ECE 667 Synthesis and Verification of Digital Systems

![Technology Mapping – standard cells • Rule-Based [LSS] • Based on structural mapping [DAGON, Technology Mapping – standard cells • Rule-Based [LSS] • Based on structural mapping [DAGON,](https://slidetodoc.com/presentation_image_h/acf26b158b2f12cb7be0f1b4475fb44f/image-3.jpg)











- Slides: 28

ECE 667 Synthesis and Verification of Digital Systems Technology Mapping (standard cells) Slides adapted (with permission) from A. Kuehlmann, UC Berkeley 2003 1

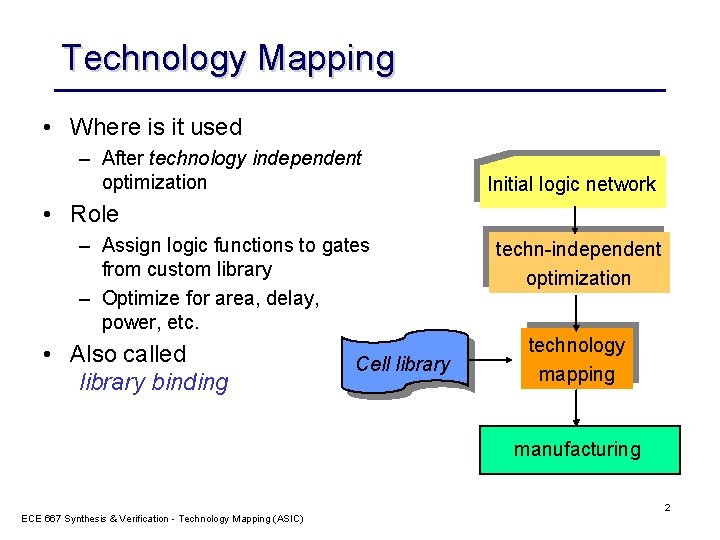
Technology Mapping • Where is it used – After technology independent optimization Initial logic network • Role – Assign logic functions to gates from custom library – Optimize for area, delay, power, etc. • Also called library binding Cell library techn-independent optimization technology mapping manufacturing ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 2
![Technology Mapping standard cells RuleBased LSS Based on structural mapping DAGON Technology Mapping – standard cells • Rule-Based [LSS] • Based on structural mapping [DAGON,](https://slidetodoc.com/presentation_image_h/acf26b158b2f12cb7be0f1b4475fb44f/image-3.jpg)
Technology Mapping – standard cells • Rule-Based [LSS] • Based on structural mapping [DAGON, MISII] – Represent each function of a network using a set of base functions • Typically the base is 2 -input NANDs and inverters • The set should be functionally complete – This representation is called the subject graph. – Each gate of the library is likewise represented using the base set. This generates pattern graphs. • Represent each gate in all possible ways – Cover the subject graph with patterns • graph-based • binate covering • Based on Boolean matching (functional) – Use BDDs to find pattern matching ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 3

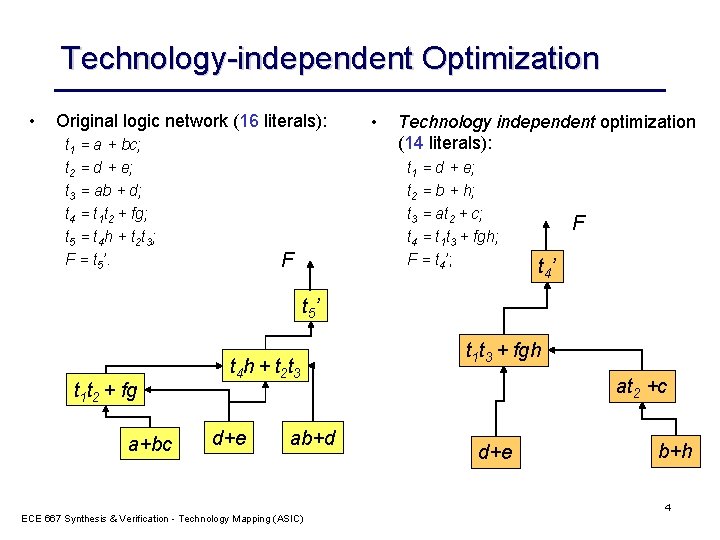
Technology-independent Optimization • Original logic network (16 literals): t 1 = a + bc; t 2 = d + e; t 3 = ab + d; t 4 = t 1 t 2 + fg; t 5 = t 4 h + t 2 t 3; F = t 5’. • Technology independent optimization (14 literals): t 1 = d + e; t 2 = b + h; t 3 = at 2 + c; t 4 = t 1 t 3 + fgh; F = t 4’; F F t 4 ’ t 5 ’ t 1 t 2 + fg a+bc t 4 h + t 2 t 3 d+e ab+d ECE 667 Synthesis & Verification - Technology Mapping (ASIC) t 1 t 3 + fgh at 2 +c d+e b+h 4

