Duke Systems Android Simplified Jeff Chase Duke University









![Virtual Machine (JVM) C/C++ [http: //www. android. com] Virtual Machine (JVM) C/C++ [http: //www. android. com]](https://slidetodoc.com/presentation_image_h/d0f28a01c9a96ec13287b75a0b779ba1/image-16.jpg)







- Slides: 40

Duke Systems Android (Simplified) Jeff Chase Duke University

Part 1: Background


From Bloomberg Krall and General Counsel Bruce Sewell have amassed a team of lawyers from inside Apple and some of the top U. S. law firms to fight Samsung, HTC, and Google’s Motorola Mobility unit over Google’s Android mobile operating system and the smartphones and tablets that run on it. The fight is central to Apple’s identity…it got 46. 4 percent of its sales from the i. Phone last quarter and 26 percent from the i. Pad. The i. Phone generated $47 billion in sales last fiscal year…. Apple and Samsung together make more than half of the smartphones sold in the world. Samsung is the biggest player in the global market and Apple is dominant in the U. S. The companies are vying for …a market that …grew 62 percent to $219 B…


“Conspiracy theory”?

Leading tech companies are filled with good system builders with vision, strong principles, and a commitment to technological purity. Others in the company focus on market strategy and tactics. By US law their commitment to profits for the company’s owners dominates other values. Good system builders learn to understand the social, legal, and market context for their work. Technology choices are always intertwined with market structure and strategic concerns.

Unix, looking backward: UI+IPC • Conceived around keystrokes and byte streams – User-visible environment is centered on a text-based command shell. • Limited view of how programs interact – files: byte streams in a shared name space – pipes: byte streams between pairs of sibling processes

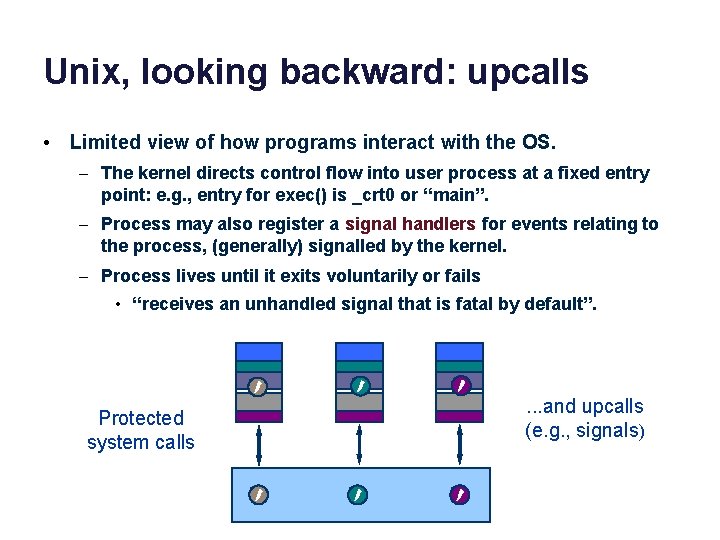
Unix, looking backward: upcalls • Limited view of how programs interact with the OS. – The kernel directs control flow into user process at a fixed entry point: e. g. , entry for exec() is _crt 0 or “main”. – Process may also register a signal handlers for events relating to the process, (generally) signalled by the kernel. – Process lives until it exits voluntarily or fails • “receives an unhandled signal that is fatal by default”. data Protected system calls data . . . and upcalls (e. g. , signals)

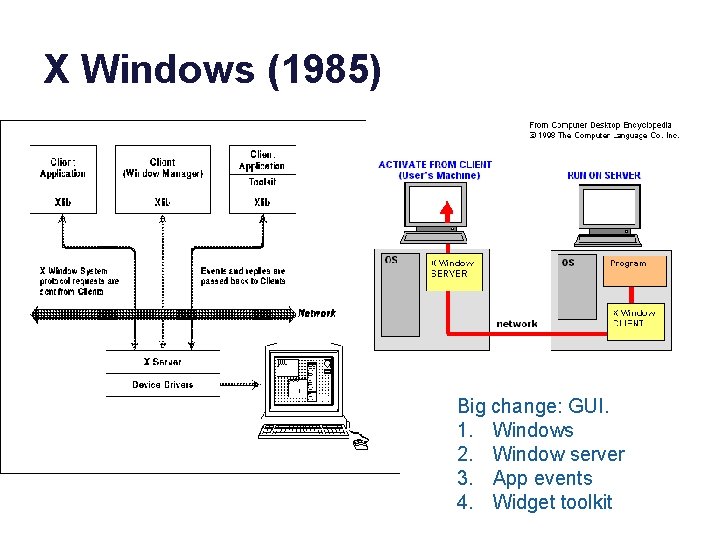
X Windows (1985) Big change: GUI. 1. Windows 2. Window server 3. App events 4. Widget toolkit

