Docker Ecosystem Vulnerability Analysis A MARTIN S RAPONI

Docker Ecosystem Vulnerability Analysis A. MARTIN, S. RAPONI, T. COMBE, R. DI PIETRO
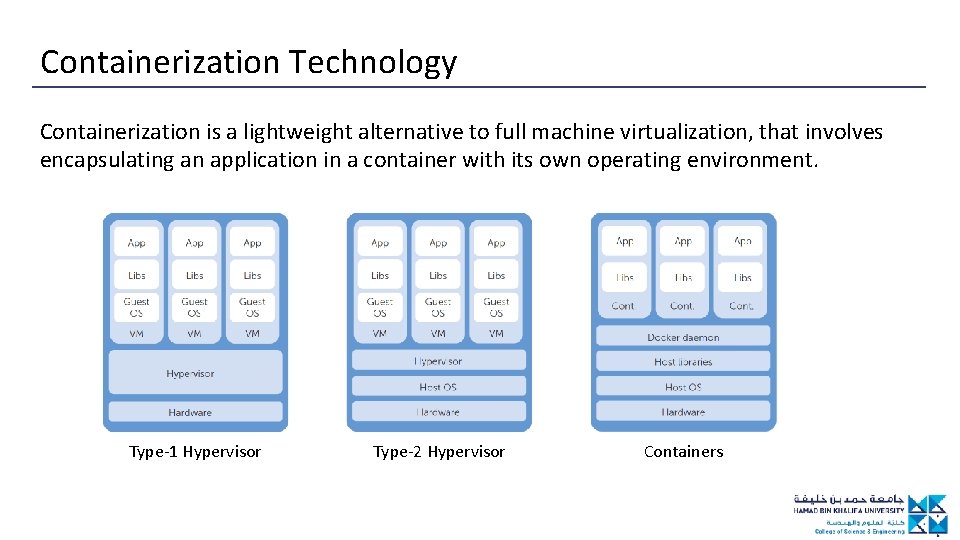
Containerization Technology Containerization is a lightweight alternative to full machine virtualization, that involves encapsulating an application in a container with its own operating environment. Type-1 Hypervisor Type-2 Hypervisor Containers
Why Docker? Docker is not the only containerization technology. . but it is currently leading the market!
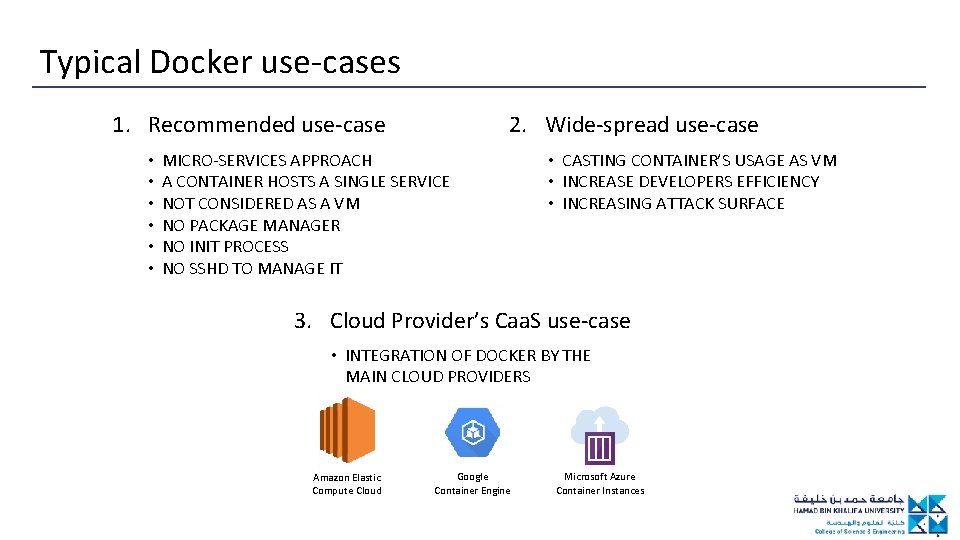
Typical Docker use-cases 2. Wide-spread use-case 1. Recommended use-case • • • MICRO-SERVICES APPROACH A CONTAINER HOSTS A SINGLE SERVICE NOT CONSIDERED AS A VM NO PACKAGE MANAGER NO INIT PROCESS NO SSHD TO MANAGE IT • CASTING CONTAINER’S USAGE AS VM • INCREASE DEVELOPERS EFFICIENCY • INCREASING ATTACK SURFACE 3. Cloud Provider’s Caa. S use-case • INTEGRATION OF DOCKER BY THE MAIN CLOUD PROVIDERS Amazon Elastic Compute Cloud Google Container Engine Microsoft Azure Container Instances
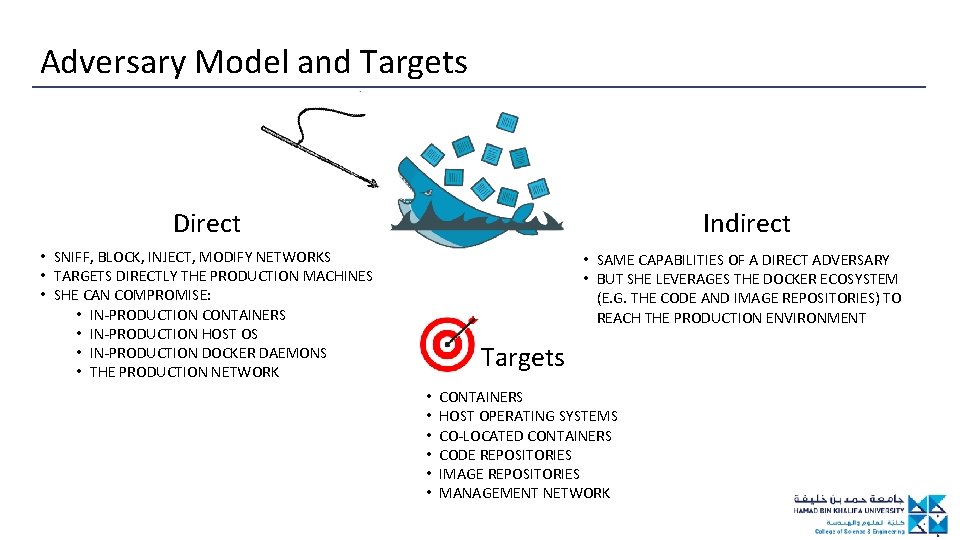
Adversary Model and Targets Direct Indirect • SNIFF, BLOCK, INJECT, MODIFY NETWORKS • TARGETS DIRECTLY THE PRODUCTION MACHINES • SHE CAN COMPROMISE: • IN-PRODUCTION CONTAINERS • IN-PRODUCTION HOST OS • IN-PRODUCTION DOCKER DAEMONS • THE PRODUCTION NETWORK • SAME CAPABILITIES OF A DIRECT ADVERSARY • BUT SHE LEVERAGES THE DOCKER ECOSYSTEM (E. G. THE CODE AND IMAGE REPOSITORIES) TO REACH THE PRODUCTION ENVIRONMENT Targets • • • CONTAINERS HOST OPERATING SYSTEMS CO-LOCATED CONTAINERS CODE REPOSITORIES IMAGE REPOSITORIES MANAGEMENT NETWORK