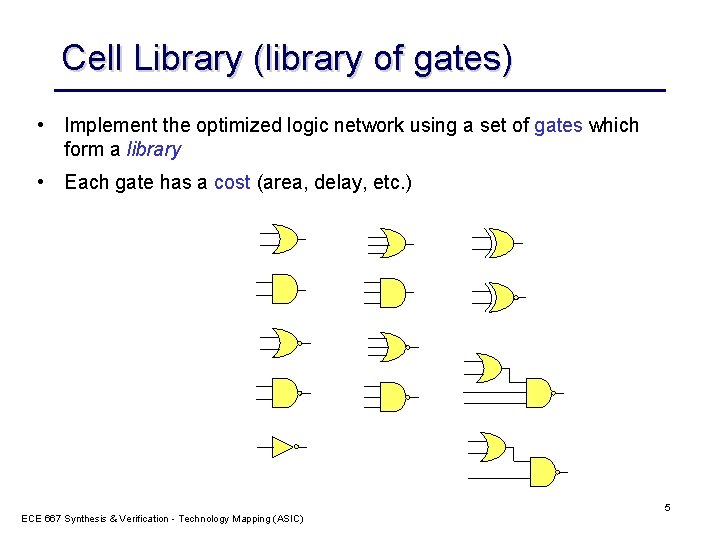
Cell Library (library of gates) • Implement the optimized logic network using a set of gates which form a library • Each gate has a cost (area, delay, etc. ) ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 5

Tree Covering Problem • Given – a rooted binary tree T(V, E), called subject tree, and – a family of rooted pattern trees, each with some cost • Define a cover of the subject tree: – a partition of the edge set E, where each block of the partition induces a tree isomorphic to a pattern tree – i. e. , a set of instances of the pattern trees must cover the subject tree without covering any edge more than once • Tree covering problem – Find a minimum cost covering of the subject graph by choosing from the collection of pattern graphs for all the gates in the library. ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 6

Subject Graph F F Subject graph of 2 -input NANDs and invertors t 4 ’ f t 1 t 3 + fgh at 2 +c c d’ e’ g d+e b+h a b’ ECE 667 Synthesis & Verification - Technology Mapping (ASIC) h h’ 7

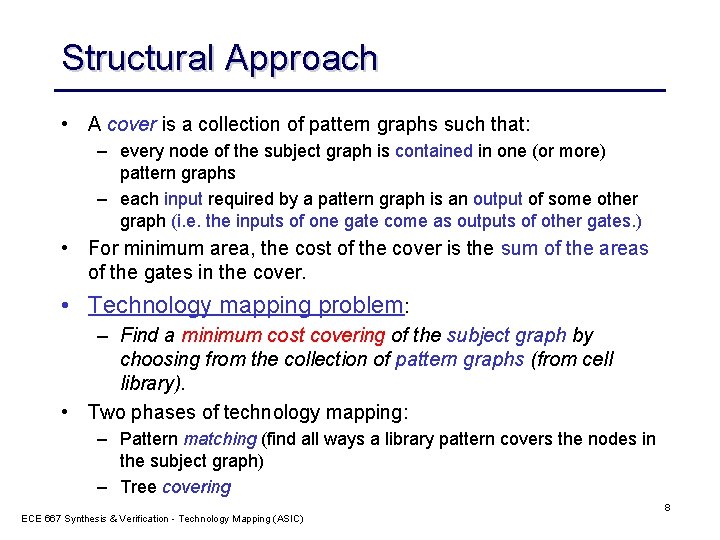
Structural Approach • A cover is a collection of pattern graphs such that: – every node of the subject graph is contained in one (or more) pattern graphs – each input required by a pattern graph is an output of some other graph (i. e. the inputs of one gate come as outputs of other gates. ) • For minimum area, the cost of the cover is the sum of the areas of the gates in the cover. • Technology mapping problem: – Find a minimum cost covering of the subject graph by choosing from the collection of pattern graphs (from cell library). • Two phases of technology mapping: – Pattern matching (find all ways a library pattern covers the nodes in the subject graph) – Tree covering ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 8

