EAP Overview Extensible Authentication Protocol Team Golmaal Vaibhav

EAP Overview (Extensible Authentication Protocol) Team Golmaal: Vaibhav Sharma Vineet Banga Manender Verma Lovejit Sandhu Abizar Attar

Contents: • Introduction • Architecture • Features • Implementations – – – Cisco LEAP EAP-TLS EAP-MD 5 PEAP Other Subtypes • Comparison Chart Cmp. E 209 Team Golmaal 2

Introduction • What is EAP? – Defined by RFC 2284 and 3748 – Universal Authentication Framework – Mainly used in Wireless Networks and Point to point connections – A flexible protocol used to carry arbitrary authentication information. – Typically rides on top of another protocol such as 802. 1 x or RADIUS Cmp. E 209 Team Golmaal 3
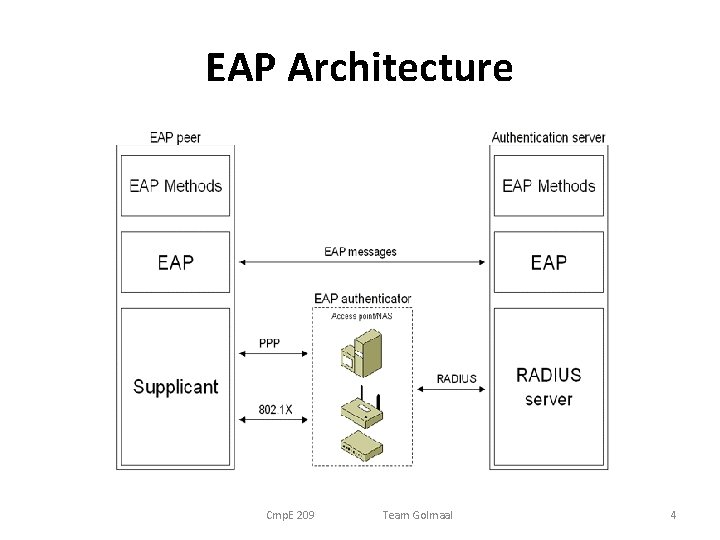
EAP Architecture Cmp. E 209 Team Golmaal 4
EAP Features • Provides some common functions and a negotiation of the desired authentication mechanism called methods. • Currently there about 40 different methods • Methods defined in IETF RFCs include – – – EAP-MD 5 EAP-OTP EAP-GTC EAP-TLS EAP-IKEv 2 and in addition a number of vendor specific methods and new proposals exist • Commonly used modern methods capable of operating in wireless networks include EAP-TLS, EAP-SIM, EAP-AKA, PEAP, LEAP and EAP-TTLS Cmp. E 209 Team Golmaal 5

