EDetective Ethernet LAN Interception System with RealTime Content





- Slides: 37

E-Detective Ethernet LAN Interception System (with Real-Time Content Reconstruction) - 2010 Decision Group www. edecision 4 u. com

Introduction to E-Detective LAN Internet Monitoring, Data Retention, Data Leakage Protection & Network Forensics Analysis Solution for: v v v Organization Internet Monitoring/Network Behavior Recording Auditing and Record Keeping for Banking and Finance Industry Forensics Analysis and Investigation, Legal and Lawful Interception (LI) Mediation Platform & Tactic Server for Telco Operator Compliance Solution for: Sarbanes Oxley Act (SOX), HIPAA, GLBA, SEC etc. . . E-Detective Standard System Models and Series (Appliance based) User can also opt to purchase software license only from us and use their own hardware/server. FX-06 FX-30 N FX-100 FX-120

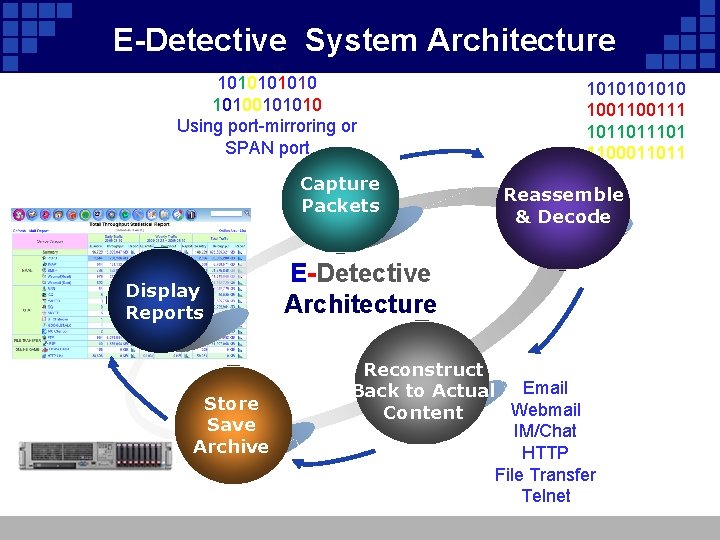
E-Detective System Architecture 1010100101010 Using port-mirroring or SPAN port Capture Packets Display Reports Store Save Archive 101010 100111 101101 1100011011 Reassemble & Decode E-Detective Architecture Reconstruct Email Back to Actual Webmail Content IM/Chat HTTP File Transfer Telnet

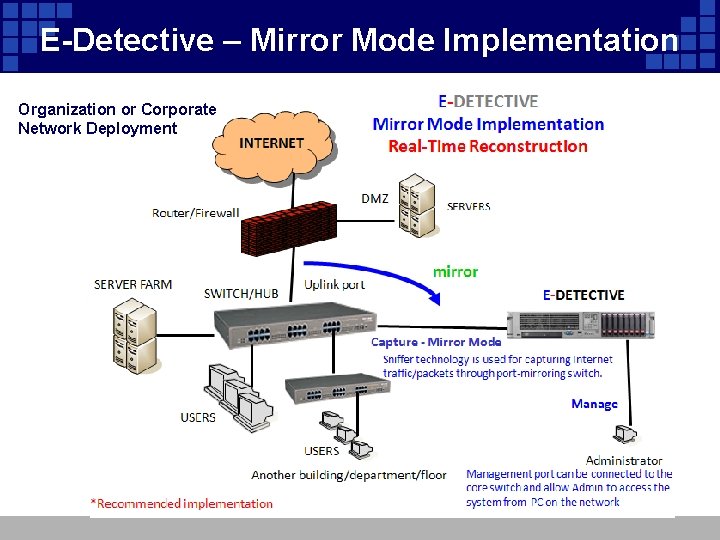
E-Detective – Mirror Mode Implementation Organization or Corporate Network Deployment

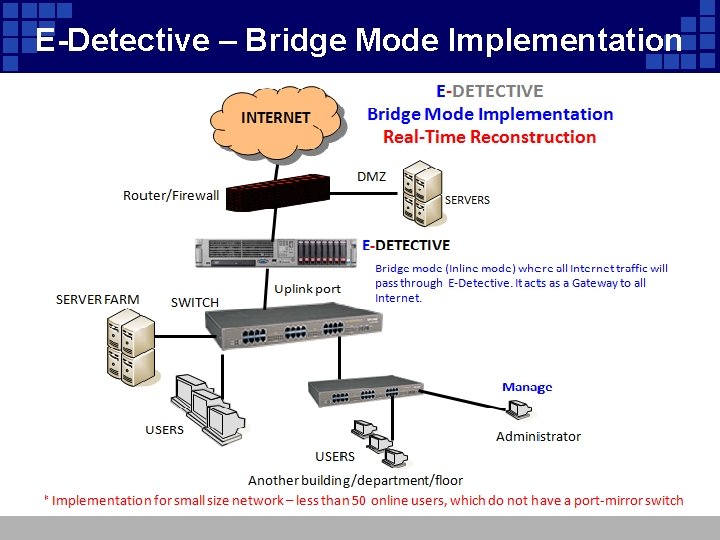
E-Detective – Bridge Mode Implementation

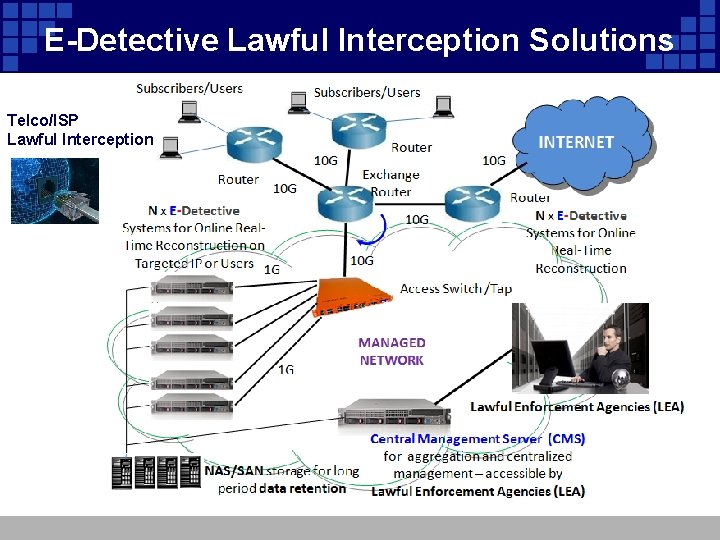
E-Detective Lawful Interception Solutions Telco/ISP Lawful Interception