Subject Graph f g t 1 = d + e; t 2 = b + h; t 3 = at 2 + c; t 4 = t 1 t 3 + fgh; F = t 4’; d F e h b a c ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 9

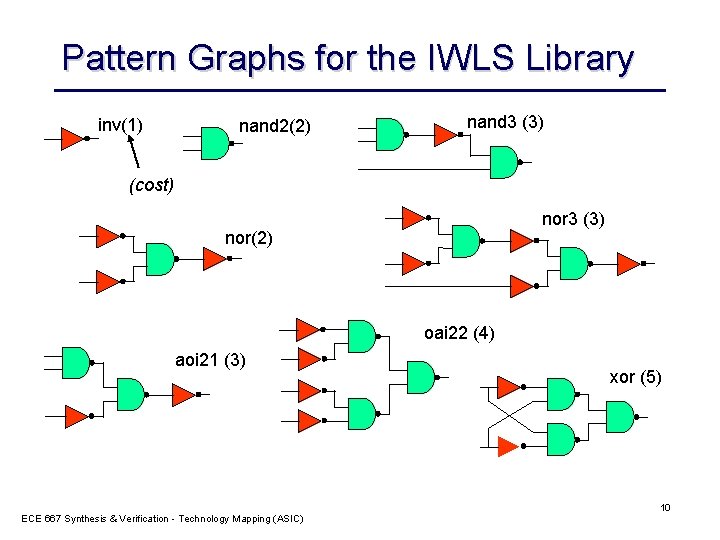
Pattern Graphs for the IWLS Library inv(1) nand 2(2) nand 3 (3) (cost) nor 3 (3) nor(2) oai 22 (4) aoi 21 (3) ECE 667 Synthesis & Verification - Technology Mapping (ASIC) xor (5) 10

Subject graph covering t 1 = d + e; t 2 = b + h; t 3 = at 2 + c; t 4 = t 1 t 3 + fgh; F = t 4’; Total cost = 23 f g d F e h b a c ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 11

Better Covering and 2(3) f t 1 = d + e; t 2 = b + h; t 3 = at 2 + c; t 4 = t 1 t 3 + fgh; F = t 4’; g d or 2(3) F e h b Total cost = 18 aoi 22(4) or 2(3) nand 2(2) a nand 2(2) c inv(1) ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 12

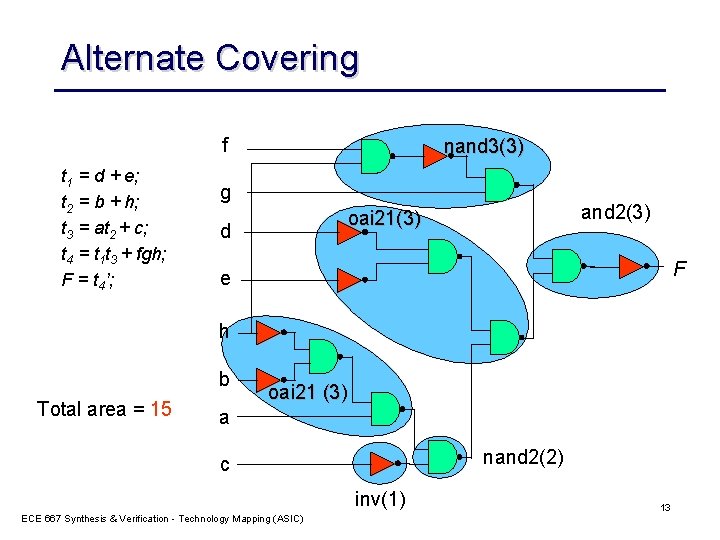
Alternate Covering f t 1 = d + e; t 2 = b + h; t 3 = at 2 + c; t 4 = t 1 t 3 + fgh; F = t 4’; nand 3(3) g and 2(3) oai 21(3) d F e h b Total area = 15 oai 21 (3) a nand 2(2) c inv(1) ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 13

