclusive OR and counting number of 1 bits in the result Fall Semester 2007 EEC-484/584: Computer Networks 18

19 Error-Correcting Codes • Hamming distance – number of bit positions in which two codewords differ • If two codewords are a Hamming distance d apart, it will require d single-bit errors to convert one into the other Fall Semester 2007 EEC-484/584: Computer Networks 19

20 Error-Correcting Codes • Complete code – Complete list of all legal codewords: 2 m possible data messages – Recall that there are m bits of data • Hamming distance of the complete code – Find two codewords whose Hamming distance is minimum Fall Semester 2007 EEC-484/584: Computer Networks 20

21 Error-Detection Codes • A distance d+1 code can detect up to d errors, why? – If there are d+1 errors, one valid codeword might be turned into another valid codeword – ≤ d errors will change a valid codeword into an illegal codeword can be detected! Fall Semester 2007 EEC-484/584: Computer Networks 21

22 Error-Correcting Codes • To correct d errors, need a distance 2 d+1 code – Legal codewords are so far part that even with d changes, original codeword is still closer than any other codeword, so it can be uniquely determined Fall Semester 2007 EEC-484/584: Computer Networks 22
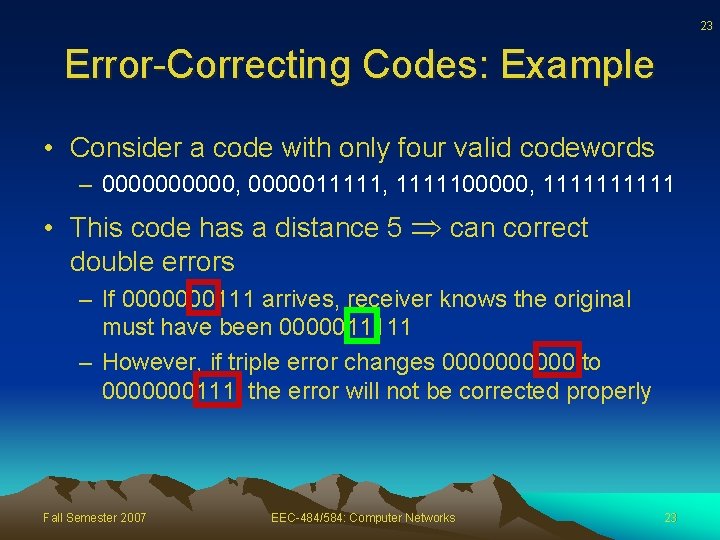
23 Error-Correcting Codes: Example • Consider a code with only four valid codewords – 00000, 0000011111, 1111100000, 11111 • This code has a distance 5 can correct double errors – If 0000000111 arrives, receiver knows the original must have been 0000011111 – However, if triple error changes 00000 to 0000000111, the error will not be corrected properly Fall Semester 2007 EEC-484/584: Computer Networks 23

