EDetective HTTPSSSL Interception MITM Proxy Decision Group www



- Slides: 12

E-Detective HTTPS/SSL Interception – MITM & Proxy Decision Group www. edecision 4 u. com

Introduction to HTTPS/SSL Interception Appliance (Software + Hardware) User can opt to purchase only software from us and use their own hardware/server. v Intercept HTTPS/SSL traffic (connection sessions) by MITM attack or by Proxy setup. v HTTPS/SSL Interception by MITM mode is carried out utilizing both DNS and ARP attacks. v HTTPS web pages on targeted user can be decrypted, decoded and reconstructed. Username and password can also be obtained for Web Login. v Apply to standard HTTPS/SSL traffic without additional security. v HTTPS/SSL Interception by Proxy mode required the target users’ Web Browser to be pre-configured to use the Proxy service. Solution for: Lawful Enforcement Agencies (Police Intelligence, Military Intelligence, National Security, Counter Terrorism, etc) and corporate organizations.

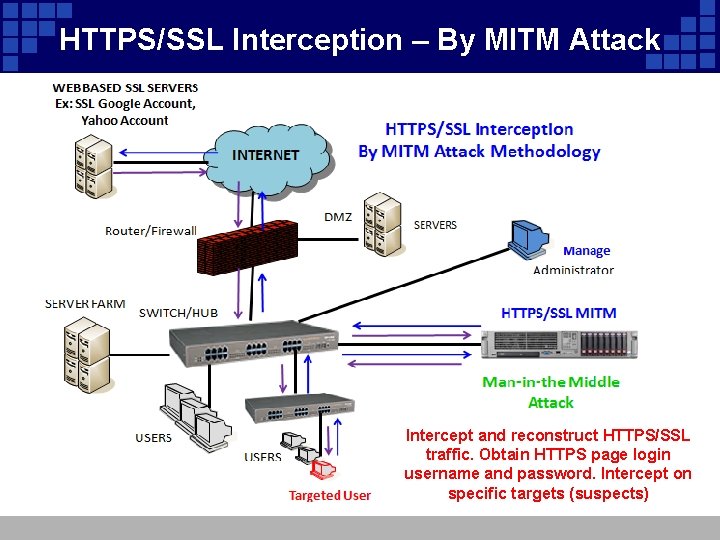
HTTPS/SSL Interception – By MITM Attack Intercept and reconstruct HTTPS/SSL traffic. Obtain HTTPS page login username and password. Intercept on specific targets (suspects)

HTTPS/SSL Interception – By MITM Attack v HTTPS/SSL Interception by MITM mode is carried out utilizing both DNS and ARP attacks. v HTTPS web pages on targeted user can be decrypted, decoded and reconstructed. Username and password can also be obtained for Web Login. v Target User (Suspect) IP Address must be known or pre-configured in the setup of HTTPS/SSL Interception system. v Target Website Links (URLs) must also be pre-configured. v Concurrently attack up to 5 users (Optional for more users). v Apply to standard HTTPS/SSL traffic without additional security. To view encrypted content, a key is a needed

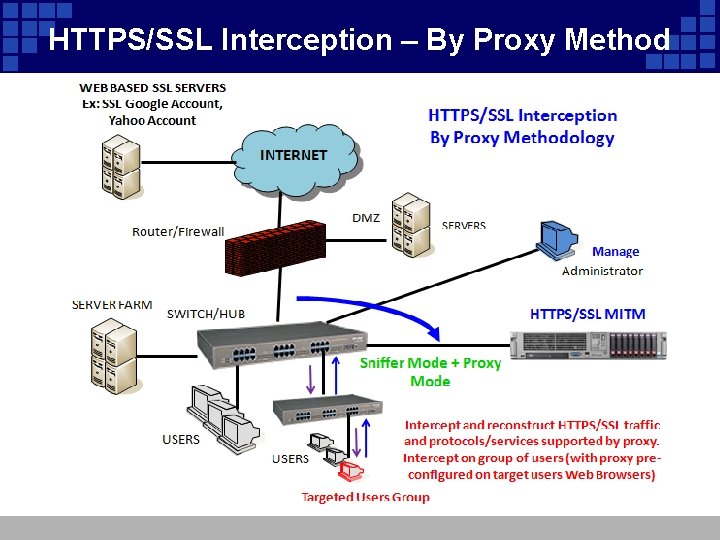
HTTPS/SSL Interception – By Proxy Method

HTTPS/SSL Interception – By Proxy Method v HTTPS/SSL Interception by Proxy implementation. v Proxy pre-configured on the targeted user(s) ‘ Web Browser is required. v HTTPS/SSL Interception by Proxy implementation can supports other protocols capturing and reconstruction besides HTTPS/SSL traffic. v Some supported protocols are: Webmail (Yahoo Mail, Gmail, Hotmail etc. ), IM (Yahoo, MSN, ICQ, IRC, QQ, Web MSN, Web Yahoo etc. ), HTTP Web Browsing, P 2 P and Online Games). v Can be implemented to a group of users (more than 100 concurrent interception) v HTTPS/SSL decryption only apply to standard HTTPS/SSL traffic without additional security. To view encrypted content, a key is a needed