Identified Vulnerabilities • Insecurity production system configuration; • Vulnerabilities in the image distribution, verification, decompression, storage process; • Vulnerabilities inside the images; • Vulnerabilities directly linked to Docker or Libcointainer; • Vulnerabilities of the Linux kernel. Libcontainer
Insecure Configuration The use of some options can provide containers an extended access to the host: • Mounting of sensitive host directories into containers • TLS configuration of remote image registries • Permission on the Docker control socket • Cgroups activation (disabled by default) • Options directly providing to containers (--net=host, --privileged, additional capabilities) Exploitation • --uts=host allows the container to see and change the host name and domain. • --cap=add=SYS_ADMIN allows the container to remount /proc and /sys in write mode. • With some storage drivers (e. g. , AUFS), Docker does not limit containers disk usage. The volume can be filled, by affecting containers of the same host. Mitigation • Follow the Docker Benchmark of the Center for Internet Security. • Follow the Docker best practices provided by Docker • Principle of least privilege
Vulnerabilities in the image distribution process (VIDB) • Docker as a package manager The architecture of the Docker Hub is similar to a package repository, with the Docker daemon acting as a package manager on the host. Exploitation • Exploit the control of part of the network to make a malicious (compromised) image downloaded on Docker hosts. • Zip bomb attacks (Do. S), path traversal attacks. Mitigation • TLS on the connection to the registry (could be disabled) • Docker Content Trust (could be disabled) -- it requires the trust of developers and it does not scale. • Automated deployment pipeline vulnerabilities Docker proposes automated builds on the Docker Hub, triggered by an event from an external code repository (Git. Hub, Bit. Bucket). Exploitation • Account hijacking, tampering with network communications, insider attacks. • API calls not secured by TLS Mitigation
