e Invoicing day CEF e Delivery Digital Service







- Slides: 20

e. Invoicing day CEF e. Delivery Digital Service Infrastructure 01 December 2016 João Rodrigues Frade, DIGIT B 4

Agenda 1 Introduction to e. Delivery 2 e. Delivery and e. IDAS ERDS in practice 3 PEPPOL and CEF e. Delivery Convergence Process

Y 1 Introduction to e. Delivery

What happened before TODAY e. Delivery Stakeholder Days 28/10/2016 Webinar - How can CEF help you set-up your e. Delivery infrastructure? 12/09/2016 Webinar - Electronic Registered Delivery Service (ERDS) and the e. IDAS Regulation 26/07/16 CEF e. Delivery - What's In It For You 26/05/16 Information session on AS 4 Profile 25/05/16 e. Delivery Extended Expert Group 19/05/16 CEF Digital Presents at the AMA More information on CEF Digital Event Calendar

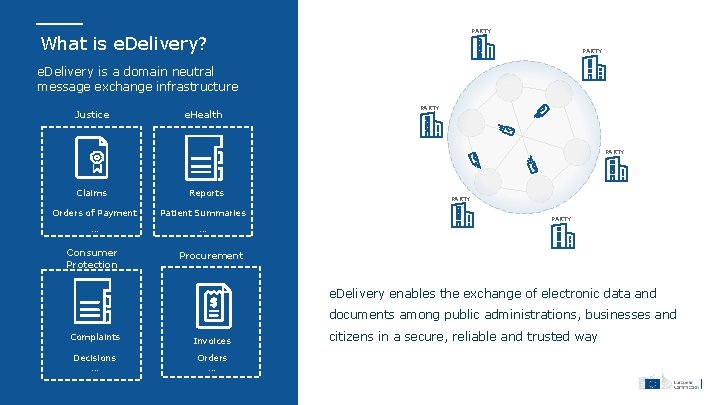
PARTY What is e. Delivery? PARTY e. Delivery is a domain neutral message exchange infrastructure Justice e. Health PARTY Claims Reports Orders of Payment Patient Summaries … … Consumer Protection PARTY Procurement e. Delivery enables the exchange of electronic data and documents among public administrations, businesses and Complaints Decisions … Invoices Orders … citizens in a secure, reliable and trusted way

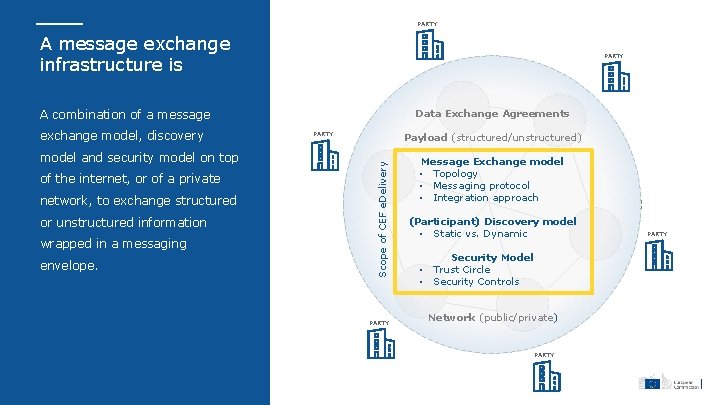
PARTY A message exchange infrastructure is PARTY A combination of a message model and security model on top of the internet, or of a private network, to exchange structured or unstructured information wrapped in a messaging envelope. PARTY Payload (structured/unstructured) Scope of CEF e. Delivery exchange model, discovery Data Exchange Agreements PARTY Message Exchange model • Topology • Messaging protocol • Integration approach (Participant) Discovery model • Static vs. Dynamic • • Security Model Trust Circle Security Controls Network (public/private) PARTY