Cisco LEAP • Lightweight Extensible Authentication Protocol also known as Cisco-Wireless EAP • Proprietary wireless LAN authentication method developed by Cisco Systems. • Provides username/password-based authentication between a wireless client and a RADIUS server like Cisco ACS or Interlink AAA • Among a few protocols used with the IEEE 802. 1 X standard for LAN port access control. Cmp. E 209 Team Golmaal 6
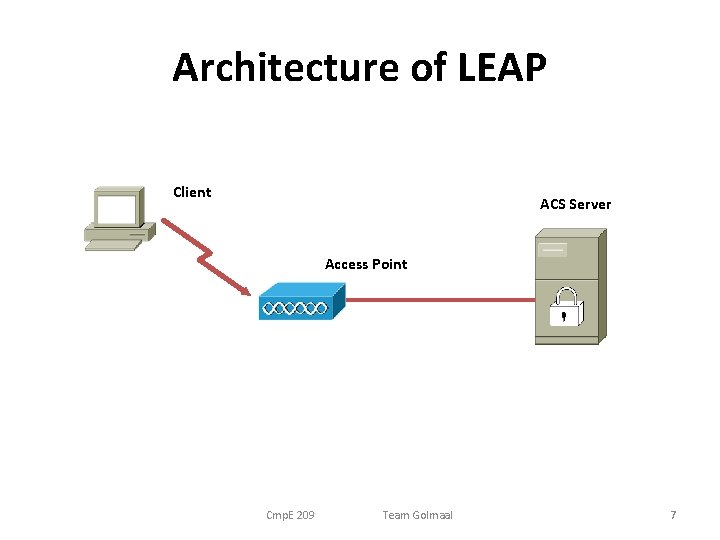
Architecture of LEAP Client ACS Server Access Point Cmp. E 209 Team Golmaal 7
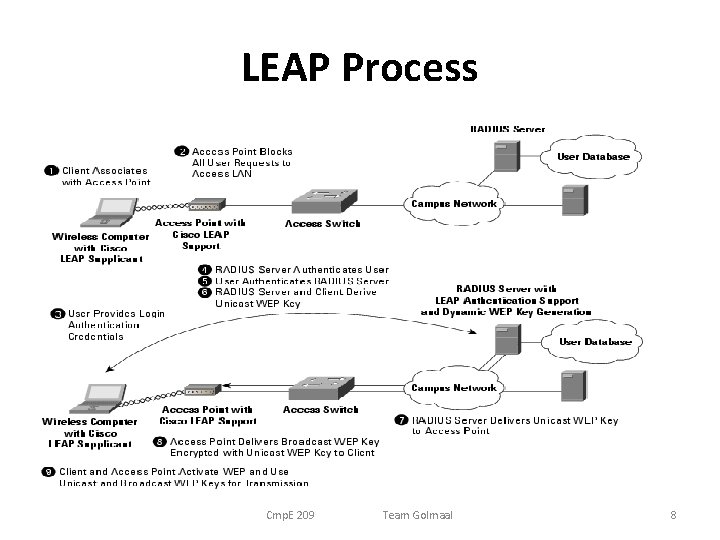
LEAP Process Cmp. E 209 Team Golmaal 8
Limitations of LEAP • Uses a modified authentication protocol version of MS-CHAP in which user credentials are not strongly protected. • Can be susceptible to eavesdropping. • For more robust implementations use of cryptography is necessary for securing user credentials Cmp. E 209 Team Golmaal 9
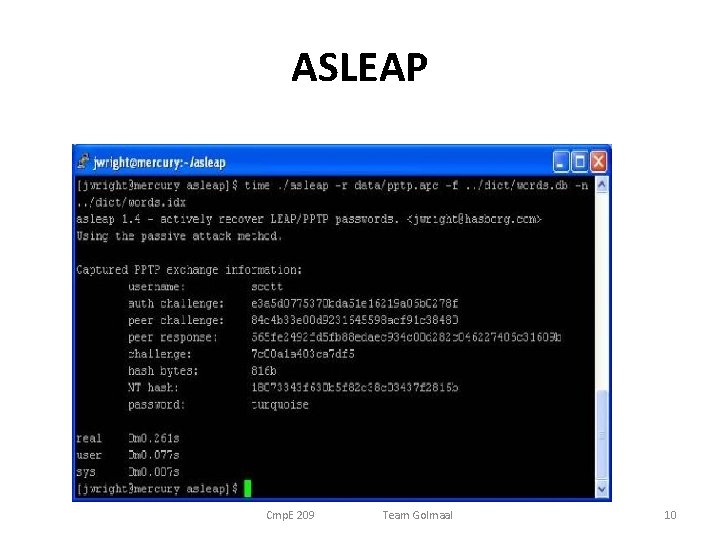
ASLEAP Cmp. E 209 Team Golmaal 10

