Ecommerce Essentials first edition Kenneth C Laudon Carol






















- Slides: 38

E-commerce Essentials first edition Kenneth C. Laudon Carol Guercio Traver Copyright © 2014 Pearson Education, Inc.

Chapter 5 E-commerce Security and Payment Systems Copyright © 2014 Pearson Education, Inc.

Class Discussion Cyberwar: MAD 2. 0 n What is the difference between hacking and cyberwar? n Why has cyberwar become more potentially devastating in the past decade? n Why has Google been the target of so many cyberattacks? n Is it possible to find a political solution to MAD 2. 0? Copyright © 2014 Pearson Education, Inc. Slide 5 -3

The E-commerce Security Environment n Overall size and losses of cybercrime unclear v Reporting issues n 2011 CSI survey: 46% of respondent firms detected breach in last year n Underground economy marketplace v Stolen information stored on underground economy servers Copyright © 2014 Pearson Education, Inc. Slide 5 -4

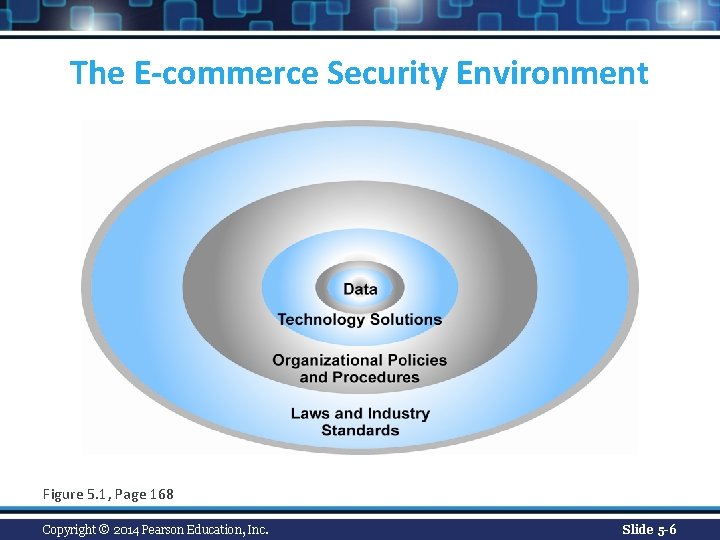
What is Good E-commerce Security? n To achieve highest degree of security v New technologies v Organizational policies and procedures v Industry standards and government laws Copyright © 2014 Pearson Education, Inc. Slide 5 -5

The E-commerce Security Environment Figure 5. 1, Page 168 Copyright © 2014 Pearson Education, Inc. Slide 5 -6

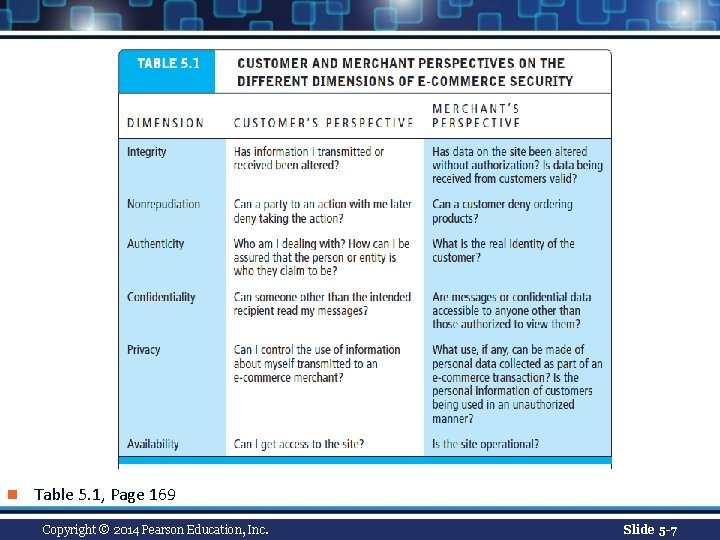
n Table 5. 1, Page 169 Copyright © 2014 Pearson Education, Inc. Slide 5 -7

