Dude wheres that IP Circumventing measurementbased IP geolocation
Dude, where’s that IP? Circumventing measurement-based IP geolocation Paper Presentation CAP 6135: Malware and Software Vulnerability Analysis – Spring 2013 Omar Nakhila

Citation and acknowledgement • Gill, Phillipa, Yashar Ganjali, and Bernard Wong. "Dude, Where’s That IP? Circumventing Measurement-based IP Geolocation. " USENIX Security Symposium 19 th , Washington DC, August 1113, 2010. • http: //en. wikipedia. org/wiki/Speed_of_electricity 2

Presentation Agenda • • 3 What is IP geolocation? Why IP geolocation? IP geolocation classification and attacks. Paper contribution. Paper weakness. Paper improvement. Questions and answers.

What is IP geolocation? • IP geolocation aims to solve the problem of determining the geographic location of a given IP address. 4

Presentation Agenda • • 5 What is IP geolocation? Why IP geolocation? IP geolocation classification and attacks. Paper contribution. Paper weakness. Paper improvement. Questions and answers.

Why IP geolocation? • Online advertisers and search engines advertise their content based on the client’s location. 6

Why IP geolocation? Cont. • Online content providers such as : – Hulu. – Youtube – etc. limit their content distribution to specific geographic regions. 7

