e Xtensible Access Control Markup Language OASIS Standard
![e. Xtensible Access Control Markup Language [OASIS Standard] Kailash Bhoopalam Java and XML Old e. Xtensible Access Control Markup Language [OASIS Standard] Kailash Bhoopalam Java and XML Old](https://slidetodoc.com/presentation_image_h2/4be1693c77b948795a6e34b93a64a25d/image-1.jpg)
e. Xtensible Access Control Markup Language [OASIS Standard] Kailash Bhoopalam Java and XML Old Dominion University 1

Contents • • • Introduction to Access Control Introduction to XACML The XACML schema. Access Control Examples and Experiments with XACML. The XACML framework. Installing and using the XACML package. Beyond Vanilla XACML User Extensions to XACML Implementation XACML in Secure Distributed Digital Libraries Old Dominion University 2
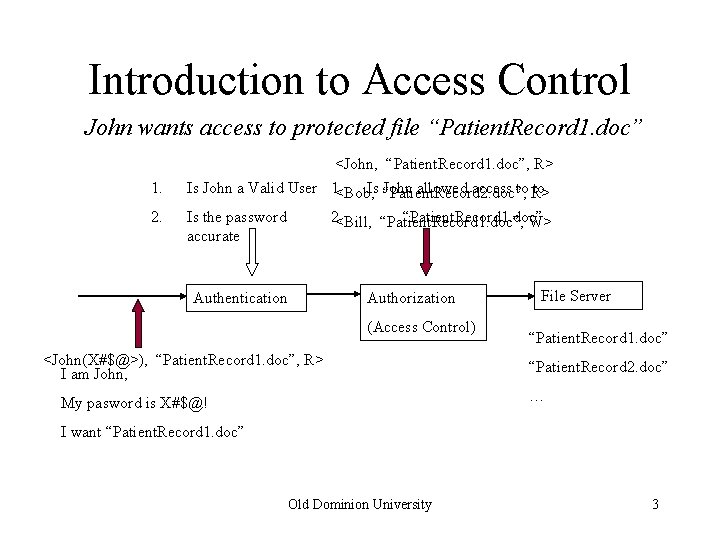
Introduction to Access Control John wants access to protected file “Patient. Record 1. doc” 1. 2. <John, “Patient. Record 1. doc”, R> Is John a Valid User 1. allowed access to R> to <Bob, Is John “Patient. Record 2. doc”, 2. “Patient. Record 1. doc” <Bill, “Patient. Record 1. doc”, W> Is the password accurate Authentication Authorization (Access Control) <John(X#$@>), “Patient. Record 1. doc”, R> I am John, File Server “Patient. Record 1. doc” “Patient. Record 2. doc” … My pasword is X#$@! I want “Patient. Record 1. doc” Old Dominion University 3
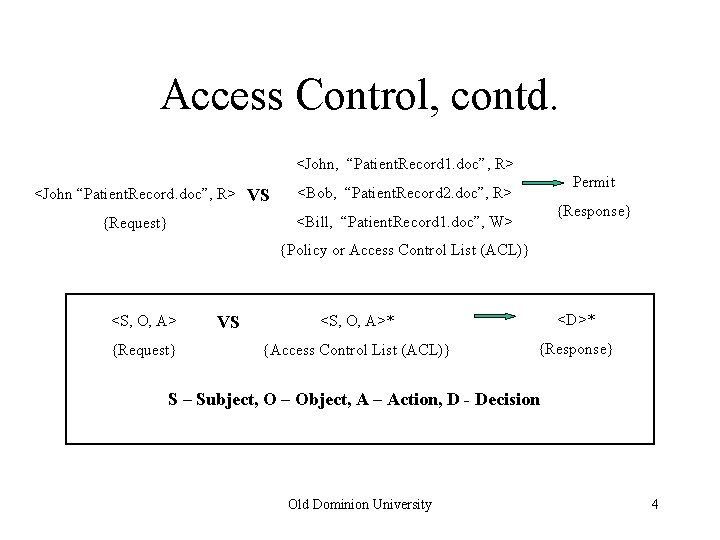