Unix, looking backward: security • Presumes multiple users sharing a machine. • Each user has a user. ID. – User. ID owns all files created by all programs user runs. – Any program can access any file owned by user. ID. • Each user trusts all programs it chooses to run. – We “deputize” every program. – Some deputies get confused. – Result: decades of confused deputy security problems. • Contrary view: give programs the privileges they need, and nothing more. – Principle of Least Privilege

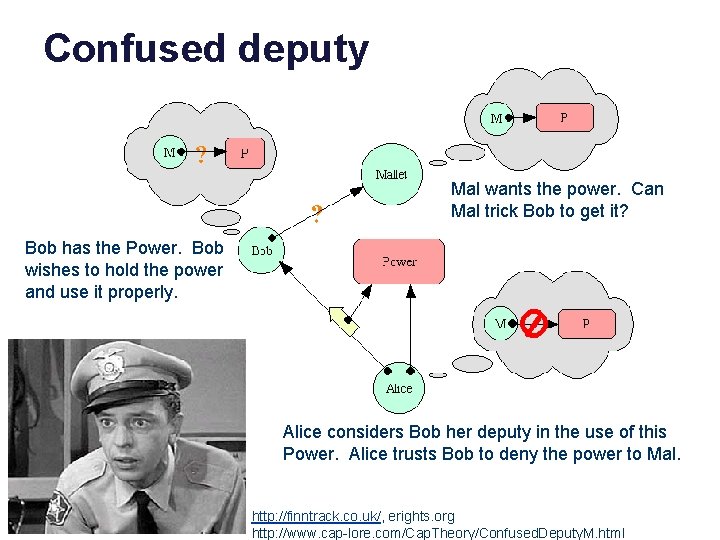
Confused deputy Mal wants the power. Can Mal trick Bob to get it? Bob has the Power. Bob wishes to hold the power and use it properly. Alice considers Bob her deputy in the use of this Power. Alice trusts Bob to deny the power to Mal. http: //finntrack. co. uk/, erights. org http: //www. cap-lore. com/Cap. Theory/Confused. Deputy. M. html

Android protection • Each application (“app”) runs with its own identity. – Each app has a private space of files, processes, etc. that defines a “sandbox”. – It does not matter that they run on behalf of the same user: the code matters more than the user. No deputies! • The system mediates access to the sensors and UI by applications. – GPS, camera, microphone, touchpad, etc. • Each app declares the named permissions it needs. – subject to user approval • Each app declares the permissions another app needs to interact with it.


Part 2, Android technology • The goal here is to present an overview of the Android structure, and rationale for that structure. • We won’t learn how to program Android apps. Detailed docs are available. – developer. android. com • What we offer is the conceptual underpinnings and connections to other OS concepts. – We choose Android for its instructive value: open source. • Some images are borrowed from material on the web. E. g. , Google material: – Anatomy and Physiology of Android
![Virtual Machine JVM CC http www android com Virtual Machine (JVM) C/C++ [http: //www. android. com]](https://slidetodoc.com/presentation_image_h/d0f28a01c9a96ec13287b75a0b779ba1/image-16.jpg)
Virtual Machine (JVM) C/C++ [http: //www. android. com]

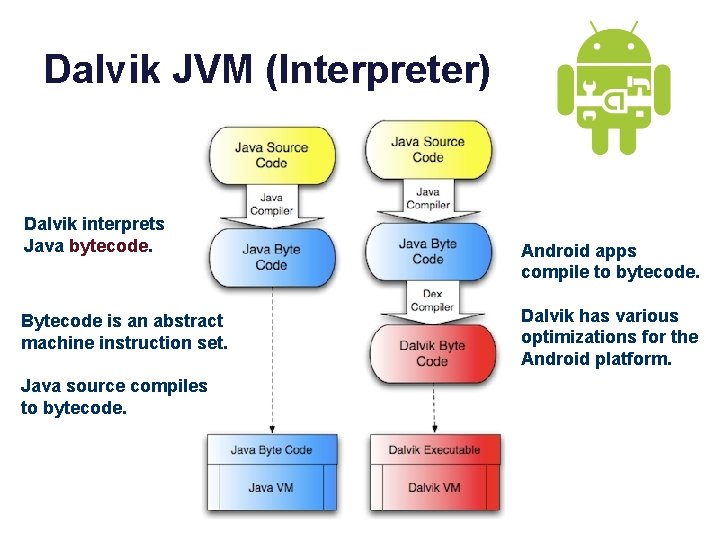
Dalvik JVM (Interpreter) Dalvik interprets Java bytecode. Bytecode is an abstract machine instruction set. Java source compiles to bytecode. Android apps compile to bytecode. Dalvik has various optimizations for the Android platform.