Why IP geolocation? Cont. • Law enforcement. 9

Presentation Agenda • • 10 What is IP geolocation? Why IP geolocation? IP geolocation classification and attacks. Paper contribution. Paper weakness. Paper improvement. Questions and answers.
IP geolocation classification • Passive IP geolocation. – Ueses geolocation databases such as : • Max. Mind. • Quova. • Active IP geolocation. – Delay-based. • Constraint-Based Geolocation (CBG) – Topology-aware. • Octant. 11 – Other.
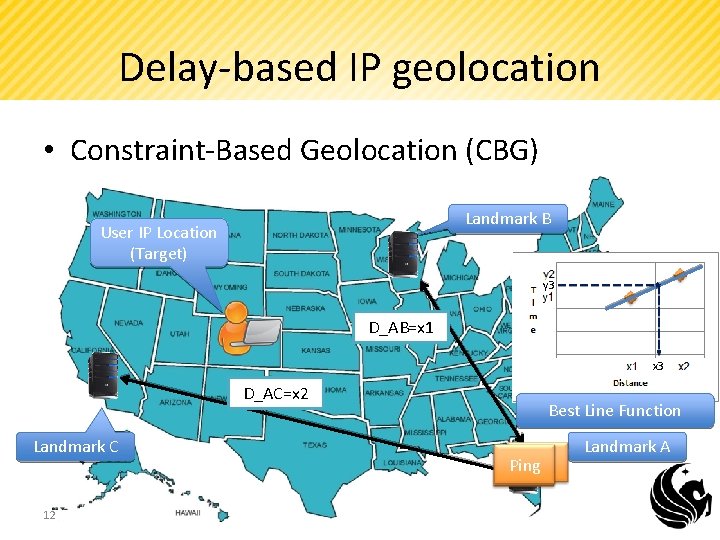
Delay-based IP geolocation • Constraint-Based Geolocation (CBG) Landmark B User IP Location (Target) y 3 D_AB=x 1 x 3 D_AC=x 2 Landmark C 12 Best Line Function Ping Landmark A
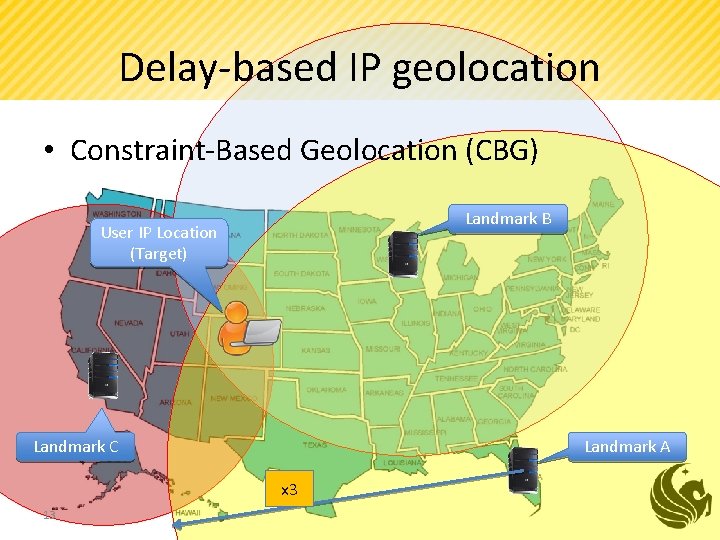
Delay-based IP geolocation • Constraint-Based Geolocation (CBG) Landmark B User IP Location (Target) Landmark A Landmark C x 3 13