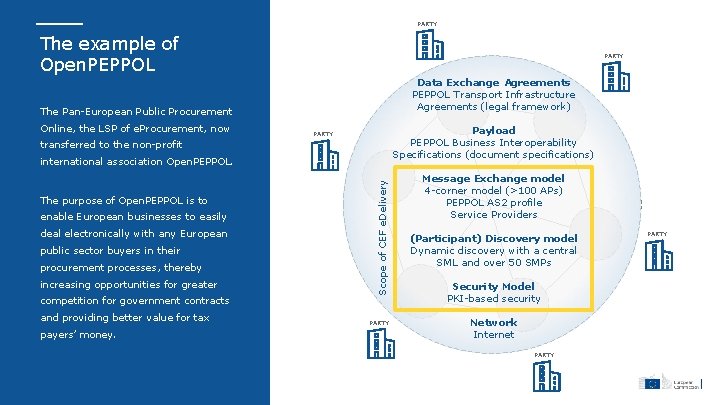
PARTY The example of Open. PEPPOL PARTY Data Exchange Agreements PEPPOL Transport Infrastructure Agreements (legal framework) The Pan-European Public Procurement Online, the LSP of e. Procurement, now Payload PEPPOL Business Interoperability Specifications (document specifications) PARTY transferred to the non-profit The purpose of Open. PEPPOL is to enable European businesses to easily deal electronically with any European public sector buyers in their procurement processes, thereby increasing opportunities for greater competition for government contracts and providing better value for tax payers’ money. Scope of CEF e. Delivery international association Open. PEPPOL. PARTY Message Exchange model 4 -corner model (>100 APs) PEPPOL AS 2 profile Service Providers (Participant) Discovery model Dynamic discovery with a central SML and over 50 SMPs Security Model PKI-based security Network Internet PARTY

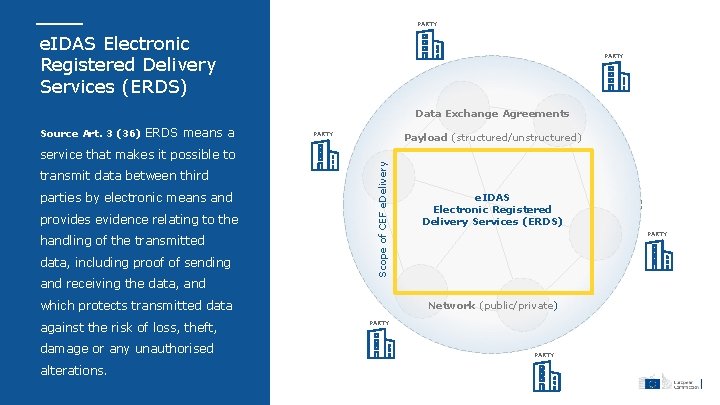
PARTY e. IDAS Electronic Registered Delivery Services (ERDS) PARTY Data Exchange Agreements Source Art. 3 (36) ERDS means a PARTY Payload (structured/unstructured) transmit data between third parties by electronic means and provides evidence relating to the handling of the transmitted data, including proof of sending and receiving the data, and Scope of CEF e. Delivery service that makes it possible to which protects transmitted data against the risk of loss, theft, damage or any unauthorised alterations. e. IDAS Electronic Registered Delivery Services (ERDS) PARTY Network (public/private) PARTY

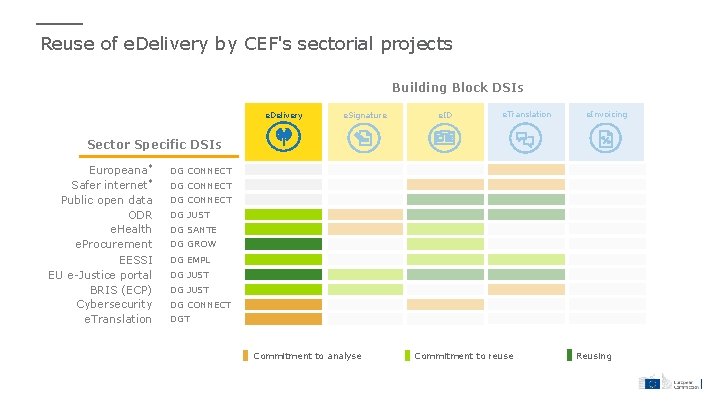
Reuse of e. Delivery by CEF's sectorial projects Building Block DSIs e. Delivery e. Signature e. ID e. Translation e. Invoicing Sector Specific DSIs Europeana* Safer internet* Public open data ODR e. Health e. Procurement EESSI EU e-Justice portal BRIS (ECP) Cybersecurity e. Translation DG CONNECT DG JUST DG SANTE DG GROW DG EMPL DG JUST DG CONNECT DGT Commitment to analyse Commitment to reuse Reusing