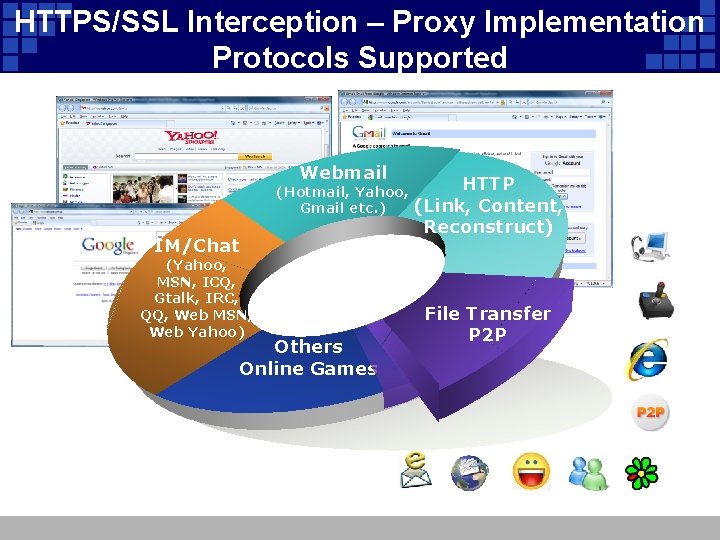
HTTPS/SSL Interception – Proxy Implementation Protocols Supported Webmail HTTP (Hotmail, Yahoo, (Link, Content, Gmail etc. ) IM/Chat (Yahoo, MSN, ICQ, Gtalk, IRC, QQ, Web MSN, Web Yahoo) Others Online Games Reconstruct) File Transfer P 2 P

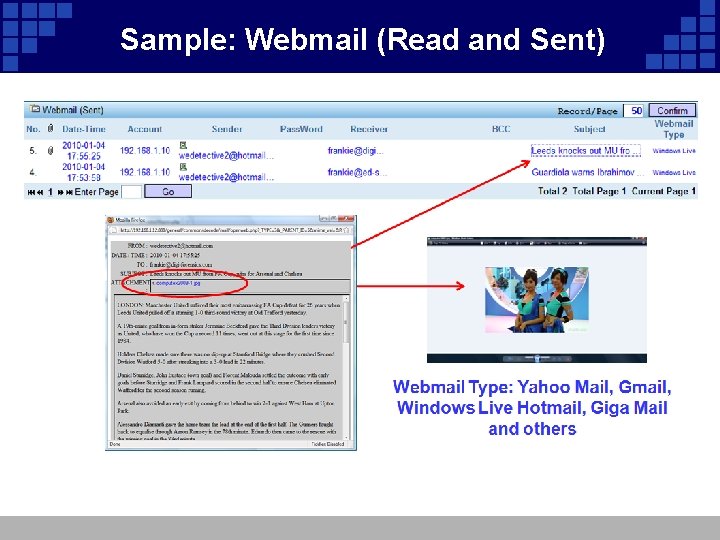
Sample: Webmail (Read and Sent)

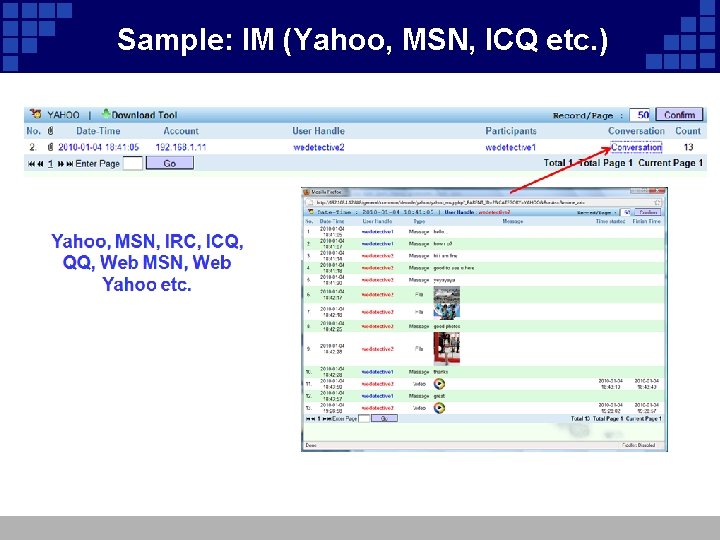
Sample: IM (Yahoo, MSN, ICQ etc. )

Sample: HTTP Link and HTTP Content

References – Implementation Sites and Customers v v v Criminal Investigation Bureau The Bureau of Investigation Ministry of Justice National Security Agency (Bureau) in various countries Intelligence Agency in various countries Ministry of Defense in various countries Counter/Anti Terrorism Department National Police, Royal Police in various countries Government Ministries in various countries Federal Investigation Bureau in various countries Telco/Internet Service Provider in various countries Banking and Finance organizations in various countries Others Notes: Due to confidentiality of this information, the exact name and countries of the various organizations cannot be revealed.

Decision Group For more information about HTTPS/SSL Interception system, please contact decision@decision. com. tw. Product demonstrations can be arranged.