ECE 526 Network Processing Systems Design Packet Processing



- Slides: 18

ECE 526 – Network Processing Systems Design Packet Processing I: algorithms and data structures Chapter 5: D. E. Comer

Goals • Understand basic packet processing operations • Learn how to design efficient network processing system by ─ Optimized data structures ─ Optimized processing algorithms • Get ready for Lab 1 Ning Weng ECE 526 2

Outline • Packet processing data structures ─ Data storage ─ Linked list • http: //cslibrary. stanford. edu/103/Linked. List. Basics. pdf ─ Hash • http: //en. wikipedia. org/wiki/Hash_table • Packet processing algorithms ─ ─ ─ Ethernet bridge Table lookup and hashing (used for lab 1) Packet flow classification (used for lab 1) IP forwarding, fragmentation and reassembly -- next TCP connection recognition and splicing - next • Lab 1 Ning Weng ECE 526 3

Data Storage: coping & buffering • Used when packet moved from one memory location to another for protocol processing ─ Expensive, why? ─ What can be done to reduce buffer copies? • Must be avoided whenever possible ─ Leave packet in buffer ─ Pass buffer address among threads/layers • Buffer allocation ─ Large, fixed buffer ─ Varied-size buffers ─ Linked list of fixed-size blocks • What size should buffers be? Ning Weng ECE 526 4

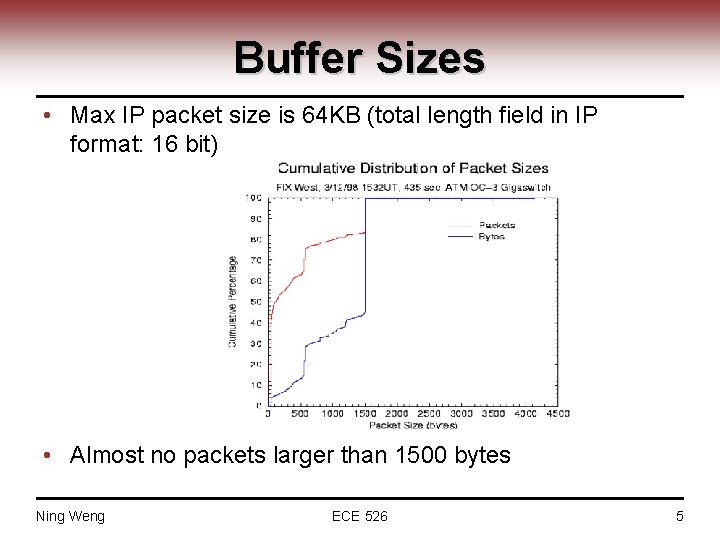
Buffer Sizes • Max IP packet size is 64 KB (total length field in IP format: 16 bit) • Almost no packets larger than 1500 bytes Ning Weng ECE 526 5

Ethernet Bridge • • • Used between a pair of Ethernets Provides transparent connections Listens in promiscuous mode Forwards frames in both directions Uses source address in frames to identify computers on each network • Uses addresses to filter ─ Uses destination address to decide whether to forward frame Ning Weng ECE 526 6

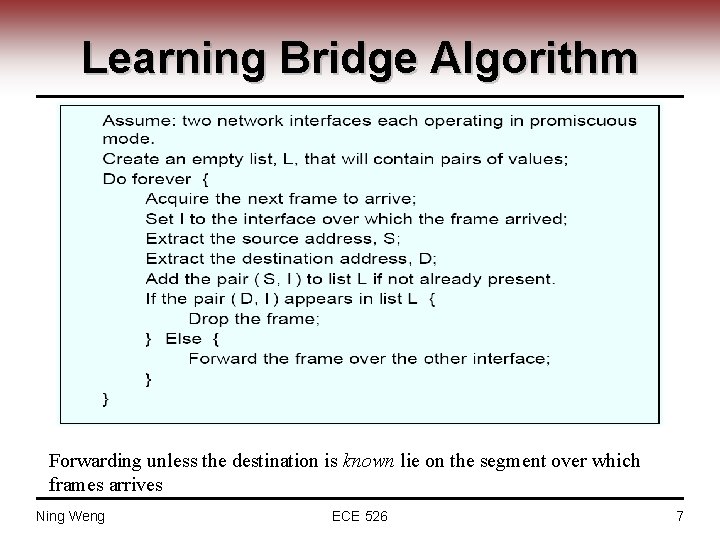
Learning Bridge Algorithm Forwarding unless the destination is known lie on the segment over which frames arrives Ning Weng ECE 526 7