Vulnerabilities inside the images The code available for download on the Docker Hub (used to build images) is directly exposed to attackers when in production. In fact: • 36% of official images contain high-priority CVE vulnerabilities. • 64% of official images contain medium/high-priority CVE vulnerabilities. Exploitation • Vulnerabilities propagation from base images to children images. • Shell. Shock (bash), Heart. Bleed (Open. SSL), Poodle (Open SSL). Mitigation • Docker Security Scanning –time consuming (from 1 to 24 hours per image), limited available (applicable only on the private repositories). • Problem: if a vulnerability is not part of the database, the scan cannot reveal it, making the service unresponsive to new attacks.
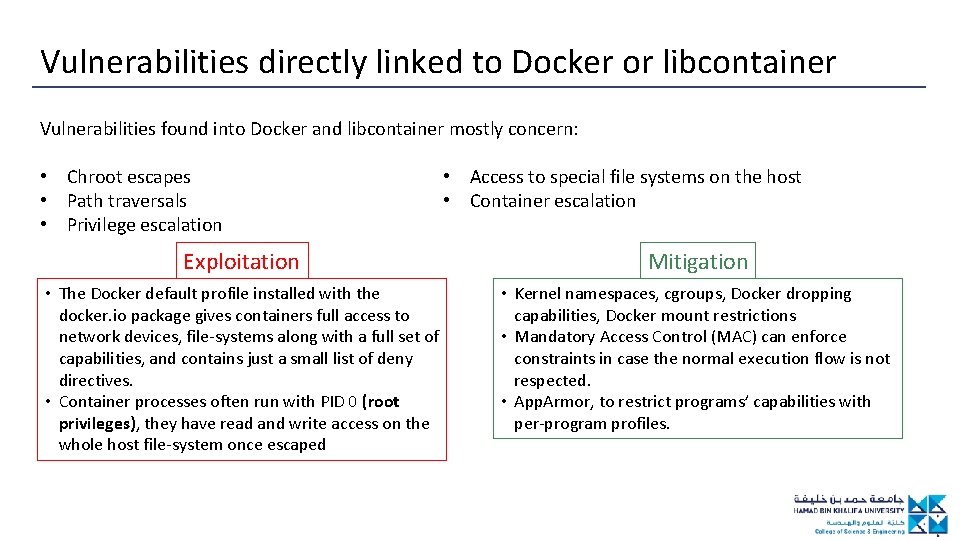
Vulnerabilities directly linked to Docker or libcontainer Vulnerabilities found into Docker and libcontainer mostly concern: • Chroot escapes • Path traversals • Privilege escalation • Access to special file systems on the host • Container escalation Exploitation Mitigation • The Docker default profile installed with the docker. io package gives containers full access to network devices, file-systems along with a full set of capabilities, and contains just a small list of deny directives. • Container processes often run with PID 0 (root privileges), they have read and write access on the whole host file-system once escaped • Kernel namespaces, cgroups, Docker dropping capabilities, Docker mount restrictions • Mandatory Access Control (MAC) can enforce constraints in case the normal execution flow is not respected. • App. Armor, to restrict programs’ capabilities with per-program profiles.