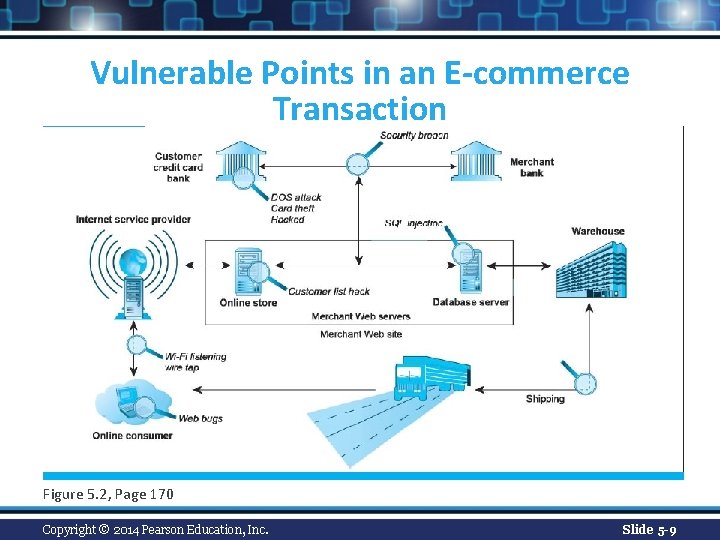
Security Threats in the E-commerce Environment n Three key points of vulnerability in e- commerce environment: 1. Client 2. Server 3. Communications pipeline (Internet communications channels) Copyright © 2014 Pearson Education, Inc. Slide 5 -8

Vulnerable Points in an E-commerce Transaction Figure 5. 2, Page 170 Copyright © 2014 Pearson Education, Inc. Slide 5 -9

Most Common Security Threats in the E-commerce Environment n Malicious code v Viruses v Worms v Trojan horses v Drive-by downloads v Backdoors v Bots, botnets v Threats at both client and server levels Copyright © 2014 Pearson Education, Inc. Slide 5 -10

Most Common Security Threats (cont. ) n Potentially unwanted programs (PUPs) v Browser parasites v Adware v Spyware n Phishing v E-mail scams v Social engineering v Identity theft Copyright © 2014 Pearson Education, Inc. Slide 5 -11

Most Common Security Threats (cont. ) n Hacking v Hackers vs. crackers v Types of hackers: White, black, grey hats v Hacktivism n Cybervandalism v Disrupting, defacing, destroying Web site n Data breach v Losing control over corporate information to outsiders Copyright © 2014 Pearson Education, Inc. Slide 5 -12

Most Common Security Threats (cont. ) n Credit card fraud/theft v Hackers target merchant servers; use data to establish credit under false identity n Spoofing (Pharming) n Spam (junk) Web sites n Denial of service (Do. S) attack v Hackers flood site with useless traffic to overwhelm network n Distributed denial of service (DDo. S) attack Copyright © 2014 Pearson Education, Inc. Slide 5 -13

Most Common Security Threats (cont. ) n Sniffing v Eavesdropping program that monitors information traveling over a network n Insider attacks n Poorly designed server and client software n Social network security issues n Mobile platform security issues v Same risks as any Internet device n Cloud security issues Copyright © 2014 Pearson Education, Inc. Slide 5 -14

Insight on Technology: Class Discussion Think Your Smartphone Is Secure? n What types of threats do smartphones face? n Are there any particular vulnerabilities to this type of device? n Are apps more or less likely to be subject to threats than traditional PC software programs? Copyright © 2014 Pearson Education, Inc. Slide 5 -15

Technology Solutions n Protecting Internet communications v Encryption n Securing channels of communication v SSL, VPNs n Protecting networks v Firewalls n Protecting servers and clients Copyright © 2014 Pearson Education, Inc. Slide 5 -16

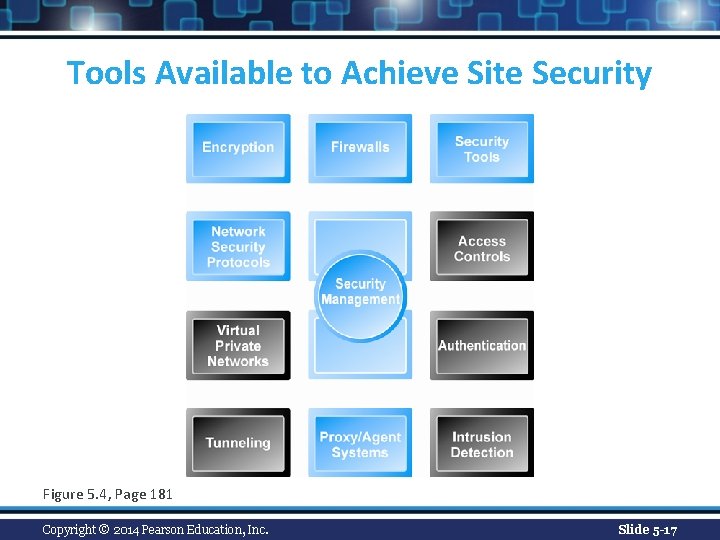
Tools Available to Achieve Site Security Figure 5. 4, Page 181 Copyright © 2014 Pearson Education, Inc. Slide 5 -17