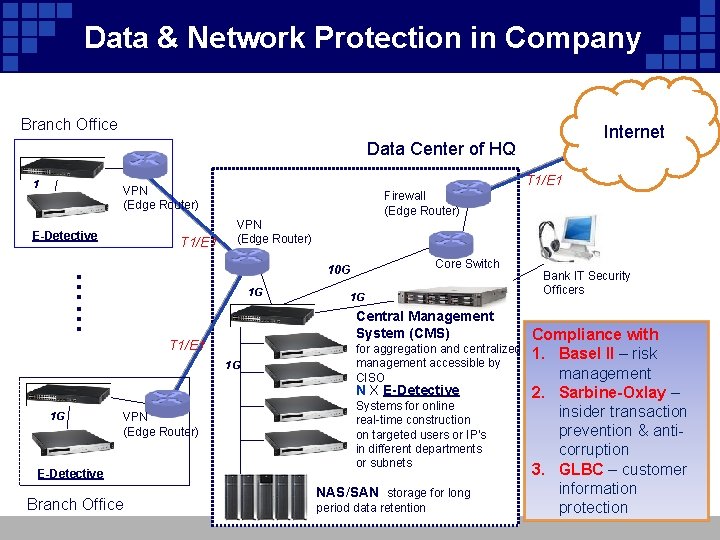
Data & Network Protection in Company Branch Office Internet Data Center of HQ 1 G T 1/E 1 VPN (Edge Router) E-Detective T 1/E 1 Firewall (Edge Router) VPN (Edge Router) Core Switch …… 10 G 1 G 1 G Central Management System (CMS) T 1/E 1 1 G for aggregation and centralized management accessible by CISO N X E-Detective 1 G VPN (Edge Router) E-Detective Branch Office Systems for online real-time construction on targeted users or IP’s in different departments or subnets NAS/SAN storage for long period data retention Bank IT Security Officers Compliance with 1. Basel II – risk management 2. Sarbine-Oxlay – insider transaction prevention & anticorruption 3. GLBC – customer information protection

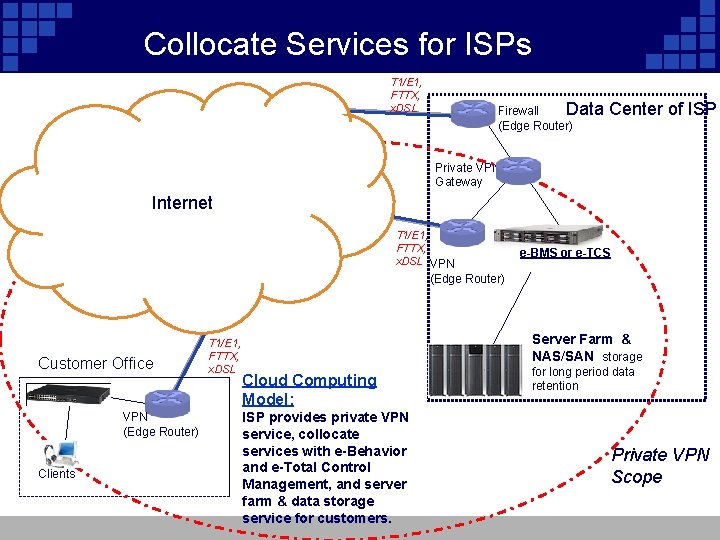
Collocate Services for ISPs T 1/E 1, FTTX, x. DSL Firewall Data (Edge Router) Center of ISP Private VPN Gateway Internet T 1/E 1, FTTX, x. DSL VPN e-BMS or e-TCS (Edge Router) Customer Office VPN (Edge Router) Clients T 1/E 1, FTTX, x. DSL Server Farm & NAS/SAN storage Cloud Computing Model: ISP provides private VPN service, collocate services with e-Behavior and e-Total Control Management, and server farm & data storage service for customers. for long period data retention Private VPN Scope

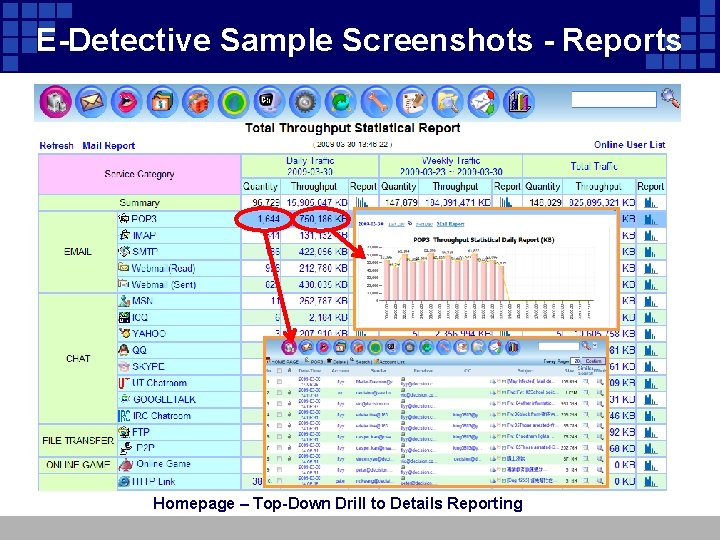
E-Detective Sample Screenshots - Reports Homepage – Top-Down Drill to Details Reporting