Vulnerabilities of the Linux Kernel Since containers run on the same kernel of the host, they are vulnerable to kernel exploits. An exploit giving full root privileges into a container can allow an attacker to break out this container and compromise the host (triggering for instance isolation and integrity breach, as well as data exposure). By compromising the Linux Kernel, all the containers hosted by the host machine will be compromised as well, causing possible extensive economic damage due to failure to provide services. Hardening techniques can be used to secure the Linux Kernel, along with the mechanisms necessary to provide the container with the fewest possible permits to perform the hob.
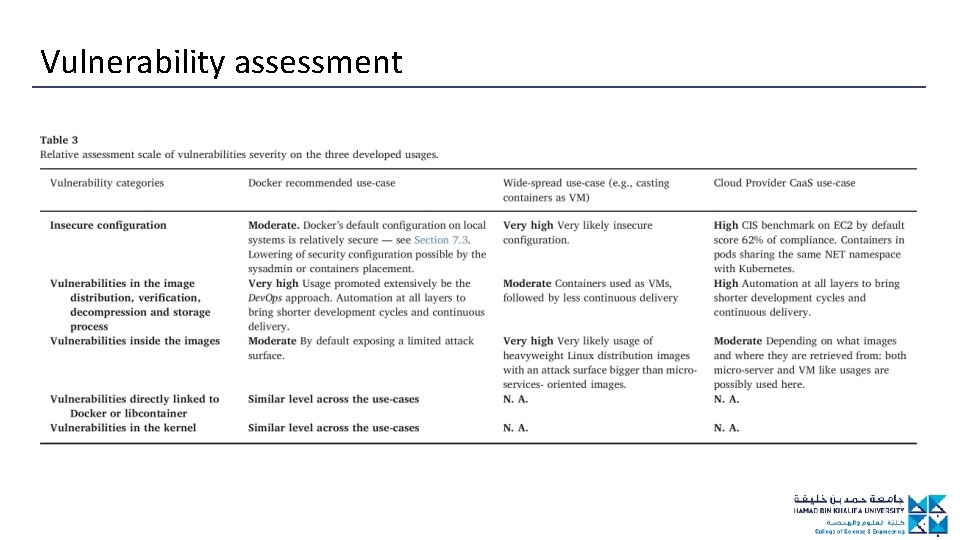
Vulnerability assessment

Conclusion In this paper, we: • perform a review of the components of the whole Docker ecosystem; • perform a security-driven classification; • identify key elements to assess the security of each component; • highlight some new classes of vulnerabilities; • performed experiments to demonstrate how tangible are the risks; We show that the comparison “VM vs. containers” is inappropriate since the use cases are different and so is the underlying architecture.