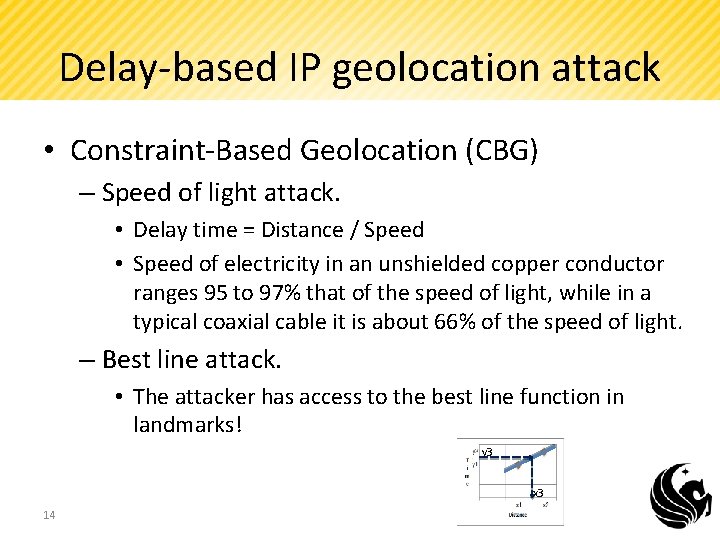
Delay-based IP geolocation attack • Constraint-Based Geolocation (CBG) – Speed of light attack. • Delay time = Distance / Speed • Speed of electricity in an unshielded copper conductor ranges 95 to 97% that of the speed of light, while in a typical coaxial cable it is about 66% of the speed of light. – Best line attack. • The attacker has access to the best line function in landmarks! y 3 x 3 14
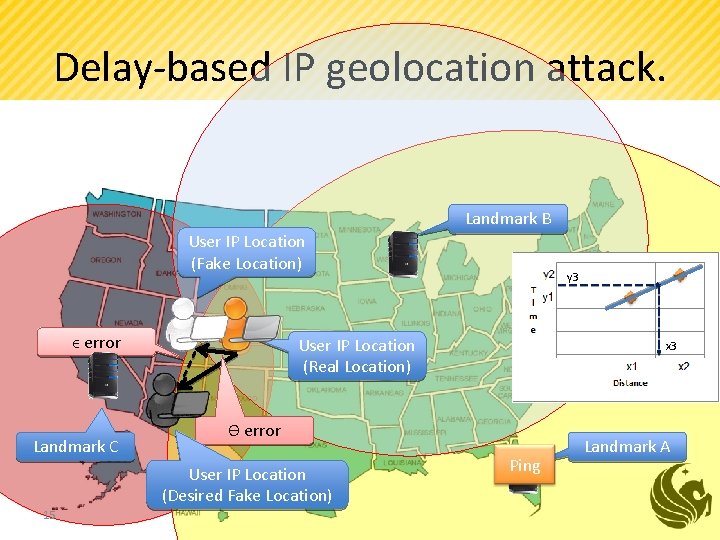
Delay-based IP geolocation attack. Landmark B User IP Location (Fake Location) ϵ error Landmark C User IP Location (Real Location) x 3 ϴ error User IP Location (Desired Fake Location) 15 y 3 Ping Landmark A
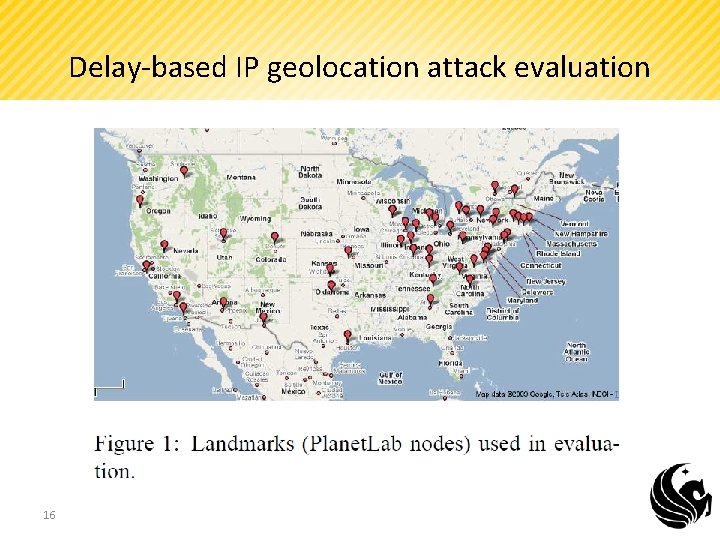
Delay-based IP geolocation attack evaluation 16
