Do ITT Identity Management Security Provisioning Authentication Prepared




- Slides: 13

Do. ITT Identity Management Security, Provisioning, Authentication Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

What is Identity Management • Identity management deals with identifying individuals in a system and controlling their access to resources within that system throughout their employment by associating user rights and restrictions with the established identity. It is the core of what is termed “Employee Lifecycle Management. ” • In an enterprise setting, identity management is used to increase security and productivity, while decreasing cost and redundant effort. • Includes: – – Password synchronization (reduced sign-on) Automated password resets Provisioning and authorization to systems De-provisioning users when they are no longer in the agency Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

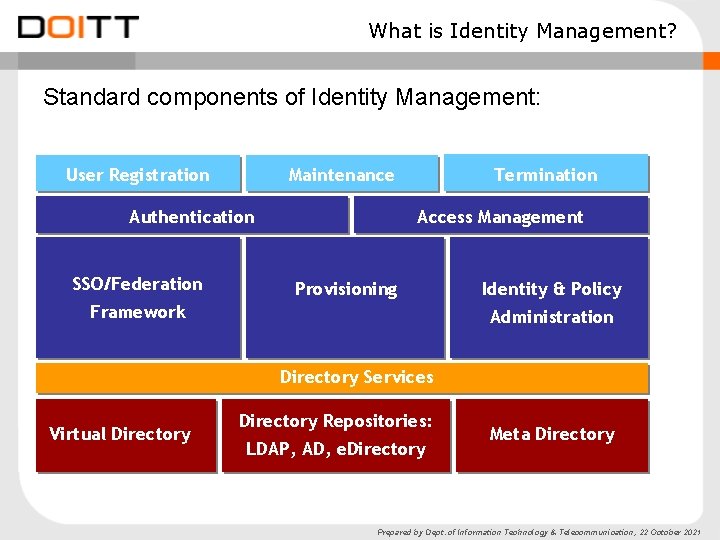
What is Identity Management? Standard components of Identity Management: User Registration Authentication SSO/Federation Termination Maintenance Access Management Provisioning Framework Identity & Policy Administration Directory Services Virtual Directory Repositories: LDAP, AD, e. Directory Meta Directory Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

Today’s Enterprise LDAP The City Meta-Directory Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

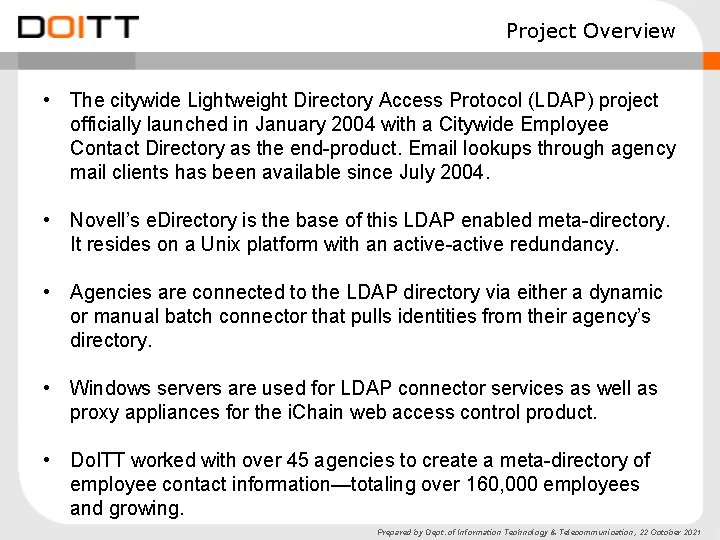
Project Overview • The citywide Lightweight Directory Access Protocol (LDAP) project officially launched in January 2004 with a Citywide Employee Contact Directory as the end-product. Email lookups through agency mail clients has been available since July 2004. • Novell’s e. Directory is the base of this LDAP enabled meta-directory. It resides on a Unix platform with an active-active redundancy. • Agencies are connected to the LDAP directory via either a dynamic or manual batch connector that pulls identities from their agency’s directory. • Windows servers are used for LDAP connector services as well as proxy appliances for the i. Chain web access control product. • Do. ITT worked with over 45 agencies to create a meta-directory of employee contact information—totaling over 160, 000 employees and growing. Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

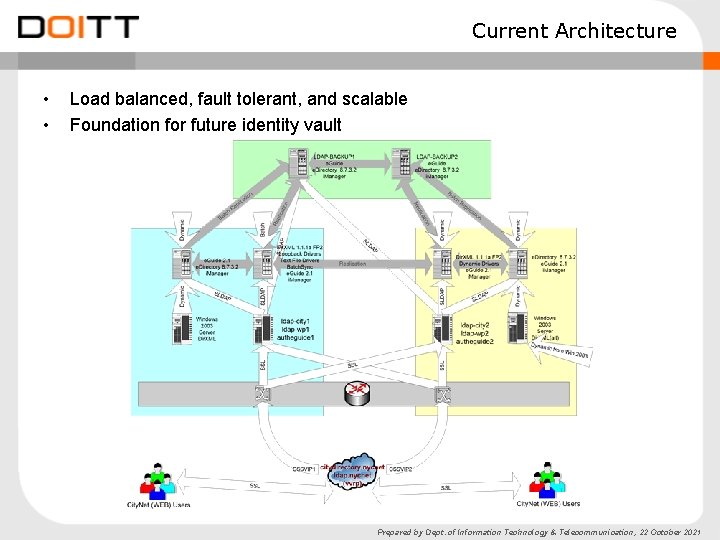
Current Architecture • • Load balanced, fault tolerant, and scalable Foundation for future identity vault Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