Cisco’s Response to Limitation of LEAP • Suggests that network administrators to have either of the two reactive techniques: – Force users to have stronger, more complicated passwords – Switch to alternative protocol developed by Cisco (EAP-FAST) for more security. Cmp. E 209 Team Golmaal 11
EAP TLS • An Internet Engineering Task Force (IETF) standard (RFC 2716) that is based on the TLS protocol (RFC 2246) • Considered extension to SSL • Uses digital certificates for both user and server authentication • It uses PKI to secure communication to the RADIUS authentication server • EAP-TLS is the original standard wireless LAN EAP authentication protocol • Supported my all operating systems and network appliances. Cmp. E 209 Team Golmaal 12
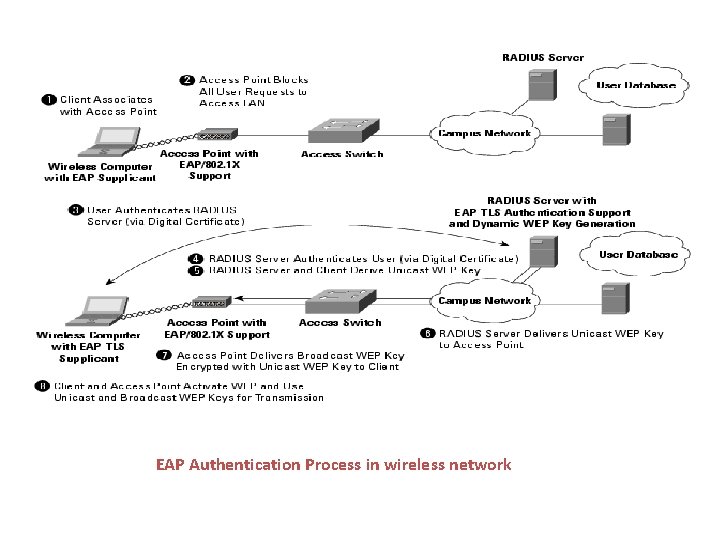
EAP Authentication Process in wireless network
EAP-TTLS (Extension of EAP-TLS) • Extends EAP-TLS • Securely tunnels Client authentication within TLS records • TTLS requires only server-side certificates but in EAP TLS more certificates are used • These certificates are used for one-way TLS authentication (network to user), and once you have a nice, safe, encrypted and integrity-checked channel, you can use EAP inside of the TLS tunnel for any other authentication Cmp. E 209 Team Golmaal 14
PEAP • PEAP is an IETF draft RFC authored by Cisco Systems, Microsoft, and RSA Security • A method to securely transmit authentication information, including passwords, over wired or wireless networks • Uses a digital certificate only for server authentication • Very similar to TTLS! • A TLS tunnel is established, and another EAP session takes place inside • For user authentication, PEAP supports various EAP-encapsulated methods within a protected TLS tunnel • PEAP sub-types - PEAPv 0/EAP-MSCHAPv 2 - PEAPv 1/EAP-GTC Cmp. E 209 Team Golmaal 15
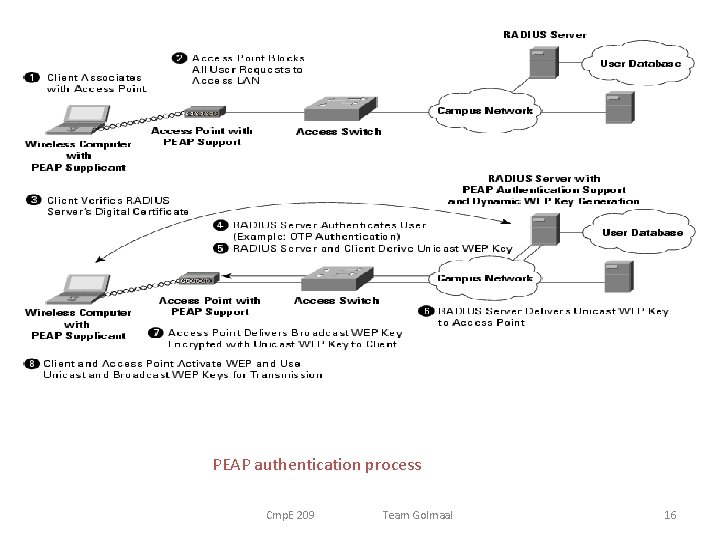
PEAP authentication process Cmp. E 209 Team Golmaal 16