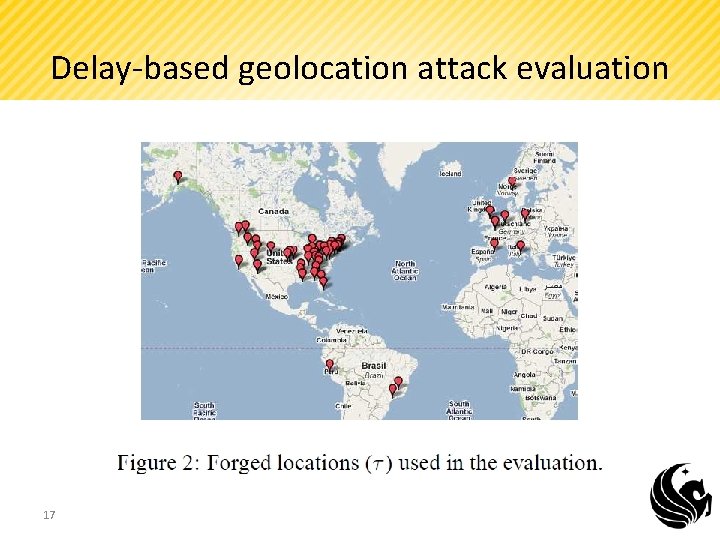
Delay-based geolocation attack evaluation 17
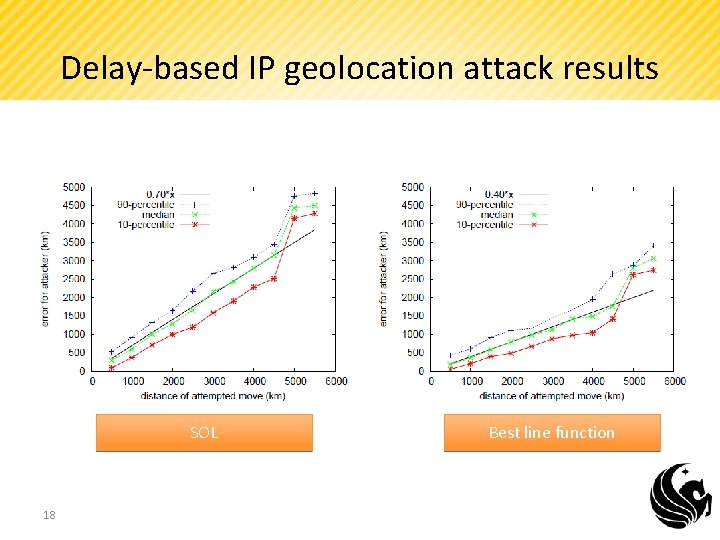
Delay-based IP geolocation attack results SOL 18 Best line function
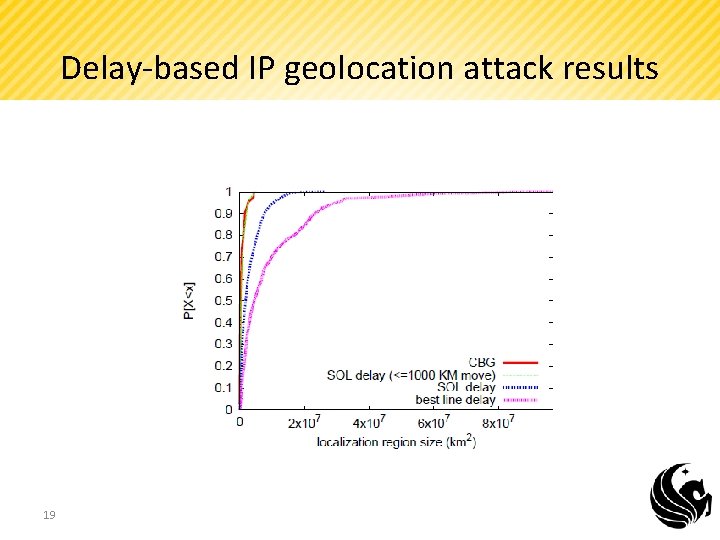
Delay-based IP geolocation attack results 19
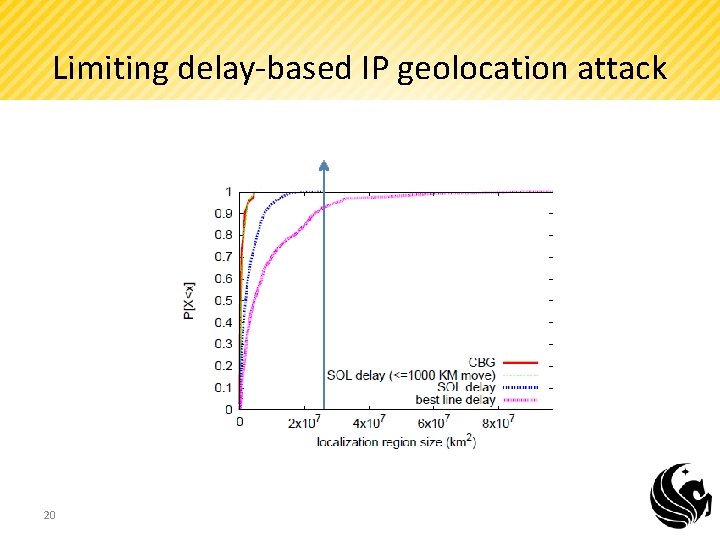
Limiting delay-based IP geolocation attack 20
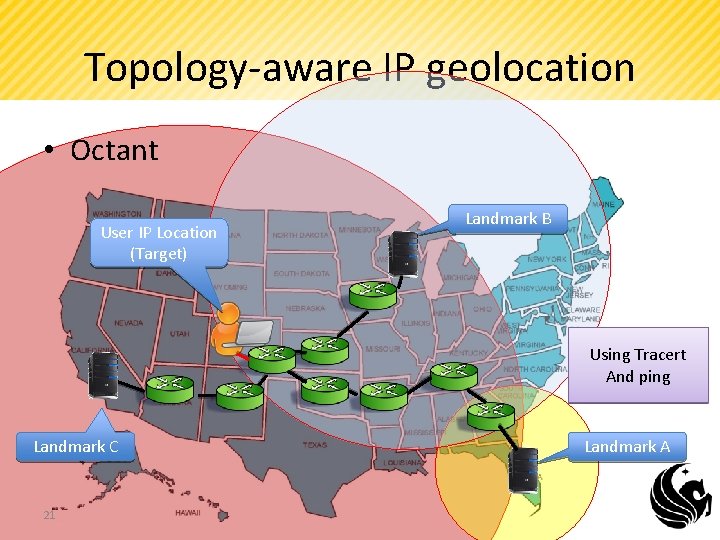
Topology-aware IP geolocation • Octant User IP Location (Target) Landmark B Using Tracert And ping Landmark C 21 Landmark A
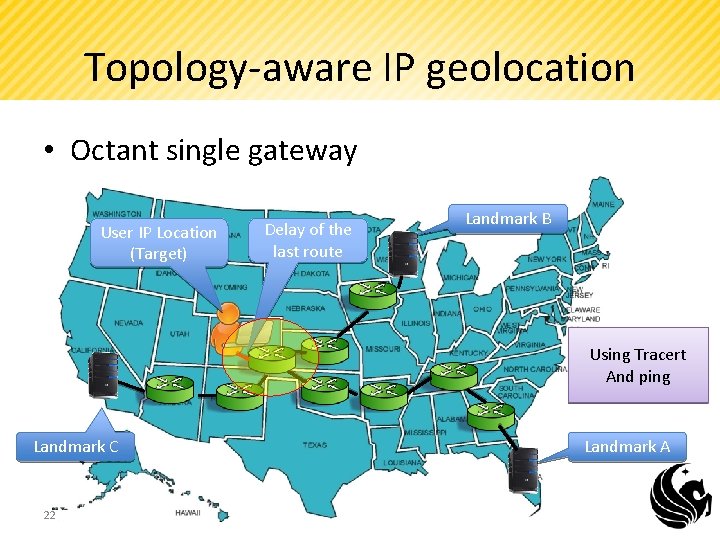
Topology-aware IP geolocation • Octant single gateway User IP Location (Target) Delay of the last route Landmark B Using Tracert And ping Landmark C 22 Landmark A
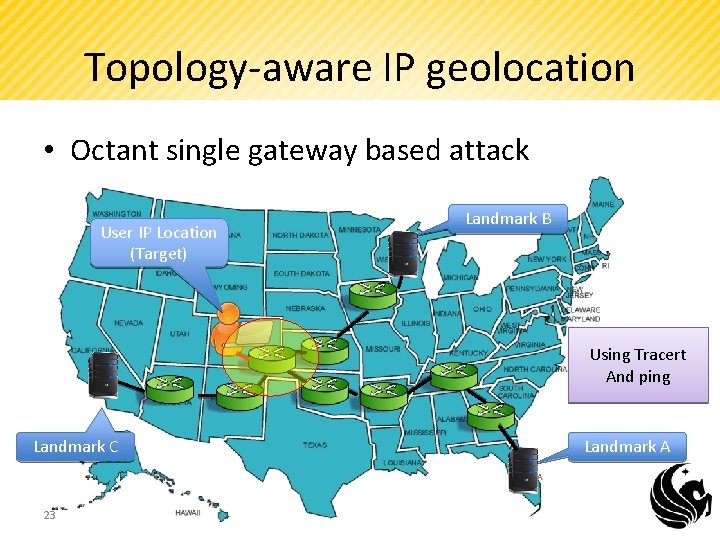