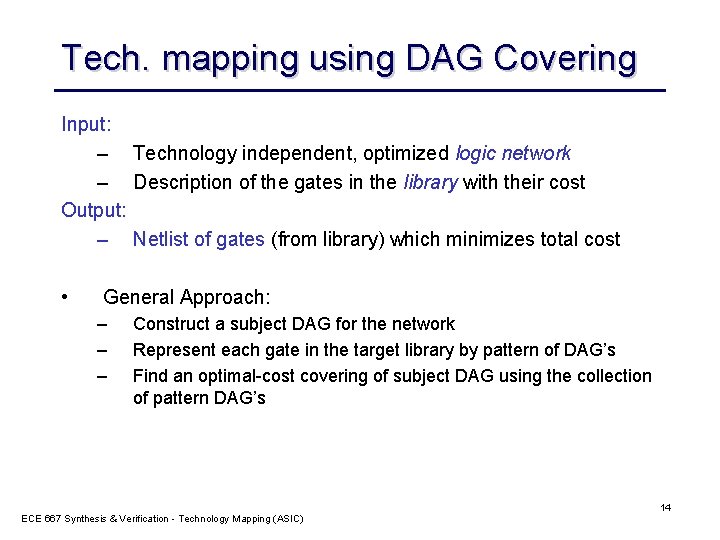
Tech. mapping using DAG Covering Input: – Technology independent, optimized logic network – Description of the gates in the library with their cost Output: – Netlist of gates (from library) which minimizes total cost • General Approach: – – – Construct a subject DAG for the network Represent each gate in the target library by pattern of DAG’s Find an optimal-cost covering of subject DAG using the collection of pattern DAG’s ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 14

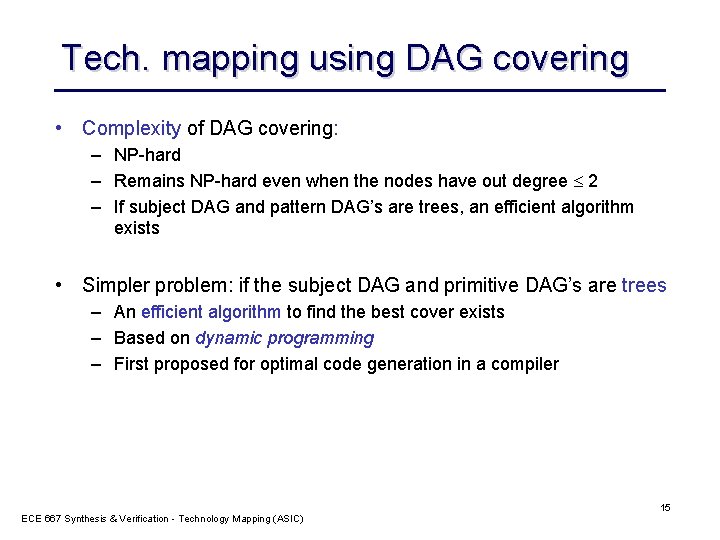
Tech. mapping using DAG covering • Complexity of DAG covering: – NP-hard – Remains NP-hard even when the nodes have out degree 2 – If subject DAG and pattern DAG’s are trees, an efficient algorithm exists • Simpler problem: if the subject DAG and primitive DAG’s are trees – An efficient algorithm to find the best cover exists – Based on dynamic programming – First proposed for optimal code generation in a compiler ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 15

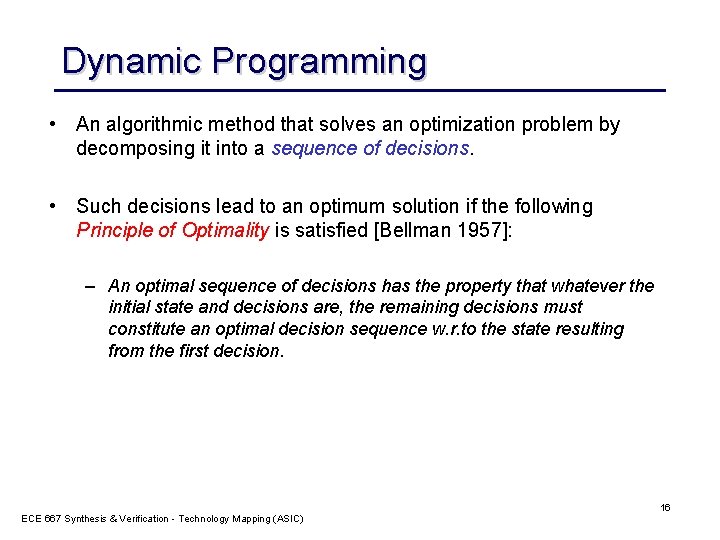
Dynamic Programming • An algorithmic method that solves an optimization problem by decomposing it into a sequence of decisions. • Such decisions lead to an optimum solution if the following Principle of Optimality is satisfied [Bellman 1957]: – An optimal sequence of decisions has the property that whatever the initial state and decisions are, the remaining decisions must constitute an optimal decision sequence w. r. to the state resulting from the first decision. ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 16

