DSS RATING MATRIX COGSWELL AWARD Security Rating Matrix
























- Slides: 30

DSS RATING MATRIX & COGSWELL AWARD

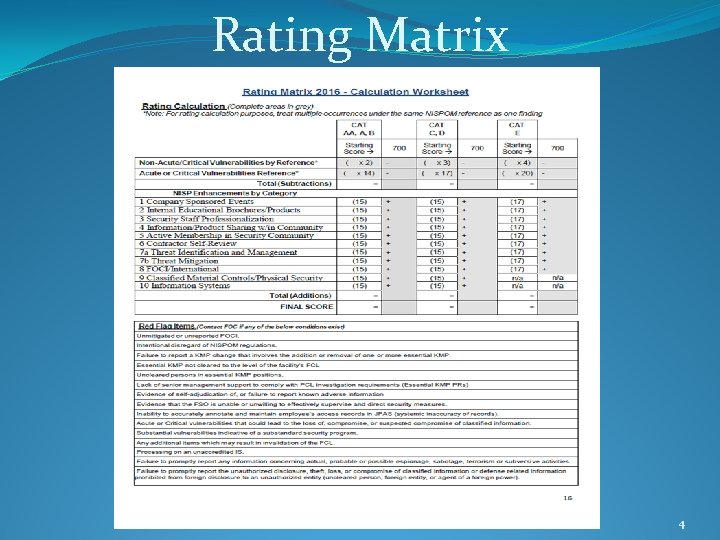
Security Rating Matrix �Provides a standardized approach to issuing security ratings throughout the Defense Security Service (DSS) �Provides a quantitative approach to assessing facilities utilizing a standard worksheet �The worksheet is a DSS tool, designed to standardize and improve consistency �Numerically based, quantifiable, and accounts for all aspects of a facility’s involvement in the National Industrial Security Program (NISP) 2

Security Rating Matrix �Points-based rating system �All facilities start with the same score (700) �Points are added for identified NISP enhancements �Points are subtracted for vulnerabilities by NISP Operating Manual (NISPOM) reference �Acute/Critical and Non-Acute/Non-Critical vulnerabilities are weighted separately �Points are subtracted by NISPOM reference, not by number of occurrences �Accounts for size and complexity of a facility 3

Rating Matrix 4

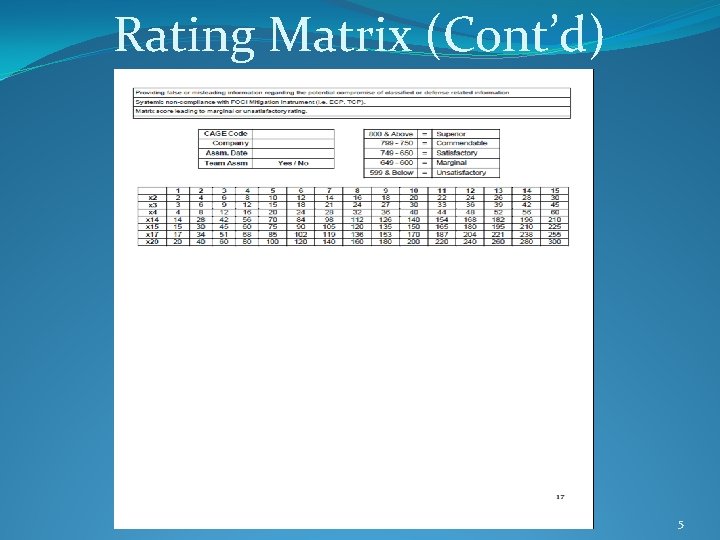
Rating Matrix (Cont’d) 5

Vulnerabilities �Acute Vulnerability – Vulnerabilities that put classified information at imminent risk of loss or compromise, or that have already resulted in the compromise of classified information. Acute vulnerabilities require immediate corrective action �Critical Vulnerability – Those instances of NISPOM noncompliance vulnerabilities that are serious, or that may place classified information at risk or in danger of loss or compromise �Once a vulnerability is determined to be Acute or Critical, it is further categorized as either “Isolated”, “Systemic”, or “Repeat” �All other vulnerabilities are defined as non-compliance with a NISPOM requirement that does not place classified information in danger of loss or compromise 6