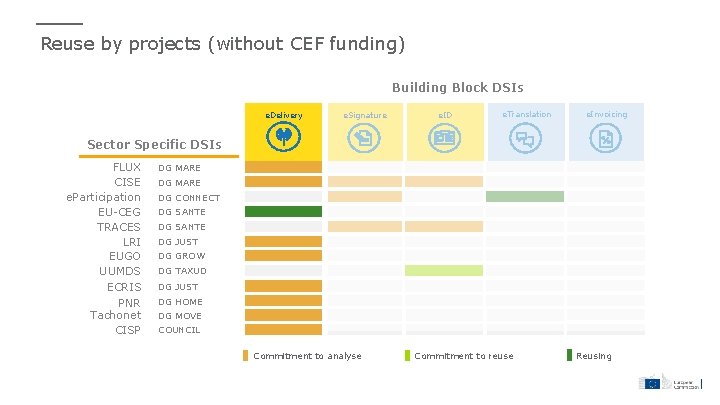
Reuse by projects (without CEF funding) Building Block DSIs e. Delivery e. Signature e. ID e. Translation e. Invoicing Sector Specific DSIs FLUX CISE e. Participation EU-CEG TRACES LRI EUGO UUMDS ECRIS PNR Tachonet CISP DG MARE DG CONNECT DG SANTE DG JUST DG GROW DG TAXUD DG JUST DG HOME DG MOVE COUNCIL Commitment to analyse Commitment to reuse Reusing

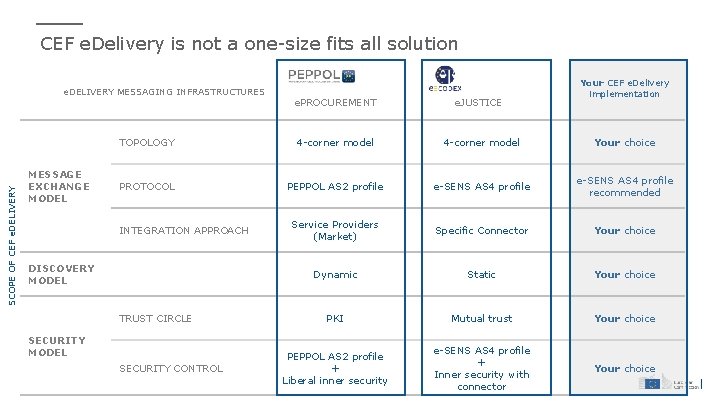
CEF e. Delivery is not a one-size fits all solution SCOPE OF CEF e. DELIVERY MESSAGING INFRASTRUCTURES MESSAGE EXCHANGE MODEL e. PROCUREMENT e. JUSTICE Your CEF e. Delivery implementation TOPOLOGY 4 -corner model Your choice PROTOCOL PEPPOL AS 2 profile e-SENS AS 4 profile recommended Service Providers (Market) Specific Connector Your choice Dynamic Static Your choice PKI Mutual trust Your choice PEPPOL AS 2 profile + Liberal inner security e-SENS AS 4 profile + Inner security with connector Your choice INTEGRATION APPROACH DISCOVERY MODEL TRUST CIRCLE SECURITY MODEL SECURITY CONTROL

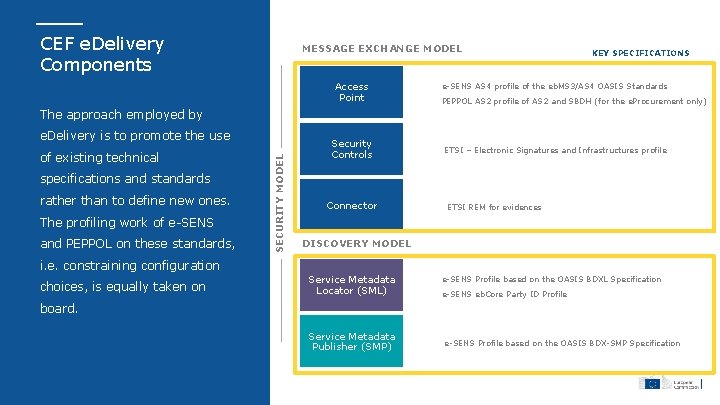
CEF e. Delivery Components MESSAGE EXCHANGE MODEL Access Point KEY SPECIFICATIONS Ø e-SENS AS 4 profile of the eb. MS 3/AS 4 OASIS Standards Ø PEPPOL AS 2 profile of AS 2 and SBDH (for the e. Procurement only) The approach employed by of existing technical specifications and standards rather than to define new ones. The profiling work of e-SENS and PEPPOL on these standards, SECURITY MODEL e. Delivery is to promote the use Security Controls Ø ETSI – Electronic Signatures and Infrastructures profile Connector Ø ETSI REM for evidences DISCOVERY MODEL i. e. constraining configuration choices, is equally taken on Service Metadata Locator (SML) Ø e-SENS Profile based on the OASIS BDXL Specification Ø e-SENS eb. Core Party ID Profile board. Service Metadata Publisher (SMP) Ø e-SENS Profile based on the OASIS BDX-SMP Specification

