Duke Systems Authorization Framework Status Jeff Chase Duke





- Slides: 16

Duke Systems Authorization Framework: Status Jeff Chase Duke University

ABAC in GENI • ABAC is a powerful declarative representation that can capture the GENI authorization/trust model. • It saves a lot of code, provides a rigorous foundation, and preserves flexibility for future innovation. • It should be easy for users, although we need some better tools there. (E. g. , to delegate rights. ) • Libabac “works off the shelf” (RT 0 does. . . RT 2 too) • In progress: policies for safe operational deployment. • New http: //groups. geni. net/geni/wiki/Auth. Story. Board GEC-12 Auth Session

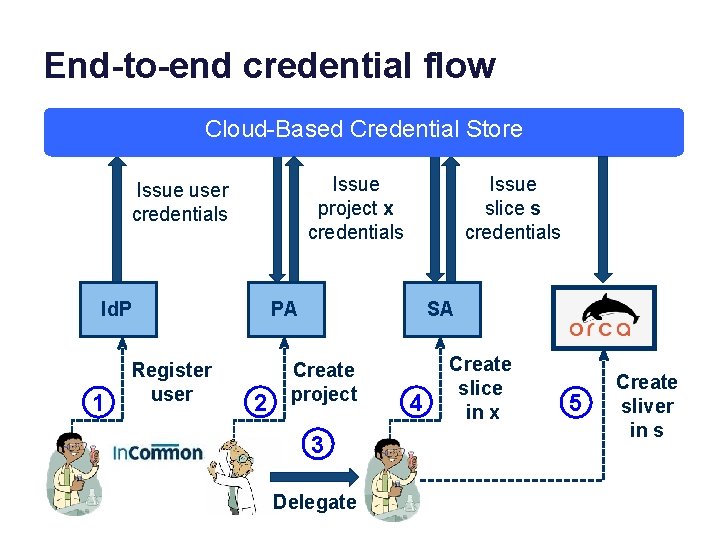
End-to-end credential flow Cloud-Based Credential Store Issue project x credentials Issue user credentials Id. P 1 Register user Issue slice s credentials PA 2 SA Create project 3 Delegate 4 Create slice in x 5 Create sliver in s

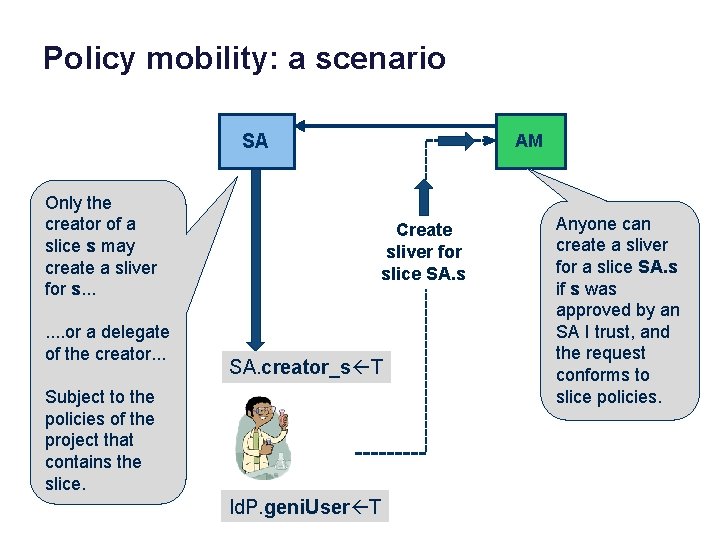
Policy mobility: a scenario SA Only the creator of a slice s may create a sliver for s. . . . or a delegate of the creator. . . AM Create sliver for slice SA. s SA. creator_s T Subject to the policies of the project that contains the slice. Id. P. geni. User T Anyone can create a sliver for a slice SA. s if s was approved by an SA I trust, and the request conforms to slice policies.

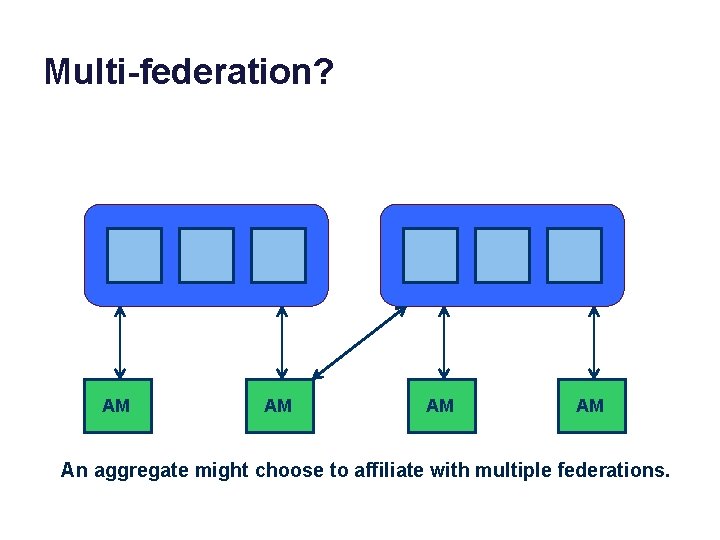
Multi-federation? AM AM An aggregate might choose to affiliate with multiple federations.