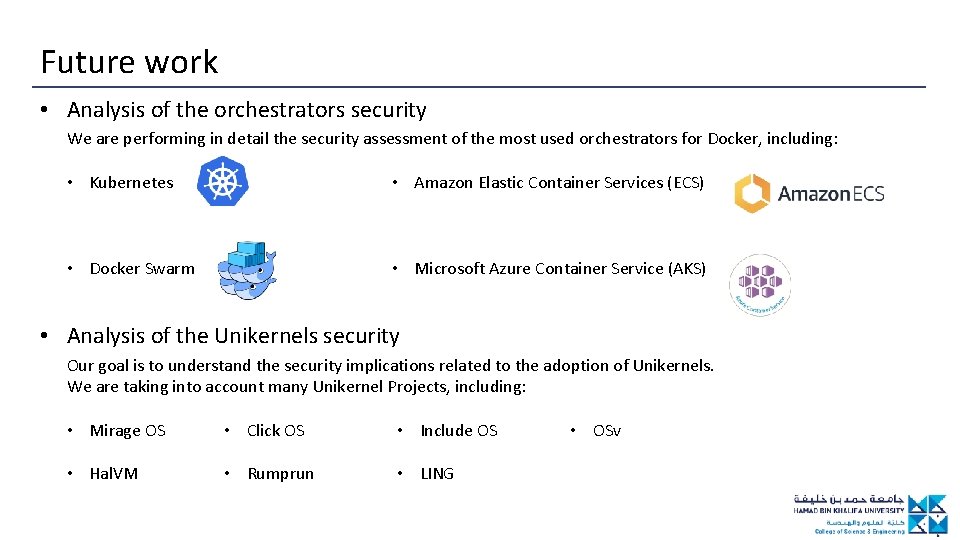
Future work • Analysis of the orchestrators security We are performing in detail the security assessment of the most used orchestrators for Docker, including: • Kubernetes • Amazon Elastic Container Services (ECS) • Docker Swarm • Microsoft Azure Container Service (AKS) • Analysis of the Unikernels security Our goal is to understand the security implications related to the adoption of Unikernels. We are taking into account many Unikernel Projects, including: • Mirage OS • Click OS • Include OS • Hal. VM • Rumprun • LING • OSv
![References Papers [1] A. Martin, S. Raponi, T. Combe, R. Di Pietro, Docker ecosystem References Papers [1] A. Martin, S. Raponi, T. Combe, R. Di Pietro, Docker ecosystem](http://slidetodoc.com/presentation_image_h/aed7970a5d8db5cc65f9520982fdbbcc/image-15.jpg)
References Papers [1] A. Martin, S. Raponi, T. Combe, R. Di Pietro, Docker ecosystem – Vulnerability Analysis [2] T. Combe, A. Martin, R. Di Pietro, To Docker or not to Docker: A security perspective. [3] F. Lombardi, R. Di Pietro, Virtualization and cloud security: Benefits, caveats, and future developments. [4] R. Di Pietro, F. Lombardi, Security for Cloud Computing. [5] T. Bui, Analysis of Docker Security. [6] A. Mouat, Docker security using containers safely in production. [7] T. Li, J. Chen, Research of penetration testing technology in Docker environment. [8] Z. Jian, L. Chen, A defense method against Docker escape attack. [9] R. Shu, X. Gu, W. Enck, A study of security vulnerabilities on Docker Hub. Some of the images contained in these slides have been taken from the following sources: http: //unikernel. org/ https: //www. odoogap. com/blog/odoogap-blog-1/post/the-lxd-container-hypervisor-7 http: //vpstutorial. com/the-differences-of-xen-kvm-openvz-which-is-right-for-me/ https: //worldvectorlogo. com/logo/rkt https: //medium. com/@sanketmeghani/docker-transferring-docker-images-without-registry-2 ed 50726495 f https: //justanotherdevblog. com/aws-certified-solutions-architect-ec 2 -70656 b 376767 https: //meteatamel. wordpress. com/2016/02/24/google-container-engine/ https: //azure. microsoft. com/en-us/services/container-instances/ http: //moziru. com/explore/Spear%20 clipart%20 harpoon/#go_post_7639_spear-clipart-harpoon-1. gif https: //www. steerlean. com/single-post/2018/03/29/How-NOT-to-use-Docker https: //www. temporealeventos. com. br/single-post/Containers-Docker-para-Desenvolvedores-Da-Criacao-a-Producao https: //www. 6 sqft. com/rich-people-have-more-bugs-is-the-most-new-york-dessert-ever/ https: //opensourceforu. com/2016/09/linux-kernel-3 -14 -wont-receive-future-updates/ https: //www. pinterest. com/pin/441352832211717649/ https: //architecht. io/kubernetes-is-a-big-deal-but-an-overlooked-one-3 c 4 dc 2 cd 67 df https: //medium. com/containers-on-aws/say-hello-to-amazon-fargate-and-amazon-elastic-container-service-for-kubernetes-66707 dd 14976 https: //rominirani. com/docker-swarm-tutorial-b 67470 cf 8872 https: //azure. microsoft. com/en-us/blog/kubernetes-now-generally-available-on-azure-container-service/
- Slides: 15