ECE 111 SHA2 Algorithms Flavors of SHA SHA0




![SHA-256 Algorithm • Kt constants K [0. . 63] = 0 x 428 a SHA-256 Algorithm • Kt constants K [0. . 63] = 0 x 428 a](https://slidetodoc.com/presentation_image_h2/5f90bdb8c12a5d8d8d952d2d1ff252f9/image-7.jpg)


- Slides: 12

ECE 111 SHA-2 Algorithms

Flavors of SHA • SHA-0 • SHA-1 • SHA-2 – SHA-224 – SHA-256 – SHA-384 – SHA-512 Longer hash value = more secure

SHA History • 1993 – The hash function SHA-0 was issued as a federal standard by NIST • 1995 – SHA-1 published as the successor to SHA-0 • 2002 – SHA-2 variants • SHA-256, SHA-384, and SHA-512 published • 2004 – SHA-224 published

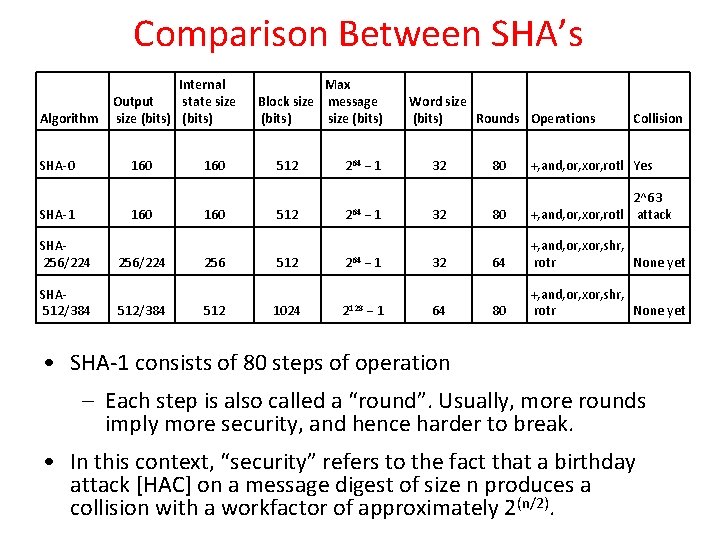
Comparison Between SHA’s Algorithm SHA-0 Internal Output state size (bits) 160 SHA-1 160 SHA 256/224 SHA 512/384 256/224 512/384 160 256 512 Max Block size message (bits) size (bits) 512 264 − 1 512 264 1024 2128 − 1 − 1 Word size Rounds Operations (bits) 32 32 32 64 Collision 80 +, and, or, xor, rotl Yes 80 2^63 +, and, or, xor, rotl attack 64 +, and, or, xor, shr, rotr None yet 80 +, and, or, xor, shr, rotr None yet • SHA-1 consists of 80 steps of operation – Each step is also called a “round”. Usually, more rounds imply more security, and hence harder to break. • In this context, “security” refers to the fact that a birthday attack [HAC] on a message digest of size n produces a collision with a workfactor of approximately 2(n/2).

SHA-256 • Message is processed in 512 -bit blocks sequentially, just like SHA-1 • Message digest is 256 bits instead of SHA-1’s 160 -bits • 64 rounds instead of 80 rounds of compression • Algorithm structure same as SHA-1 – Step 1: Padding bits – Step 2: Appending length as 64 bit unsigned – Step 3: Buffer initiation – Step 4: Processing of message – Step 5: Output

SHA-256 Algorithm • Buffer initiation: Eight 32 -bit words instead of five in SHA-1 H 0 = 0 x 6 a 09 e 667 H 1 = 0 xbb 67 ae 85 H 2 = 0 x 3 c 6 ef 372 H 3 = 0 xa 54 ff 53 a H 4 = 0 x 510 e 527 f H 5 = 0 x 9 b 05688 c H 6 = 0 x 1 f 83 d 9 ab H 7 = 0 x 5 be 0 cd 19
![SHA256 Algorithm Kt constants K 0 63 0 x 428 a SHA-256 Algorithm • Kt constants K [0. . 63] = 0 x 428 a](https://slidetodoc.com/presentation_image_h2/5f90bdb8c12a5d8d8d952d2d1ff252f9/image-7.jpg)
SHA-256 Algorithm • Kt constants K [0. . 63] = 0 x 428 a 2 f 98, 0 x 71374491, 0 xb 5 c 0 fbcf, 0 xe 9 b 5 dba 5, 0 x 3956 c 25 b, 0 x 59 f 111 f 1, 0 x 923 f 82 a 4, 0 xab 1 c 5 ed 5, 0 xd 807 aa 98, 0 x 12835 b 01, 0 x 243185 be, 0 x 550 c 7 dc 3, 0 x 72 be 5 d 74, 0 x 80 deb 1 fe, 0 x 9 bdc 06 a 7, 0 xc 19 bf 174, 0 xe 49 b 69 c 1, 0 xefbe 4786, 0 x 0 fc 19 dc 6, 0 x 240 ca 1 cc, 0 x 2 de 92 c 6 f, 0 x 4 a 7484 aa, 0 x 5 cb 0 a 9 dc, 0 x 76 f 988 da, 0 x 983 e 5152, 0 xa 831 c 66 d, 0 xb 00327 c 8, 0 xbf 597 fc 7, 0 xc 6 e 00 bf 3, 0 xd 5 a 79147, 0 x 06 ca 6351, 0 x 14292967, 0 x 27 b 70 a 85, 0 x 2 e 1 b 2138, 0 x 4 d 2 c 6 dfc, 0 x 53380 d 13, 0 x 650 a 7354, 0 x 766 a 0 abb, 0 x 81 c 2 c 92 e, 0 x 92722 c 85, 0 xa 2 bfe 8 a 1, 0 xa 81 a 664 b, 0 xc 24 b 8 b 70, 0 xc 76 c 51 a 3, 0 xd 192 e 819, 0 xd 6990624, 0 xf 40 e 3585, 0 x 106 aa 070, 0 x 19 a 4 c 116, 0 x 1 e 376 c 08, 0 x 2748774 c, 0 x 34 b 0 bcb 5, 0 x 391 c 0 cb 3, 0 x 4 ed 8 aa 4 a, 0 x 5 b 9 cca 4 f, 0 x 682 e 6 ff 3, 0 x 748 f 82 ee, 0 x 78 a 5636 f, 0 x 84 c 87814, 0 x 8 cc 70208, 0 x 90 befffa, 0 xa 4506 ceb, 0 xbef 9 a 3 f 7, 0 xc 67178 f 2