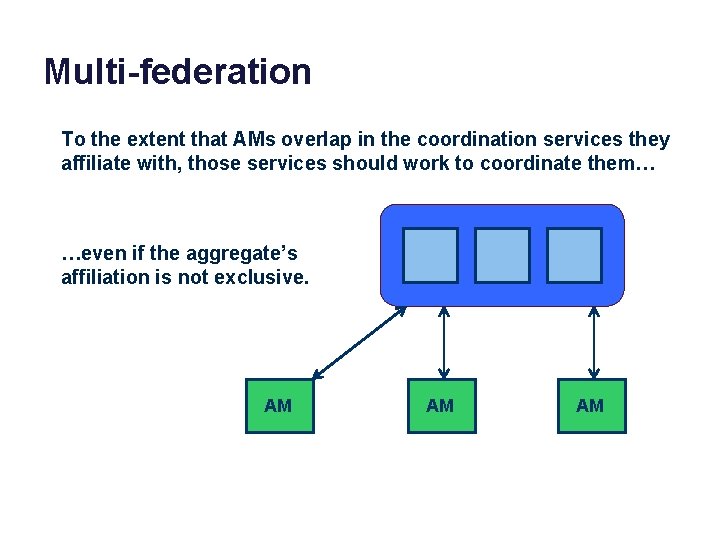
Multi-federation To the extent that AMs overlap in the coordination services they affiliate with, those services should work to coordinate them… …even if the aggregate’s affiliation is not exclusive. AM AM AM

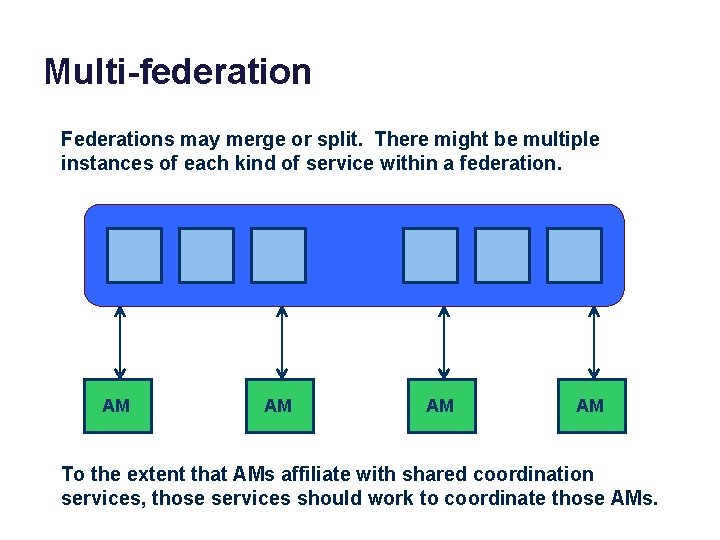
Multi-federation Federations may merge or split. There might be multiple instances of each kind of service within a federation. AM AM To the extent that AMs affiliate with shared coordination services, those services should work to coordinate those AMs.

I stopped there. . . the rest is background.

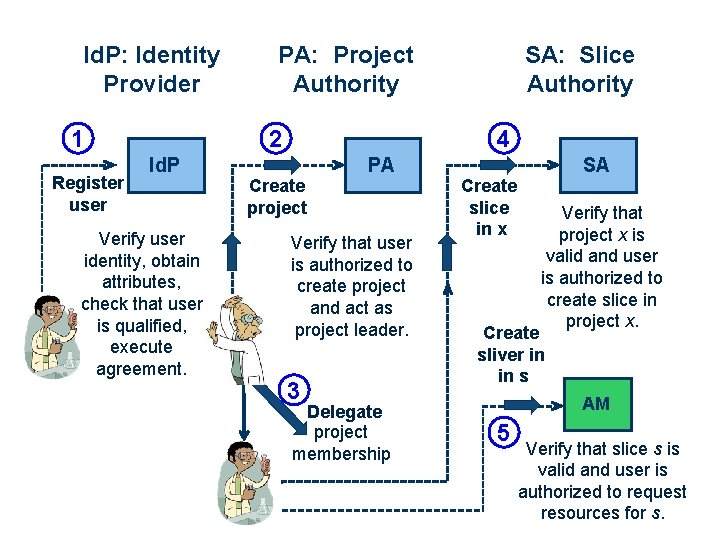
Id. P: Identity Provider 1 Register user PA: Project Authority 2 4 Id. P Verify user identity, obtain attributes, check that user is qualified, execute agreement. SA: Slice Authority PA Create project Verify that user is authorized to create project and act as project leader. 3 Delegate project membership SA Create slice in x Verify that project x is valid and user is authorized to create slice in project x. Create sliver in in s AM 5 Verify that slice s is valid and user is authorized to request resources for s.