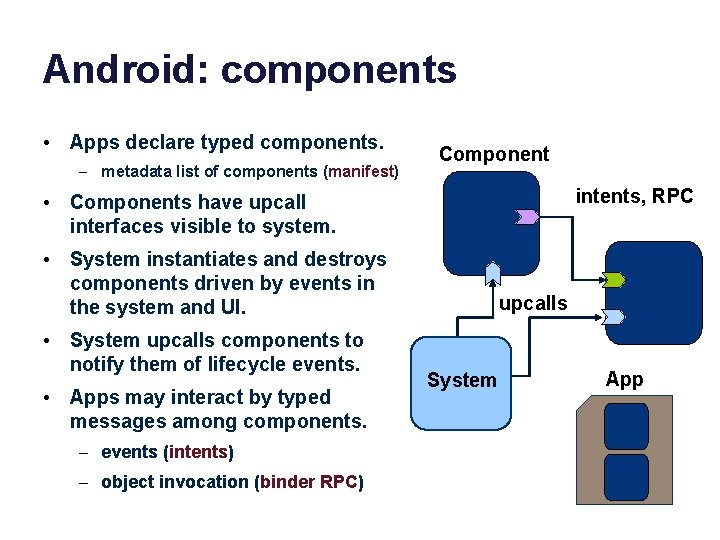
Android: components • Apps declare typed components. – metadata list of components (manifest) Component intents, RPC • Components have upcall interfaces visible to system. • System instantiates and destroys components driven by events in the system and UI. • System upcalls components to notify them of lifecycle events. • Apps may interact by typed messages among components. – events (intents) – object invocation (binder RPC) upcalls System App

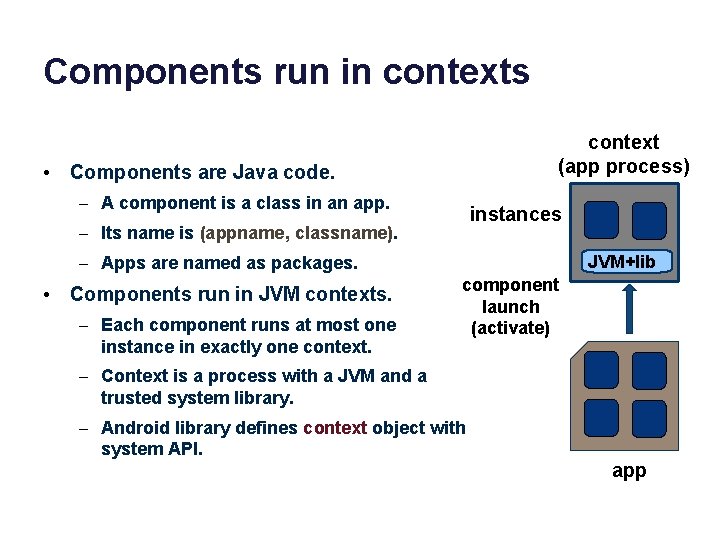
Components run in contexts context (app process) • Components are Java code. – A component is a class in an app. instances – Its name is (appname, classname). JVM+lib – Apps are named as packages. • Components run in JVM contexts. – Each component runs at most one instance in exactly one context. component launch (activate) – Context is a process with a JVM and a trusted system library. – Android library defines context object with system API. app