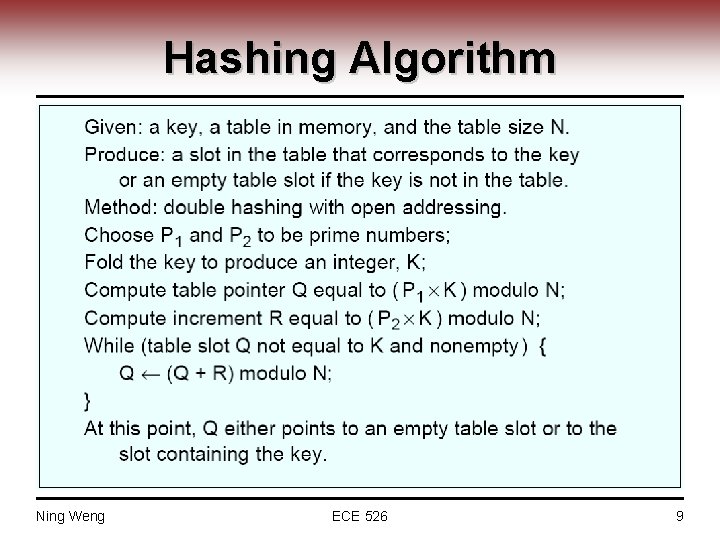
Hash Table Lookup • Table lookup ─ Need high speed ─ Software-based systems use hashing for table lookup • Hashing: ─ Scheme for providing rapid access to data items which are distinguished by some key • Hash table and hash function • Hashing function ─ Function assigns a data item distinguished by some “key” into one of a number of possible “hash buckets” in a hash table ─ Ideal hash function should distribute items evenly between the buckets • Hashing collision ─ Two different items hash to the same location in a hash table ─ Double hashing: one of popular collision resolution technique • Two values: one as a starting value and one as interval between successive values Ning Weng ECE 526 8

Hashing Algorithm Ning Weng ECE 526 9

Packet Classification • Process of mapping a packet to one of the finite sets of “flows” or categories • Flow – set of packets that share common characteristics, for example ─ to the same destination ─ use the same procedure to process • Packets can be classified according to packet header information Ning Weng ECE 526 10

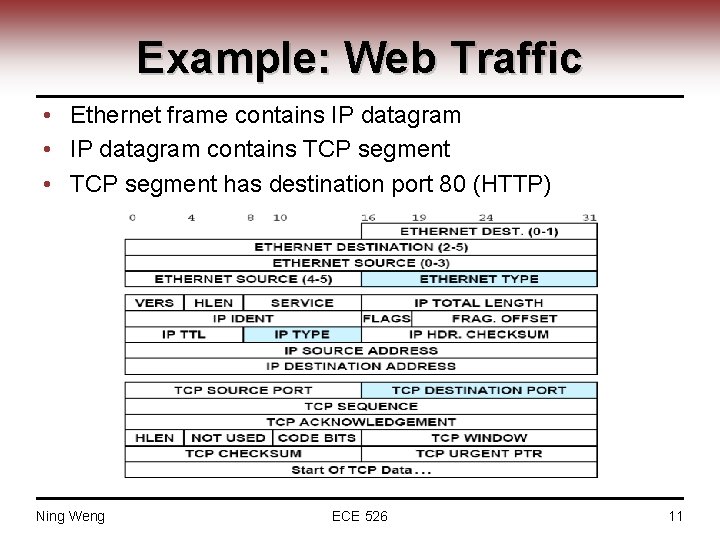
Example: Web Traffic • Ethernet frame contains IP datagram • IP datagram contains TCP segment • TCP segment has destination port 80 (HTTP) Ning Weng ECE 526 11