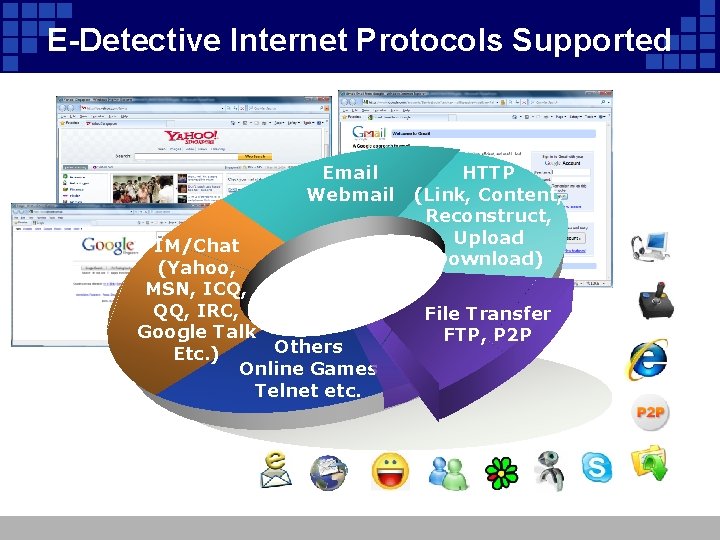
E-Detective Internet Protocols Supported Email Webmail IM/Chat (Yahoo, MSN, ICQ, QQ, IRC, Google Talk Others Etc. ) Online Games Telnet etc. HTTP (Link, Content, Reconstruct, Upload Download) File Transfer FTP, P 2 P

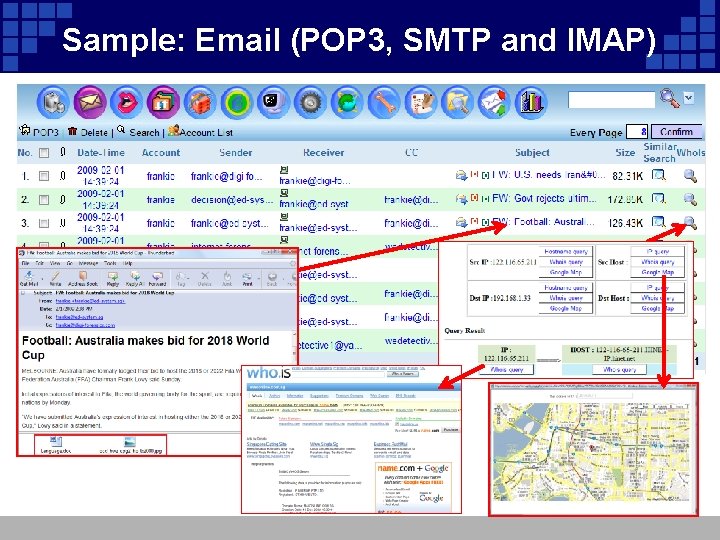
Sample: Email (POP 3, SMTP and IMAP)

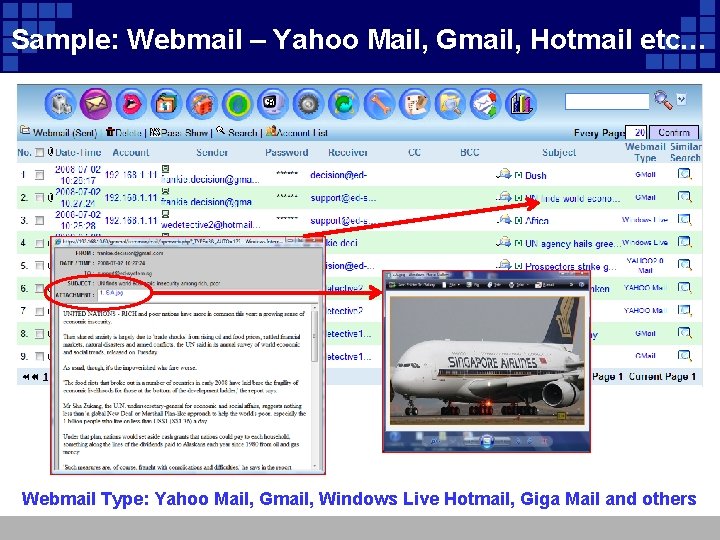
Sample: Webmail – Yahoo Mail, Gmail, Hotmail etc… Webmail Type: Yahoo Mail, Gmail, Windows Live Hotmail, Giga Mail and others

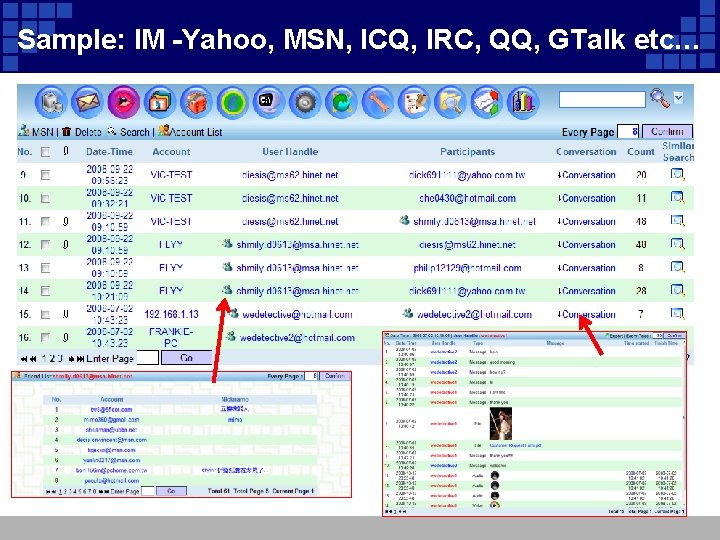
Sample: IM -Yahoo, MSN, ICQ, IRC, QQ, GTalk etc…

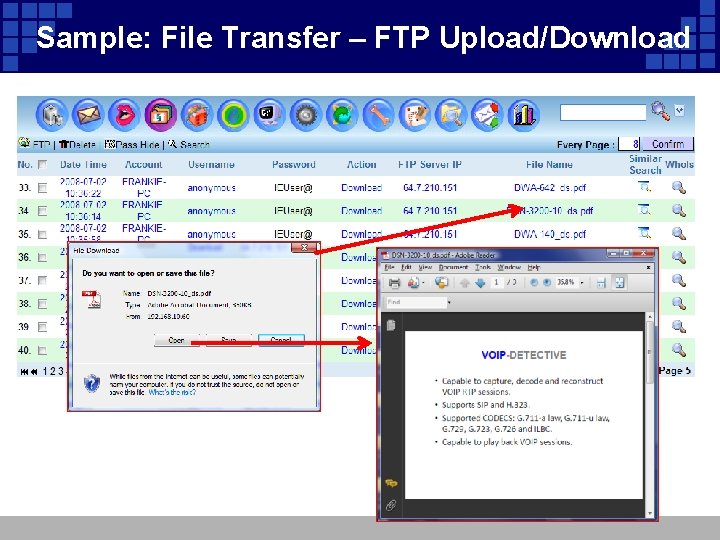
Sample: File Transfer – FTP Upload/Download