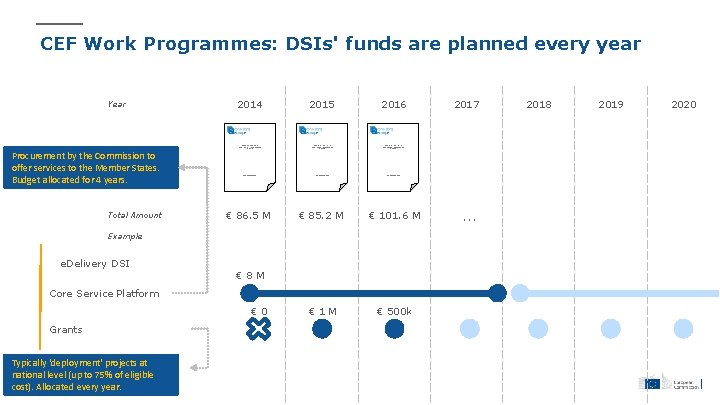
CEF Work Programmes: DSIs' funds are planned every year Year Procurement by the Commission to offer services to the Member States. Budget allocated for 4 years. Total Amount 2014 2015 2016 CONNECTING EUROPE FACILITY TRANS-EUROPEAN TELECOMMUNICATIONS NETWORKS WORK PROGRAMME 201 X € 86. 5 M € 85. 2 M € 101. 6 M € 1 M € 500 k Example e. Delivery DSI € 8 M Core Service Platform € 0 Grants Typically 'deployment' projects at … national level (up to 75% of eligible cost). Allocated every year. 2017 . . . 2018 2019 2020

Y 2 e. Delivery and e. IDAS ERDS in practice

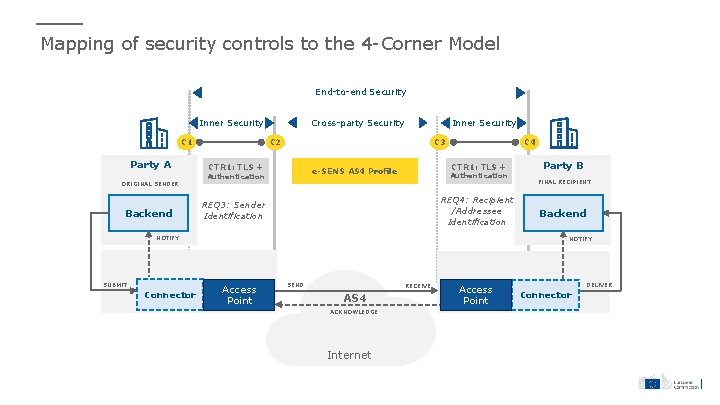
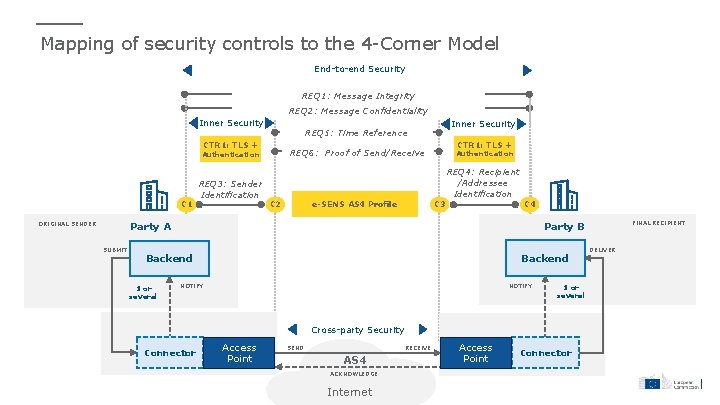
Mapping of security controls to the 4 -Corner Model End-to-end Security Inner Security C 1 Party A ORIGINAL SENDER Backend Cross-party Security Inner Security C 2 C 3 CTR 1: TLS + e-SENS AS 4 Profile Authentication C 4 Authentication REQ 4: Recipient /Addressee Identification REQ 3: Sender Identification NOTIFY SUBMIT Connector Party B FINAL RECIPIENT Backend NOTIFY Access Point SEND RECEIVE AS 4 ACKNOWLEDGE Internet Access Point DELIVER Connector