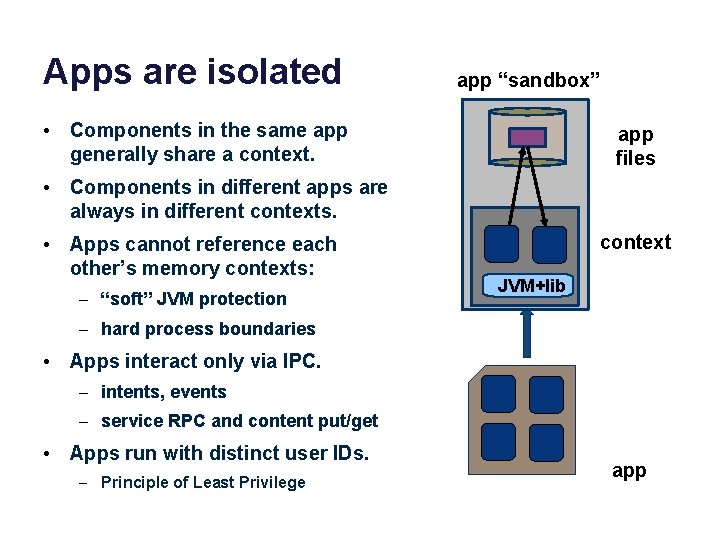
Apps are isolated app “sandbox” • Components in the same app generally share a context. app files • Components in different apps are always in different contexts. • Apps cannot reference each other’s memory contexts: – “soft” JVM protection context JVM+lib – hard process boundaries • Apps interact only via IPC. – intents, events – service RPC and content put/get • Apps run with distinct user IDs. – Principle of Least Privilege app

Component launch app context • To launch a component: – Select a JVM context to run it. – Tell JVM to instantiate the class. • System communicates with the context via its system library. • System obtains info about the component from app manifest. – Class component type: the component class descends from a system base class. – List of event profiles (intent filters) that trigger component launch System read manifest If there is no JVM context active for the component’s app, then the system must start one. JVM+lib load class manifest app

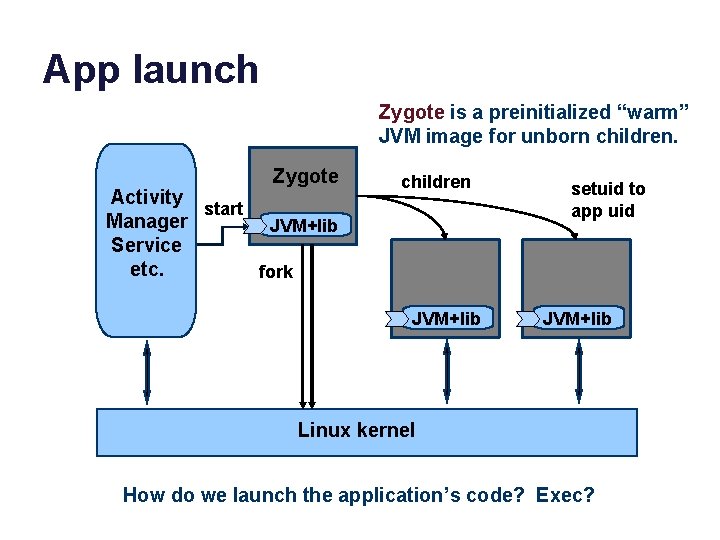
App launch Zygote is a preinitialized “warm” JVM image for unborn children. Zygote Activity start Manager JVM+lib Service etc. fork children JVM+lib setuid to app uid JVM+lib Linux kernel How do we launch the application’s code? Exec?

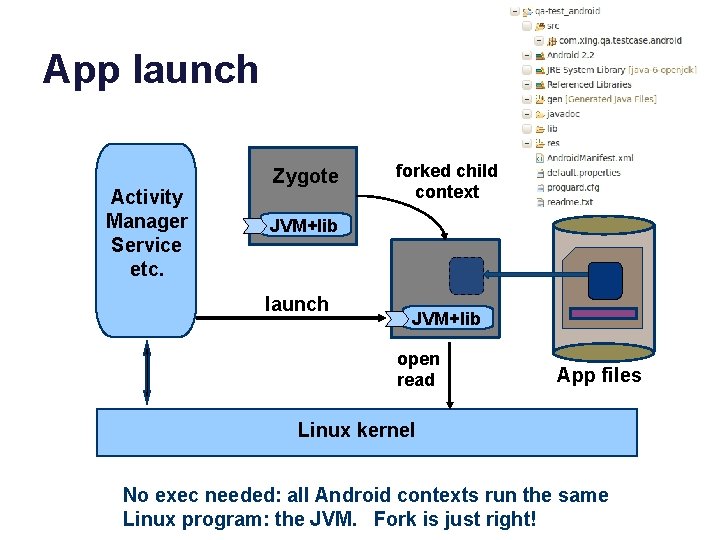
App launch Activity Manager Service etc. Zygote forked child context JVM+lib launch JVM+lib open read App files Linux kernel No exec needed: all Android contexts run the same Linux program: the JVM. Fork is just right!


