EAP WG EAP Key Management Framework Draftietfeapkeying03 txt










- Slides: 18

EAP WG EAP Key Management Framework Draft-ietf-eap-keying-03. txt Bernard Aboba Microsoft

Outline l The problem l l l l The participants The conversation The requirements The invariants EAP key hierarchy Key naming Key lifetime issues

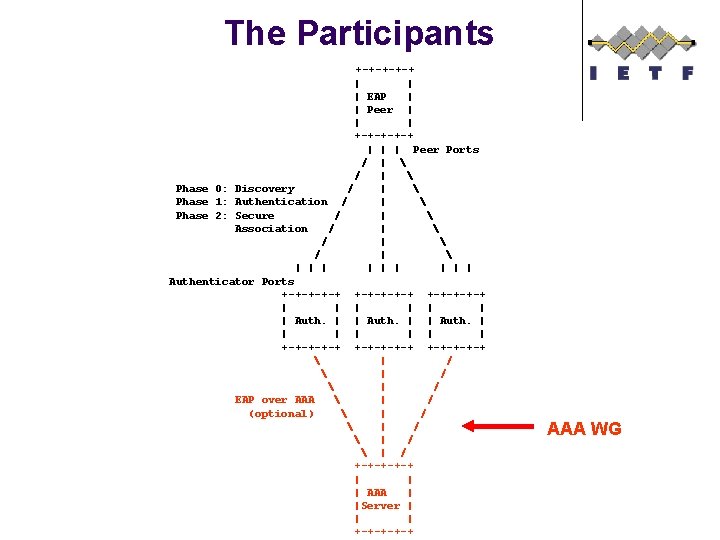
The Participants +-+-+ | | | EAP | | Peer | | | +-+-+ | | | Peer Ports / | Phase 0: Discovery / | Phase 1: Authentication / | Phase 2: Secure / | Association / | | | | | | Authenticator Ports +-+-+-+-+ | | | | Auth. | | | | +-+-+-+-+ | / EAP over AAA | / (optional) | / +-+-+ | | | AAA | |Server | | | +-+-+ AAA WG

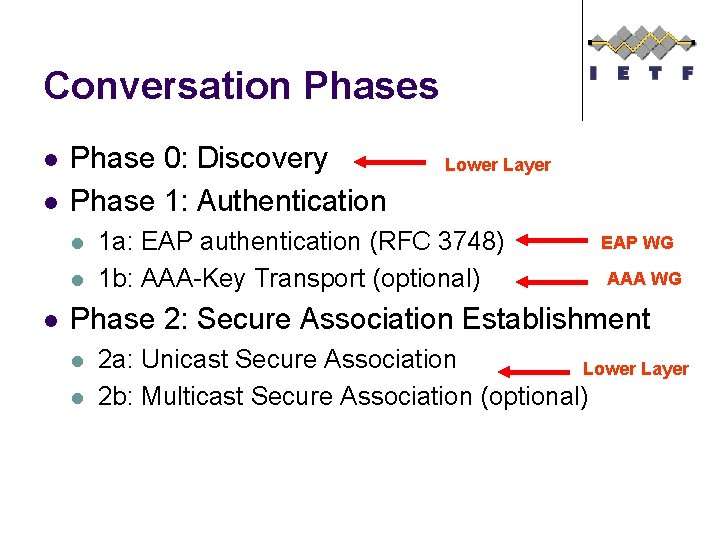
Conversation Phases l l Phase 0: Discovery Phase 1: Authentication l l l Lower Layer 1 a: EAP authentication (RFC 3748) 1 b: AAA-Key Transport (optional) EAP WG AAA WG Phase 2: Secure Association Establishment l l 2 a: Unicast Secure Association Lower Layer 2 b: Multicast Secure Association (optional)

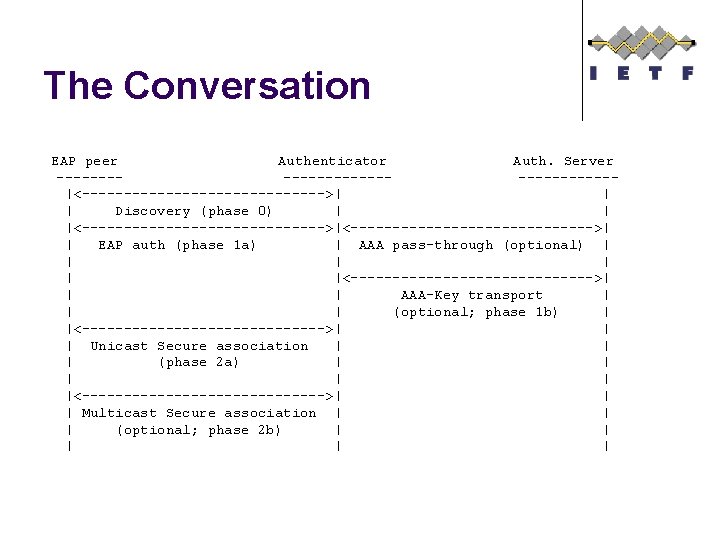
The Conversation EAP peer Authenticator Auth. Server ---------------|<--------------->| | | Discovery (phase 0) | | |<----------------------------->| | EAP auth (phase 1 a) | AAA pass-through (optional) | | |<--------------->| | | AAA-Key transport | | | (optional; phase 1 b) | |<--------------->| | | Unicast Secure association | | | (phase 2 a) | | |<--------------->| | | Multicast Secure association | | | (optional; phase 2 b) | | |