Common Vulnerabilities �Failure to initiate a preliminary inquiry upon notification of a report of loss, compromise, or suspected compromise of classified information �Failure to appropriately mark classified information and material �Retaining classified information from an expired contract beyond the authorized two-year retention period without obtaining written retention authority from the government contracting activity �Failure to change safe combinations to closed areas/containers when employees having access were terminated �Operating an information system that is or will process classified information without appropriate approval �Failure to perform audits on classified systems �Lack of anti-virus software �Unreported facility clearance (FCL) change conditions �Periodic reinvestigations out of scope 7

Enhancements �A NISP enhancement directly relates to and enhances the protection of classified information beyond baseline NISPOM requirements � Directly related to the NISP and does not include other commonplace security measures or best practices �NISP enhancements will be validated during the assessment as having an effective impact on the overall security program �In order for an enhancement to be granted, the facility must meet the baseline NISPOM requirements in that area � An enhancement directly related to a NISPOM requirement cited for a vulnerability may not be granted � If there are other effective enhancement activities in a specific category unrelated to a specific vulnerability in that category, the enhancement credit may still be granted 8

Rating Matrix Categories �Category 1: Company Sponsored Events �Category 2: Internal Educational Brochures/Products �Category 3: Security Staff Professionalization �Category 4: Information & Product Sharing within Security Community �Category 5: Active Membership in Security Community �Category 6: Contractor Self-Review �Category 7 a: Threat Identification and Management � 7 b: Threat Mitigation �Category 8: FOCI / International �Category 9: Classified Material Controls/Physical Security �Category 10: Information Systems 9

Presentation of Enhancements �Enhancement validated during the assessment �Provide documentation supporting enhancements to the DSS representative �DSS must be able to validate the enhancement �Make the validation as easy as possible �Identify the enhancements that you believe you qualify for and state why you feel your program qualifies for it �Provide all supporting documentation �Keep it neat, organized, and concise � Consider using a binder, folder, or some other mechanism to provide all supporting information in one place 10

Enhancements �For complete information and examples of what qualifies as an enhancement, please see the DSS 2016 Vulnerability Assessment Rating Matrix Vulnerabilities and NISP Enhancement Categories Guide 11

COGSWELL AWARD • • What is the Cogswell Award? Backward Glances of Facility Selections 2015/2016 Cogswell Numbers and Companies Selected Nomination Process Selection Process General Keys to Success My Keys to being Nominated/Selected 12

Cogswell Award Established � 1966 in honor of the late Air Force Col James S. Cogswell �First chief of the unified office of Industrial Security �Created the basic principles forming the National Industrial Security Program (NISP) �Places emphasis on the need for a true partnership between industry and government to ensure the protection of classified information, materials, and programs 13

What is the Cogswell Award? • Outstanding Industrial Security Achievement Award • Presented to companies that understand the complexity of the security environment • Companies go above and beyond the minimum requirements expected of them • Winning facilities represent the “best of the best” • Their security programs stand as models for others to emulate • Awarded on an annual basis • DSS partners with NCMS to host the Cogswell Award presentations during its annual training conference • Awards are presented by DSS Director Stan Sims 14

Backward Glances of Facility Selections � 2010 9 Facilities Selected � 2011 17 Facilities Selected � 2012 26 Facilities Selected � 2013 24 Facilities Selected � 2014 40 Facilities Selected � 2015 41 Facilities Selected � 2016 42 Facilities Selected 15

2015 Cogswell Numbers by Facility 41 Facilities Selected � � � � � � Alliant Techsystems-Minn BAE Systems Technology-RI Batelle Memorial Institute-Va Crowell & Moring LLP-DC DRS ICAS LLC-Ohio DRS Sensors & Targeting Sys-Calif General Dynamics Advanced-Va General Dynamics IT-Pa Honeywell International-Minn Jacobs Technology-Tenn L-3 Communications Integrated-Texas L-3 Unidyne-RI Lockheed Martin Systems-Colo Lockheed Martin Missiles Fire Control-Fla Logistics Management Institute-Va Raytheon Company-Ariz Raytheon Company-Fla Raytheon/Lockheed Martin Javelin-Ariz Scientific Research Corp-Ga Texas A&M University-Texas Vencore Services & Solutions-Ohio BAE Systems Land-Calif Batelle Colonial Place-Va Charles Stark Draper-Mass DCS Corporation-Fla DRS Power Technology-Mass Force 3 -Md General Dynamics C 4 -Ariz General Dynamics IT-Va i. Gov Technologies-FL Jacobs Technology-Ohio L-3 Systems Company-NJ Lexis. Nexis Special Services-DC Lockheed Martin Mission &Sys-Fla Lockheed Martin Sippicon-Mass The Protective Group Inc-Fla Raytheon Company-Calif Raytheon Company-Va Saab Defense and Security-NY Stanley Associates-Fla University of Rhode Island-RI 16