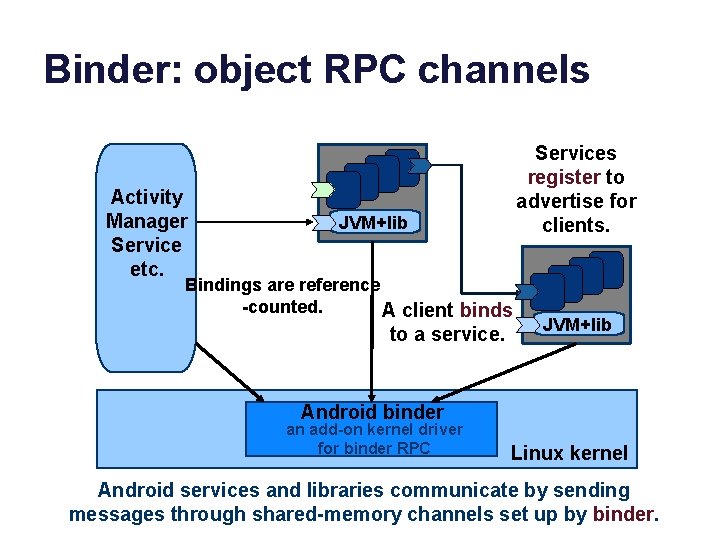
Binder: object RPC channels Activity Manager Service etc. Services register to advertise for clients. JVM+lib Bindings are reference -counted. A client binds to a service. JVM+lib Android binder an add-on kernel driver for binder RPC Linux kernel Android services and libraries communicate by sending messages through shared-memory channels set up by binder.

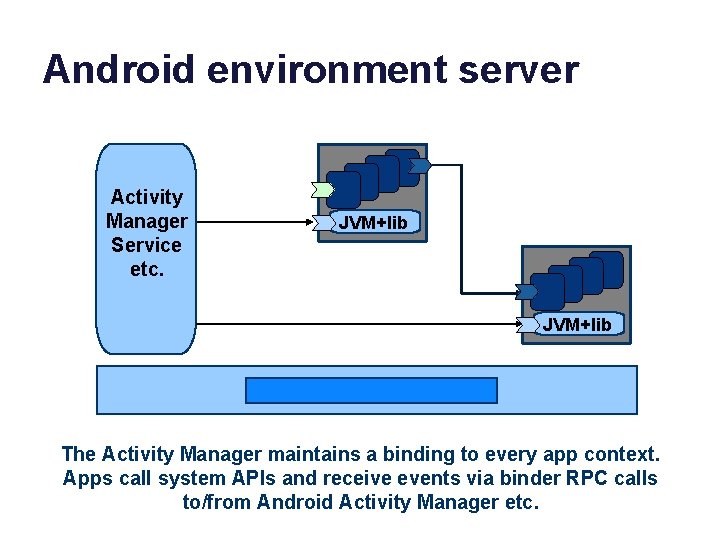
Android environment server Activity Manager Service etc. JVM+lib The Activity Manager maintains a binding to every app context. Apps call system APIs and receive events via binder RPC calls to/from Android Activity Manager etc.

Post-note • Zygote also forks a system service manager on system startup. • SM is a process that forks a lot of the basic Java android services. • SM looks for installed apps with binder services in the manifest, and starts those components. - They include daemons that listen to usb, audio etc. and send events

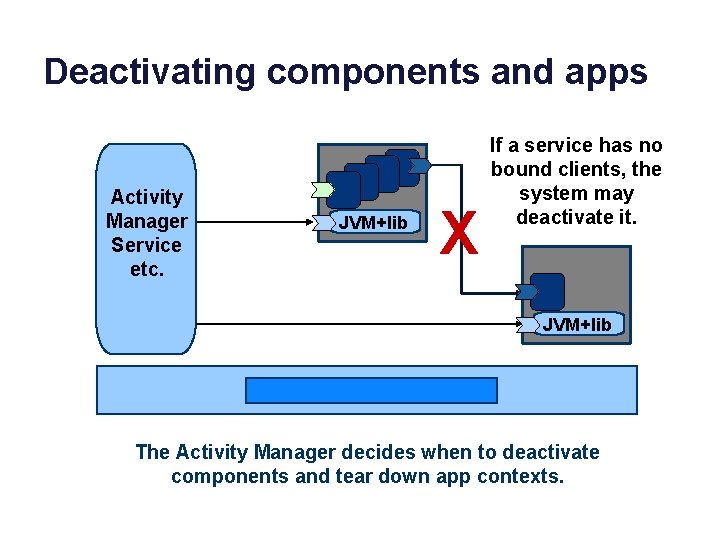
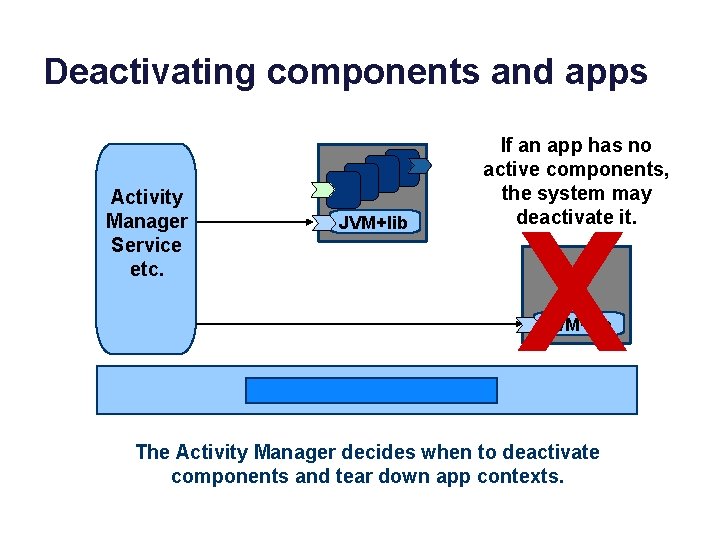
Deactivating components and apps Activity Manager Service etc. JVM+lib X If a service has no bound clients, the system may deactivate it. JVM+lib The Activity Manager decides when to deactivate components and tear down app contexts.