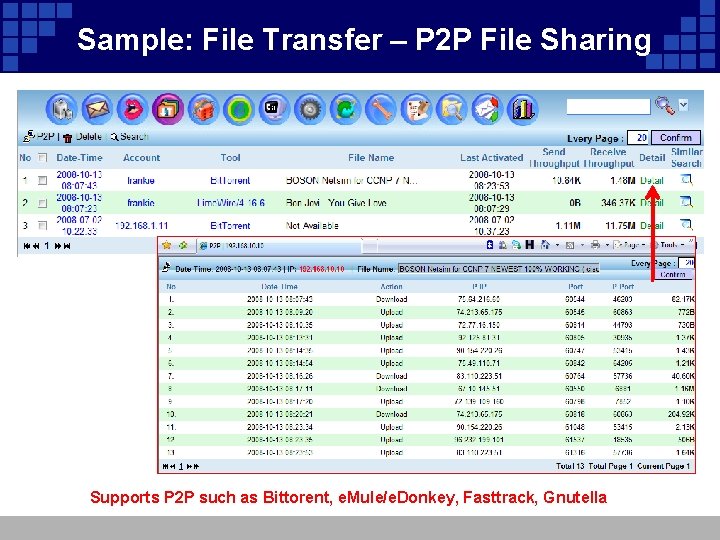
Sample: File Transfer – P 2 P File Sharing Supports P 2 P such as Bittorent, e. Mule/e. Donkey, Fasttrack, Gnutella

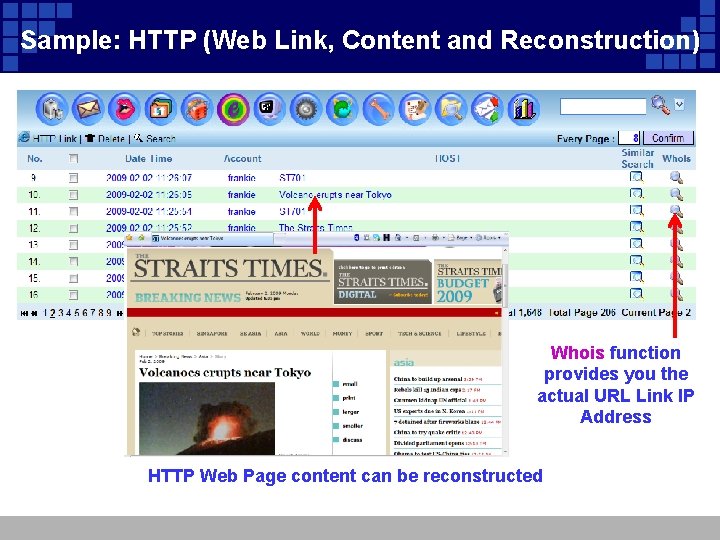
Sample: HTTP (Web Link, Content and Reconstruction) Whois function provides you the actual URL Link IP Address HTTP Web Page content can be reconstructed

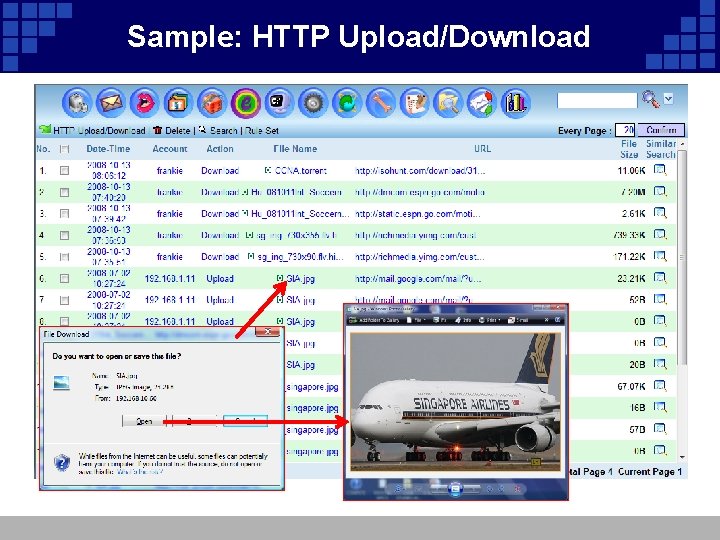
Sample: HTTP Upload/Download

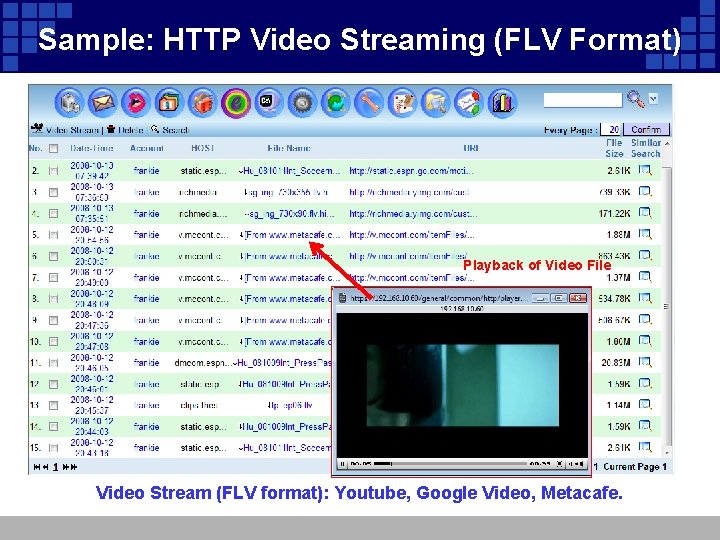
Sample: HTTP Video Streaming (FLV Format) Playback of Video File Video Stream (FLV format): Youtube, Google Video, Metacafe.