Encryption n Encryption v Transforms data into cipher text readable only by sender and receiver v Secures stored information and information transmission v Provides 4 of 6 key dimensions of e-commerce security n Message integrity n Nonrepudiation n Authentication n Confidentiality Copyright © 2014 Pearson Education, Inc. Slide 5 -18

Symmetric Key Encryption Sender and receiver use same digital key to encrypt and decrypt message n Requires different set of keys for each transaction n Strength of encryption n v n Length of binary key used to encrypt data Advanced Encryption Standard (AES) Most widely used symmetric key encryption v Uses 128 -, 192 -, and 256 -bit encryption keys v n Other standards use keys with up to 2, 048 bits Copyright © 2014 Pearson Education, Inc. Slide 5 -19

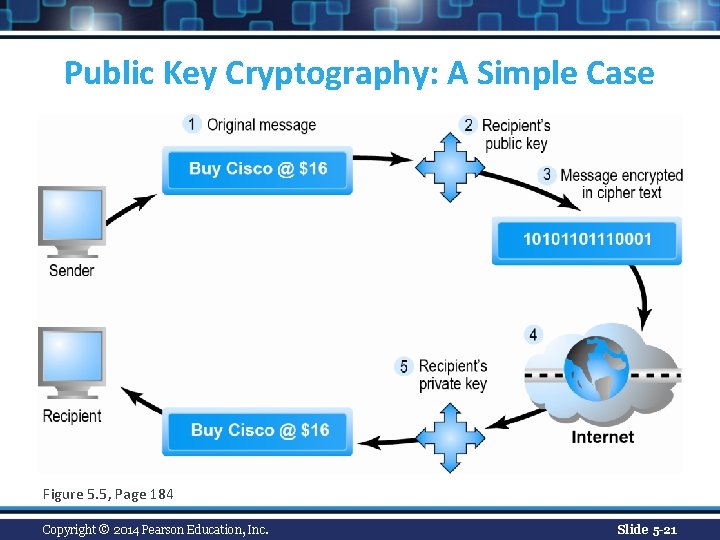
Public Key Encryption n Uses two mathematically related digital keys v Public key (widely disseminated) v Private key (kept secret by owner) n Both keys used to encrypt and decrypt message n Once key used to encrypt message, same key cannot be used to decrypt message n Sender uses recipient’s public key to encrypt message; recipient uses private key to decrypt it Copyright © 2014 Pearson Education, Inc. Slide 5 -20

Public Key Cryptography: A Simple Case Figure 5. 5, Page 184 Copyright © 2014 Pearson Education, Inc. Slide 5 -21

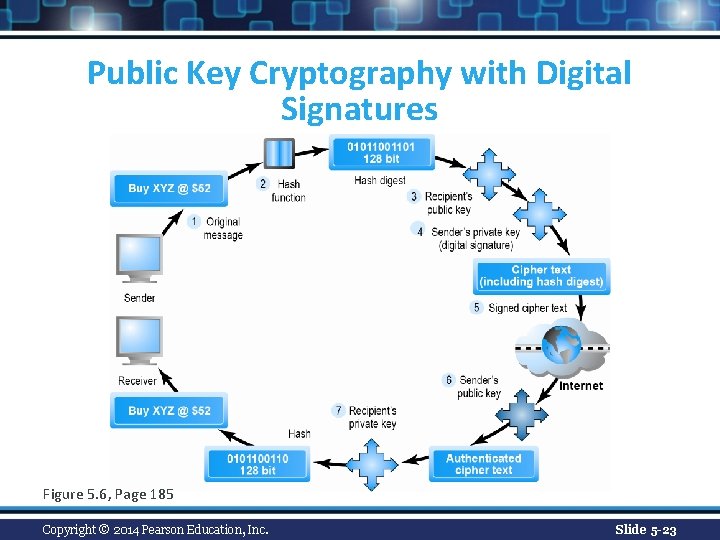
Public Key Encryption Using Digital Signatures and Hash Digests n Hash function: v Mathematical algorithm that produces fixed-length number called message or hash digest Hash digest of message sent to recipient along with message to verify integrity n Hash digest and message encrypted with recipient’s public key n Entire cipher text then encrypted with recipient’s private key—creating digital signature—for authenticity, nonrepudiation n Copyright © 2014 Pearson Education, Inc. Slide 5 -22