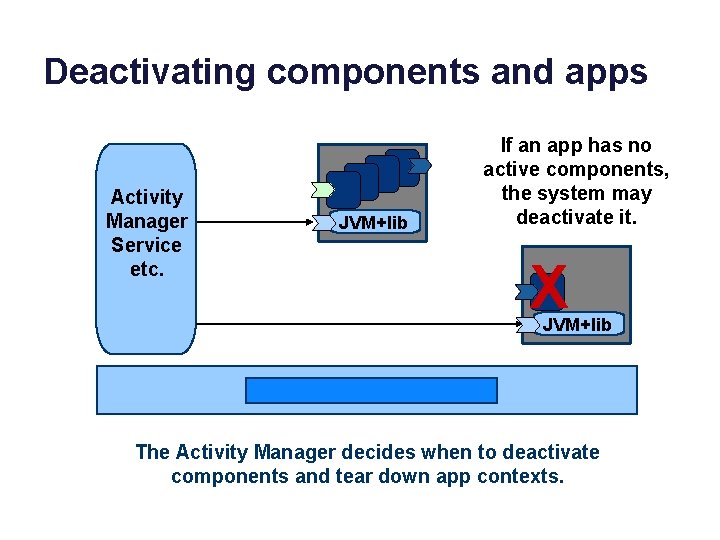
Deactivating components and apps Activity Manager Service etc. JVM+lib If an app has no active components, the system may deactivate it. X JVM+lib The Activity Manager decides when to deactivate components and tear down app contexts.

Deactivating components and apps Activity Manager Service etc. JVM+lib If an app has no active components, the system may deactivate it. X JVM+lib The Activity Manager decides when to deactivate components and tear down app contexts.

Deactivating components and apps Activity Manager Service etc. JVM+lib The user navigates with the screen and buttons, activating components and moving on. The components set up interactions among themselves as needed to serve the user. The system monitors activity and memory pressure and cleans up behind components as needed.

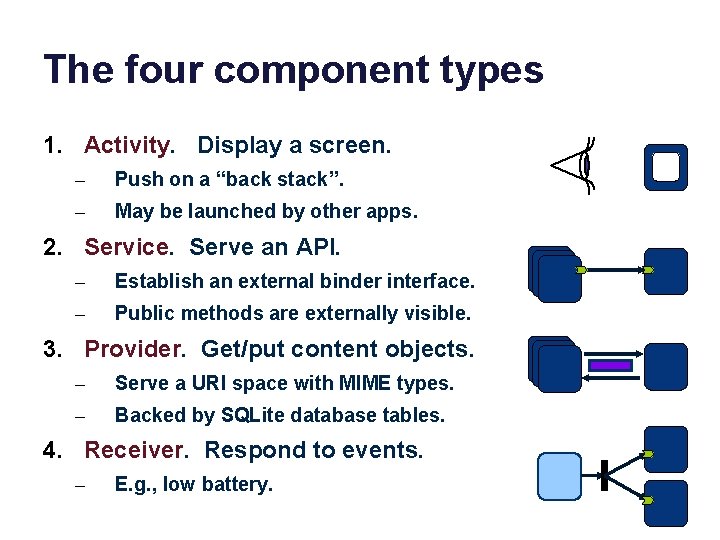
The four component types 1. Activity. Display a screen. – Push on a “back stack”. – May be launched by other apps. 2. Service. Serve an API. – Establish an external binder interface. – Public methods are externally visible. 3. Provider. Get/put content objects. – Serve a URI space with MIME types. – Backed by SQLite database tables. 4. Receiver. Respond to events. – E. g. , low battery.