The Requirements l Outlined by Russ Housley at IETF 56 l All AAA WG documents doing key distribution need to meet these requirements l EAP Key Management Framework document chartered to analyze the security of the EAP system

Acceptable solution MUST… (Housley, IETF 56) l Be algorithm independent protocol l l Establish strong, fresh session keys l l l For interoperability, select at least one suite of algorithms that MUST be implemented Maintain algorithm independence Include replay detection mechanism Authenticate all parties l l Maintain confidentiality of authenticator NO plaintext passwords

Acceptable solution MUST also … l l l Perform client and NAS authorization Maintain confidentiality of session keys Confirm selection of “best” ciphersuite Uniquely name session keys Compromise of a single NAS cannot compromise any other part of the system, including session keys and long-term keys Bind key to appropriate context

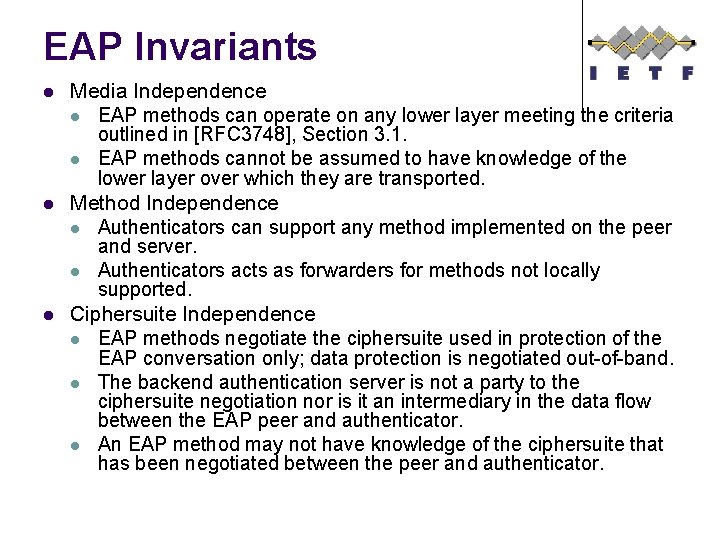
EAP Invariants l l l Media Independence l EAP methods can operate on any lower layer meeting the criteria outlined in [RFC 3748], Section 3. 1. l EAP methods cannot be assumed to have knowledge of the lower layer over which they are transported. Method Independence l Authenticators can support any method implemented on the peer and server. l Authenticators acts as forwarders for methods not locally supported. Ciphersuite Independence l EAP methods negotiate the ciphersuite used in protection of the EAP conversation only; data protection is negotiated out-of-band. l The backend authentication server is not a party to the ciphersuite negotiation nor is it an intermediary in the data flow between the EAP peer and authenticator. l An EAP method may not have knowledge of the ciphersuite that has been negotiated between the peer and authenticator.

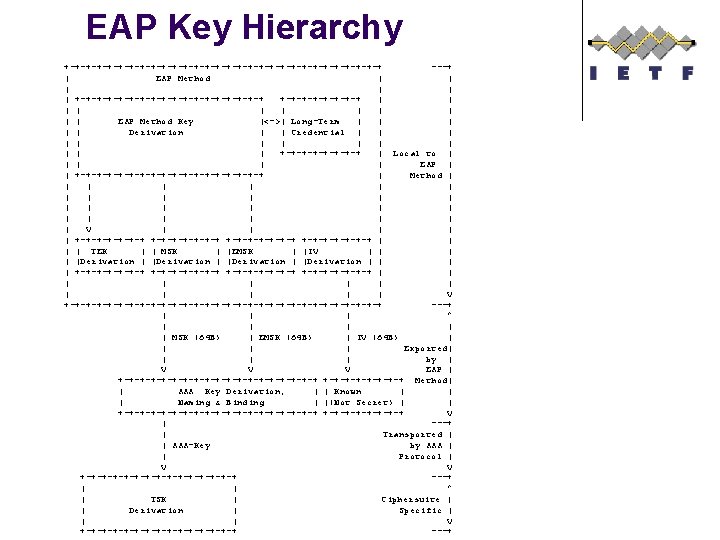
Types of EAP Keys l l Keys calculated locally by the EAP method but not exported by the EAP method, such as the Transient EAP Keys exported by the EAP method: MSK, EMSK, IV Keys calculated from exported quantities: AAA-Key, Application Master Session Keys (AMSKs). Keys calculated by the Secure Association Protocol: Transient Session Keys.