Public Key Cryptography with Digital Signatures Figure 5. 6, Page 185 Copyright © 2014 Pearson Education, Inc. Slide 5 -23

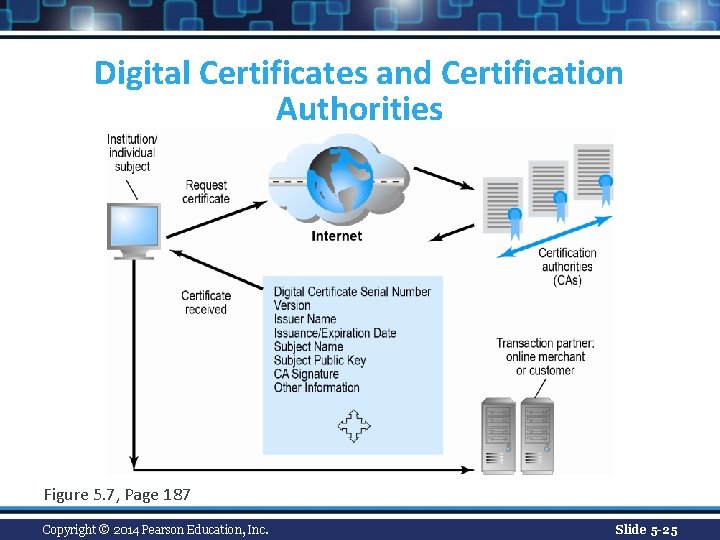
Digital Certificates and Public Key Infrastructure (PKI) n Digital certificate includes: v Name of subject/company v Subject’s public key v Digital certificate serial number v Expiration date, issuance date v Digital signature of CA n Public Key Infrastructure (PKI): v CAs and digital certificate procedures v PGP Copyright © 2014 Pearson Education, Inc. Slide 5 -24

Digital Certificates and Certification Authorities Figure 5. 7, Page 187 Copyright © 2014 Pearson Education, Inc. Slide 5 -25

Limits to Encryption Solutions n Doesn’t protect storage of private key v PKI not effective against insiders, employees v Protection of private keys by individuals may be haphazard n No guarantee that verifying computer of merchant is secure Copyright © 2014 Pearson Education, Inc. Slide 5 -26

Insight on Society: Class Discussion Web Dogs and Anonymity: Identity 2. 0 n What are some of the benefits of continuing the anonymity of the Internet? n Who are the groups involved in creating an identity system for the Internet? n Who should control a central identity system? Copyright © 2014 Pearson Education, Inc. Slide 5 -27

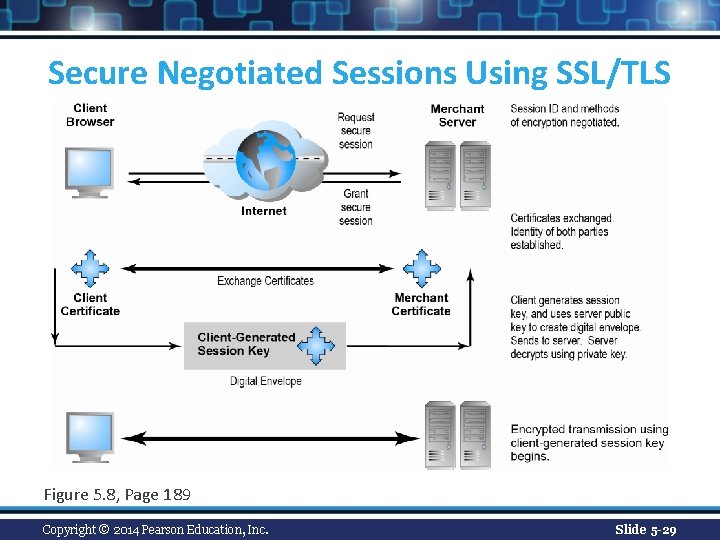
Securing Channels of Communication n Secure Sockets Layer (SSL) and Transport Layer Security (TLS) v Establishes a secure, negotiated client-server session in which URL of requested document, along with contents, is encrypted n Virtual Private Network (VPN) v Allows remote users to securely access internal network via the Internet Copyright © 2014 Pearson Education, Inc. Slide 5 -28