Intents for activities and receivers • Intents are named events. – Components signal intents with various attributes and data. – They declare filters to specify which intents they may receive. – Filter specifies named permissions the sender must have. • A component may invoke an activity with an explicit intent, which invokes a named target component. • A component may broadcast an implicit intent for delivery to any interested receiver component. – Sender names permissions that each receiver must have. – The event may be sent to its receivers in order or in parallel. • See also: implicit vs. explicit invocation in Garlan/Shaw. – Explicit intents and ordered broadcasts may receive a result.

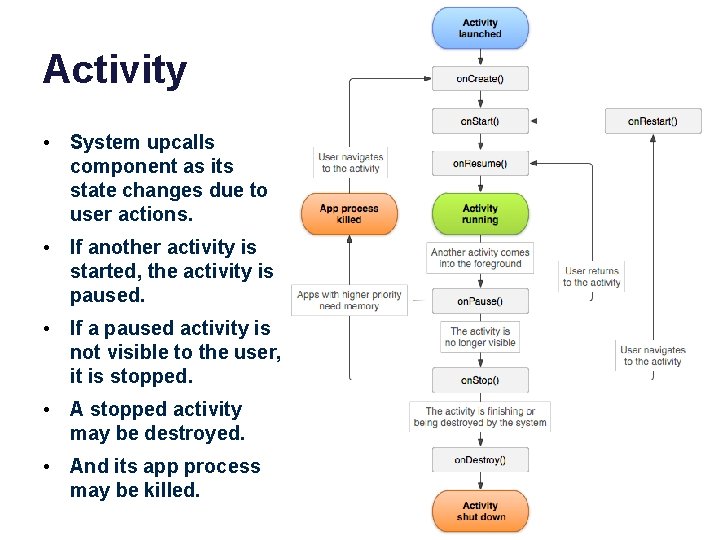
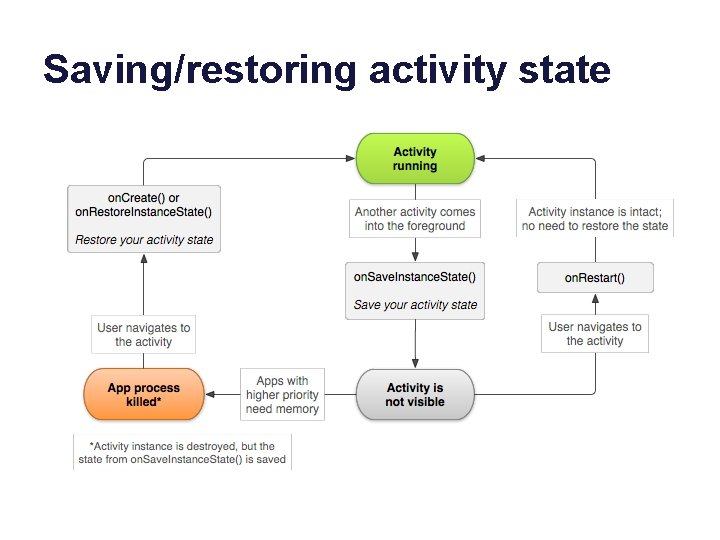
Post-note • We did not discuss the state diagrams on the following slides in any detail. • But understand that each executing component is a finite state machine. – States are defined by the component type. – Transitions are driven by UI events and/or other system or app events. – These events generate system upcalls or intents to the component, which change its state. – Components in certain states are eligible to be reclaimed by the system.

Activity • System upcalls component as its state changes due to user actions. • If another activity is started, the activity is paused. • If a paused activity is not visible to the user, it is stopped. • A stopped activity may be destroyed. • And its app process may be killed.