It’s all about credential flow 1 2 Register user 4 Id. P PA Create project Project x created user registered Issue user credentials Issue project credentials SA Create slice in x Slice s created Issue slice credentials 3 Delegate project credentials AM Create sliver in in s 5

Policy mobility: a scenario SA Only the creator of a slice s may create a sliver for s. . . . or a delegate of the creator. . . AM Create sliver for slice SA. s SA. creator_s T Subject to the policies of the project that contains the slice. Id. P. geni. User T Anyone can create a sliver for a slice SA. s if s was approved by an SA I trust, and the request conforms to slice policies.

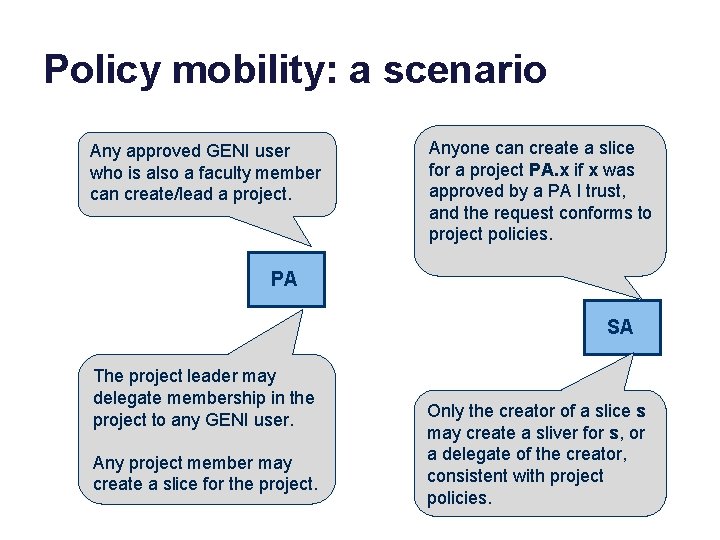
Policy mobility: a scenario Any approved GENI user who is also a faculty member can create/lead a project. Anyone can create a slice for a project PA. x if x was approved by a PA I trust, and the request conforms to project policies. PA SA The project leader may delegate membership in the project to any GENI user. Any project member may create a slice for the project. Only the creator of a slice s may create a sliver for s, or a delegate of the creator, consistent with project policies.

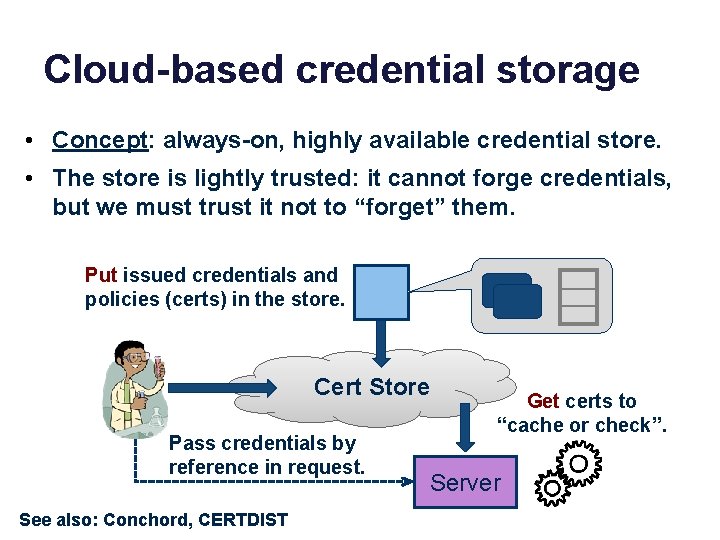
Cloud-based credential storage • Concept: always-on, highly available credential store. • The store is lightly trusted: it cannot forge credentials, but we must trust it not to “forget” them. Put issued credentials and policies (certs) in the store. Cert Store Pass credentials by reference in request. See also: Conchord, CERTDIST Get certs to “cache or check”. Server