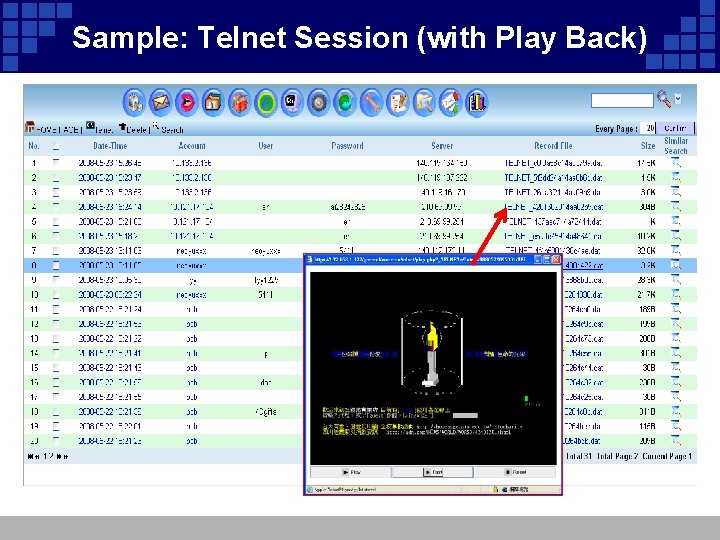
Sample: Telnet Session (with Play Back)

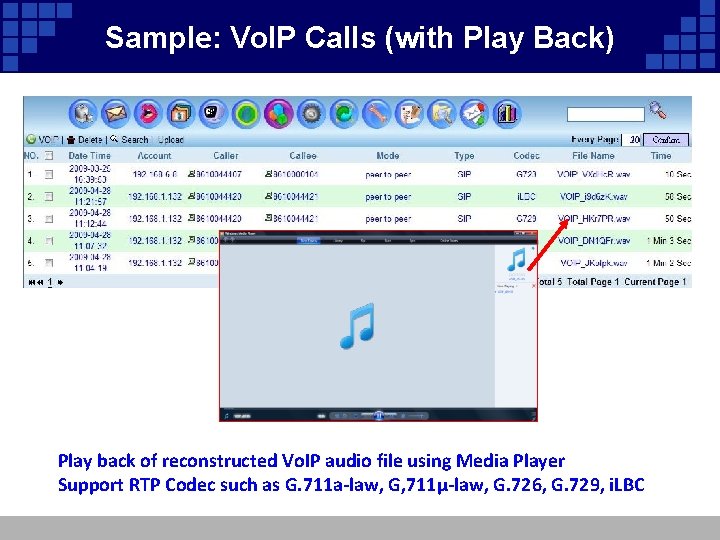
Sample: Vo. IP Calls (with Play Back) Play back of reconstructed Vo. IP audio file using Media Player Support RTP Codec such as G. 711 a-law, G, 711µ-law, G. 726, G. 729, i. LBC

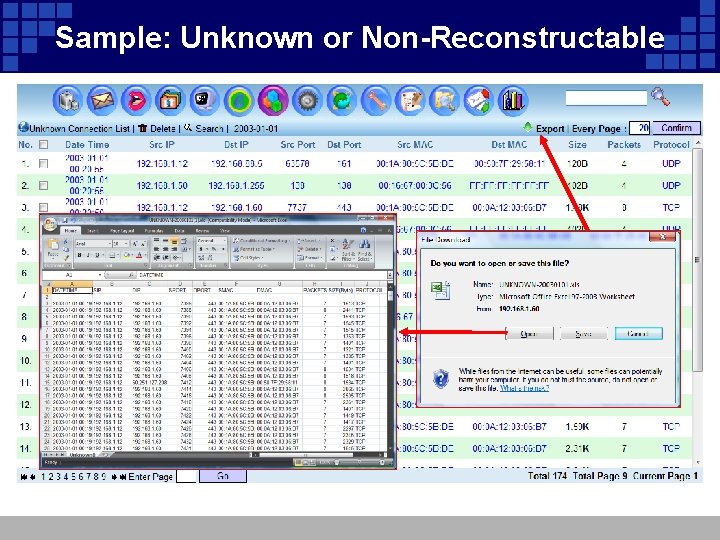
Sample: Unknown or Non-Reconstructable

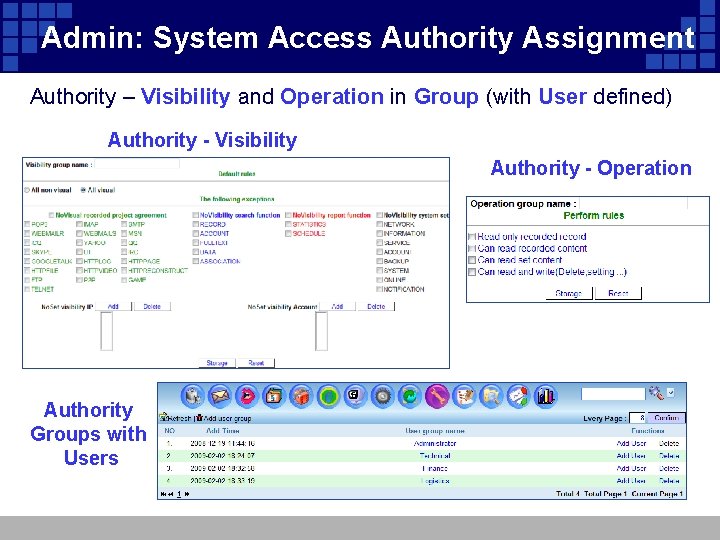
Admin: System Access Authority Assignment Authority – Visibility and Operation in Group (with User defined) Authority - Visibility Authority - Operation Authority Groups with Users