Topology-aware IP geolocation • Octant single gateway based attack User IP Location (Target) Landmark B Using Tracert And ping Landmark C 23 Landmark A
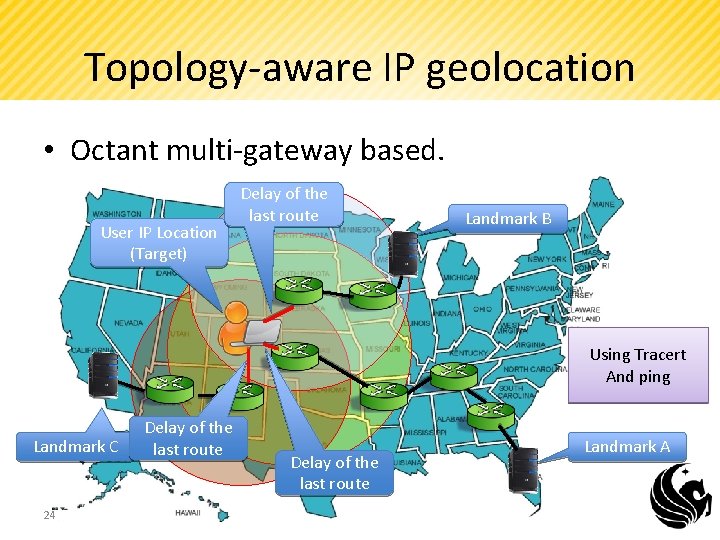
Topology-aware IP geolocation • Octant multi-gateway based. User IP Location (Target) Delay of the last route Landmark B Using Tracert And ping Landmark C 24 Delay of the last route Landmark A
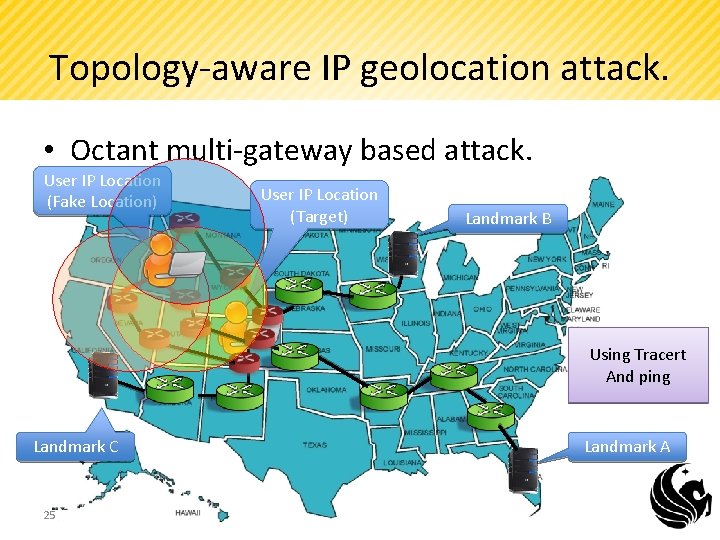
Topology-aware IP geolocation attack. • Octant multi-gateway based attack. User IP Location (Fake Location) User IP Location (Target) Landmark B Using Tracert And ping Landmark C 25 Landmark A
Topology-aware IP geolocation attack. • Naming attack, can effect on both single and mutli-gateway topology-aware geolocation. • The attack based on undns tool. • Each router will have a DNS domain name. • undns tool will map router DNS domain name to a city. • This naming attack requires the attacker is capable of crafting a domain name that can deceive the undns tool. 26