EAP Key Hierarchy +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ ---+ | EAP Method | | | +-+-+-+-+-+-+-+-+-+ | | | EAP Method Key |<->| Long-Term | | | Derivation | | Credential | | | | +-+-+-+-+ | Local to | | | EAP | | +-+-+-+-+-+-+-+-+-+ | Method | | | | | | | V | | | +-+-+-+-+-+-+ | | TEK | | MSK | |EMSK | |IV | | |Derivation | | | | +-+-+-+-+-+-+ | | | | V +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ ---+ | | | ^ | | | MSK (64 B) | EMSK (64 B) | IV (64 B) | | Exported| | by | V V V EAP | +-+-+-+-+-+-+-+-+-+ Method| | AAA Key Derivation, | | Known | | | Naming & Binding | |(Not Secret) | | +-+-+-+-+-+-+-+-+-+ V | ---+ | Transported | | AAA-Key by AAA | | Protocol | V V +-+-+-+-+-+-+-+ ---+ | | ^ | TSK | Ciphersuite | | Derivation | Specific | | | V +-+-+-+-+-+-+-+ ---+

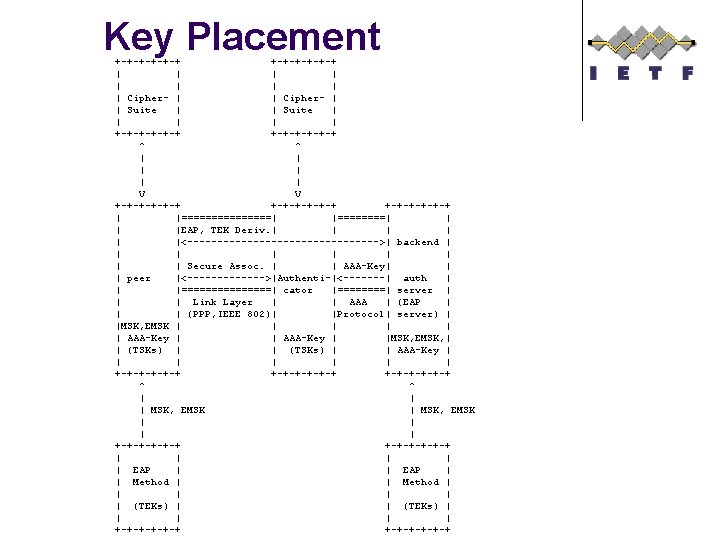
Key Placement +-+-+-+-+-+ | | | | | Cipher- | | Suite | | | +-+-+-+-+-+ ^ ^ | | | V V +-+-+-+-+-+ | |========| |====| | | |EAP, TEK Deriv. | | |<---------------->| backend | | | | | Secure Assoc. | | AAA-Key| | | peer |<------->|Authenti-|<-------| auth | | |========| cator |====| server | | | Link Layer | | AAA | (EAP | | | (PPP, IEEE 802)| |Protocol| server) | |MSK, EMSK | | | AAA-Key | |MSK, EMSK, | | (TSKs) | | AAA-Key | | | | +-+-+-+-+-+ ^ ^ | | | MSK, EMSK | | +-+-+-+-+-+ | | | EAP | | Method | | | | (TEKs) | | | +-+-+-+-+-+