24 Parity Bit • Parity bit – a single bit is appended to the data • Parity bit is chosen so that number of 1 bits in the codeword is even or odd • Example: Given 1011010 – With even parity 10110100 – With odd parity 10110101 • A code with a single parity bit has a distance 2 – Since any single-bit error produces a codeword with wrong parity can be used to detect single bit errors Fall Semester 2007 EEC-484/584: Computer Networks 24
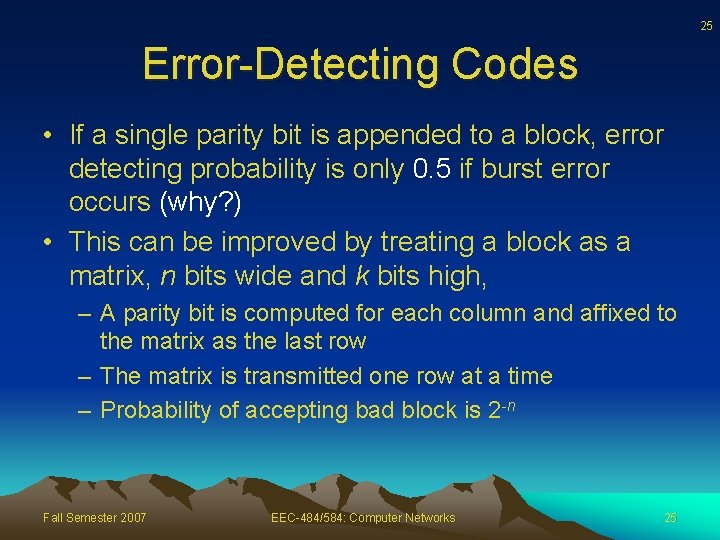
25 Error-Detecting Codes • If a single parity bit is appended to a block, error detecting probability is only 0. 5 if burst error occurs (why? ) • This can be improved by treating a block as a matrix, n bits wide and k bits high, – A parity bit is computed for each column and affixed to the matrix as the last row – The matrix is transmitted one row at a time – Probability of accepting bad block is 2 -n Fall Semester 2007 EEC-484/584: Computer Networks 25
26 Error-Detecting Codes: CRC • Polynomial code, also known as CRC (Cyclic Redundant Code) • Treat bit string as polynomial with 0 and 1 coefficients • m-bit frame: M(x) = bm-1 xm-1 + … + b 0 • E. g. : 11011010 => M(x) = x 7 + x 6 + x 4 + x 3 + x 1 • Use modulo 2 arithmetic – No carries or borrows: XOR • The degree of a polynomial is the maximum of the degrees of all terms in the polynomial Fall Semester 2007 EEC-484/584: Computer Networks 26
27 Cyclic Redundant Code • Sender and receiver agree on generator polynomial G(x) (High & low order bits must be 1) • For a frame with m bits corresponding to M(x), m > deg G(x) = r • Append checksum to end of frame so polynomial T(x) corresponding to checksummed frame is divisible by G(x) • When receiver gets checksummed frame, divides T(x) by G(x) • If remainder R(x) != 0, then transmission error Fall Semester 2007 EEC-484/584: Computer Networks 27
28 Algorithm to Compute CRC Checksum • Let m = deg M(x), r = deg G(x) • Append r 0 bits to lower-order end of frame: xr. M(x) • Divide bit string corresponding to xr. M(x) by bit string corresponding to G(x) • Subtract remainder R(x) from bit string corresponding to xr. M(x), result is checksummed frame. Let T(x) be its polynomial – xr. M(x) = Q(x)G(x) + R(x) – xr. M(x) – R(x) = Q(x)G(x) = T(x) Fall Semester 2007 EEC-484/584: Computer Networks 28
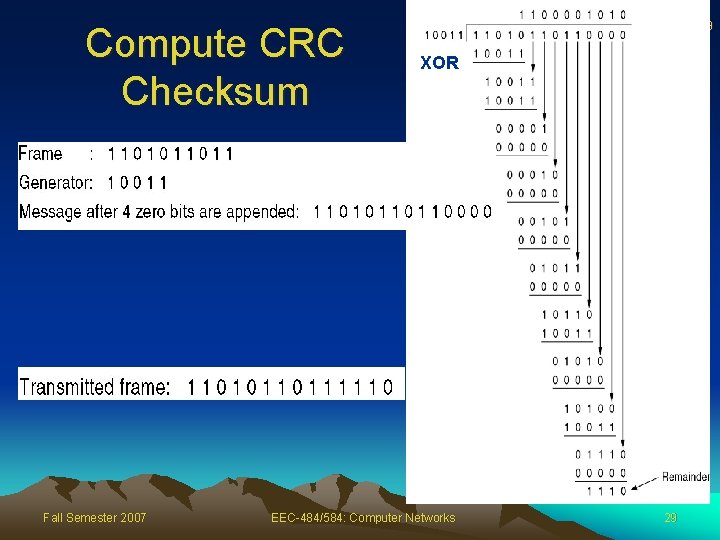
Compute CRC Checksum Fall Semester 2007 29 XOR EEC-484/584: Computer Networks 29
30 International Standard Polynomials • CRC-12 G(x) = x 12 + x 11 + x 3 + x 2 + x 1 + 1 – Used for 6 -bit characters • CRC-16 G(x) = x 16 + x 15 + x 2 + 1 CRC-CCITT G(x) = x 16 + x 12 + x 5 + 1 – Used for 8 -bit characters • CRC-32 G(x) = x 32 + x 26 + x 23 + x 22 + x 16 + x 11 + x 10 + x 8 + x 7 + x 5 + x 4 + x 2 + x 1 + 1 – Used in IEEE 802 – Detects all bursts of length 32 or less and all bursts affecting an odd number of bits Fall Semester 2007 EEC-484/584: Computer Networks 30

31 Exercise • Q 1. The following character encoding is used in a data link protocol: A: 01000111; B: 11100011; FLAG: 01111110; ESC: 11100000 Show the bit sequence transmitted (in binary) for the fourcharacter frame: A B ESC FLAG when each of the following framing methods are used: (a) Character count. (b) Flag bytes with byte stuffing. (c) Starting and ending flag bytes, with bit stuffing Fall Semester 2007 EEC-484/584: Computer Networks 31

32 Exercise • Q 2. The following data fragment occurs in the middle of a data stream for which the bytestuffing algorithm described in the text is used: A B ESC C ESC FLAG D. What is the output after stuffing? Fall Semester 2007 EEC-484/584: Computer Networks 32

33 Exercise • Q 3. A bit string, 01111101111110, needs to be transmitted at the data link layer. What is the string actually transmitted after bit stuffing? Fall Semester 2007 EEC-484/584: Computer Networks 33
34 Exercise • Q 4. One of your classmates, Scrooge, has pointed out that it is wasteful to end each frame with a flag byte and then begin the next one with a second flag byte. One flag byte could do the job as well, and a byte saved is a byte earned. Do you agree? Fall Semester 2007 EEC-484/584: Computer Networks 34

35 Exercise • Q 5. To provide more reliability than a single parity bit can give, an error-detecting coding scheme uses one parity bit for checking all the odd-numbered bits and a second parity bit for all the even-numbered bits. What is the Hamming distance of this code? Fall Semester 2007 EEC-484/584: Computer Networks 35

36 Exercise • Q 6. A bit stream 10011101 is transmitted using the standard CRC method described in the text. The generator polynomial is x 3 + 1. Show the actual bit string transmitted. Suppose third bit from the left is inverted during transmission. Show that this error is detected at the receiver's end. Fall Semester 2007 EEC-484/584: Computer Networks 36
- Slides: 36