Access Control, contd. <John, “Patient. Record 1. doc”, R> <John “Patient. Record. doc”, R> VS Permit <Bob, “Patient. Record 2. doc”, R> {Response} <Bill, “Patient. Record 1. doc”, W> {Request} {Policy or Access Control List (ACL)} <S, O, A> {Request} VS <S, O, A>* <D>* {Access Control List (ACL)} {Response} S – Subject, O – Object, A – Action, D - Decision Old Dominion University 4
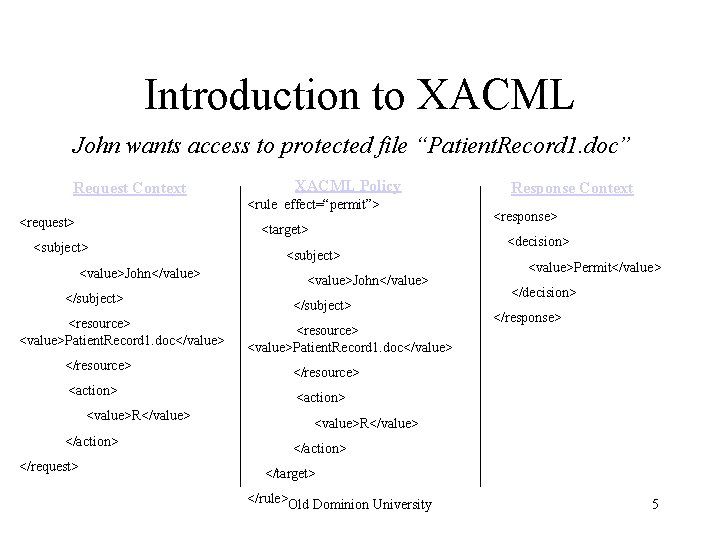
Introduction to XACML John wants access to protected file “Patient. Record 1. doc” Request Context XACML Policy <rule effect=“permit”> <request> <target> <subject> <value>John</value> </subject> <resource> <value>Patient. Record 1. doc</value> </resource> <action> <value>R</value> </action> </request> <subject> <value>John</value> </subject> <resource> <value>Patient. Record 1. doc</value> Response Context <response> <decision> <value>Permit</value> </decision> </response> </resource> <action> <value>R</value> </action> </target> </rule>Old Dominion University 5
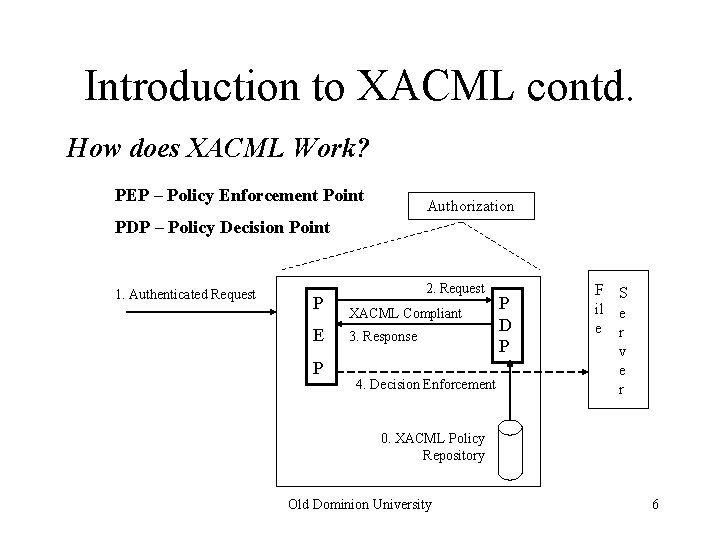
Introduction to XACML contd. How does XACML Work? PEP – Policy Enforcement Point Authorization PDP – Policy Decision Point 1. Authenticated Request P E P 2. Request XACML Compliant 3. Response 4. Decision Enforcement P D P F S il e e r v e r 0. XACML Policy Repository Old Dominion University 6
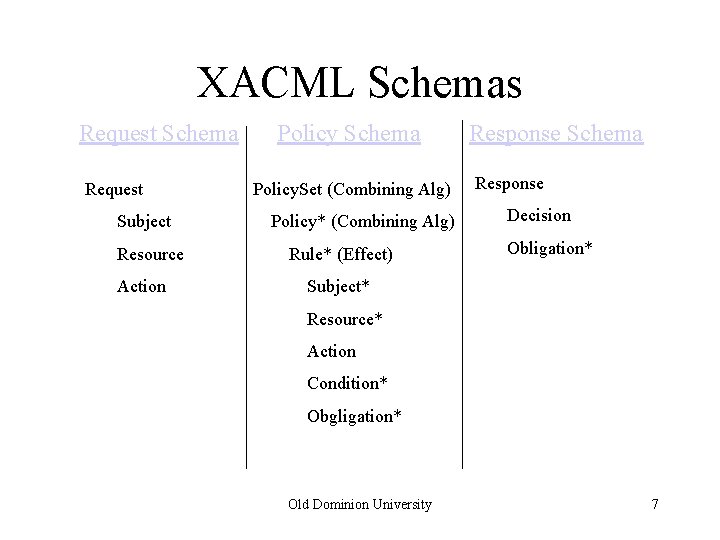
XACML Schemas Request Schema Request Subject Resource Action Policy Schema Policy. Set (Combining Alg) Policy* (Combining Alg) Rule* (Effect) Response Schema Response Decision Obligation* Subject* Resource* Action Condition* Obgligation* Old Dominion University 7