Dynamic Programming Simpler statement of Principle of Optimality In an optimal sequence of decisions or choices each subsequence must also be optimal. • Typical recursive equation: cost(i) = mink{ dik + cost(k) } k 1 cost(i) i dik ki cost(ki) kj ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 17

Dynamic Programming - example • Example: shortest path problem in a layered network cost(i) = mink{ dik + cost(k) } Step 1: going from Output(s) to Input(s), compute cost of each node (+ mark the node k that gave minimum cost for i) 9 1 8 3 c s 2 4 7 a 6 d 5 5 5 t b 3 0 3 Step 2: going from Input(s) to Ouput(s), select the node on critical path: (s→c→a→t) ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 18

Dynamic Programming - example • Similarly, for node i at gate gi: cost(i) = mink{cost(gi) + k cost(kj) } i gi k 1 k 2 k inputs to gi ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 19

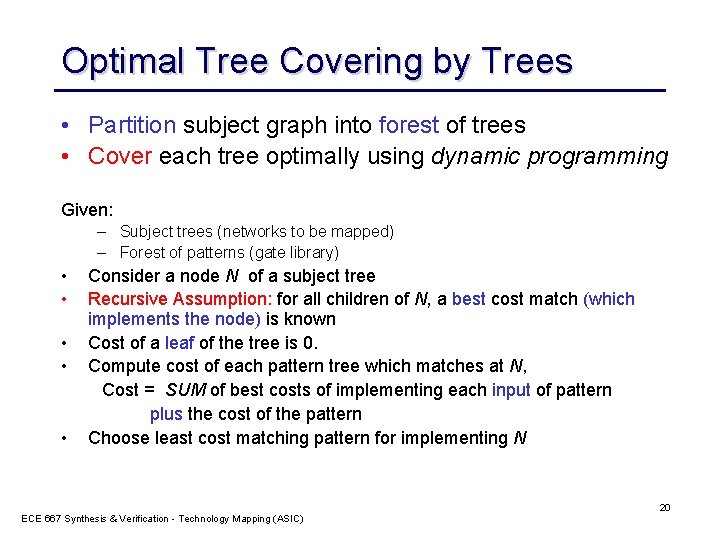
Optimal Tree Covering by Trees • Partition subject graph into forest of trees • Cover each tree optimally using dynamic programming Given: – Subject trees (networks to be mapped) – Forest of patterns (gate library) • • • Consider a node N of a subject tree Recursive Assumption: for all children of N, a best cost match (which implements the node) is known Cost of a leaf of the tree is 0. Compute cost of each pattern tree which matches at N, Cost = SUM of best costs of implementing each input of pattern plus the cost of the pattern Choose least cost matching pattern for implementing N ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 20

Optimum Area Algorithm OPTIMAL_AREA_COVER(node) { foreach input of node { OPTIMAL_AREA_COVER(input); // satisfies recurs. assumption } // Using these, find the best cover at node area = INFINITY; node match = 0; foreach match at node { area = match area; foreach pin of match { area = area + pin area; } if (area < node area) { node area = area; node match = match; } } } ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 21