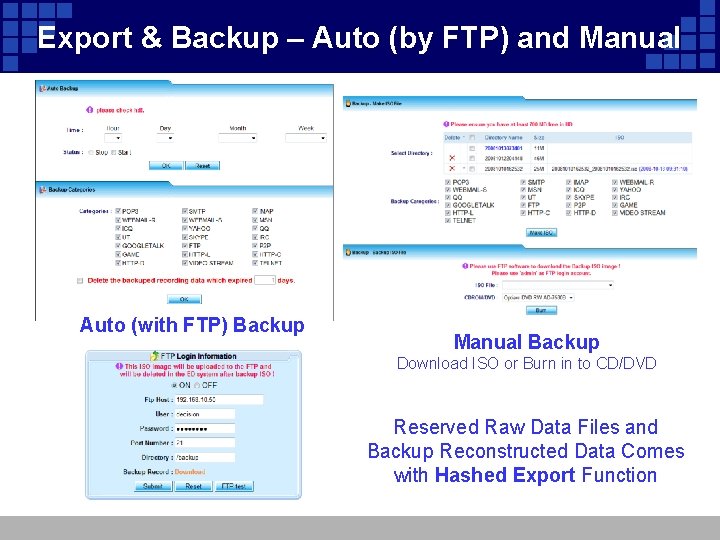
Export & Backup – Auto (by FTP) and Manual Auto (with FTP) Backup Manual Backup Download ISO or Burn in to CD/DVD Reserved Raw Data Files and Backup Reconstructed Data Comes with Hashed Export Function

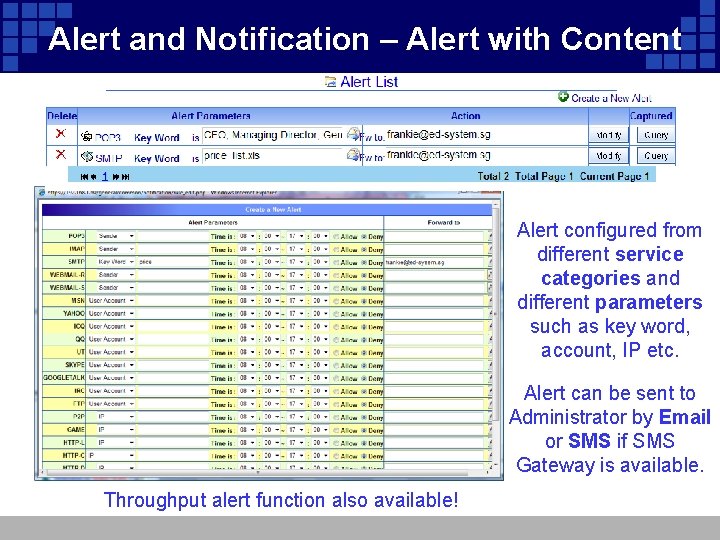
Alert and Notification – Alert with Content Alert configured from different service categories and different parameters such as key word, account, IP etc. Alert can be sent to Administrator by Email or SMS if SMS Gateway is available. Throughput alert function also available!

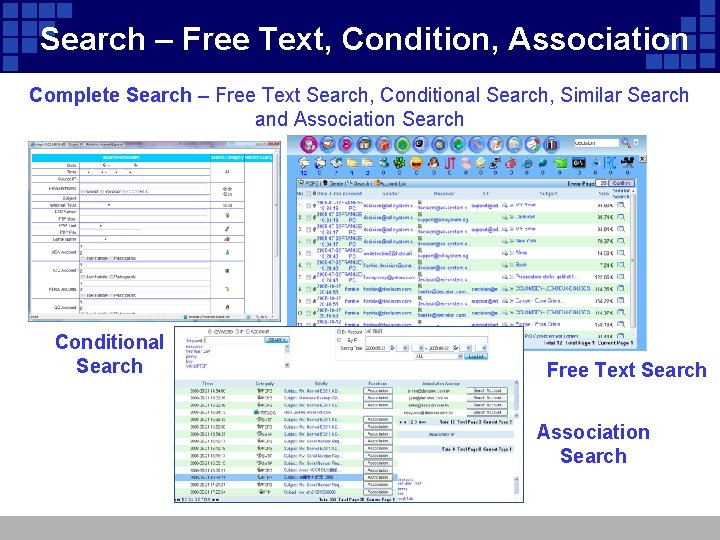
Search – Free Text, Condition, Association Complete Search – Free Text Search, Conditional Search, Similar Search and Association Search Conditional Search Free Text Search Association Search

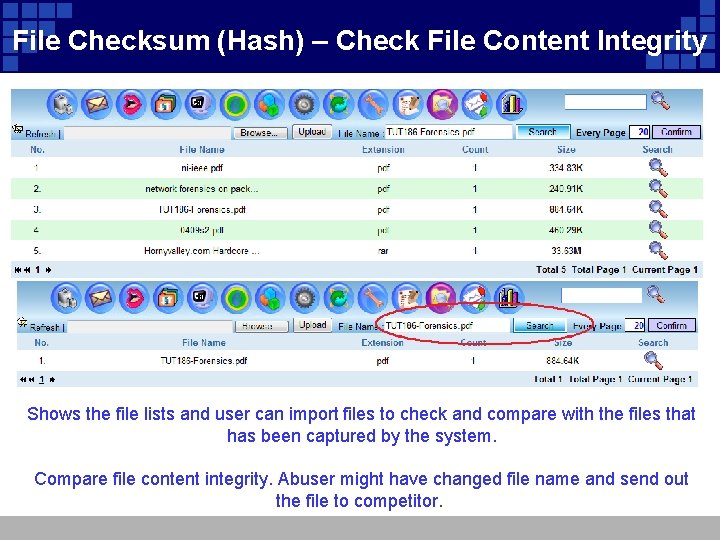
File Checksum (Hash) – Check File Content Integrity Shows the file lists and user can import files to check and compare with the files that has been captured by the system. Compare file content integrity. Abuser might have changed file name and send out the file to competitor.