EAP MD 5 • One of the most simple EAP types that can be used. Uses MD 5 hashing. • EAP-MD 5 offers no key management or dynamic key generation, requiring the use of static WEP keys • Okay for wired LANs, offers minimal security in wireless • Vulnerable to dictionary attacks, and does not support mutual authentication or key generation • Unsuitable with dynamic WEP, or WPA/WPA 2 enterprise Cmp. E 209 Team Golmaal 17
Other EAP Subtypes • EAP-PSK: pure symmetric-key EAP • EAP-IKEv 2: EAP authentication method based on the Internet Key Exchange Protocol version 2 (IKEv 2) • EAP-FAST: Flexible Authentication via Secure Tunneling (it is a proposal by Cisco Systems to fix the weaknesses of LEAP) • EAP-SIM: Used for authentication and session key distribution using the Global System for Mobile Communications (GSM) Subscriber Identity Module (SIM) • EAP-AKA: It is for UMTS Authentication and Key Agreement is used for authentication and session key distribution using the Universal Mobile Telecommunications System (UMTS) Cmp. E 209 Team Golmaal 18
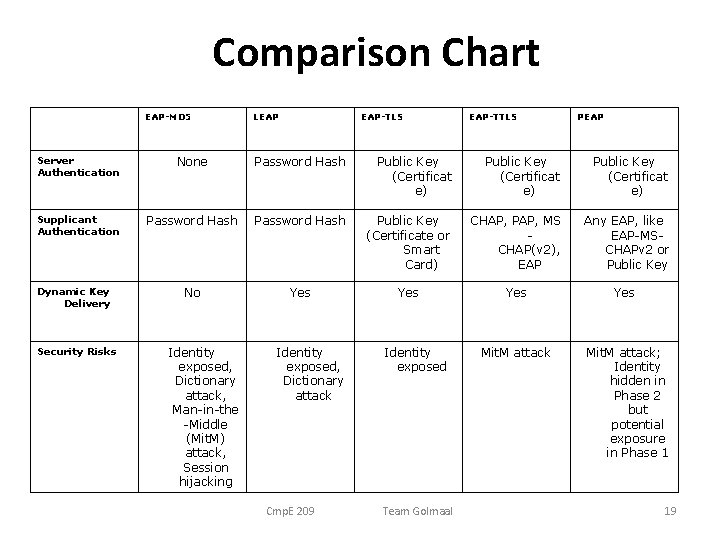
Comparison Chart EAP-MD 5 LEAP EAP-TLS EAP-TTLS PEAP Server Authentication None Password Hash Public Key (Certificat e) Supplicant Authentication Password Hash Public Key (Certificate or Smart Card) CHAP, PAP, MS CHAP(v 2), EAP Any EAP, like EAP-MSCHAPv 2 or Public Key No Yes Yes Mit. M attack; Identity hidden in Phase 2 but potential exposure in Phase 1 Dynamic Key Delivery Security Risks Identity exposed, Dictionary attack, Man-in-the -Middle (Mit. M) attack, Session hijacking Identity exposed, Dictionary attack Cmp. E 209 Identity exposed Team Golmaal 19

References • http: //en. wikipedia. org/wiki/Extensible_Authentication_Protocol • http: //www. wifiplanet. com/tutorials/article. php/3075481 • http: //wireless. utk. edu/documentation/papers/802. 1 x-chris. pdf • http: //www. cisco. com/en/US/netsol/ns 339/ns 395/ns 176/ns 178/n etworking_solutions_white_paper 09186 a 008009 c 8 b 3. shtml • http: //searchnetworking. techtarget. com/original. Content/0, 289142, sid 7_gci 843996, 00. html • http: //asleap. sourceforge. net Cmp. E 209 Team Golmaal 20
- Slides: 20