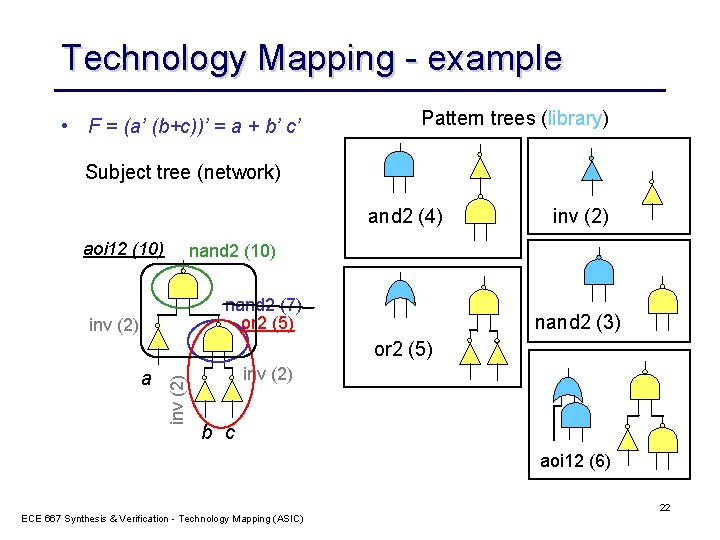
Technology Mapping - example • F = (a’ (b+c))’ = a + b’ c’ Pattern trees (library) Subject tree (network) and 2 (4) aoi 12 (10) inv (2) nand 2 (10) nand 2 (7) or 2 (5) inv (2) nand 2 (3) a inv (2) or 2 (5) inv (2) b c aoi 12 (6) ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 22

Tree Covering in Action Library: (=cost) nand 2(3) nand 2(8) inv(2) aoi 21 nand 2(13) inv(2) nand 4 inv(6) inv(5) and 2(8) nand 2(3) and 2(4) nand 2(7) nand 3(4) ECE 667 Synthesis & Verification - Technology Mapping (ASIC) nand 2(21) nand 3(22) nand 4(18) nand 2 = 3 inv = 2 nand 3 = 4 nand 4 = 5 and 2 = 4 aio 21 = 4 oai 21 = 4 inv(20) aoi 21(18) nand 4 nand 2(21) nand 3(23) nand 4(22) 23

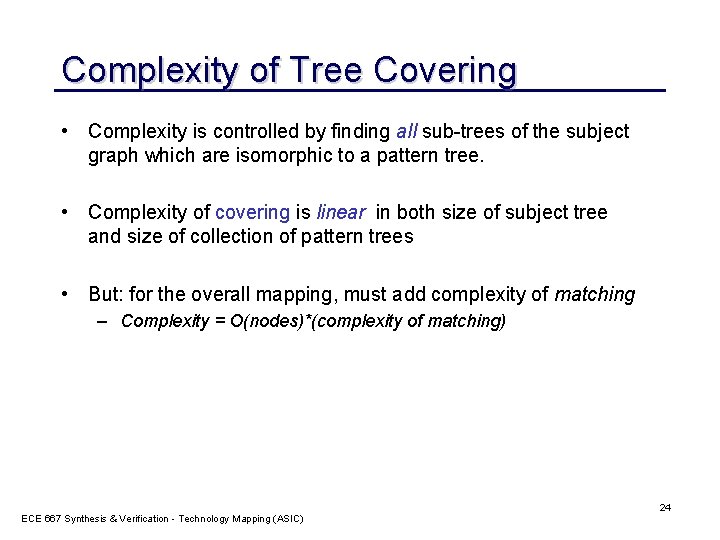
Complexity of Tree Covering • Complexity is controlled by finding all sub-trees of the subject graph which are isomorphic to a pattern tree. • Complexity of covering is linear in both size of subject tree and size of collection of pattern trees • But: for the overall mapping, must add complexity of matching – Complexity = O(nodes)*(complexity of matching) ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 24

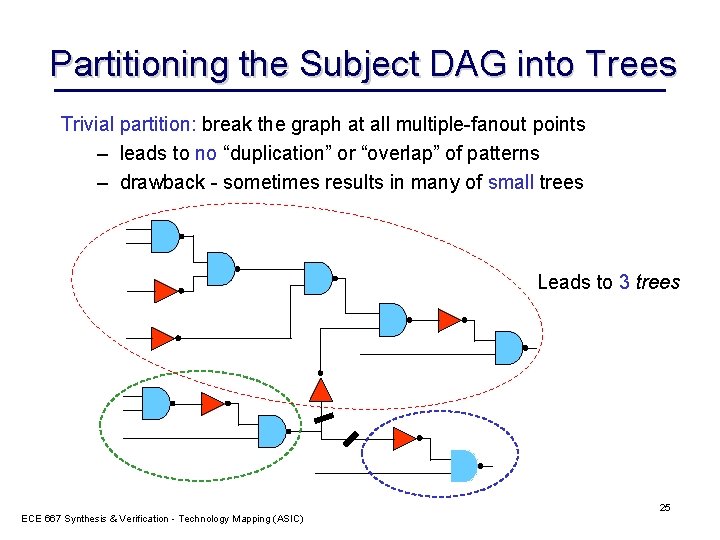
Partitioning the Subject DAG into Trees Trivial partition: break the graph at all multiple-fanout points – leads to no “duplication” or “overlap” of patterns – drawback - sometimes results in many of small trees Leads to 3 trees ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 25