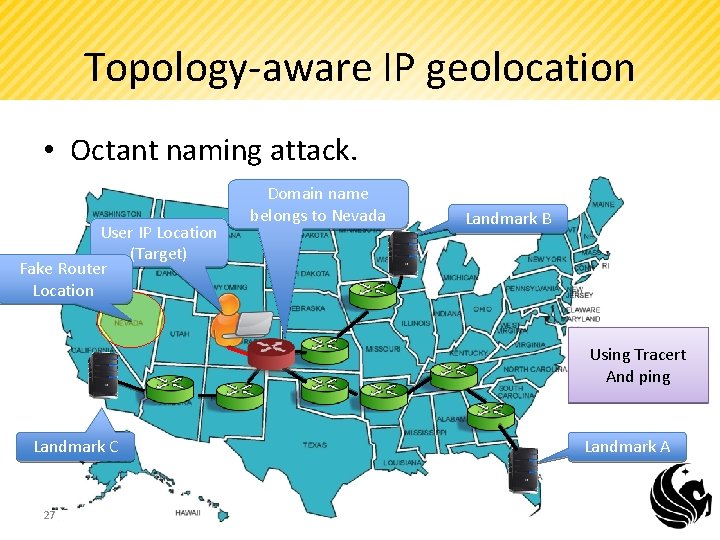
Topology-aware IP geolocation • Octant naming attack. User IP Location (Target) Fake Router Location Domain name belongs to Nevada Landmark B Using Tracert And ping Landmark C 27 Landmark A
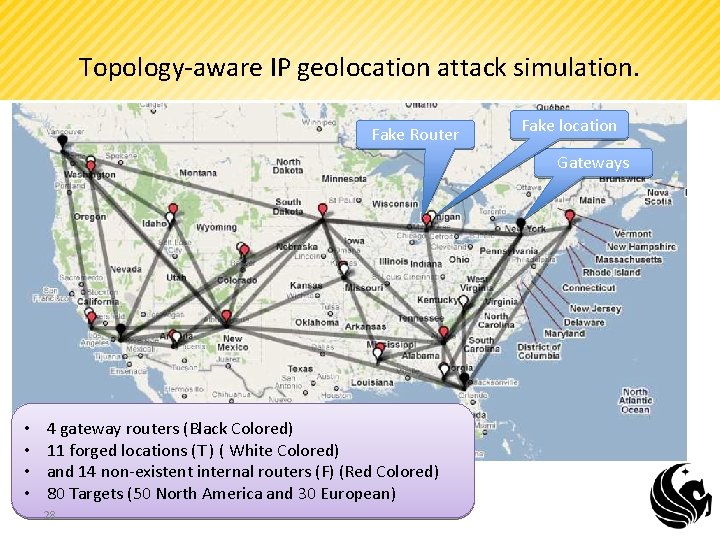
Topology-aware IP geolocation attack simulation. Fake Router Fake location Gateways • • 4 gateway routers (Black Colored) 11 forged locations (T ) ( White Colored) and 14 non-existent internal routers (F) (Red Colored) 80 Targets (50 North America and 30 European) 28
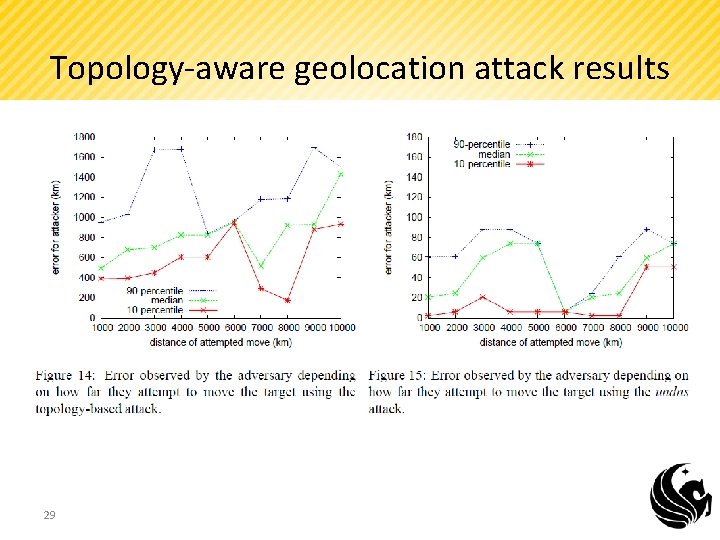
Topology-aware geolocation attack results 29
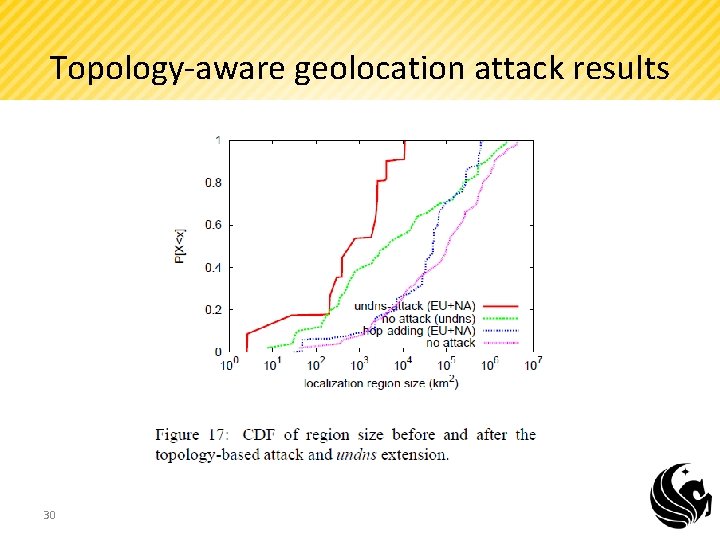
Topology-aware geolocation attack results 30