Security and Uniqueness • Agencies define what information is visible through the Citywide Employee Contact Directory. • Agencies have a variety of means of hiding or removing data from the system. • The biggest challenge and most important element of the project was to determine a preexisting unique identifier for each employee. • Name and agency, email address, and even combinations of these aren’t sufficient since none of these are truly unique in NYC. • Current unique identifier: Surname + Given name, Organizational Unit (s), Organization (nycnet) • Future unique identifier: PMS Employee I. D. Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

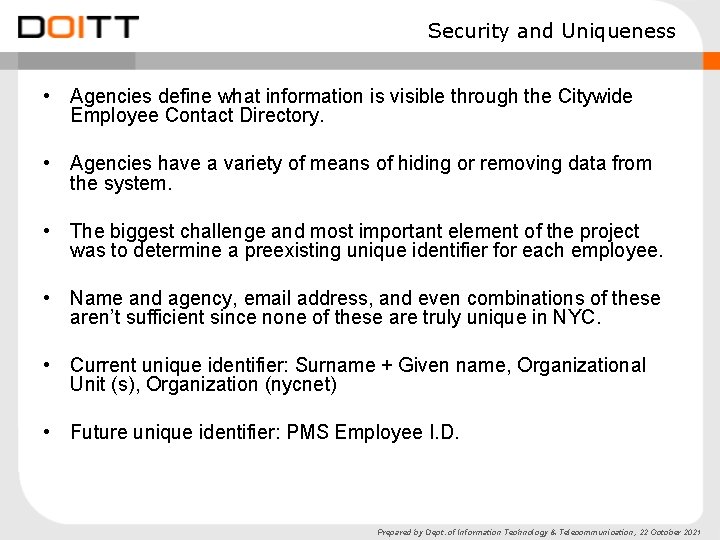
Employee White Pages • The web front-end for LDAP is the Citywide Employee Contact Directory. It is available through the City’s intranet, http: //cityshare. nycnet. • The directory has advanced filtering options. • Data appearing in the directory or through email client lookups is based on what the agency feeds LDAP and what is defined as being visible to the public. Therefore, LDAP participating agencies need to keep data clean and sensitive accounts hidden. • As part of the long-term identity management strategy, we encourage every agency to put every employee’s PMS ID and active code into the agency directory. Do. ITT is piloting a script to help agency LDAP liaisons provide this data along with the help from their HR Departments. Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

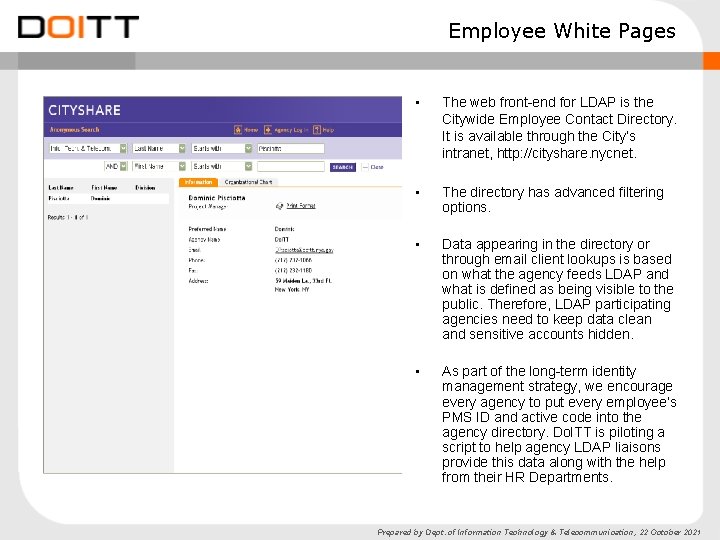
Simple Employee Lookup A more simple Employee Search that ties into LDAP and displays the same data is globally available within City. Share. Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

Next Steps Moving from White Pages to Identity Vault Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

High-level Plan • LDAP meta-directory building block is in place for the next step in establishing a citywide identity management plan. • Critical milestones will have to take place for successful implementation: – Do. ITT, FISA and NYCAPS are working together to use the PMS ID as the unique identifier, which will populate every City employee in a large citywide identity vault. NYCAPS will be established as the sole identity source of employee data in the future. – Establishment of an identity management policy board to guide the LDAP project team on key identity management issues found throughout the Employee Management Lifecycle. – Determining the best products and approaches for authentication and authorization will enable enterprise applications and agency directories to utilize one citywide meta directory for authorization. • The long-term goal is to eventually have reduced sign-on, provisioning capabilities, and digital signature capability for enterprise applications and participating agencies. Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

Key Considerations • Work with agencies to identify their requirements and IM needs as well as bring currently non-participating ones into LDAP. • Convert all batch connected agencies to dynamic connections. This will be instrumental with future user provisioning and de-provisioning in the Employee Management Lifecycle. • Create a policy board consisting of multiple agencies to make decisions on: – – – Technologies Timeframes Functionality Policies Standards • Determine the structure of the identity vault and all dependencies. • Receive buy-in from agencies. Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021

Interested in Learning More? Contact: Dominic Pisciotta Sr. Project Manager, ETD dpisciotta@doitt. nyc. gov 212 -232 -1066 OR Teri Moore Director of Enterprise Technology Development tmoore@doitt. nyc. gov 212 -232 -0938 Prepared by Dept. of Information Technology & Telecommunication, 22 October 2021