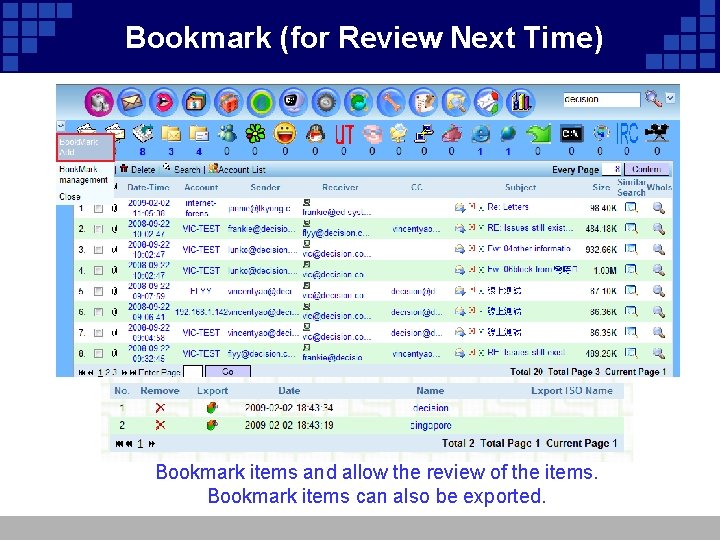
Bookmark (for Review Next Time) Bookmark items and allow the review of the items. Bookmark items can also be exported.

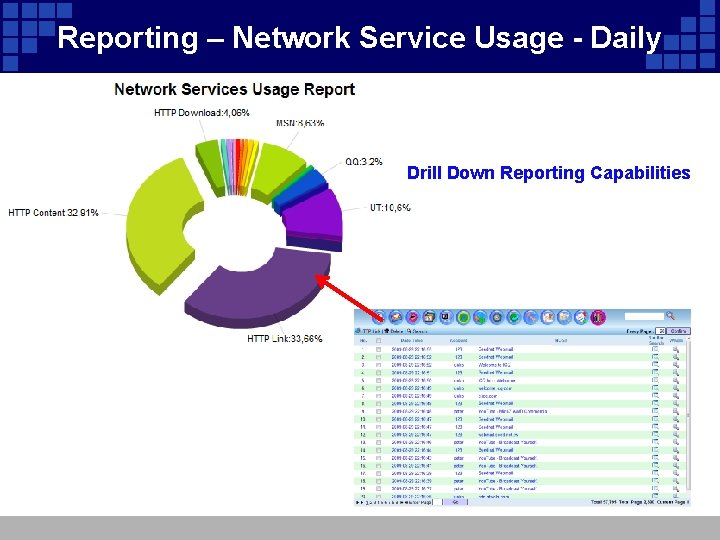
Reporting – Network Service Usage - Daily Drill Down Reporting Capabilities

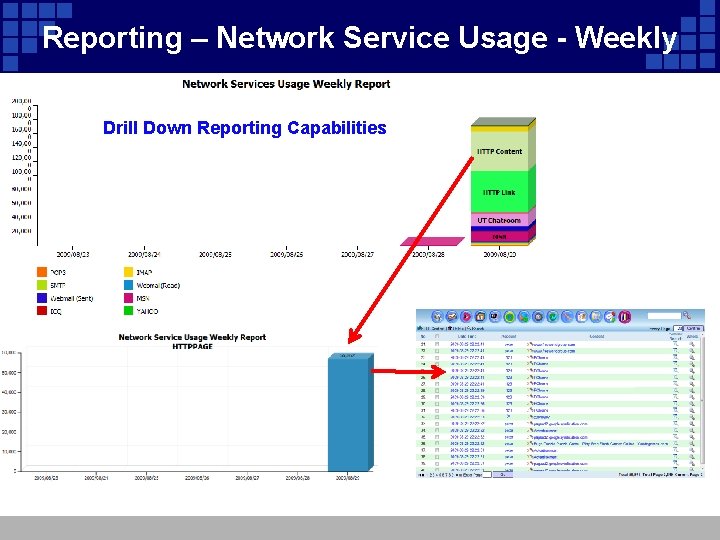
Reporting – Network Service Usage - Weekly Drill Down Reporting Capabilities

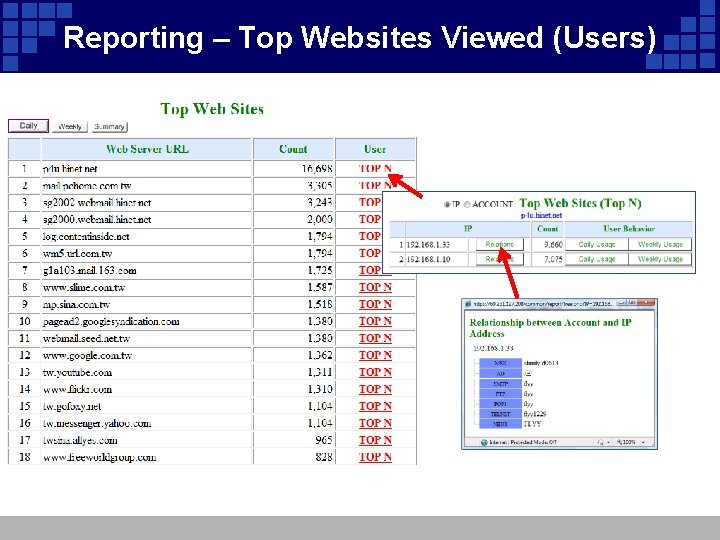
Reporting – Top Websites Viewed (Users)