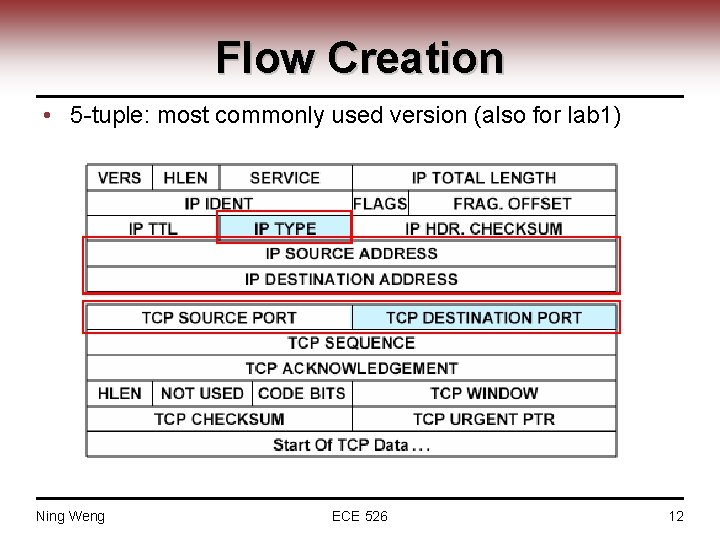
Flow Creation • 5 -tuple: most commonly used version (also for lab 1) Ning Weng ECE 526 12

Flow Creation: major steps • Extract the five tuples from packet header • Calculate the hash value of the five tuples using function • Follows the concept of hashing algorithm ─ to find the right slot: either empty or the one has the same hashing value but also same five tuples ─ different way to compute hash value ─ different way to resolve the collision Ning Weng ECE 526 13

Lab 1 • TCP/IP flow identification • Your program should read a trace of packets and tell the following statistics at the end of the run ─ Number of flows observed. That is the number of unique 5 -tuples consisting of IP source and destination, layer 4 protocol number, and source and destination ports. • We provide you with support functions to read and write packet trace ─ You just need to write partial “packet processing code” based on the guidance. Ning Weng ECE 526 14

Lab 1 • Modify file “flowid. c” only • Three key functions: ─ Init_flowid() • Initialize any data structures that you need • You don’t need modify it, but you need understand it ─ Int flowid(packet *pass_packet) • Packet processing code • You need modify the partial code ─ Finish_flowid() • Called at the end of trace, so you can output results • You need modify this code Ning Weng ECE 526 15

Lab 1: Help • Help: ─ Dr. Weng Office Hours: (MW 2: 30 pm to 3: 30 pm) ─ TAs: Kajal P. Patil and Mini Mathew kajal@siu. edu, mini 10@siu. edu ─ Help Hours: Tu: 11: 00 am-1: 00 pm; Tr: 9: 30 -11: 30 am and Fr: 1 -3 pm Ning Weng ECE 526 16

For Next Class • Read Comer Chapter 5 Ning Weng ECE 526 17

Quiz • Note: (Please write clearly as you can; only a few key words required for each question) • Why packet processing is more and more important compared with other sources of packet delay? Hint: think about the technology/application trend, and the way to reduce each of them. • Why is hashing table efficient for table lookup? Can hashing table be used for layer 2 lookup? How about for layer 3? Please explain to support why and why not. • What is the basic idea of optimize NIC? List of three techniques of using this idea. Ning Weng ECE 526 18