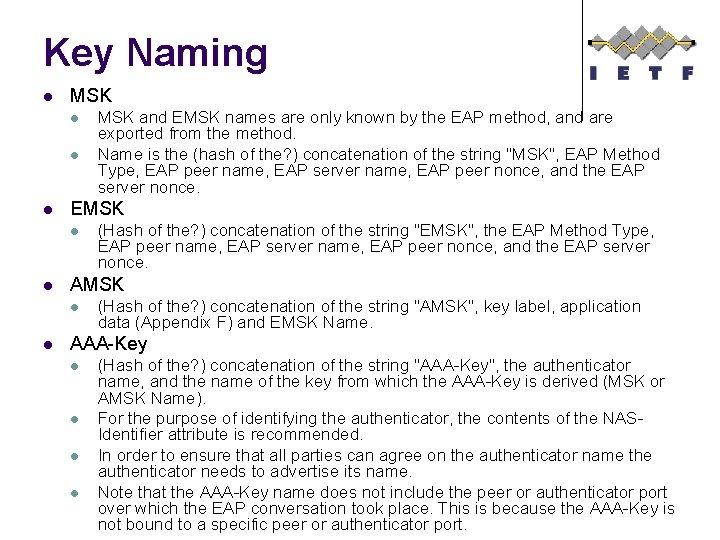
Key Naming l MSK l l l EMSK l l (Hash of the? ) concatenation of the string "EMSK", the EAP Method Type, EAP peer name, EAP server name, EAP peer nonce, and the EAP server nonce. AMSK l l MSK and EMSK names are only known by the EAP method, and are exported from the method. Name is the (hash of the? ) concatenation of the string "MSK", EAP Method Type, EAP peer name, EAP server name, EAP peer nonce, and the EAP server nonce. (Hash of the? ) concatenation of the string "AMSK", key label, application data (Appendix F) and EMSK Name. AAA-Key l l (Hash of the? ) concatenation of the string "AAA-Key", the authenticator name, and the name of the key from which the AAA-Key is derived (MSK or AMSK Name). For the purpose of identifying the authenticator, the contents of the NASIdentifier attribute is recommended. In order to ensure that all parties can agree on the authenticator name the authenticator needs to advertise its name. Note that the AAA-Key name does not include the peer or authenticator port over which the EAP conversation took place. This is because the AAA-Key is not bound to a specific peer or authenticator port.

Key Name Characteristics l l Key Name is not based on the key itself (unlike IEEE 802. 11 i) Key Name used for cache negotiation between peer and authenticator AAA server provides the Key Name (and AAA-Key) ot the authenticator Key Name sent to the authenticator by the EAP server along with the key l l Key Name not known by the authenticator prior to this. No reason for an authenticator to ask the AAA server for a key by name.

Key Lifetime Issues l Management l How are the key lifetimes managed on the peer, authenticator, and AAA server? l l l Negotiation Out of band management Resource reclamation l What happens if resources need to be reclaimed and key state is removed by one or more of the parties?

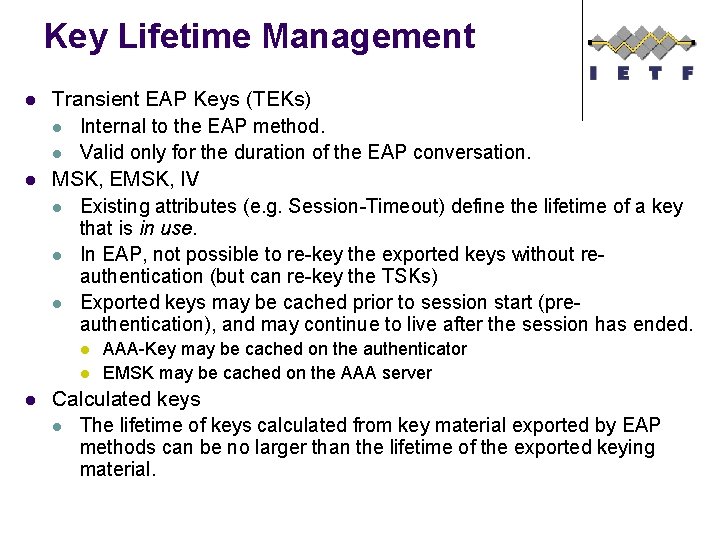
Key Lifetime Management l l Transient EAP Keys (TEKs) l Internal to the EAP method. l Valid only for the duration of the EAP conversation. MSK, EMSK, IV l Existing attributes (e. g. Session-Timeout) define the lifetime of a key that is in use. l In EAP, not possible to re-key the exported keys without reauthentication (but can re-key the TSKs) l Exported keys may be cached prior to session start (preauthentication), and may continue to live after the session has ended. l l l AAA-Key may be cached on the authenticator EMSK may be cached on the AAA server Calculated keys l The lifetime of keys calculated from key material exported by EAP methods can be no larger than the lifetime of the exported keying material.

Thoughts on Exported Key Lifetimes l Where we are today l EAP methods do not negotiate the lifetime of the exported keys. l EAP, defined in [RFC 3748], also does not support the negotiation of lifetimes for exported keying material such as the MSK, EMSK and IV. l To date, Secure Association Protocols also do not negotiate the lifetime of exported keys. l Gap may exist between EAP authentication and the Secure Association Protocol, so not clear it would help Discovery (phase 0) solutions under investigation Recommendations l On the EAP server, it is RECOMMENDED that the cache lifetime of exported keys be managed as a system parameter. l Where a negotiation mechanism is not provided by the lower, it is RECOMMENDED that the peer assume a default value of the exported key lifetime. l May be desirable to manage the TSK re-key time via AAA. l Not clear it is helpful that AAA management of exported key cache lifetime is helpful. l l l AAA server is not aware of authenticator resource constraints Not clear how AAA server, authenticator and peer keep in sync Per-user cache lifetime management may complicate discovery phase solutions

Feedback?