Dynamic Authentication of Typing Patterns Luke Knepper Introduction





- Slides: 13

Dynamic Authentication of Typing Patterns Luke Knepper

Introduction Passwords are outdated Many biometrics are expensive Typing patterns differ by person People can be authenticated by their typing patterns Cheap and flexible to implement

Agenda Background Final Process Experimentation Current Results Goals

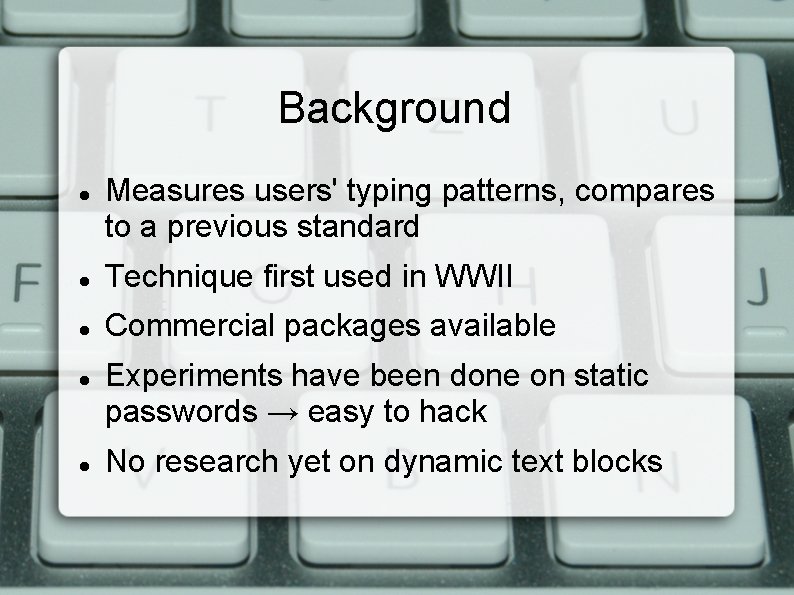
Background Measures users' typing patterns, compares to a previous standard Technique first used in WWII Commercial packages available Experiments have been done on static passwords → easy to hack No research yet on dynamic text blocks

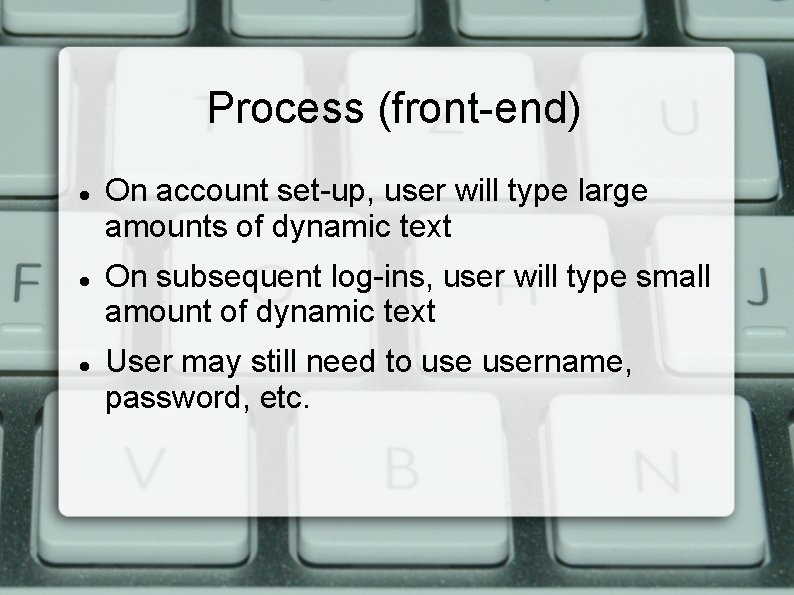
Process (front-end) On account set-up, user will type large amounts of dynamic text On subsequent log-ins, user will type small amount of dynamic text User may still need to username, password, etc.