Saving/restoring activity state

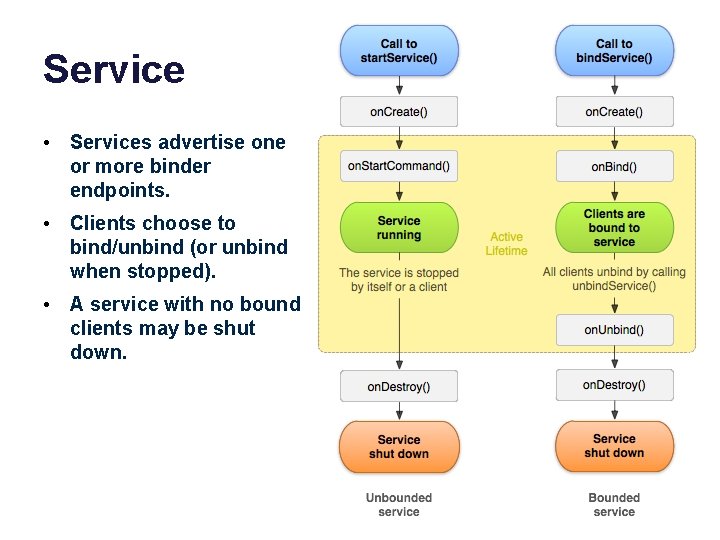
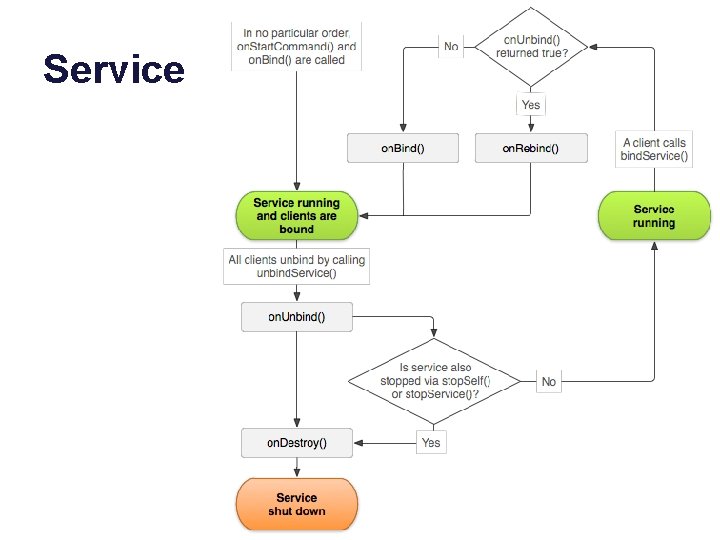
Service • Services advertise one or more binder endpoints. • Clients choose to bind/unbind (or unbind when stopped). • A service with no bound clients may be shut down.

Service

For later • Threading models and concurrency – Each app has a main thread (activity thread) that controls its UI and invokes the upcalls of its components as they are needed. Apps must never block the activity thread. – Components can create other threads in various ways. • Binder/RPC structure – Service threading/queue models and request handling – RPC data translation • Permission structure – An extensible namespace of permissions whose meaning is defined by system or by apps. For any interaction, both components define the permissions needed by the other.

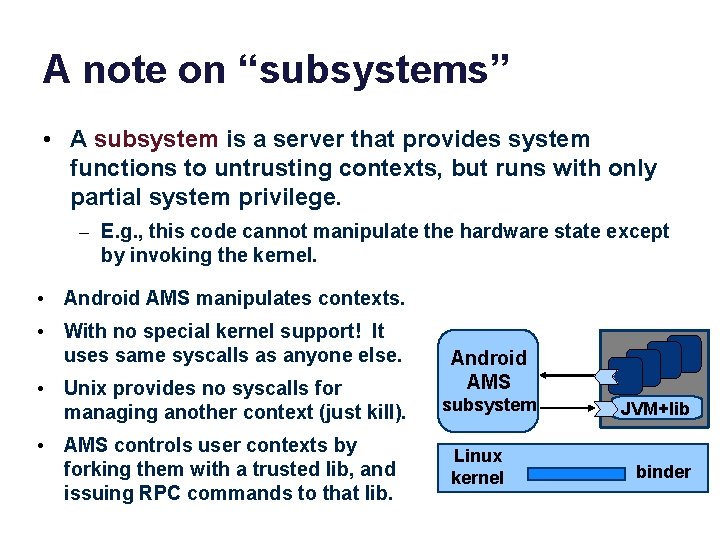
A note on “subsystems” • A subsystem is a server that provides system functions to untrusting contexts, but runs with only partial system privilege. – E. g. , this code cannot manipulate the hardware state except by invoking the kernel. • Android AMS manipulates contexts. • With no special kernel support! It uses same syscalls as anyone else. • Unix provides no syscalls for managing another context (just kill). • AMS controls user contexts by forking them with a trusted lib, and issuing RPC commands to that lib. Android AMS subsystem Linux kernel JVM+lib binder