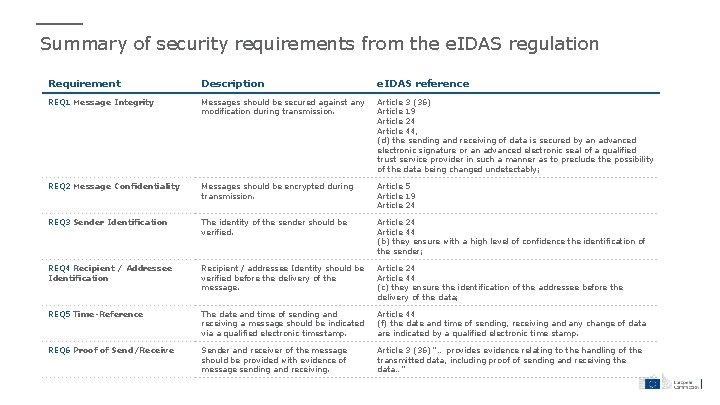
Summary of security requirements from the e. IDAS regulation Requirement Description e. IDAS reference REQ 1 Message Integrity Messages should be secured against any modification during transmission. Article 3 (36) Article 19 Article 24 Article 44, (d) the sending and receiving of data is secured by an advanced electronic signature or an advanced electronic seal of a qualified trust service provider in such a manner as to preclude the possibility of the data being changed undetectably; REQ 2 Message Confidentiality Messages should be encrypted during transmission. Article 5 Article 19 Article 24 REQ 3 Sender Identification The identity of the sender should be verified. Article 24 Article 44 (b) they ensure with a high level of confidence the identification of the sender; REQ 4 Recipient / Addressee Identification Recipient / addressee Identity should be verified before the delivery of the message. Article 24 Article 44 (c) they ensure the identification of the addressee before the delivery of the data; REQ 5 Time-Reference The date and time of sending and receiving a message should be indicated via a qualified electronic timestamp. Article 44 (f) the date and time of sending, receiving and any change of data are indicated by a qualified electronic time stamp. REQ 6 Proof of Send/Receive Sender and receiver of the message should be provided with evidence of message sending and receiving. Article 3 (36) “… provides evidence relating to the handling of the transmitted data, including proof of sending and receiving the data…”

Mapping of security controls to the 4 -Corner Model End-to-end Security REQ 1: Message Integrity REQ 2: Message Confidentiality Inner Security CTR 1: TLS + C 1 ORIGINAL SENDER CTR 1: TLS + REQ 6: Proof of Send/Receive Authentication REQ 3: Sender Identification Inner Security REQ 5: Time Reference Authentication REQ 4: Recipient /Addressee Identification e-SENS AS 4 Profile C 2 C 3 C 4 Party A SUBMIT NOTIFY Backend 1 or several FINAL RECIPIENT Party B NOTIFY 1 or several Cross-party Security Connector Access Point SEND RECEIVE AS 4 ACKNOWLEDGE Internet Access Point Connector DELIVER

Y 3 PEPPOL and CEF e. Delivery Convergence Process

e. Delivery alignment between CEF and PEPPOL Timeline 2017 2018 2019 20 xx Q 4 2016 T 1: Lo. U Q 4 2017 T 2: Phase In T 3: Transition TBD T 4: Phase Out Milestones AS 4 adopted as optional protocol (AS 2 Mandatory) ~Q 1 2019 Announcement of T 3 AS 4 Mandatory (AS 2 Optional) Only AS 4 • 2 c-s • 4 a-d • 3 e Criteria • 3 a Example: There exists a stable, well documented CEF AS 4 profile specification, including SMP and PKI implementation. • • 1 a-c 2 a-b 3 b-c 5 a-d

Find out more on CEF Digital DIGIT Directorate-General for Informatics DG CONNECT Directorate-General for Communications Networks, Content and Technology Contact us CEF-BUILDING-BLOCKS@ec. europa. eu/cefdigital © European Union, 2016. All rights reserved. Certain parts are licensed under conditions to the EU. Reproduction is authorized provided the source is acknowledged.