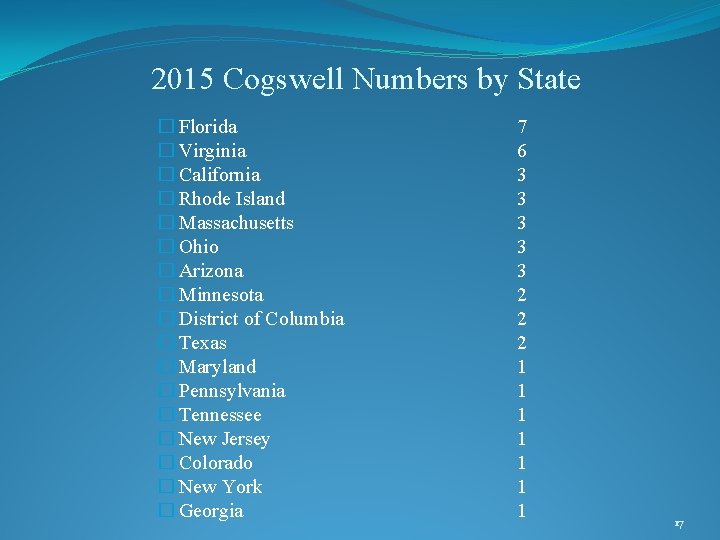
2015 Cogswell Numbers by State � Florida � Virginia � California � Rhode Island � Massachusetts � Ohio � Arizona � Minnesota � District of Columbia � Texas � Maryland � Pennsylvania � Tennessee � New Jersey � Colorado � New York � Georgia 7 6 3 3 3 2 2 2 1 1 1 17

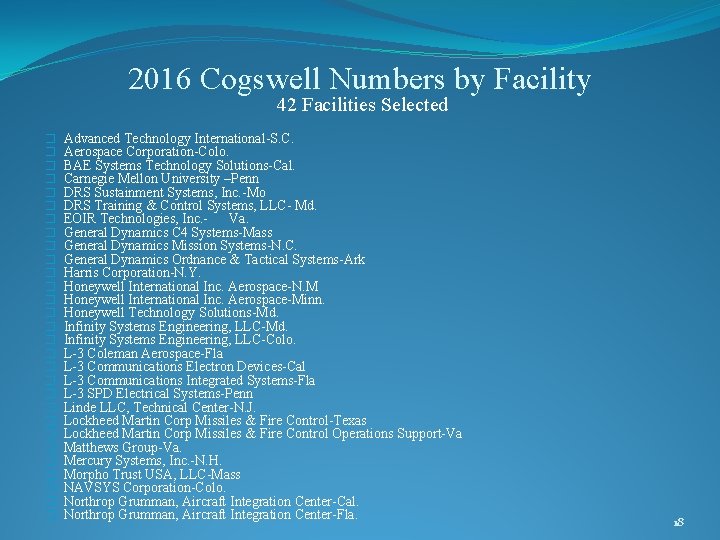
2016 Cogswell Numbers by Facility 42 Facilities Selected � � � � � � � � Advanced Technology International-S. C. Aerospace Corporation-Colo. BAE Systems Technology Solutions-Cal. Carnegie Mellon University –Penn DRS Sustainment Systems, Inc. -Mo DRS Training & Control Systems, LLC- Md. EOIR Technologies, Inc. Va. General Dynamics C 4 Systems-Mass General Dynamics Mission Systems-N. C. General Dynamics Ordnance & Tactical Systems-Ark Harris Corporation-N. Y. Honeywell International Inc. Aerospace-N. M Honeywell International Inc. Aerospace-Minn. Honeywell Technology Solutions-Md. Infinity Systems Engineering, LLC-Colo. L-3 Coleman Aerospace-Fla L-3 Communications Electron Devices-Cal L-3 Communications Integrated Systems-Fla L-3 SPD Electrical Systems-Penn Linde LLC, Technical Center-N. J. Lockheed Martin Corp Missiles & Fire Control-Texas Lockheed Martin Corp Missiles & Fire Control Operations Support-Va Matthews Group-Va. Mercury Systems, Inc. -N. H. Morpho Trust USA, LLC-Mass NAVSYS Corporation-Colo. Northrop Grumman, Aircraft Integration Center-Cal. Northrop Grumman, Aircraft Integration Center-Fla. 18