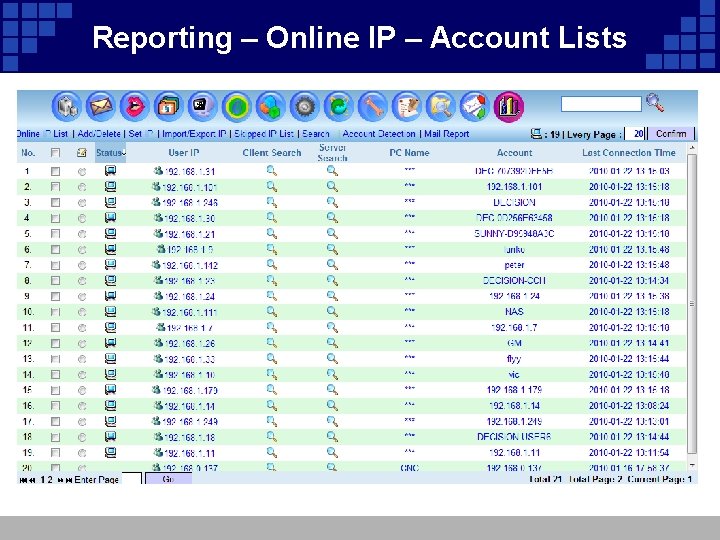
Reporting – Online IP – Account Lists

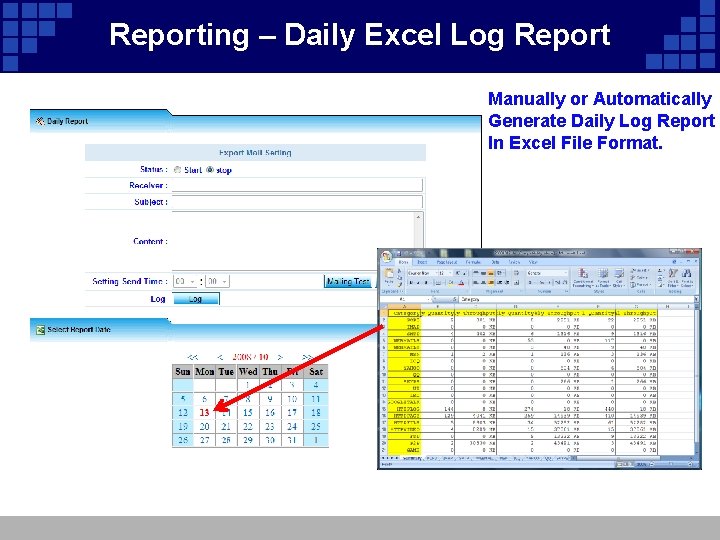
Reporting – Daily Excel Log Report Manually or Automatically Generate Daily Log Report In Excel File Format.

High Availability v 2 ways of high availability configuration based on customer requirement v Single and simple cluster configuration for small and mid-size network structure v Multiple and complex cluster configuration for large or ISP network structure with real-time performance v Site survey and customer requirement in advance Company Logo

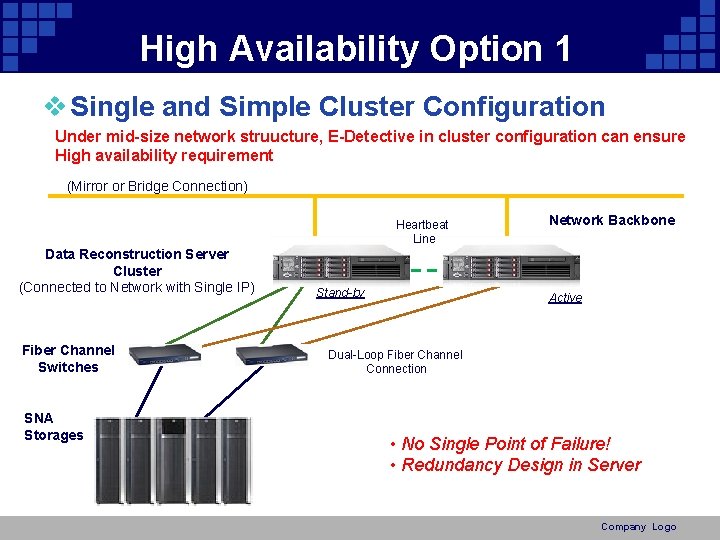
High Availability Option 1 v Single and Simple Cluster Configuration Under mid-size network struucture, E-Detective in cluster configuration can ensure High availability requirement (Mirror or Bridge Connection) Heartbeat Line Data Reconstruction Server Cluster (Connected to Network with Single IP) Fiber Channel Switches SNA Storages Stand-by Network Backbone Active Dual-Loop Fiber Channel Connection • No Single Point of Failure! • Redundancy Design in Server Company Logo

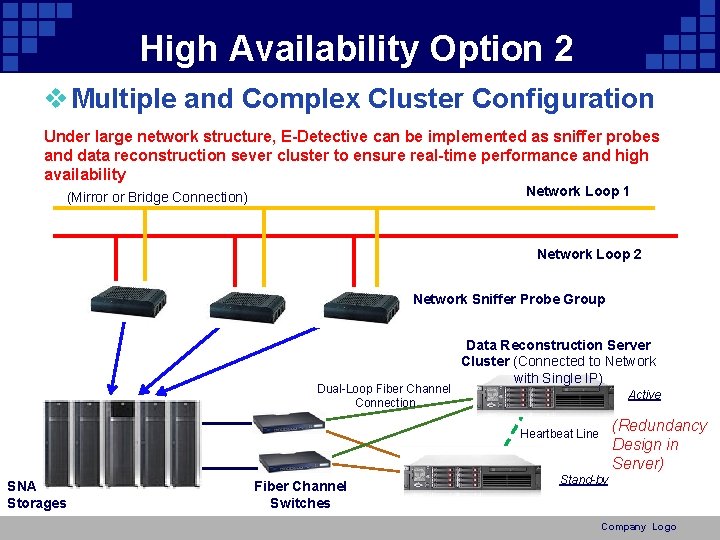
High Availability Option 2 v Multiple and Complex Cluster Configuration Under large network structure, E-Detective can be implemented as sniffer probes and data reconstruction sever cluster to ensure real-time performance and high availability Network Loop 1 (Mirror or Bridge Connection) Network Loop 2 Network Sniffer Probe Group Dual-Loop Fiber Channel Connection Data Reconstruction Server Cluster (Connected to Network with Single IP) Active (Redundancy Design in Server) Heartbeat Line SNA Storages Fiber Channel Switches Stand-by Company Logo

References – Implementation Sites and Customers v v v Criminal Investigation Bureau The Bureau of Investigation Ministry of Justice National Security Agency (Bureau) in various countries Intelligence Agency in various countries Ministry of Defense in various countries Counter/Anti Terrorism Department National Police, Royal Police in various countries Government Ministries in various countries Federal Investigation Bureau in various countries Telco/Internet Service Provider in various countries Banking and Finance organizations in various countries Others Notes: Due to confidentiality of this information, the exact name and countries of the various organizations cannot be revealed.

E-Detective Online Demo https: //60. 251. 127. 208 (root/000000) Decision Group www. edecision 4 u. com