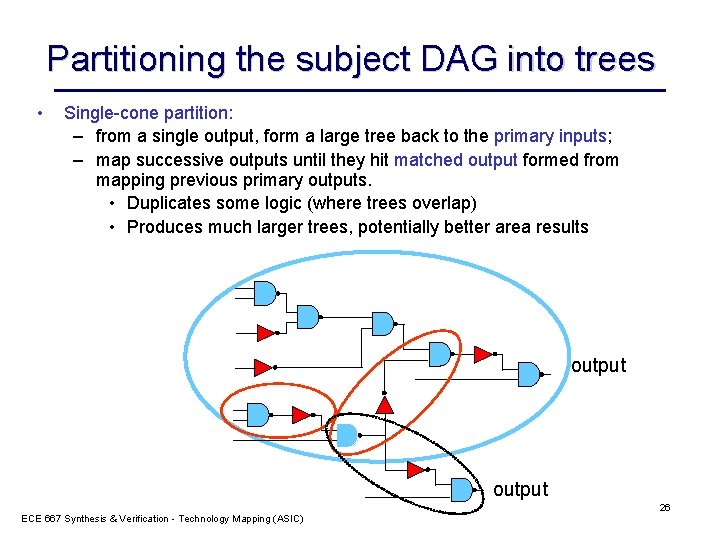
Partitioning the subject DAG into trees • Single-cone partition: – from a single output, form a large tree back to the primary inputs; – map successive outputs until they hit matched output formed from mapping previous primary outputs. • Duplicates some logic (where trees overlap) • Produces much larger trees, potentially better area results output ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 26

Min-Delay Covering • For trees: – identical to min-area covering – use optimal delay values within the dynamic programming paradigm • For DAGs: – if delay does not depend on number of fanouts: use dynamic programming as presented for trees – leads to optimal solution in polynomial time • “we don’t care if we have to replicate logic” • Combined objective – e. g. apply delay as first criteria, then area as second – combine with static timing analysis to focus on critical paths ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 27

Summary • Two approaches to technology mapping – DAG covering – Binate mapping • New approaches: combined logic decomposition and technology mapping – – Lehman, Watanabe allgorithm [1994] Efficiently encode a set on AND 2/INV decompositions Dynamically perform logic decomposition Was implemented and used for commercial design projects (in DEC/Compac alpha) ECE 667 Synthesis & Verification - Technology Mapping (ASIC) 28
 Art 667 cc
Art 667 cc Derechos asertivos básicos
Derechos asertivos básicos Zline 667-36
Zline 667-36 667
667 Systems engineering verification methods
Systems engineering verification methods Verilog hdl: a guide to digital design and synthesis pdf
Verilog hdl: a guide to digital design and synthesis pdf Verilog hdl: a guide to digital design and synthesis
Verilog hdl: a guide to digital design and synthesis Unique features of digital markets
Unique features of digital markets Digital systems testing and testable design
Digital systems testing and testable design Introduction to analog and digital control systems
Introduction to analog and digital control systems Bcd addition of 184 and 576
Bcd addition of 184 and 576 Introduction to digital control
Introduction to digital control Illumination in entrepreneurship
Illumination in entrepreneurship Verification and validation
Verification and validation Verification and validation
Verification and validation Unit 6
Unit 6 Software verification & validation
Software verification & validation Verification principle strengths and weaknesses
Verification principle strengths and weaknesses Shelf rectification and stock verification
Shelf rectification and stock verification Asme v&v 10
Asme v&v 10 Verification and validation
Verification and validation Verification and validation
Verification and validation Verification and validation plan
Verification and validation plan Verification and validation
Verification and validation Amr vs crr
Amr vs crr A software verification and validation method. section 19
A software verification and validation method. section 19 Software verification and validation plan
Software verification and validation plan Decision support systems and intelligent systems
Decision support systems and intelligent systems Hukum digitalmengatur tentang
Hukum digitalmengatur tentang