2016 Cogswell Numbers by Facility (Cont) � Oshkosh Corporation-Wis. � PAE Applied Technologies-Md. � Pro. Logic Inc. -Va. � Quest Software Public-Md. � Raytheon Company-Colo. � Raytheon Company EWS Self Protect Systems-Cal. � Raytheon Company Raytheon Vision Systems-Cal. � SES Government Solutions-Va. � Ultra Electronics Advanced Tactical Systems, Inc. -Texas � Ultra Electronics Secure Intelligence Systems Inc. -Va. � University of New Mexico-N. M. � Virginia Polytechnic Institute and State University-Va. � Wiley Wilson-Va. 19

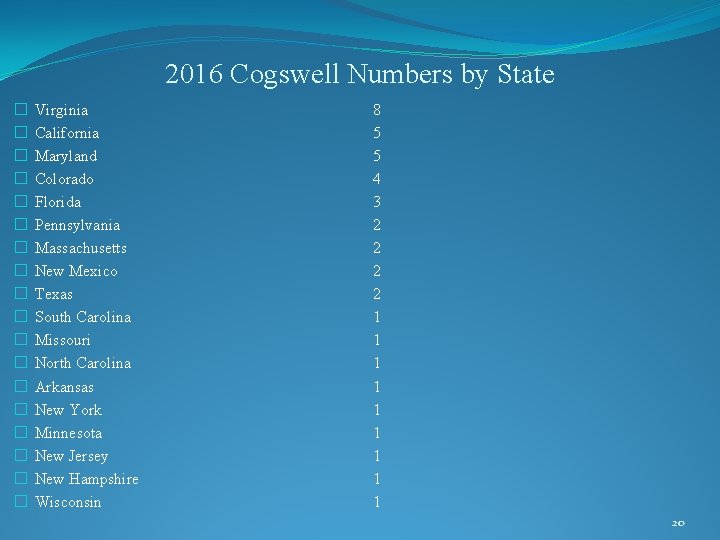
2016 Cogswell Numbers by State � � � � � Virginia California Maryland Colorado Florida Pennsylvania Massachusetts New Mexico Texas South Carolina Missouri North Carolina Arkansas New York Minnesota New Jersey New Hampshire Wisconsin 8 5 5 4 3 2 2 1 1 1 1 1 20

Nomination/Selection Process � DSS Industrial Security Representative nominates the facility � Facility must have two consecutive superior ratings to be considered � Of the 12, 800 -plus cleared facilities, approximately 8% receive superior ratings each year � Two consecutive superior ratings demonstrates a facility’s commitment to security over time � Once Nominated � Facility enters an eight month DSS internal review process � Includes a National Review Team of DSS Regional directors and representatives from across DSS who consider each nomination � National Review Team vets all nominations with 30 external agencies and makes recommendations to DSS senior leaders for a final decision 21

Criteria Final Decision Is Based Upon �Overall Security Program/Company Procedures � Documented, formal SOP, EAP, TCP � Comprehensive, published and disseminated to the employee population �Senior Management Support � Resources, time, training, etc. � Including security staff and company personnel �Security Vulnerability Assessments History � Company history of not just meeting but exceeding NISP requirements � Violations – Does the company have a history of negligence? � Has the company been culpable for the violations? �Security Education and Awareness �Facility Security Officer (FSO) and Security Staff Level of Experience �Classified Material Controls 22

General Keys to Success �Education awareness and training programs �Well organized �Strong partnership and open dialogue with DSS/CI/IA representatives �Full compliance with the NISPOM requirements § Management support is imperative § Membership groups (NCMS, Industrial Security Awareness Council) § Be committed to your role in security § Attend security events (NCMS, FISWG) 23