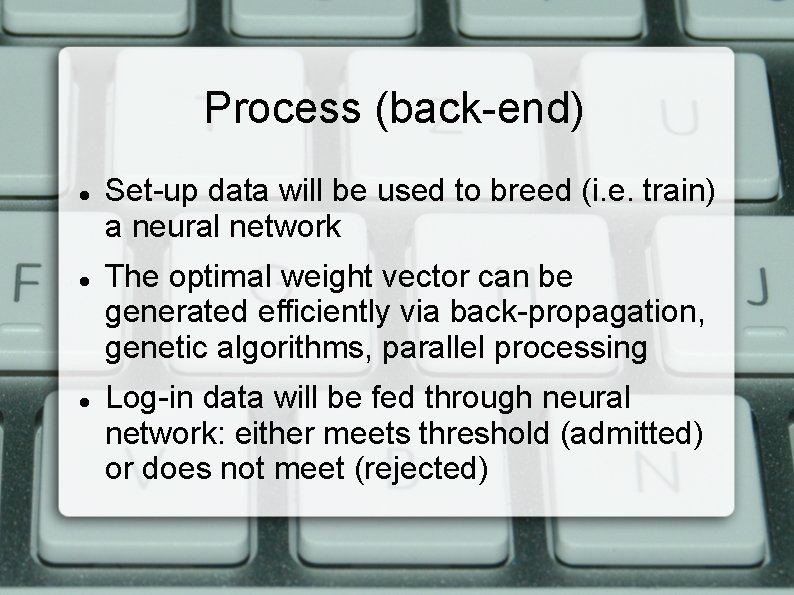
Process (back-end) Set-up data will be used to breed (i. e. train) a neural network The optimal weight vector can be generated efficiently via back-propagation, genetic algorithms, parallel processing Log-in data will be fed through neural network: either meets threshold (admitted) or does not meet (rejected)

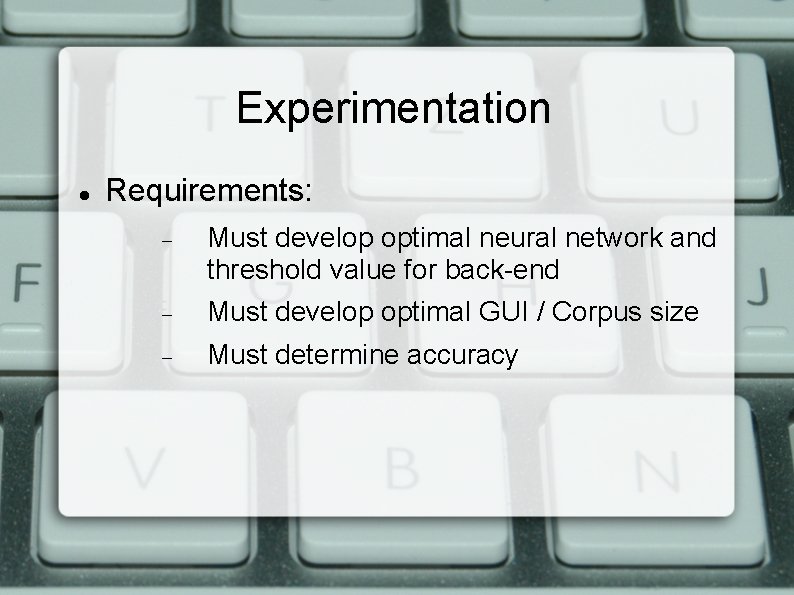
Experimentation Requirements: Must develop optimal neural network and threshold value for back-end Must develop optimal GUI / Corpus size Must determine accuracy

Experimentation Neural Network Optimization: 1. Develop online data collection applet 2. Collect massive amounts of data 3. Use data to train multiple neural network types 4. Test different network types to determine optimal network and threshold

Experimentation GUI / Corpus Optimization: 1. Collect ~20 test subjects 2. Have them set up dummy accounts 3. Subjects attempt to log into their accounts and accounts of others 4. Repeat for different GUI layouts, corpus sizes

Experimentation Accuracy Testing: 1. Collect large number of test subjects 2. Subjects set up dummy accounts 3. Subjects attempt to log into their accounts and accounts of others on subsequent sittings (spaced out by 1 week and 1 month) 4. Measure final accuracy

Current Results Proof-of-concept program Determines the mystery typer between two known users Uses simple single-layer neural network Correct 18 / 20 = 90%

Goals Final program will be: Easily implementable Difficult to crack Accurate above 90% Will be combined with password security to make inexpensive and secure system

Fin Who wants a cookie?