Presentation Agenda • • 31 What is IP geolocation? Why IP geolocation? IP geolocation classification and attacks. Paper contribution. Paper weakness. Paper improvement. Questions and answers.
Paper Contribution • The paper surveyed that the current IP geolocation algorithms such as (CBG and Octant) accuracies of 35 -194 km, making them suitable for geolocation within a country. • Also, the paper illustrated how the above IP geolocation algorithm can be vulnerable. • Then, the paper proposed that a delay based attack can be detected by setting a certain threshold to the size of the localization region. 32

Presentation Agenda • • 33 What is IP geolocation? Why IP geolocation? IP geolocation classification and attacks. Paper contribution. Paper weakness. Paper improvement. Questions and answers.

Paper Weakness • The paper didn’t explain the complexity of gaining access to the best line function. • The paper also didn’t explain the complexity to manipulate undns tool. • Lack of an efficient detection method to catch undns topology-aware IP geolocation attack. • The scientific reasoning for Plant. Lab landmarks distribution with the relation to the IP geolocation was not clear. • Using ping and trace-route to measure the delay time and route information is not recommended since administrator tend to drop theses types of packets. 34

Presentation Agenda • • 35 What is IP geolocation? Why IP geolocation? IP geolocation classification and attacks. Paper contribution. Paper weakness. Paper improvement. Questions and answers.

Paper Improvement • The impact of Landmarks distribution on both attacks. • Study the effect of using a reliable protocols to limit both attacks. 36

Presentation Agenda • • 37 What is IP geolocation? Why IP geolocation? IP geolocation classification and attacks. Paper contribution. Paper weakness. Paper improvement. Questions and answers.

Question and Answer 38

Thank You 39
- Slides: 38