Secure Negotiated Sessions Using SSL/TLS Figure 5. 8, Page 189 Copyright © 2014 Pearson Education, Inc. Slide 5 -29

Protecting Networks n Firewall v Hardware or software v Uses security policy to filter packets n Proxy servers (proxies) v Software servers that handle all communications originating from or being sent to the Internet Copyright © 2014 Pearson Education, Inc. Slide 5 -30

Protecting Servers and Clients n Operating system security enhancements v Upgrades, patches n Anti-virus software v Easiest and least expensive way to prevent threats to system integrity v Requires daily updates Copyright © 2014 Pearson Education, Inc. Slide 5 -31

E-commerce Payment Systems n Credit cards v Still the dominant online payment method in United States n Limitations of online credit card payment systems v Security, merchant risk v Cost v Social equity Copyright © 2014 Pearson Education, Inc. Slide 5 -32

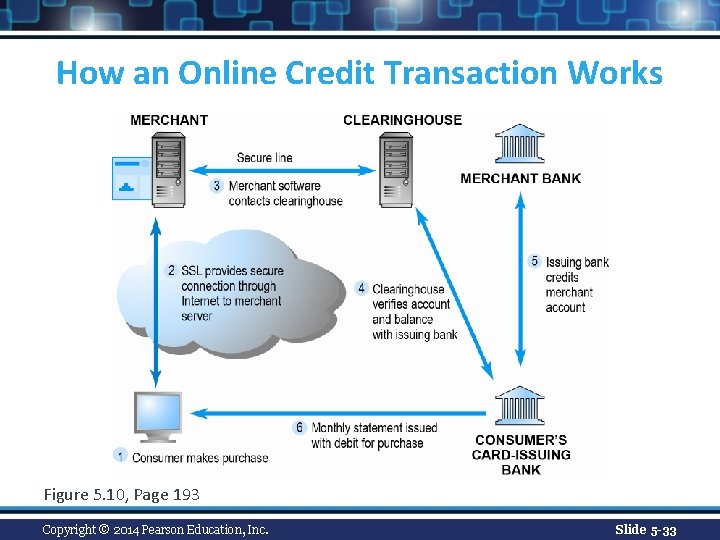
How an Online Credit Transaction Works Figure 5. 10, Page 193 Copyright © 2014 Pearson Education, Inc. Slide 5 -33

Alternative Online Payment Systems n Online stored value systems v Based on value stored in a consumer’s bank, checking, or credit card account v e. g. : Pay. Pal n Other alternatives v Amazon Payments v Google Checkout Copyright © 2014 Pearson Education, Inc. Slide 5 -34

Mobile Payment Systems n Use of mobile phones as payment devices established in Europe, Japan, South Korea n Near field communication (NFC) v Short-range (2”) wireless for sharing data between devices n Expanding in United States v Google Wallet n Mobile app designed to work with NFC chips v Pay. Pal v Square Copyright © 2014 Pearson Education, Inc. Slide 5 -35

Digital Cash and Virtual Currencies n Digital cash v Based on algorithm that generates unique tokens that can be used in “real” world v e. g. : Bitcoin n Virtual currencies v Circulate within internal virtual world v e. g. : Linden Dollars in Second Life, Facebook Credits Copyright © 2014 Pearson Education, Inc. Slide 5 -36

Electronic Billing Presentment and Payment (EBPP) n Online payment systems for monthly bills n 50% of all bill payments n Two competing EBPP business models: v Biller-direct (dominant model) v Consolidator n Both models are supported by EBPP infrastructure providers Copyright © 2014 Pearson Education, Inc. Slide 5 -37

Copyright © 2014 Pearson Education, Inc. Slide 5 -38