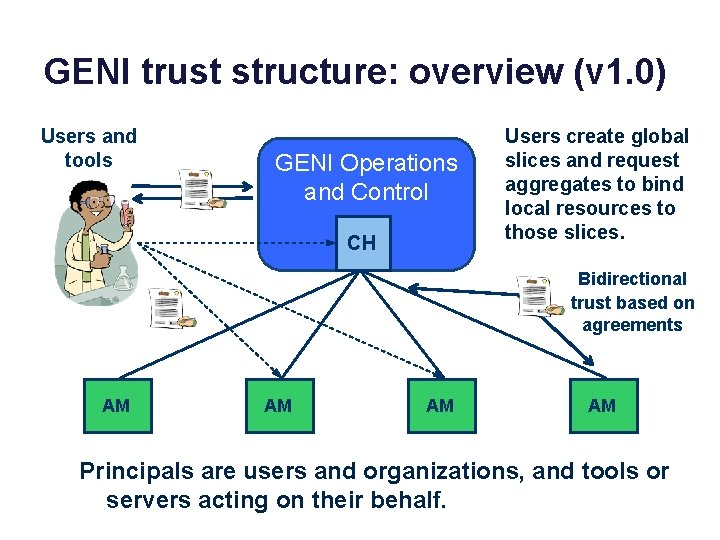
GENI trust structure: overview (v 1. 0) Users and tools GENI Operations and Control CH Users create global slices and request aggregates to bind local resources to those slices. Bidirectional trust based on agreements AM AM Principals are users and organizations, and tools or servers acting on their behalf.

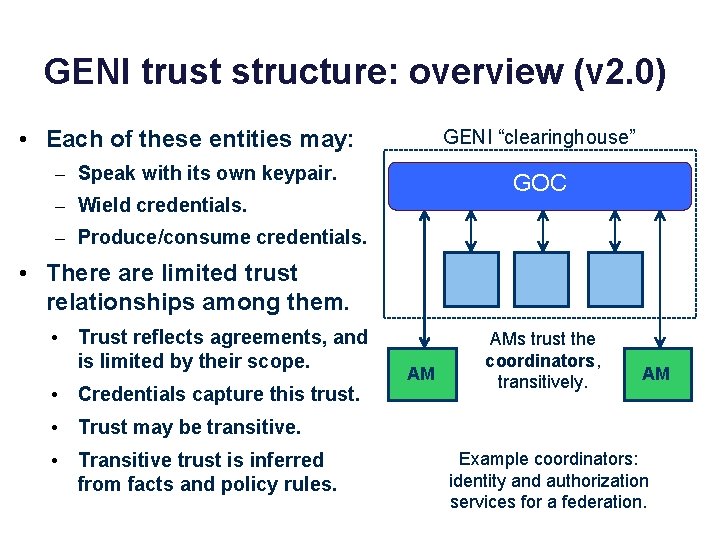
GENI trust structure: overview (v 2. 0) • Each of these entities may: GENI “clearinghouse” – Speak with its own keypair. GOC – Wield credentials. – Produce/consume credentials. • There are limited trust relationships among them. • Trust reflects agreements, and is limited by their scope. • Credentials capture this trust. GMOC AM AMs trust the coordinators, transitively. I&M AM • Trust may be transitive. • Transitive trust is inferred from facts and policy rules. Example coordinators: identity and authorization services for a federation.

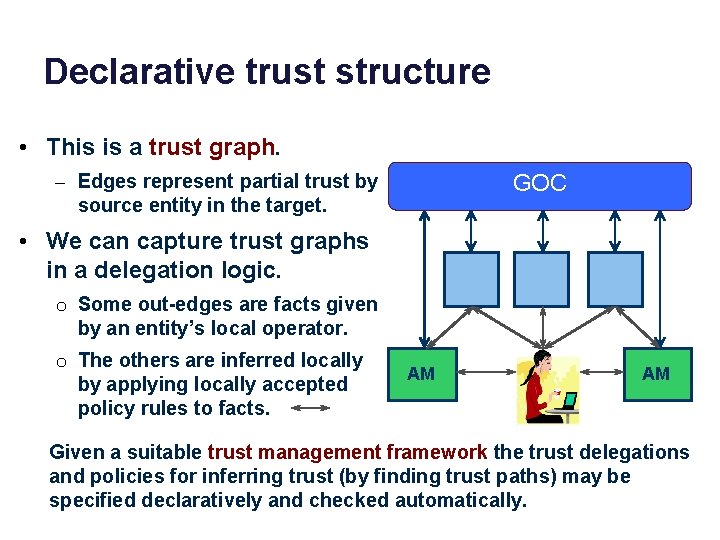
Declarative trust structure • This is a trust graph. GOC – Edges represent partial trust by source entity in the target. • We can capture trust graphs in a delegation logic. GMOC I&M o Some out-edges are facts given by an entity’s local operator. o The others are inferred locally by applying locally accepted policy rules to facts. AM AM Given a suitable trust management framework the trust delegations and policies for inferring trust (by finding trust paths) may be specified declaratively and checked automatically.