Some Experiments • Ex 1 • Ex 2 • Ex 3 Old Dominion University 8
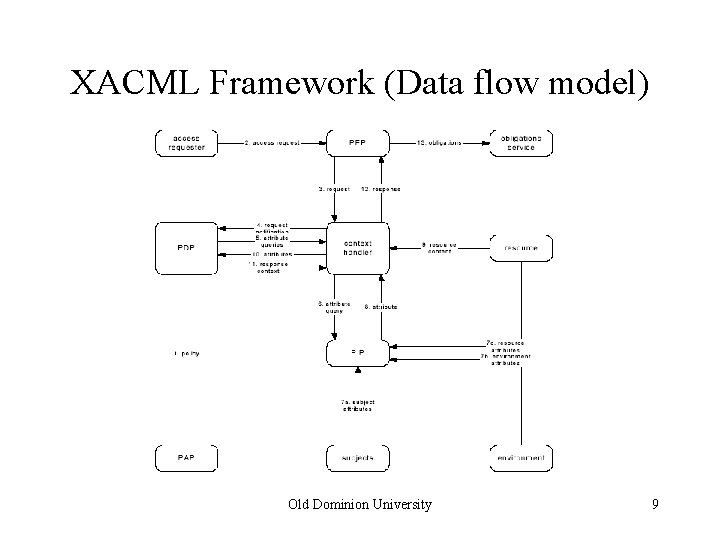
XACML Framework (Data flow model) Old Dominion University 9
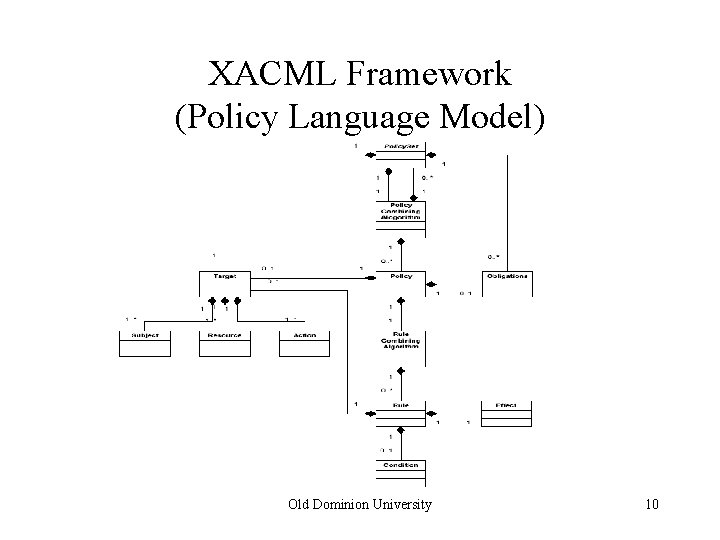
XACML Framework (Policy Language Model) Old Dominion University 10
Installing and using the XACML Implementation • Available Implementations – Sun Microsystems (here) (download) • You may also optionally copy from ~kbhoopal/public_html/xacml/sunxacml. jar – Jiffy Software (here) More on Sun’s XACML implementation Available as zip file. unzip and build with “ant” (download ant) include the sunxacml. jar in the class path. Old Dominion University 11
Using the XACML Implementation (A Programmers Guide) • Using Sun’s XACML Implementation – Overview of APIs – Building a basic PDP – Building the basic PEP – Validating Policies and Requests • Some Experiments Old Dominion University 12

Beyond Vanilla Access Control – Policy & Rule Combining algorithms Permit Overrides: If a single rule permits a request, irrespective of the other rules, the result of the PDP is Permit Deny Overrides: If a single rule denies a request, irrespective of the other rules, the result of the PDP is deny. First Applicable: The first applicable rule that satisfies the request is the result of the PDP Only-one-applicable: If there are two rules with different effects for the same request, the result is indeterminate Old Dominion University 13

Beyond Vanilla, contd. • Conditions – Declarative use of boolean expressions – Using Environment variables like time, etc. • E. g. , John can access patientrecord 1. doc only between 9 am and 4 pm. • Obligations – An operation performed in a policy or policy set that should be performed in conjunction with the enforcement of an authorization decision. Old Dominion University 14
Beyond Vanilla, contd. • XACML Functions – – – – Equality Predicates Arithmetic & Arithmetic comparison String Conversion Numeric Data Type Conversion Logical Date and Time Set And Many more. Old Dominion University 15
User Extensions to XACML Implementation • Extend – Attributes – Functions – Combining algorithms – Finder modules. Old Dominion University 16
XACML in SDDL • Implementation PAP, PIP using a Policy Editor (here) • Implementation of Sun. XACML’s PDP with a custom PEP and integration with Shibboleth and Archon. (here) Old Dominion University 17

References • XACML Specification • Sun’s XACML Implementation Old Dominion University 18
- Slides: 18