Personal Keys to Success � Create Separate Binders: �Binder #1 DSS Master Documents � 441 -1 � SF 328 FOCI � Prime DD 254 s � Facility Clearance Letter/ISFD Printout � Appointment Letters � Organizational Charts/Company Business Structure �Binder #2 Training Binder/Training Spreadsheet � Initial COMSEC Insider Threat � Refresher Active Shooter Classified EAP � CI Safe Room Data Spill Plan � OPSEC Classified Wrapping/Mailing � Cyber Sectera v. IPer Secure Phone 24

Personal Keys to Success � Create Separate Binders: � Binder #3, 4, 5, 6 (Contracts that you support) � � � Prime DD 254 Handout, brochure, flyers, statement about the contract Subcontractor DD 254 ISFD printouts for subcontractors Statement of Work (SOW) Security Classification Guide (SCG) � Binder #7 Counterintelligence Info � Listing of all individuals that went on foreign travel during that SVA period � Foreign travel briefing statements � Return suspicious contact briefing � Foreign travel logs for exiting and returning � Copy of suspicious contact emails sent to CI representative � Defensive briefing example � Training conducted for CI, Cyber, OPSEC � Annual CI briefing sign in sheets � Copy of Technology Control Plan; Appointment Letter for TCP/ITAR representative � Monthly Newsletter with CI articles 25

Personal Keys to Success � Create Separate Binders: � Binder #8 Enhancements � Category 1: Company Sponsored Events � Monthly Security Luncheon � Hosted Counterintelligence Event Briefing � CBT Training Online Classes � Category 2: Internal Education Brochures/Products � Monthly Security Newsletter � Security Web Site for DSS Brochures/Pamphlets � Category 3: Security Staff Professionalization � FSO Training Certificates � Briefing at FISWG � Briefing at NCMS � Memberships in NCMS, Federal IT Security Institute (FITSI) 26

Personal Keys to Success � Create Separate Binders: � Binder #8 Enhancements � Category 4: Information/Product Sharing within Security Community � Guest speaker at 2014 FISWG � NCMS mentor � Assisted COMNAVSPECWARCOM with SIPRNet connection process � Category 5: Active Membership in Security Community � Guest speaker at NCMS 2014 � Attended FISWG, DSS Outreach, NCMS Cybersecurity USF � Category 6: Contractor Self-Inspection � Thorough documented self-inspections � Provide DSS detailed reports � Completed DSS self-inspection training � Several inspections conducted throughout the year 27

Personal Keys to Success � Create Separate Binders: � Binder #8 Enhancements � Category 7 a: Threat Identification and Management � Annual CI briefing conducted by DSS CI representative � All employees completed Thwarting the Enemy training � Established TCP, OPSEC � Category 7 B: Threat Mitigation � Active Suspicious Contact Report submitted to CI � Category 8: Foreign Ownership Control or Influence FOCI � TCP Plan � Foreign visitors color-coded badges � 30 Day notification required � Copy of Foreign travel briefings Out & Returning 28

Personal Keys to Success � Create Separate Binders: � Binder #8 Enhancements � Category 9: Classified Material Control/Physical Security � Enhanced process for managing classified information � Built-in countermeasures to identify anomalies � 100% inventory conducted on a random basis � Information Management System � Limited Access � Access Controlled � Category 10: Information Systems � Process enhancements and leveraging tools to expand the overall security posture of accredited information systems � SOP � Additional IS oversight processes put in place to enhance security of classified information residing on IS 29

Additional Enhancements � Color Badges/Holders Identify Security Clearance Level � Red � Brown � Yellow � Blue � Green � Purple No Clearance/Escort Required Trusted Individual (No Clearance) Secret Top Secret/SCI Foreign Visitor � Six-Part, Color-Coded Security Personnel Folders � See JPAS Personnel Summary � SF 86 & Notification Letter of Review for SF 86 Adequacy & Completeness � Training Acknowledgement Sheets � SF 312 Nondisclosure Agreement (see JPAS) � Clearance Justification letter, Visit Request Letters, SCI Nomination Letters � Network User Agreement, Hiring Notification 30