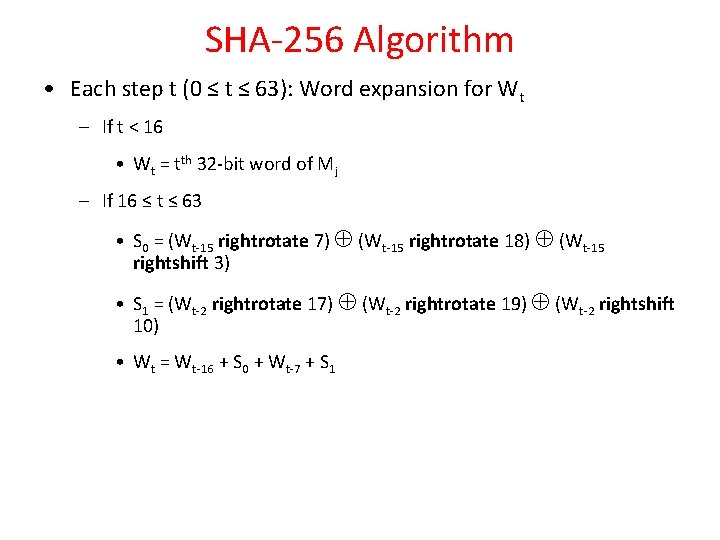
SHA-256 Algorithm • Each step t (0 ≤ t ≤ 63): Word expansion for Wt – If t < 16 • Wt = tth 32 -bit word of Mj – If 16 ≤ t ≤ 63 • S 0 = (Wt-15 rightrotate 7) (Wt-15 rightrotate 18) (Wt-15 rightshift 3) • S 1 = (Wt-2 rightrotate 17) (Wt-2 rightrotate 19) (Wt-2 rightshift 10) • Wt = Wt-16 + S 0 + Wt-7 + S 1

SHA-256 Algorithm • Each step t (0 ≤ t ≤ 63): S 0 = (A rightrotate 2) (A rightrotate 13) (A rightrotate 22) maj = (A ^ B) (B ^ C) t 2 = S 0 + maj S 1 = (E rightrotate 6) (E rightrotate 11) (E rightrotate 25) ch = (E ^ F) (( E) ^ G) t 1 = H + S 1 + ch + Kt + Wt (A, B, C, D, E, F, G, H) = (t 1 + t 2, A, B, C, D + t 1, E, F, G)

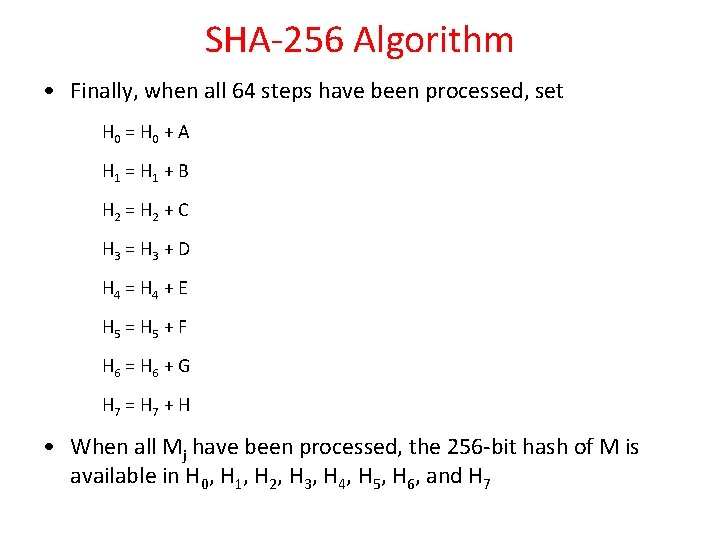
SHA-256 Algorithm • Finally, when all 64 steps have been processed, set H 0 = H 0 + A H 1 = H 1 + B H 2 = H 2 + C H 3 = H 3 + D H 4 = H 4 + E H 5 = H 5 + F H 6 = H 6 + G H 7 = H 7 + H • When all Mj have been processed, the 256 -bit hash of M is available in H 0, H 1, H 2, H 3, H 4, H 5, H 6, and H 7

SHA-512 • SHA-512 is identical in structure, but: – all numbers are 64 bits long, – there are 80 rounds instead of 64, – the initial values and additive constants are extended to 64 bits, and – the shift and rotate amounts used are different.

More Information • Here is the Wikipedia page. – http: //en. wikipedia. org/wiki/SHA-2